Over the past few months, the cybersecurity world was at buzz due to the infamous WannaCry ransomware attack. The attack was launched on a massive scale. The campaign started after the disclosure of NSA exploit leak by a hacker group called Shadow Brokers. Taking advantage of unpatched systems all over the globe, the attack spread across 150 countries. The WannaCry ransomware attack sought the exploit called ‘EternalBlue’. The worm-like functionality of this exploit made a deadlier impact by propagating to interconnected computers over Windows SMB protocol. Microsoft’s security bulletin MS17-010 addresses the vulnerabilities exploited in this particular attack.
This blog post will give an insight into the attack’s timeline and recent observations made around its existence till date.
Here is how it happened

On April 8, 2017, the NSA leaked exploits were made publically available by the Shadow Broker group. A week later, Microsoft issued a blog post stating its patches for the vulnerabilities targeted in the leaked NSA exploits. The exploits used in the WannaCry attack were patched in MS17-010 security bulletin released on March 14, 2017. As it’s quite visible from the above timeline (see Fig 1.), Quick Heal and Seqrite products were having the IDS/IPS detections to detect ‘EternalBlue’ and other exploits way before the first report of WannaCry got reported. Quick Heal Security Labs released an IDS/IPS advisory on May 13, 2017, to address this issue.
In addition to IDS/IPS (network based) detections, other detection mechanisms present in Quick Heal and Seqrite products were capable of detecting the WannaCry ransomware. This was the perfect example of how multi-layered security products such as Quick Heal and Seqrite could mitigate such severe attacks. The below-mentioned features played a crucial role in dealing with this attack.
- IDS/IPS (Network-based detections)
- Virus Protection (Host-based detections)
- Behavior Detection System (Host-based behavioral detections)
- Anti-ransomware system (Host-based behavioral detections specially designed to detect ransomwares)
Apart from above features, the “Backup and Restore” functionality turned out to be a useful tool for users to back up critical data on their machine.
The WannaCry attack continues
Even after more than a month since the WannaCry attack started, its traces still are seen to date. This clearly implies the existence of unpatched systems. We are still observing pings to ‘kill switch’ domains which were found in early WannaCry ransomware samples.
The ‘kill switch’ was referred to a domain name which was hard coded in WannaCry ransomware. If the domain was found alive, the WannaCry attack would stop.
Pings were seen to the below ‘kill switch’ domains,
iuqerfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
ifferfsodp9ifjaposdfjhgosurijfaewrwergwea[.]com
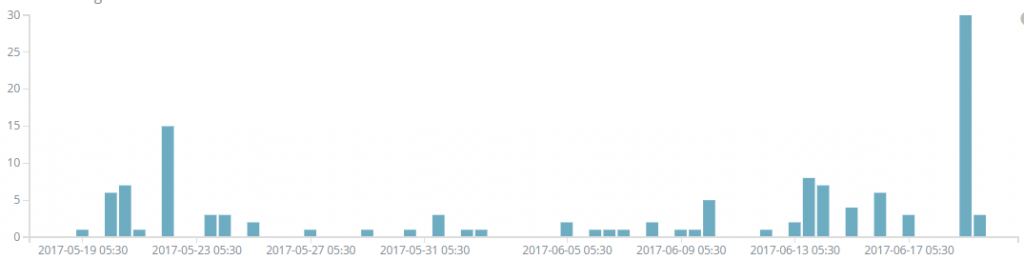
Although recorded pings for the above domains were not huge in numbers, they still show the existence of the attack.
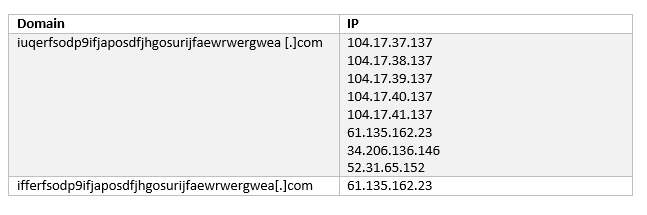
The Passive DNS replication seen for the above domains look like the below:
IPS hits trend for Shadow Broker exploits
Soon after the WannaCry ransomware attack, the exploits were integrated into various campaigns such as EternalRocks, and Adylkuzz. Below is the detection hits trend for the Shadow Broker exploits.
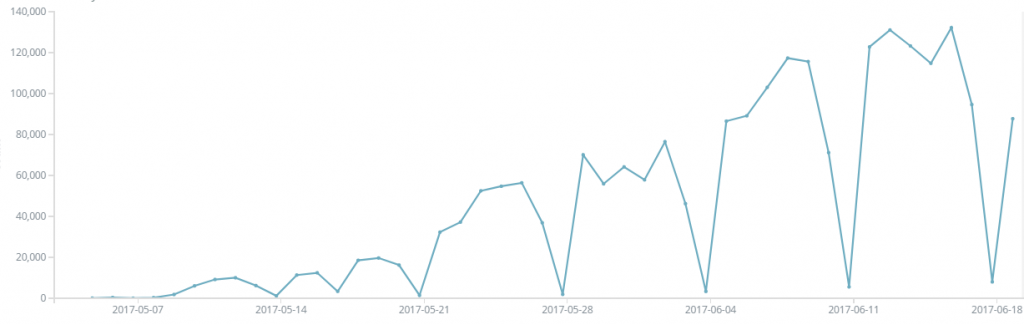
Over 2 million hits have been recorded so far for all the Shadow Broker exploits. The dips are observed on weekends.
Conclusion
All the evidence discussed in this post clearly signifies the presence of the WannaCry ransomware attacks in the wild. Despite the available patches from Microsoft, there are still unpatched machines which are still at risk. The multi layered approach in Quick Heal and Seqrite products provides a good strong defence for such complex attacks. Quick Heal and Seqrite users are protected from the WannaCry ransomware attack. We strongly recommend users to apply the latest security updates released by Microsoft and also apply the latest security updates by Quick Heal.
Also Read





No Comments