Ransomware are causing major disruptions in recent years.
Recently leaked dump of NSA EternalBlue exploit is used by cybercriminals to spread WannaCry ransomware worldwide. Dump of MS-17-010 Windows OS Vulnerability was made public by the notorious Shadow Broker group on 14th April, 2017. This vulnerability affects most of the desktop and server editions Microsoft Windows and Microsoft has released patch for the same in March, 2017. However, systems that have not applied this patch are affected by the WannaCry ransomware which uses wormlike behavior to affect vulnerable system on the network.
WannaCry Creating Havoc Worldwide
This ransomware has already affected high profile organizations in Spain, UK, China and other countries including India. These organizations include clinics and hospitals in UK, telecom, gas, electricity and other utility providers. Many universities in China have also been targeted.
In Quick Heal Security Labs, till now 3000+ WannaCry ransomware attacks have been detected out of which around 2450 are from India. Quick Heal and Seqrite have successfully defended these cases of attacks from compromise and data encryption.
How WannaCry Ransomware works?
Attack is carried when systems are connected to network using SMB services. These services are attacked and exploited by “EternalBlue” exploit, planting WannaCry Ransomware causing the file encryption after successful execution. When files are encrypted, it appends “.WNCRY” extension to all encrypted files.
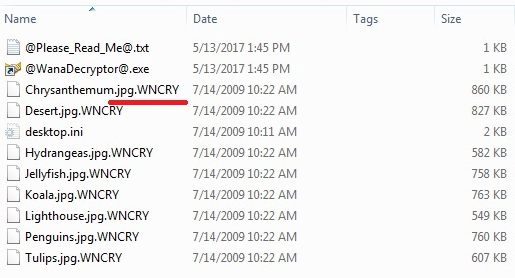
Image 1: WannaCry Ransomware Encrypted files
After successful exploitation, it adds below files to the system:
- C:\ProgramData\<random_alphanumeric>\@WanaDecryptor@.exe
- C:\ProgramData\<random_alphanumeric>\tasksche.exe
- C:\ProgramData\<random_alphanumeric>\taskdl.exe
- C:\ProgramData\<random_alphanumeric>\taskse.exe
WannaCry adds below malicious registry entries to make persistence into the system, so that it could launch the infection after each system reboots:
- [HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run]
- “xwjfzbtm432″=”\”C:\\ProgramData\\<random_alphanumeric>\\tasksche.exe\””
After successful encryption it shows below warning message containing instructions to follow to recover the files. The countdown timer is shown to create panic so as to make the victim pay the demanded ransom. Otherwise it threatens that all encrypted data would be deleted. WannaCry shows ransomware warning message in the language of current region.
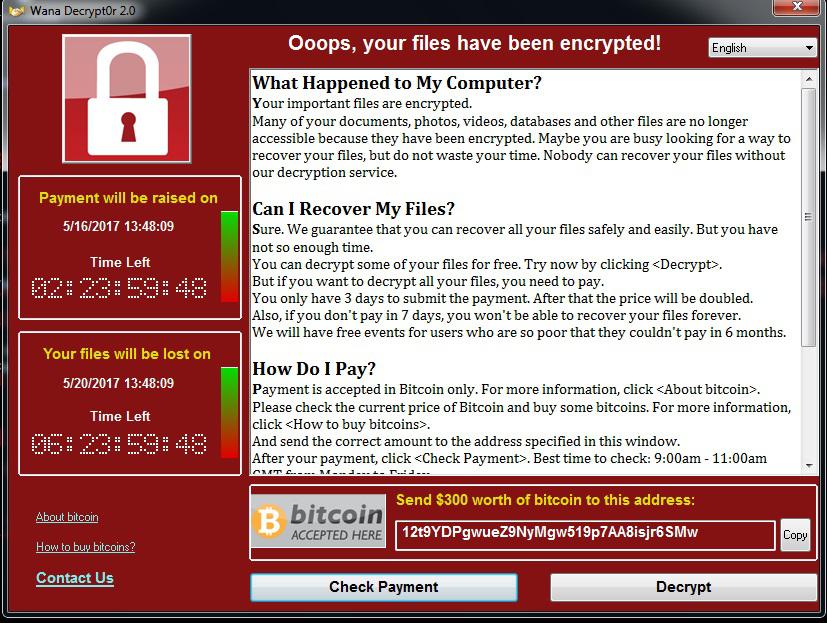
Image 2: WannaCry Ransomware Warning Message
How Seqrite Endpoint Security protects against WannaCry Ransomware?
Seqrite Virus Protection successfully detects and cleans malicious file responsible for file encryption as “TrojanRansom.Wanna”
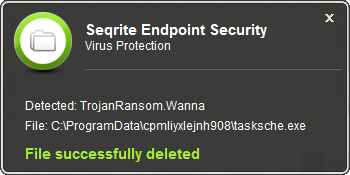
Image 3: Seqrite Virus Protection Warning Message
Seqrite Advanced Behavior Detection System proactively detects this ransomware activity successfully based on its behavior. User needs to click on BLOCK button in this situation to stop encryption activity.
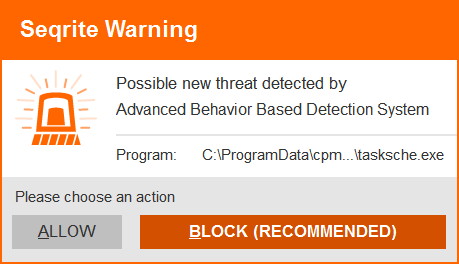
Image 4: Seqrite Advanced Behavior Based Detection Prompt
Seqrite Anti-ransomware technology also successfully detects file encryption activity of WannaCry Ransomware:
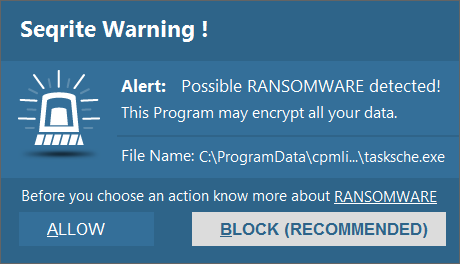
Image 5: Seqrite Anti-ransomware detects encryption activity
Recommendations to reduce ransomware attacks:
Quick Heal Security Labs highly recommends taking the following measures to reduce the risk of infection by WannaCry Ransomware:
- Apply Patch for vulnerabilities used by this ransomware from Microsoft
- Take regular back up of your important data and periodically check the backup restoration process to make sure files are getting properly restored.
- Ensure that security solutions are switched on all nodes of the network.
- Always keep installed security software up-to-date with latest signature updates.
- Perform Full System Scan using installed security software.
- Avoid clicking on links and opening attachment in emails from unknown and suspicious sources.
Acknowledgement:
Subject matter experts –
Prashil Moon and Dipali Zure
Quick Heal Security Labs





No Comments