The Microsoft Windows SMB (Server Message Block) is being actively exploited in the wild, post the Shadow Brokers (TSB) leak in April 2017. According to Microsoft’s blog, the exploits were already covered in previously released security bulletins. The Shadow Broker exploits named ‘EternalBlue’ and ‘EternalRomance’ and ‘EternalSynergy’ are addressed by Microsoft in security bulletin MS17-010. According to security advisory published by CCN-CERT of Spain’s national computer emergency response team on May 12, 2017, the infamous exploit ‘EternalBlue’ is currently being used in a massive ransomware outbreak. The ransomware used in this campaign is ‘WannaCrypt’ (aliases WannaCry , WanaCrypt0r , WCry). Microsoft’s latest updated on this outbreak are tracked here.
Quick Heal & Seqrite Detections
Quick Heal and Seqrite have released the following IPS detections for the vulnerabilities reported in security bulletin MS17-010.
- VID-01899 : [MS17-010] Windows SMB Remote Code Execution Vulnerability
- VID-01901 : [MS17-010] Windows SMB Remote Code Execution Vulnerability
- VID-01906 : [MS17-010] Windows SMB Remote Code Execution Vulnerability
- VID-01907 : [MS17-010] Windows SMB Remote Code Execution Vulnerability
- VID-01912 : [MS17-010] Windows SMB Information Disclosure Vulnerability
Quick Heal and Seqrite users are protected from the vulnerabilities reported in security bulletin MS17-010.
IPS Hits Trend
As observed in Quick Heal Security Labs, below is the trend of the exploitation for MS17-010.
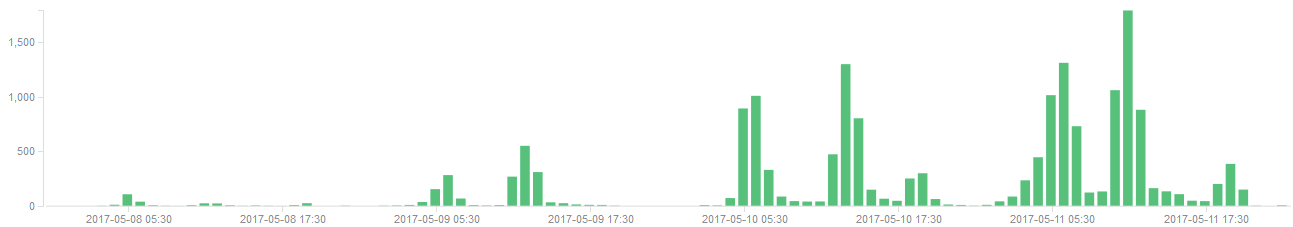
Exploitation of vulnerabilities reported in MS17-010
- Hits reported after May 09, 2017 shows a spike in the activity.
Safety Measures
- Disable SMB service (running on port 445) if not used.
- Apply security updates from Microsoft, especially for MS17-010.
- Apply the latest security updates released by Quick Heal.
Conclusion
The high-profile leak from Shadow Broker has resulted in massive ransomware outbreak. Such leaks enable attackers to use the readily available exploits in various such outbreaks. We advise our users to stay protected by following safety measures stated above.



