New targeted ransomware called SNAKE or EKANS was found in early January. Malware is written in the Go language and it is heavily obfuscated and goes after ICS environments. Snake Ransomware seems to be distributed via a focused and targeted campaign that concentrates exclusively on targeting business enterprise networks — it uses AES and RSA for encryption. Upon infection, relevant files are overwritten with encrypted data. Each modified file is also tagged with the string “EKANS” at the end of the file.
Malware includes a check for a hardcoded internal system name and public IP addresses, In Our case it is related to Honda Company. It exits immediately if DNS queries to an internal domain belonging to Honda are not resolved.
Technical Analysis:
The file is a PE32 executable for MS Windows and has “.symtab” section with fewer imports which indicates that file is written & compiled in Go language.
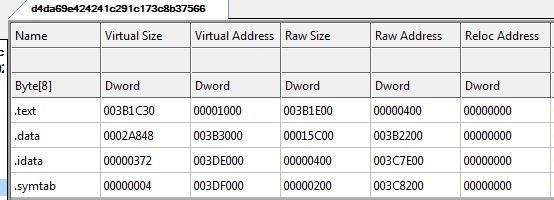
Various strings are found which confirms that the binary is compiled in Go language. Below is the Go build Id.

The malware starts requesting a DNS resolution of “MDS.HONDA.COM”. Honda is recently hit by a ransomware cyber-attack on its technology systems. So it seems this sample is the one used to compromise Honda’s site.
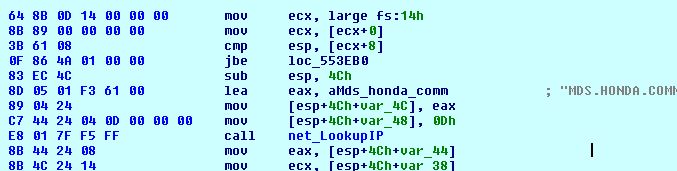
Malware resolves “MDS.HONDA.COM” to the associated IP address, it also contains a reference to the US IP address 170.108.71.15, which resolves to the ‘unspec170108.amerhonda.com‘ hostname. If the DNS resolution fails, then the malware will abort its execution.
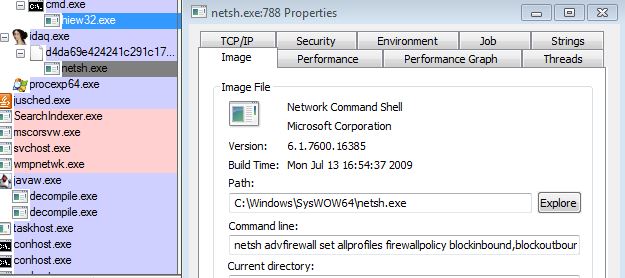
When the malware finds that domain name has been resolved then it changes the firewall settings by sending a command to netsh.exe (networking tool). The command passed is:
“Netsh advfirewall set allprofiles firewallpolicy blockinbound,blockoutbound”.
This command will block all incoming and outgoing connections for all profiles that do not match the in and out rules using the Windows firewall function.
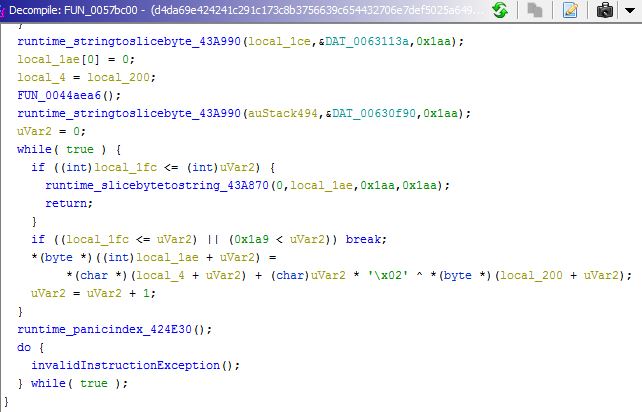
Malware uses below algorithm to decrypt all strings which are used during the execution of malware, however, each encrypted data uses a different XOR key.
The below decryption loop decrypt RSA public key, which will be used to encrypt each of the AES keys used to encrypt the files.
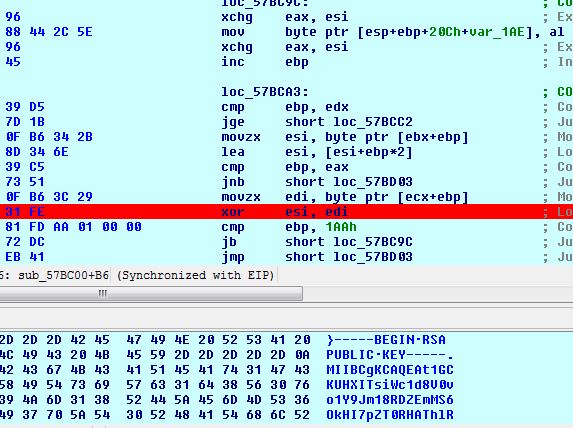
Decompiled code for the algorithm is given as below.
Malware checks for the presence of the Mutex named “EKANS”. If present, the ransomware will stop its execution and it will not infect the systems. Otherwise, the mutex is created and the infection moves forward.
It contains a hard-coded process and service list which is present as encrypted strings of the malware. If any of the services are running in the victim system, the ransomware will stop the service. Also, if any processes are running in the system it kills the processes using the function TerminateProcess(). Some of the process names are given below.

Malware will remove all Volume Shadow Copy backups found on the system. Malware skips some extensions of the file from encryption. Some of those are mentioned below:
.sys .mui .tmp .lnk .config .tlb .olb .blf .ico .manifest .bat .cmd .ps1 etc
Some of the extensions which are mentioned below are decrypted by the malware although these are not used while encryption.
The encryption process of snake is a mix of symmetric and asymmetric cryptography which includes AES-256 and RSA-2048. A symmetric key is required for encrypting and decrypting of files. This Symmetric key is encrypted with the attacker’s public key. Decryption is only possible with the attacker’s private key. So, this makes decryption difficult or impossible for security vendors.
Malware uses AES CTR mode for encryption of the file with a 0x20 bytes random key and a random IV of 0x10 bytes. RSA public key is hardcoded in the file. After encryption malware appends “EKANS” marker at the end. EKANS is reverse of SNAKE.
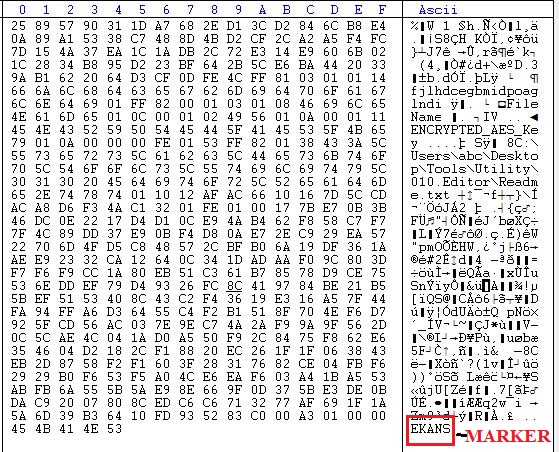
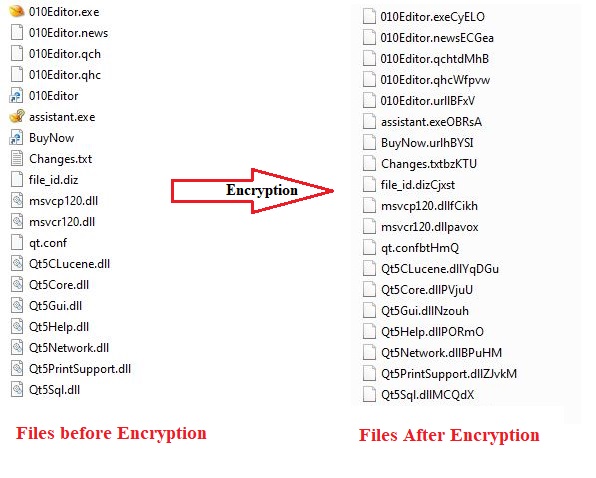
After encrypting all the files, malware renames each encrypted file. It appends a random 5-character string to the file’s extension. Extensions are ransom so it makes it difficult to identify the ransomware through extensions. Below is the image which shows the renaming of files by the snake ransomware.
Conclusion
Ransomware has become a perpetual threat for individual users and businesses too. Once it encrypts any files, it is very difficult to decrypt the data. Given the extent of the damage any ransomware can do to your data, you must follow the recommended security measures mentioned below.
- Use a multi-layered antivirus that can stop real-time threats.
- Keep your antivirus up to date.
- Update your Operating System regularly as critical patches are released every day.
- Keep your software up to date.
- Never directly connect remote systems to the Internet.
- Do not click on links or download attachments in emails received from unknown sources.
- Take regular data backup and keep it in a secure location.
- Audit gateway system & check for misconfiguration.
Seqrite products are equipped with multilayered detection technologies like IDS/IPS, DNA Scan, Email Scan, BDS, Web Protection and Patented Anti Ransomware detection. This multi-layered security approach helps us in protecting our customers against these type of Ransomware and other known, unknown threats efficiently.
Indicator of Compromise
d4da69e424241c291c173c8b3756639c654432706e7def5025a649730868c4a1




