An antivirus software keeps your computer safe from malware, viruses, online threats, and suspicious or harmful elements. Although bypassing this protective guard is a difficult task for attackers, they never stop trying to do so. Recently, we came across a malware that is designed to interfere with the infected system’s security software by disallowing its certificate. This malware is called CertLock.
The Infection Chain
CertLock enters into the victim’s system by bundling itself with other free software. On an infected system, when the user tries to access their installed security software, they come across an error message saying that the access is blocked by Windows. The malware also blocks new installation of security programs in infected systems. Without any security, these systems are left defenseless and hence stay completely at the mercy of the attacker.
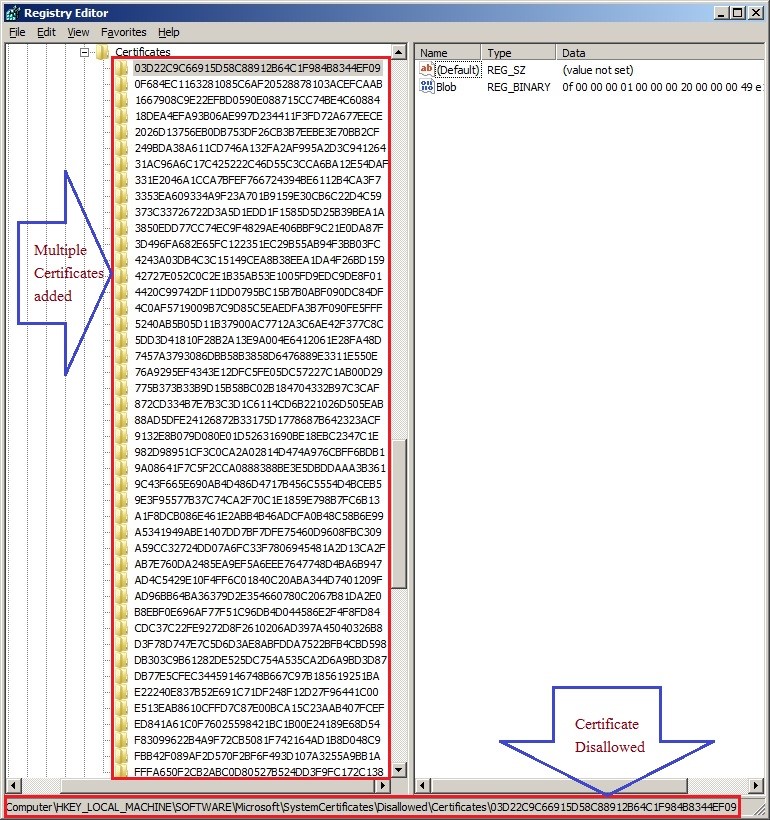
CertLock manipulates the Windows feature of system certificates. These certificates are trusted by the operating system and can be used by applications to make themselves trustworthy. In this case, the attacker added certificates of the security software to a special registry of Windows, which prevents programs signed with that certificate from getting executed on the system.
These certificates are added under the below registry entry:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\Disallowed\Certificates
A certificate’s key is added to the above registry with a certificate value in a blob.
Any software with certificates registered under the above key is not recognized as a trusted publisher and this prevents its installation or execution in the infected machine.
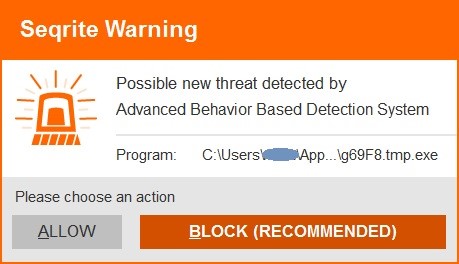
Seqrite Detection
CertLock does not affect the functioning of an installed Seqrite product nor can it block any new installations.
Seqrite’s Behavior Detection System successfully detects and blocks CertLock for performing any malicious activity.
Seqrite detects the malicious files of CertLock malware with signature-based detection as ‘Trojan.CertLock’.
Steps to stay safe against malware such as CertLock
- Free software, especially those with unverified publishers are usually used by attackers to spread malware. Always go for genuine and licensed software.
- Use a security software that offers multilayered protection. Keep the software updated to stay safe from the latest and emerging threats.
- Always keep your Operating System and programs patched with the latest updates.
Acknowledgement
Subject Matter Expert
- Prashil Moon | Quick Heal Security Labs




