Estimated reading time: 6 minutes
Cyber-attacks through phishing emails are increasing and generally, attackers use DOC embedded macros to infiltrate victim’s machine. Recently Quick Heal Security Labs came across a Phishing e-mail sample which uses Microsoft’s equation editor exploit to spread Hawkeye keylogger. Cybercriminals...
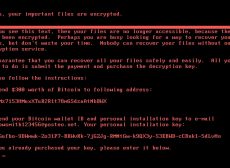
Estimated reading time: 3 minutes
Earlier we had blogged about how JAVA based jRAT malware were evolved in the recent times. At Quick Heal Security Labs, we are actively observing jRAT campaigns happening in the wild. These JAVA malware spread through phishing campaigns. While analyzing one such phishing campaign, we found...
Estimated reading time: 4 minutes
.NET Framework Remote Code Execution Vulnerability (CVE-2017-8759) is a code injection vulnerability in the SOAP WSDL parser of .net framework. This vulnerability was a zero-day when it was spotted in the wild. Quick Heal Security Labs had released advisory in the month of...
Estimated reading time: < 1 minute
The recent zero-day vulnerability in Microsoft Office vulnerability CVE-2017-11826 enables attackers to perform a Remote Code Execution on targeted machines. According to a recently published blog post, this vulnerability is being exploited in the wild. Microsoft has released a security update on October 10, 2017,...
Estimated reading time: 2 minutes
A critical remote code execution vulnerability has been discovered in famous web application framework Apache Struts, which allows attackers to execute arbitrary code. To address this issue, Apache Struts has issued a security advisory and CVE-2017-9805 has been assigned...