Earlier we had blogged about how JAVA based jRAT malware were evolved in the recent times. At Quick Heal Security Labs, we are actively observing jRAT campaigns happening in the wild. These JAVA malware spread through phishing campaigns. While analyzing one such phishing campaign, we found that an International embassy in India was being targeted by phishers. The malware used in the phishing campaign was the infamous JAVA malware called jRAT. Phishers sent phishing emails to the official email address of the targeted embassy.
This is how the phishing email looks like.

As shown in the figure above, a fake shipment notification by DHL is sent to the targeted email address. This is an example of a classic phishing email scam. The overall content of the email looks neat and attractive enough to trick the user into opening the attachment in order to know more about this shipment notification. The email attachment “ORIGINAL SHIPPING DOCUMENT.zip” is a ZIP archive file containing a “ORIGINAL SHIPPING DOCUMENT.jar” file. It’s unusual for a shipment notification to have “.jar” file as an attachment. Once the user double clicks on this jar file, the malware is executed. Nowadays, many applications require JAVA/JRE for their execution. So, the chances of having a JAVA/JRE installed on the end user systems are extremely high. This increases every possibility of the execution of the Java-based malware on the targeted system.
Seqrite detection
This particular phishing attempt carried out on the targeted embassy was successfully blocked by Seqrite products with its JAVA detection “JAR.Suspicious.A”.
Infection Chain
A typical infection chain found in this JRAT phishing campaign is as follows.
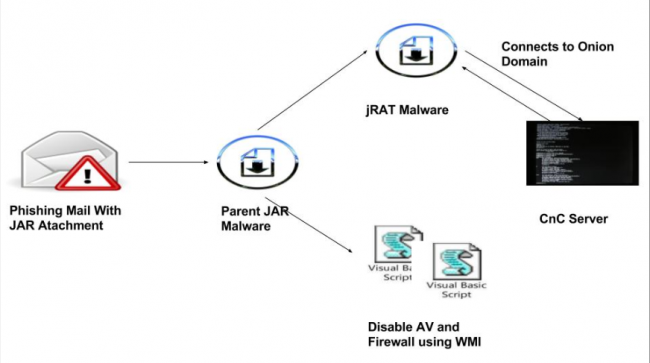
Technical details
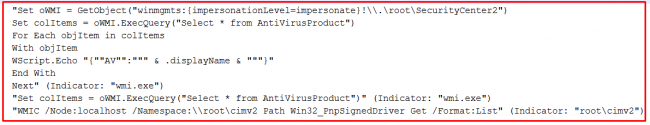
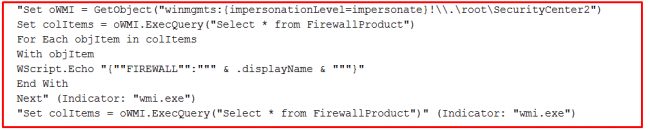
As depicted in fig 2, upon execution of the ‘Parent JAR’ malware, it drops 2 VB script files and jRAT malware at ‘%Temp%’ location which are embedded in it. These VB scripts are responsible for identifying different antivirus products as well as firewall products installed on a system. It also checks for ‘Win32_PnpSignedDriver’ pipe which is required to identify a virtual environment. And if this pipe is found to be open, then the malware will stop its activity.
Below are the images of VBS files.
The dropped JRAT file is connected to a CNC domain ‘vvrhhhnaijyj6s2m.onion[.]top‘. This CNC domain is hosted on 46.246.120.179. The reputation of this domain and the IP is malicious according to online scanners. The communication happens over an SSL channel.
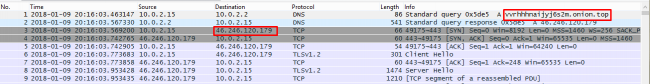
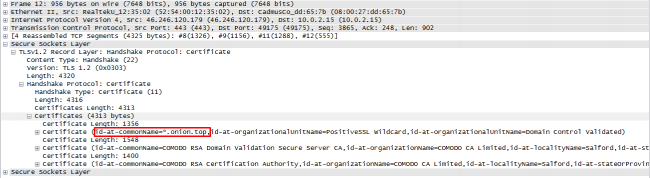
At the time of our analysis, the CNC server did not respond with the final payload. Generally, we have observed infostelaer malware being delivered in ongoing jRAT campaigns.
Although phishing is an old technique to spread malware, it is still one of the simple and most effective techniques used by phishers. Using this simple technique of malware distribution, phishers are going after high profile targets such as the internal embassy in this case. We advise our users to stay protected by keeping their Endpoint Security solution(EPS) up-to-date with the latest security updates.
Security measures
Here’s an infographic that explains phishing. And below are some useful tips to stay away from phishing attacks.
- Do not open emails that come from unknown, unwanted or unexpected sources.
- Do not click on links or download attachments in such emails.
- Do not open email attachment with extension such as .js, .jar, .exe., and .pdf.
- Disable VBA macro in Microsoft Office application.
- Apply all recommended updates on your Operating System, programs like Adobe, Java, Internet browsers, etc.
- Make sure that your Endpoint Security solution(EPS) software is up-to-date.
- Take regular backups of your files.
Indicators of compromise
DHL Shipment Notification: 85482550044
ORIGINAL SHIPPING DOCUMENT.zip
ORIGINAL SHIPPING DOCUMENT.jar
F2727B26A75F9DF01E464B9144117AE1
B01F4758F4FD791B851D64FC16B56D08
vvrhhhnaijyj6s2m.onion[.]top
46.246.120.179
Subject Matter Experts
Pradeep Kulkarni, Prashant Kadam | Quick Heal Security Labs





No Comments