Microsoft is about to release a new update for its Windows 10 Operating System called Windows 10 May 2020 Update (also known as Version 2004). The company has codenamed it “20H1” and will likely make it available by the end of May 2020.
Windows 10 20H1 update brings in multiple new features, enhancement and fixes.
Click here for more information.
In our internal validations with a pre-release version of Windows 10 20H1 update, we observed the system with existing clients of Seqrite Encryption Manager (SEM) 1.2.x going into repair mode after applying the latest Windows 20H1 Update.
To avoid the above-described situation, Seqrite has released an important update which will make the existing Windows 10 SEM clients and server compatible with the Windows 20H1.
This document describes the steps to apply this important SEM update and some precautionary measures to be taken before applying Windows 10 20 H1 update.
Important: Seqrite recommends that all the endpoints must be restarted (if restart is pending, due to any software updates/installation) before updating the SEM server.
There are two mandatory steps to be performed before applying Windows 10 20H1 update:
- Update your SEM 1.2.x server with the released update
- After successful update configure SEM Policies
Update your SEM 1.2.x server with the released update
You can apply the update using one of the following methods:
- Through Seqrite Encryption Manager
- Through Seqrite Encryption Manager Installer
Through Seqrite Encryption Manager
1. Login to SEM Server as an Administrator.
2. In the title bar, click on Administration.
3. In the left pane, click on Software update.
4. Click on Check and Download Now In the older version (1.2.0), click on the Check Now button.
5. The updates will be displayed, in the following format
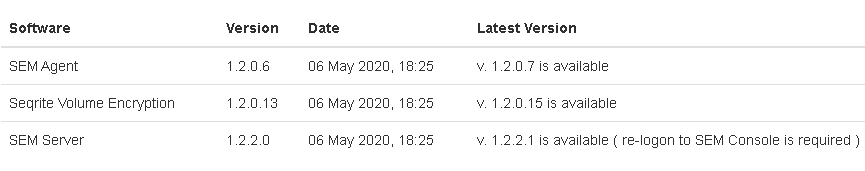 6. The Latest Version column will show the versions of the modules.
6. The Latest Version column will show the versions of the modules.
7. Click on the Update Now button, the following popup will be shown with the updated information
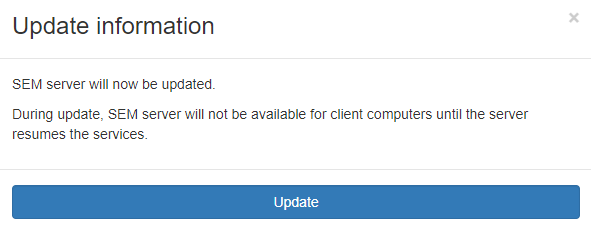 8. Click on Update.
8. Click on Update.
SEM Server will update the existing Server silently. Once the update is applied successfully, Seqrite Encryption Manager version will be updated from 1.2.x to 1.2.2.1.
9. Refresh the web console after few minutes (approximately after 5-7 minutes) to login to the updated SEM Server.
Through Seqrite Encryption Manager Installer
1. Download Seqrite Encryption Manager installer from here
2. Run downloaded installer on the existing SEM Server.
3. In the SEM Upgrade setup dialogue box, click Next.
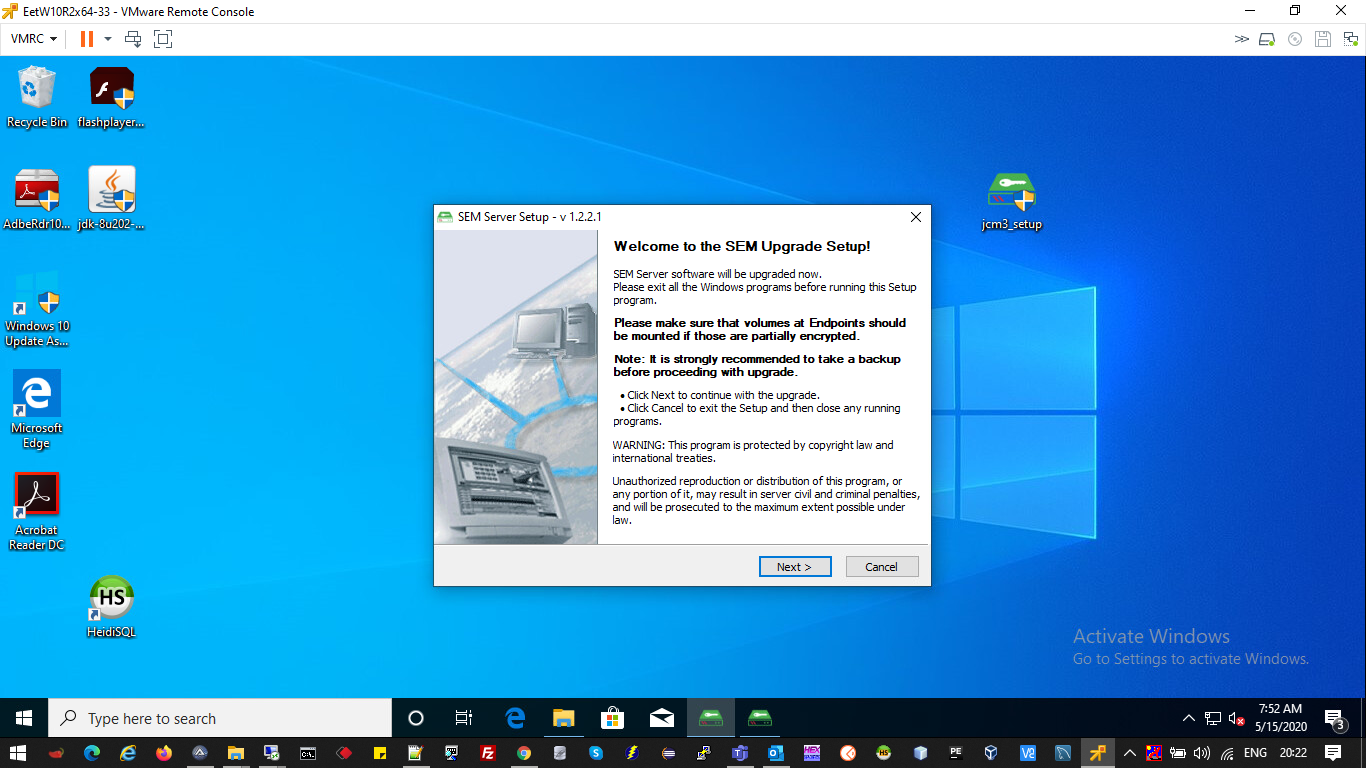
4. On the License Agreement dialogue box, select “I accept the Agreement and consent checkbox and click Next.
5. In SEM setup dialogue box, click Finish, to start the update.
Once the Seqrite Encryption Manager is updated successfully, Seqrite Encryption Manager version will be upgraded from 1.2.x to 1.2.2.1.
6. To login to SEM Console, click Start Server.
Note:
SEM clients will be upgraded to the latest version automatically, whenever the client communicates with the server after the server update.
After successful update configure SEM Policies
Configure the SEM policies as described below before applying Windows 10 20H1 update.
- If the policy is set as Encrypt, then follow the Encrypted Policy procedure
- If the policy is set as Manage Locally, then follow the Manage Locally Policy procedure
Encrypted Policy procedure
If the policy is set as Encrypted, then perform the following steps
1. Login to SEM console as Administrator
2. Click Seqrite Volume Encryption: Encryption Policies, (refer the screenshot below)
3. In the Edit Policy dialogue box clear the Encrypt volumes without driver letter (mount points) (refer the screenshot below)
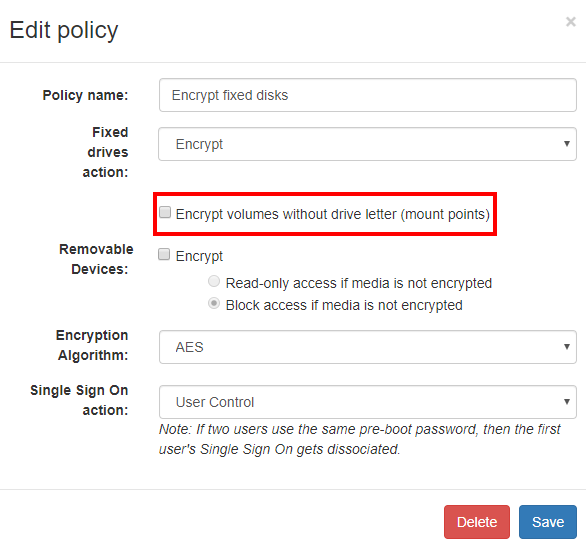 4. Do not change any other option (Recommended)
4. Do not change any other option (Recommended)
5. Repeat the above steps [1-4] for all the Encrypt polices
Manage Locally Policy procedure
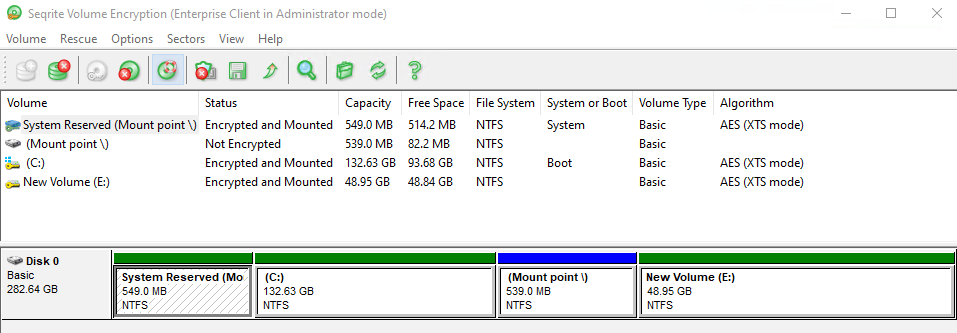
Identify the endpoints on which the Manage Locally policy is applied. Before the Windows update, first, decrypt the mount points. Perform the following steps:
1. On the endpoint, go to Start > Seqrite Volume Encryption folder.
2. Open Seqrite Volume Encryption
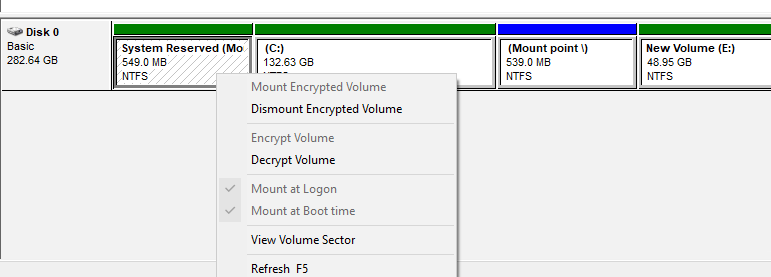
3. If the System Reserved (Mount Point) is encrypted, then right-click on the encrypted volume (mount point) and select Decrypt Volume (refer screenshot below)
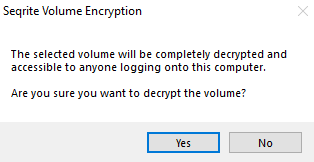
4. The confirmation dialogue box is shown, click Yes to proceed.
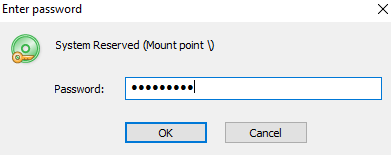
 5. The password dialogue box is shown, enter the password and click OK.
5. The password dialogue box is shown, enter the password and click OK.
Decryption starts for the selected volume.
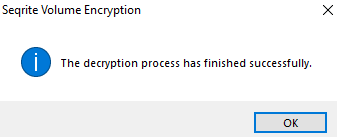
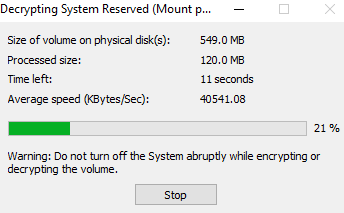 6 A success message is displayed after successful decryption, click OK to exit.
6 A success message is displayed after successful decryption, click OK to exit.