Over the past few months, job economy has been marked by uncertainty, with constant news about layoffs, restructuring, hiring freezes, and aggressive cost-cutting measures. This atmosphere has created widespread anxiety among both employees and organizations, and cybercriminals have quickly learned to exploit these emotions.
Malware authors increasingly craft phishing emails and malicious attachments disguised as termination notices, updated HR policies, severance documents, or “urgent layoff lists,” preying on people’s fear and curiosity. In moments of stress, employees are more likely to click on suspicious files or links without verifying their authenticity, giving attackers an easy entry point into corporate networks. As layoffs continue to dominate headlines, threat actors are leveraging this vulnerability at scale, using believable layoff-themed lures to deliver malware, steal credentials, and launch broader cyberattacks.
At Seqrite Labs, during our monitoring we observed one of such a spam campaign distributing malware through emails disguised as internal HR announcements. Attackers delivered a malicious attachment posing as a “staff record pdf”. Files in attachment is an NSIS compiled remote access tool, Remcos.
Initial Vector
Initial vector of the campaign is an email pretends to be a “Staff Performance Report for October 2025”, supposedly sent by the company’s HR Department. The message is intentionally brief and formal, with a reference to “employees to be terminated”, designed to increase the chances of the attachment being opened.
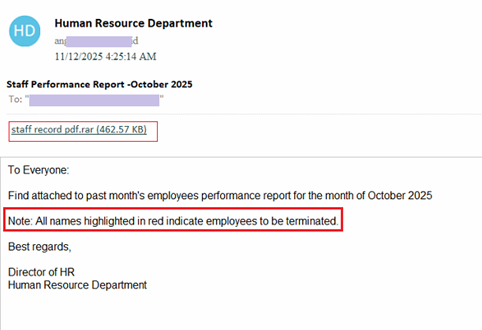
As we can see in above image, despite appearing to contain a PDF document, the email attachment is a RAR archive named using a double-extension (pdf.rar) to conceal its true nature. Inside the archive is not a document, but a NSIS-compiled executable masquerading as “staff record pdf”. Upon execution, the file performs initialization, configuration and further malicious activity.
This neatly designed spam email highlights how threat actors continue to rely on social engineering and lures tied to current organizational trends to gain initial access to targeted victims.
Analysis of Attachment
The email attachment, named “staff record pdf.rar”, is intentionally designed to appear like a PDF file. Inspection of the archive reveals that it contains a single Windows executable with name “staff record pdf.exe”, masquerading as a document. This double-extension naming convention (pdf.exe) is a common technique used to mislead users and evade basic file-type identification.
Analysis of the Embedded Executable File
The executable file embedded in attachment is a Remcos RAT and is a NSIS (Nullsoft Scriptable Install System) compiled executable, a packaging format commonly abused by threat actors to conceal its intent.
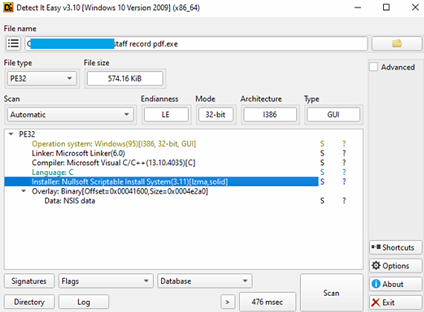
Once the file is executed it drops NSIS related configuration files at below location –
- C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\
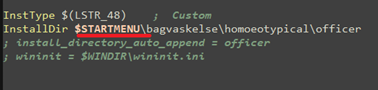
Then the file is self copied to below location –
- c:\ProgramData\Remcos\remcos.exe
Remcos creates and stores victim related and other configuration data at below registry –
- HKCU\Software\Rmc-<VictimID>
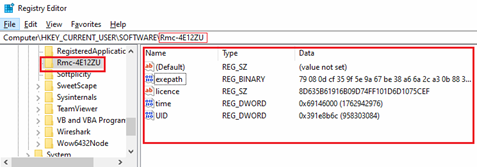
Key and Values in configuration registry –
- exepath – Values are Encrypted and stores path to the installed EXE.
- licence – Probably, cracked Remcos licence key.
- time – UNIX timestamp when Remcos first executed.
- UID – Victim machine ID.
Persistence
Persistence is achieved by adding itself in commonly known Run registry –
- HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
- Rmc-4E12ZU = c:\ProgramData\Remcos\remcos.exe
Post-Deployment activity and CnC Communication
After setup, the Remcos payload spawns multiple threads, each responsible for different operational components of the RAT. These threads handle capabilities such as keylogging, screen capture, clipboard monitoring, and the main command-handling loop.
A few seconds later, the malware establishes an outbound connection to its command-and-control server , confirming that the RAT is fully active and ready to receive instructions from the attacker.
Conclusion
This campaign highlights how threat actors continue to exploit ongoing workforce-related conditions to deliver malware through convincing social-engineering lures. In this case, a simple HR-themed message was enough to disguise an NSIS-based Remcos on the system.
Once installed, Remcos establishes persistence, collects system information, and prepares the infected host for remote access.
Organizations should ensure that staff remain cautious when handling unsolicited HR or performance related communications and reinforce email security controls capable of detecting malicious archives and executable payloads.
Indicators of Compromise (IoC)
Hashes (MD5)
c95f2a7556902302f352c97b7eed4159
6f7d3f42fa6fe3b0399c42473f511acc
76c28350c8952aef08216d9493bae385
CnC
196.251.116.219
Seqrite/QH Detection
Trojan.Remcos.S38451216
MITRE Attack Tactics, Techniques, and Procedures (TTP’s)
| Tactics (ATT&CK ID) | Techniques / Sub-technique (ID) |
Procedure |
| Initial Access (TA0001) | T1566.001 | Delivery of a malicious HR-themed email. |
| Execution (TA0002) | T1204.002 | User opens the double-extension file disguised as a PDF. |
| Defense Evasion (TA0005) | T1036 | Executable masquerades as a PDF inside a RAR archive. |
| Defense Evasion (TA0005) | T1027 | Use of NSIS compiler to hide actual code. |
| Persistence (TA0003) | T1547.001 | Remcos registers itself at – HKCU\Software\Microsoft\Windows\CurrentVersion\Run for autorun. |
| Persistence (TA0003) | T1112 | Store configuration at HKCU\Software\Rmc-<VictimID>. |
| Discovery (TA0007) | T1082 | Collects host information after execution (UID, timestamp, paths). |
| Collection (TA0009) | T1056.001 | Keylogging module |
| Collection (TA0009) | T1113 | Threads for screenshot capture. |
| Collection (TA0009) | T1115 | Clipboard monitoring thread initialized. |
| Command and Control (TA0011) | T1071.004 | Outbound connection to attacker-controlled server |
Authors
Prashil Moon
Rumana Siddiqui




