Estimated reading time: 4 minutes
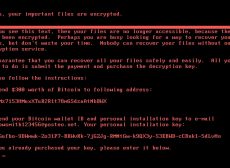
If you think that schools and colleges don’t need any cyber security as they don’t store any data that will interest criminals, think again. In May 2015, Pennsylvania State University’s engineering school was the target of a cyber attack. The...
Estimated reading time: 3 minutes
The education sector, especially institutions of higher education, have been the focus of Information Security Professionals in recent times. It has been observed that the education sector ranks very high in the list of targets for cyber-attacks. Investigations have...