Remote Access Trojans are programs that allow attackers to gain unauthorized access to a targeted computer without the victim’s knowledge. Java RAT malware is a Trojan-Dropper written in Java. It is designed to steal passwords, access files, for keylogging (recording what the user types on the keyboard) and for screen-capture. Information collected by a RAT is forwarded to a remote server controlled by the attacker.
Distribution Method
A Java RAT malware arrives via spam emails that contain malicious attachments (fig 1).
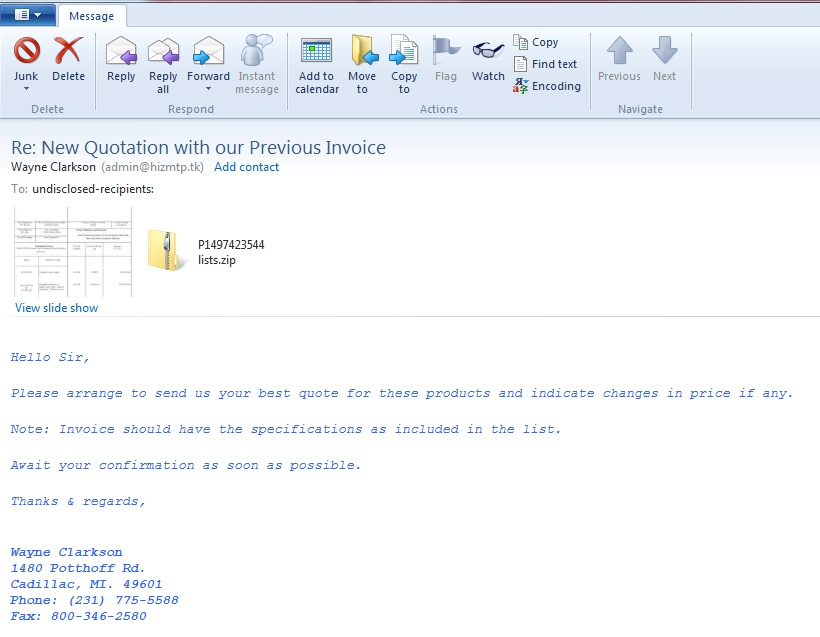
How Java RAT gets into a system
Once a JAR file is executed, it drops a copy of itself onto the below path with the name ‘LyOCtxhwRyz.yrDUql’
Path: %userprofile%\ YzQqKjGoxHz(Hidden Folder)
For example, C:\Users\Public\YzQqKjGoxHz
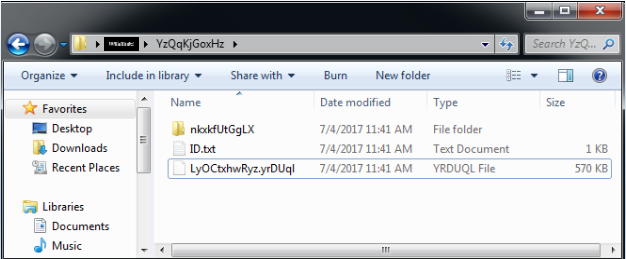
The malware drops the following files:
C:\Users\Public\YzQqKjGoxHz\ID.txt
C:\Users\Public\AppData\Local\Temp\OlfYXmVqfL9024669788070560515.reg
%temp%\Retrive2638932198378221530.vbs
%temp%/\ _0.354484486304158635925511204328476438.class
%Application Data%\Oracle\ (Contains copy of files from java installation folder)
It creates the following folders:
C:\Users\Public\YzQqKjGoxHz (Contains copy of actual malware i.e JAR file)
C:\Users\Public\fUTkALeaTxM
The below registry entry dropped by the malware is used to launch itself every time the system boots and download the executable file to infect the system.
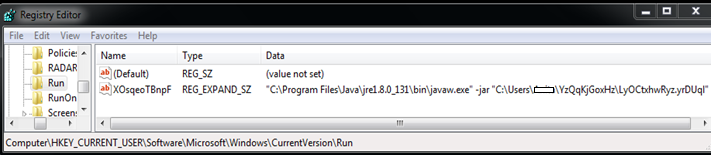
The malware adds the below registry entries to disable security solutions and different analysis tools.
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\procexp.exe]
“debugger”=”svchost.exe”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\wireshark.exe]
“debugger”=”svchost.exe”
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SCANNER.EXE]
“debugger”=”svchost.exe”
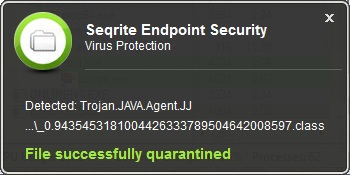
Seqrite Detection
Seqrite’s real-time protection detects the JAR file and its component as ‘Trojan.JAVA.Agent.JRAT’ and ‘Trojan.JAVA.Agent.JJ’
Security measures to stay away from Java RAT
- Do not click on links or download attachments that arrive in emails from unwanted or unexpected sources.
- Apply recommended security updates for your computer’s Operating System and all other programs such as Adobe, Java, Internet browsers, etc.
- Use an antivirus software that gives layers of protection against infected emails and malicious websites. Keep the software up-to-date.
- Take regular backups of your important data.
- Free software, especially those with unverified publishers are usually used by attackers to spread malware. Always go for genuine and licensed software.
ACKNOWLEDGMENT
Subject Matter Expert
- Anita Ladkat | Quick Heal Security Labs




