We are aware of an ongoing Supply Chain Attack affecting Kaseya VSA users. As per the recent update from Kaseya, the attackers were able to exploit zero-day vulnerabilities in the VSA product to bypass authentication and run arbitrary command execution. This allowed the attackers to leverage the standard VSA product functionality to deploy ransomware protection to endpoints. There is no evidence that Kaseya’s VSA codebase has been maliciously modified.
Kaseya has issued an advisory on this:
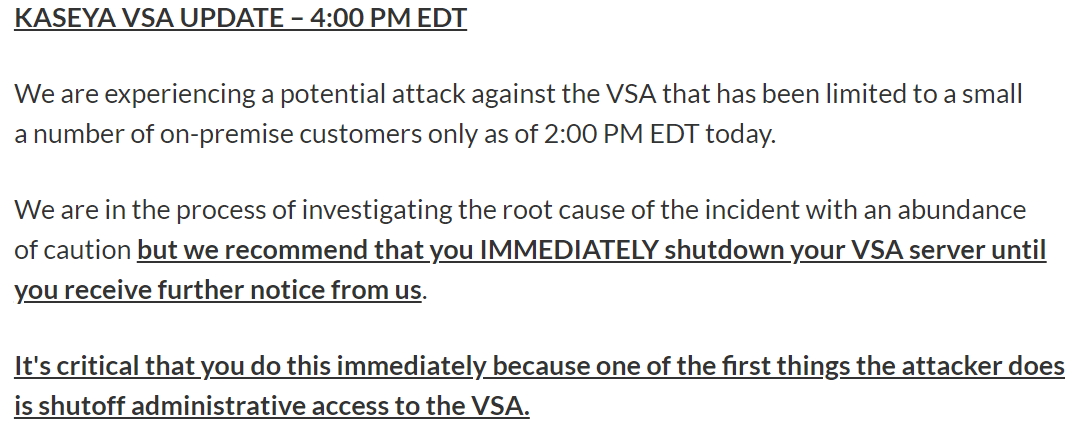
What is Kaseya VSA, and how severe is this Supply Chain Attack?
KASEYA VSA is a Unified Remote Monitoring & Management software used for centralized Endpoint Management and Network Monitoring. Many MSPs (Managed Service Providers) use this software for remote patch management and client monitoring of their customer’s IT infrastructure. This software runs with higher privileges on such systems and, if exploited, can spread laterally very quickly. To that end, the damage could be devastating!
If you are using Kaseya VSA software, we request you to follow the advisory issued by Kaseya and immediately shut down your VSA server(s) until further communication from Kaseya.
Additionally, keep your Seqrite EPS products updated with the latest virus definitions. We at Seqrite are continuously monitoring all the developments around this Supply Chain Attack and will update our detections as necessary. As of now, we already have detection for REvil Ransomware, and the IoCs found during this supply chain attack.
IoCs:
- d55f983c994caa160ec63a59f6b4250fe67fb3e8c43a388aec60a4a6978e9f1e
- e2a24ab94f865caeacdf2c3ad015f31f23008ac6db8312c2cbfb32e4a5466ea2
- 8dd620d9aeb35960bb766458c8890ede987c33d239cf730f93fe49d90ae759dd




