Issue
Received the following installer setup file corruption error during installation of the Seqrite product
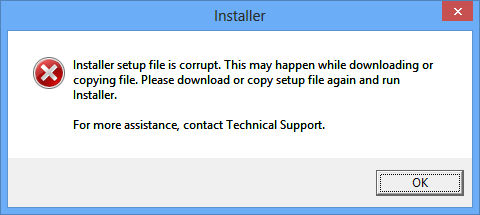
Reason
This error occurs due to missing security certificates in Windows OS. This error is encountered during installation of the Seqrite product.
Solutions
Steps to successfully update security certificate to install Seqrite products
Following are the solutions to resolve this issue.
Solution 1: Keep your computer connected to the Internet during the time of installation of the Seqrite product. If the installation detects any missing certificates, they would be installed automatically.
Solution 2: To install the certificate manually on a Windows computer without direct Internet connection, kindly follow these steps.
- Click here to download the latest trusted root certificate authority (DigiCert Trusted Root G4)
- To launch the certificate import wizard, double click on the .crt file that is downloaded in Step 1.

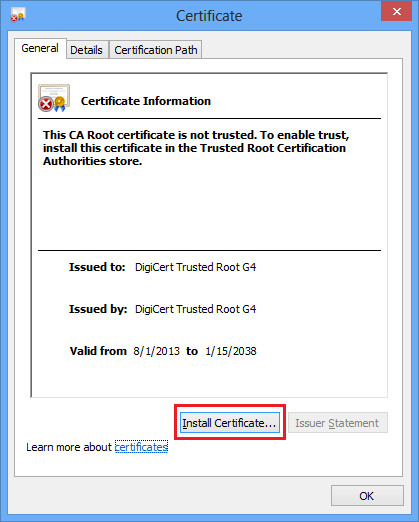
3. Click Install Certificate.
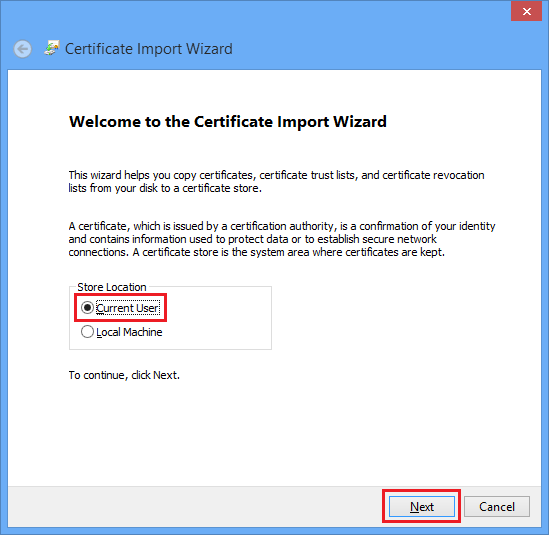
4. Select Current user and then click Next.
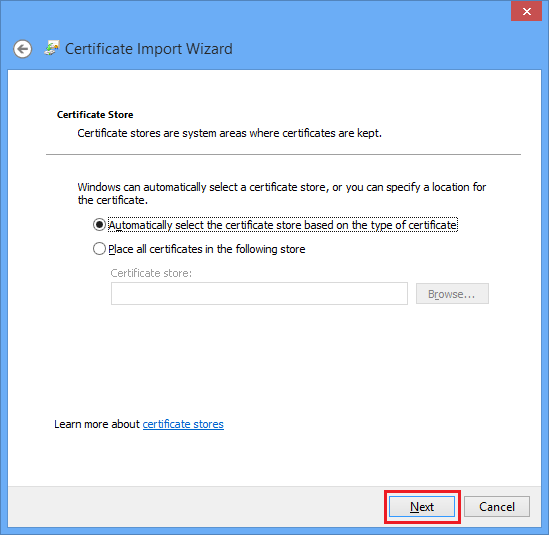
5. Select the Automatically select the certificate store based on the type of certificate Click Next.\
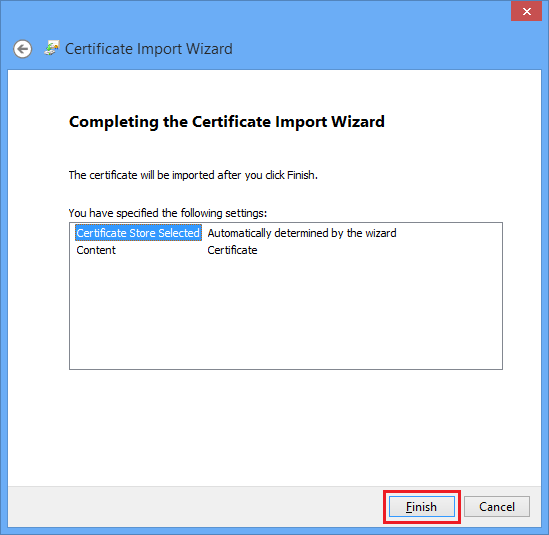
6. Click Finish.
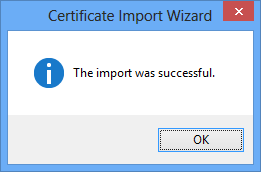
7. Click OK
After the certificate is imported successfully, run the Seqrite’s installer setup file again.
Recommendation
Always keep your Windows operating system up-to-date with the latest updates and security patches. Using the latest version of operating systems will help you avoid the risk of exploits targeting vulnerabilities of the operating systems.



