Introduction:
Originating in March 2023, Abyss Locker, a recently established ransomware operation, has swiftly targeted companies, transforming into a significant threat across various sectors, such as industrial control systems (ICS), enterprises, and public-sector organizations. It poses a significant threat to both Windows and Linux systems.
This escalation is tied to introducing a bespoke Linux encryptor, meticulously crafted to infiltrate VMware’s ESXi virtualized environments. This strategic move expands Abyss Locker’s reach and amplifies its impact across diverse sectors.
The Abyss ransomware, seemingly associated with the HelloKitty ransomware infrastructure, has undergone a notable modification in its encryption algorithm, shifting from AES to salsa_20. This adaptability highlights the group’s sophisticated tactics and poses an increased risk to cybersecurity.
Technical Analysis:
Firstly, it creates a Log file and then acts on the hardcoded list of services and processes.
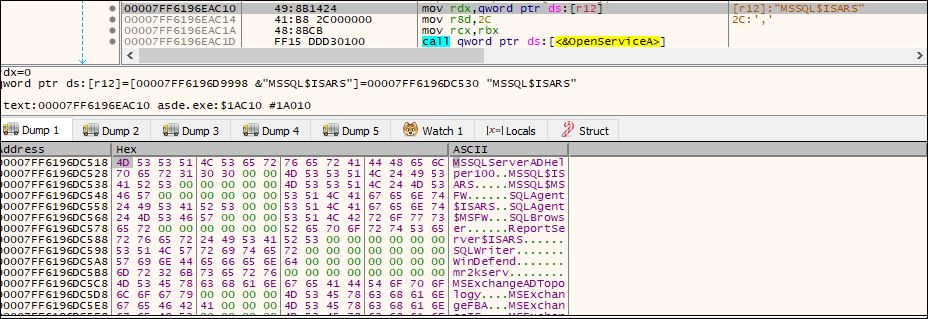
Fig: List of services to be terminated
It terminates the following services:
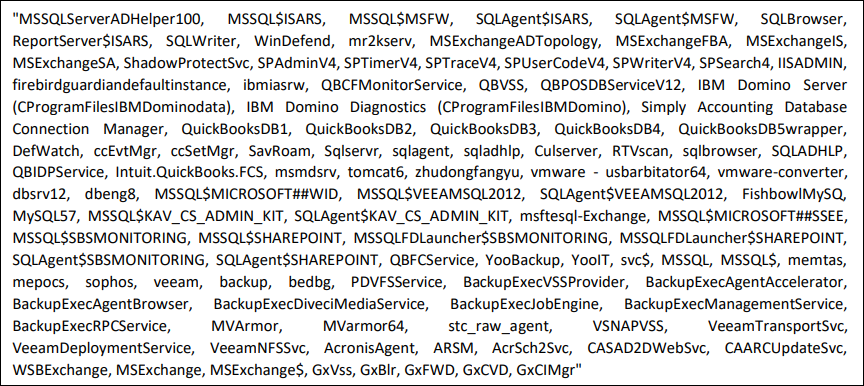
Fig: Services to be terminated
The ransomware ensures it terminates a specified list of processes before commencing its operations, thereby preventing any interference from these processes with accessing and encrypting files on the victim’s system.
The following processes are killed:
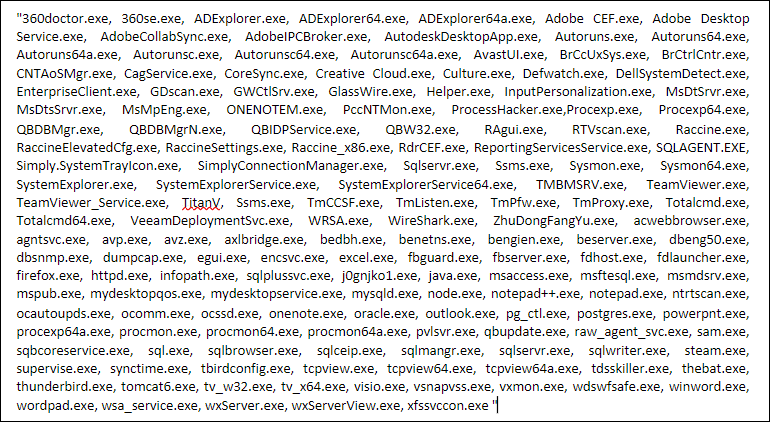
Fig: Processes to be killed
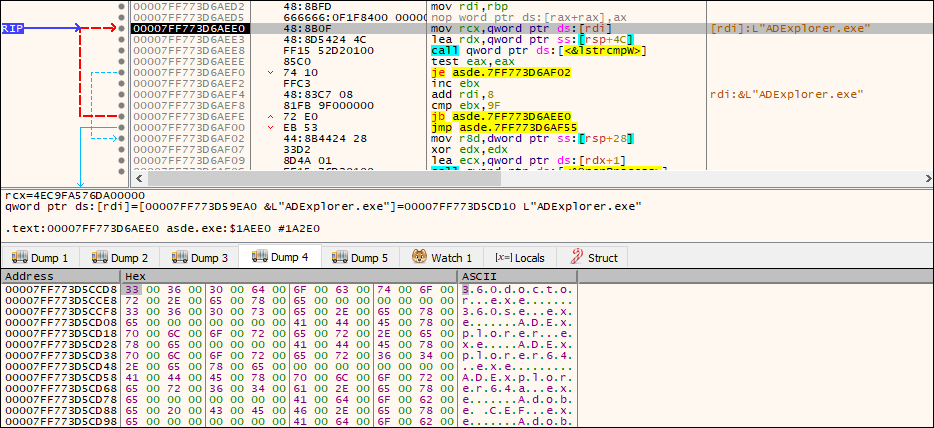
Fig: List process compared with the running process
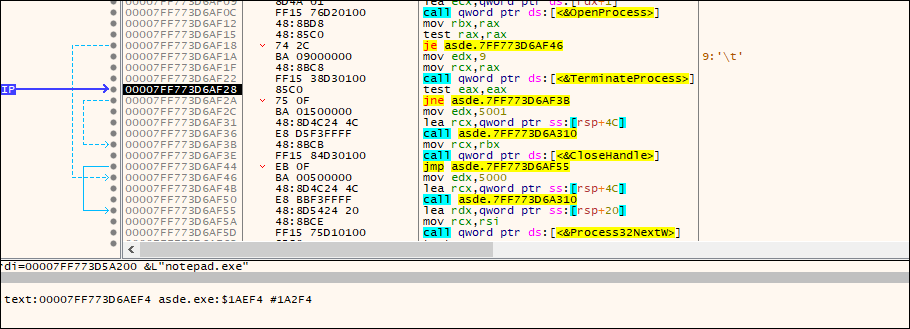
Fig: Process is ended with a terminate process API call
It uses the following commands to delete the shadow copy and disable the recovery boot options
- vssadmin.exe delete shadows /all /quiet
- wmic SHADOWCOPY DELETE
- bcdedit / set{ default } recoveryenabled No
- bcdedit / set{ default } bootstatuspolicy IgnoreAllFailures
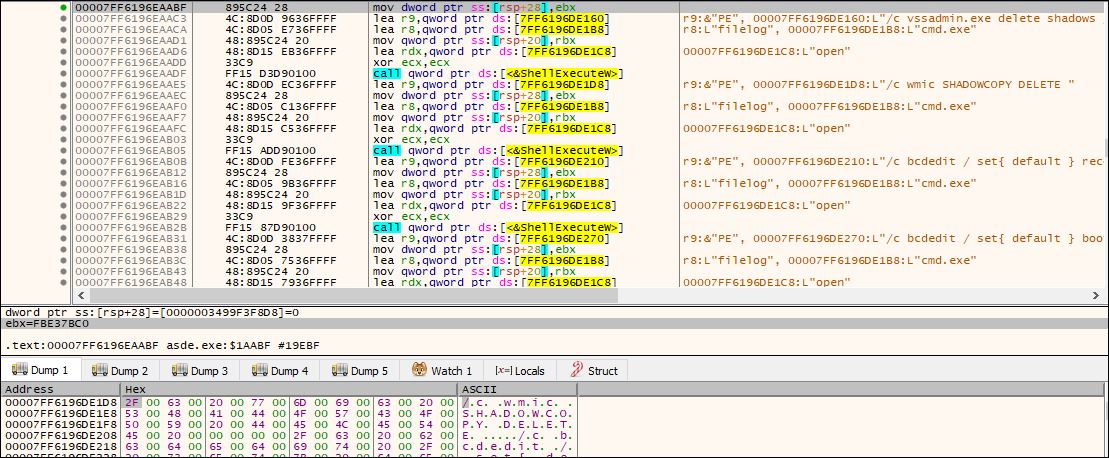
Fig: Use of CMD
Mutex Creation by Abyss:
It checks if there is any “DontWorryBeHappy” mutex present or not. Otherwise, it will create the mutex using the same name.
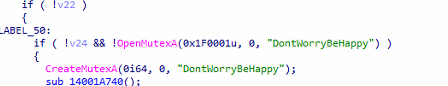
Fig: Creation of Mutex
Folders, files, and extension exclusion by Abyss:
The ransomware employs a thread routine to encrypt the victim’s data, concurrently conducting checks for excluded files and excluded extensions within the same thread. This dual functionality is evident in the encryption function illustrated in the figure below.
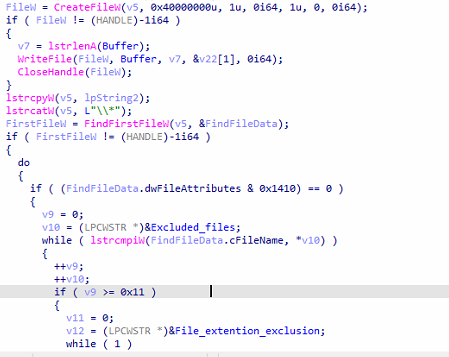
Fig: Traversing files and extensions for exclusion
Abyss ransomware has hard coded the folder, files, and extensions to be excluded at the time of encryption, as mentioned in the below figures:
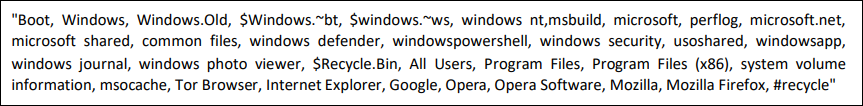
Fig: Excluded folder from the encryption routine

Fig: Excluded files from the encryption routine
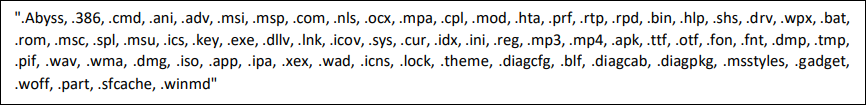
Fig: Excluded extension from the encryption routine
Encryption:
Encryption threads are created based on the number of existing processors, with a maximum limit of 64 threads.
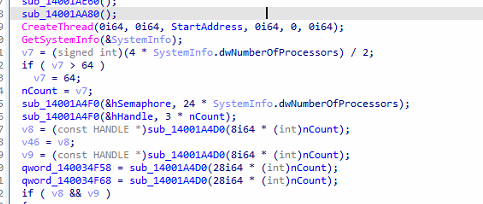
Fig: Encryption thread
It uses the salsa_20 encryption mechanism to encrypt the samples.
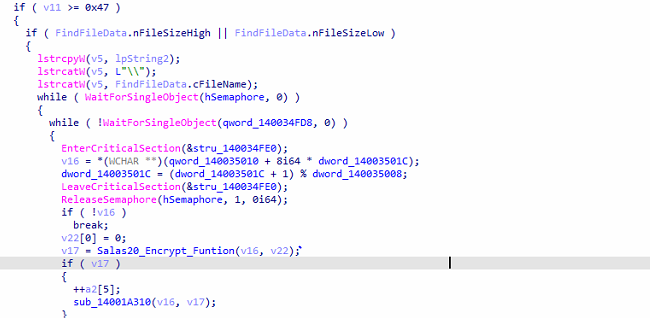
Fig: Use of Salsa_20 for encryption
Ransom Note:
It drops the Ransom Note on the Desktop, and each directory has the name “WhatHappened.txt.” It contains the Tor link to communicate with attackers.
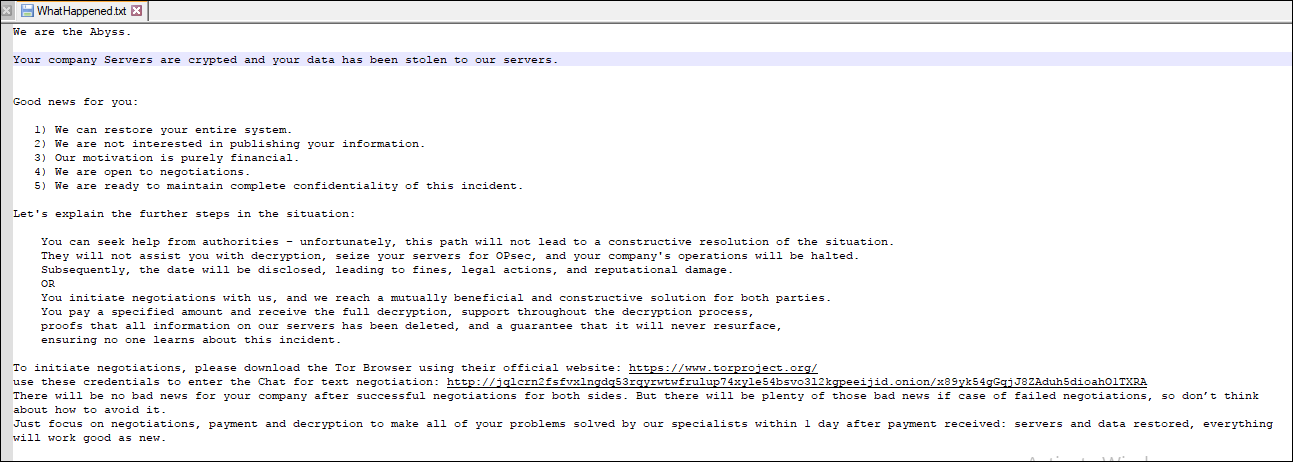
Fig: Ransom note
Fig: Appended. Abyss as extension
After encryption, it also set the desktop wallpaper as a ransom note.
Tips to prevent such kinds of attacks.
Regularly update your operating system, applications, and software to fix any known vulnerabilities that are often exploited by Attackers.
Use security software that can protect the system from the latest threats.
Be cautious with email attachments, especially from unknown senders. Avoid clicking on suspicious links or downloading files from untrusted sources.
Seqrite Protection:
Ransom.Rook.S32195182
Conclusion:
Emerging in July 2023, Abyss Locker ransomware traces its roots back to the HelloKitty ransomware source code, revealing a lineage that predates its official release. It uses the sala20 algorithm to encrypt files.
In line with typical ransomware behavior, Abyss Locker infiltrates corporate networks, engages in data exfiltration for extortion purposes, and encrypts devices, presenting a significant threat to systems running both Linux and Windows operating systems.
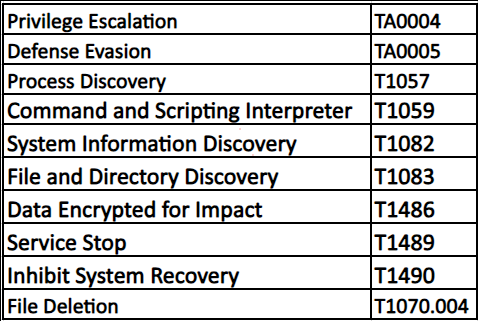
MITRE ATT&CK TTPs:
IOCs:
3B55904D3B37C810FC230B991A257939
2E4C626E67DF46B2A7258E73C04C4F73
B1095D0837DD11B5280FCB29B5A1BB84
18BAEDF43F4A68455E8D36B657AFF03C
D75E1C01C59B63D73F22E84A8A8819BF
6FF538DFD4B6A6FA796EA74EED50C80E
E93EDA81803040E70D64168C8A83228F
2442FF56720D1887CB46DD37ED732407
4704CD96029606D6F501826D41805486
0B53120151A20A46EDF3EF85B8AC450F
Author:
Soumen Burma
Co-author:
Vaibhav Krushna Billade




