What is Spear Phishing?
Spear phishing is a variation of a phishing scam wherein hackers send a targeted email to an individual which appears to be from a trusted source. The agenda of these mails like any other cyber fraud is to either gain access to the user’s system or obtain other classified information. Spear phishing is considered one of the most successful cyber-attack techniques because of the superior level of personalization done to attack users which makes it highly believable.
There is a minute difference between phishing and spear phishing. A phishing mail generally appears to come from large organizations such as your bank, email provider, social networking site, insurance company etc.
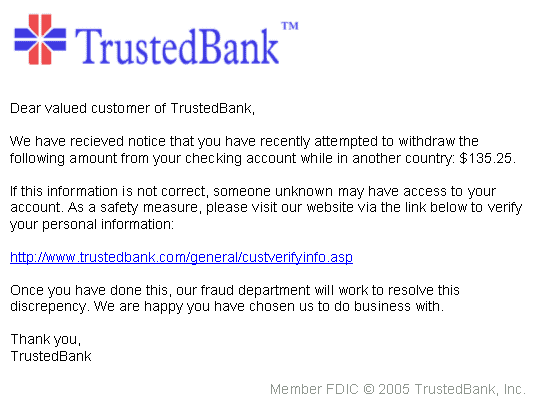
Image Credit: Andrew Levine (Wikimedia)
In spear phishing, users get meticulously personalized mails from a trusted source or a company you’re familiar with and interact quite often. This could be as scrupulous as an email from a friend, colleague or your boss asking you for access to classified information. Spear phishing hackers thrive on their knowledge about you which lets you lose your guard in most cases. This may include your email address, professional details and some other personal information gathered from various sources such as your last purchase, social media activity etc. At workplace, a possible example of spear phishing could be a mail from the CEO (on the corporate domain) which the hackers must have found out by simply looking up their name on the internet.
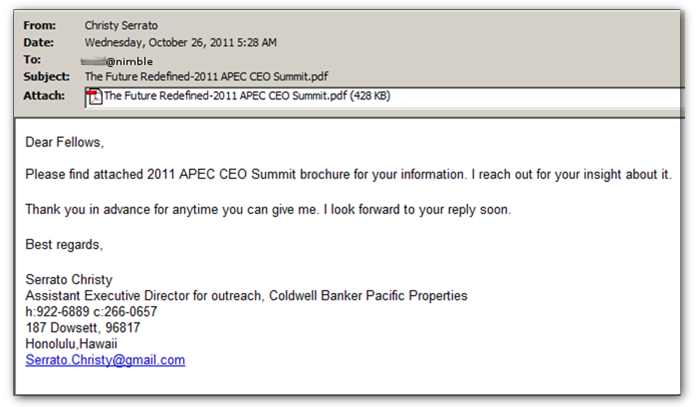
Image Credit: K7computing.com
How spear phishing can affect your business?
Your employees are your first line of defense in cybersecurity as they are usually the first point of attack as well. They could receive an email from a vendor or someone from within the organization who is familiar to them. This email is usually meticulously designed along with the company logo and other convincing details and motivates the user to click on a malicious link or attachment. Because the email might come from a trusted source your employee might end up clicking on the malicious link or opening the attachment. Once the link or attachment is clicked, a malware is executed on the system and the hackers can then establish their network and proceed with their attack.
Some of the most reputed names in the business like JP Morgan, Home Depot, and Target have lost millions of dollars along with crucial customer data in spear phishing attacks.
Defending your business from spear phishing attacks
You can reduce the risk of a spear phishing attack with a little help from your employees. If you thought ‘phishing’ is ‘fishing’ spelled wrong until you read this post then there is a good chance your employees don’t know anything about it either. Start off by educating them about the different kinds of security risks and the consequences of a phishing attack. Allocating some portion of your budgets in employee training programs for cybersecurity will go a long way in helping your company reduce the risks of these cyberattacks.
Seqrite’s enterprise security products are designed to facilitate world-class protection for every system within your enterprise with advanced features such as application control, file activity monitor and more. Seqrite rapidly defends and offers protection from such phishing attacks that originate from malicious codes over the Internet. It carefully thwarts these threats before they can enter the network and spread.




