Behind the screen, a delicate balance of trust and deception plays out. Honey traps, once the preserve of espionage, have now insidiously spread into the digital realm, capitalizing on human emotions. What starts as a harmless-looking chat or friend request can unexpectedly spiral into blackmail, extortion, or theft. The truth is, vulnerability knows no bounds – whether you’re an ordinary citizen or a high-profile target, you could be at risk. Let’s delve into the complex world of digital honey traps, understand their destructive power, and uncover vital strategies to safeguard ourselves. Attackers do break the firewall, but an insider threat bypasses it.

Who Gets Targeted?
- Government officers with access to classified documents
- Employees in IT, finance, defense, or research divisions
- Anyone with access credentials or decision-making power
Takeaway : If someone online gets close fast and wants details about your work or sends flirty messages too soon — that’s a red flag.
Fake romantic relationships are used to manipulate officials into breaching confidentiality, exploiting emotions rather than digital systems. Attackers gain unauthorized access through clever deception, luring victims into sharing sensitive data. This sophisticated social engineering tactic preys on human vulnerabilities, making it a potent threat. It’s catfishing with a malicious intent, targeting high-stakes individuals for data extraction. Emotional manipulation is the key to this clever attack.
Anatomy of the crime
- Targeting / victim profiling : Takeaway #1: Social Media is the First Door
Scammers often target individuals in authoritative positions with access to sensitive corporate or government data. They collect personal info like marital status and job profile to identify vulnerabilities. The primary vulnerability they exploit is emotional weakness, which can lead to further digital breaches. Social media is often the starting point for gathering this information.
- Initiation:
Scammers use social media platforms like Facebook, LinkedIn, and dating apps to establish initial contact with their victims. They trace the victim’s online footprint and create a connection, often shifting the conversation from public platforms to private ones like WhatsApp. As communication progresses, the tone of messages changes from professional to friendly and eventually to romantic, marking a significant escalation in the scammer’s approach.
Takeaway #2: Verify Before You Trust
- Gaining the trust: Takeaway #3: Flattery is the Oldest Trap
Scammers build trust with their victims through flattery, regular chats, and video calls, giving them unnecessary attention and care. They exchange photos, which are later used as leverage to threaten the victim if they try to expose the scammer. The scammer coerces the victim by threatening to damage their public image or spread defamatory content.
Enterprise Alert: A sudden behavioral shift in an employee — secrecy, emotional distraction, or odd online behavior — may hint at psychological compromise.

- Exploitation:
In the final stage of the scam, the scammer reveals their true intentions and asks the victim for confidential data, such as project details or passwords to encrypted workplace domains. This stolen information can pose a serious threat to national security and is often sold on the black market, leading to further exploitation and deeper security breaches.
- Threat to defamation: Takeaway #4: Silence Helps the Scammer
If the victim tries to expose the scam, the scammer misuses private data like photos, chats, and recordings to threaten public defamation. This threat coerces the victim into silence, preventing them from reporting the crime due to fear of reputational damage.
Enterprise Tip: Conduct employee awareness sessions focused on psychological manipulation and emotional engineering.

Psychological Manipulation
Takeaway #5: Cybersecurity is Emotional, Not Just Technical
- Love Bombing: intense attention and flattering messages.
- Induction of Fear: Threathen to leak the private images / chats unless the confidential data is presented .
Takeaway #6: Real Love Doesn’t Ask for Passwords
- Guilt-tripping: Push the victim into a state of guilt using expressions such as “ Dont you trust me anymore?”
Takeaway #7: The ‘Urgency’ Card Is a Red Flag
- Urgency: The urgent need of money is presented to gain the sympathy of the victim
- Isolation: Preventing the victim from being in contact with others and thus maintaining the identity of the scammer , not exposed.
Risk to Corporate and National Security
Takeaway #8: Corporate Security Starts With Personal Awareness
These scams can lead to severe consequences, including insider threats where employees leak confidential data, espionage by state-sponsored actors targeting government officials, and intellectual property loss that can compromise national security. Additionally, exposure of scandalous content can result in reputation damage, tarnishing brands and causing long-lasting harm.
Detection: Takeaway #9: Watch the Behavioral Shift
Suspicious behaviors include a sudden shift from a friendly to romantic tone, refusal to real-time video calls, controlling communication terms, sharing personal life details to evoke pity, and requesting huge financial support – all potential warning signs of a scam.

Prevention
Protect yourself by avoiding sharing personal info, verifying profile photos via reverse image search, and refraining from sending money or explicit content. Also, be cautious with unknown links and files, and enforce zero-trust access control.
Legal Horizon
Honey traps can lead to serious offenses like extortion, privacy violation, and transmission of obscene material. Victims can report such cases to cybercrime cells for action.
Proof in Action
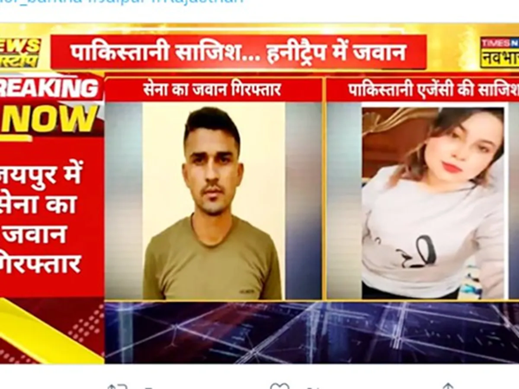
1. Indian Army Honey Trap Case (2023)
A 2023 case involved an Army Jawan arrested for leaking sensitive military information to a Pakistani intelligence operative posing as a woman on Facebook. The jawan was lured through romantic conversations and later blackmailed. Such incidents highlight the threat of honey traps to national security.
2. DRDO Scientist Arrested (2023)
Similarly, a senior DRDO scientist was honey-trapped by a foreign spy posing as a woman, leading to the sharing of classified defense research material. The interaction occurred via WhatsApp and social media, highlighting the risks of online espionage.

3. Pakistan ISI Honey Traps in Indian Navy (2019–2022)
Indian Navy personnel were arrested for being honey-trapped by ISI agents using fake female profiles on Facebook and WhatsApp. The agents gathered sensitive naval movement data through romantic exchanges.
Conclusion
Honey traps prey on emotions, not just systems. Stay vigilant and protect yourself from emotional manipulation. Real love doesn’t ask for passwords. Be cautious of strangers online and keep personal info private. Awareness is key to staying safe. Lock down your digital life.




