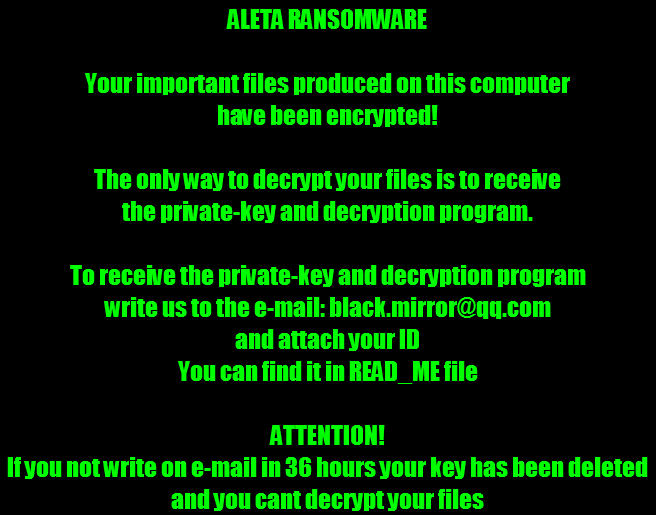
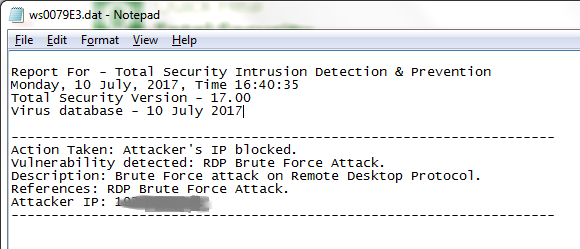
Quick Heal Security Labs has observed the entry of a new BTCWare ransomware (first observed at the beginning of 2017) variant called ‘Aleta’. This ransomware is called so because it appends a “.aleta” extension to files it encrypts in an infected computer. Although BTCWare ransomware variants do not seem to use any special techniques or exploits like WannaCry or NotPetya ransomware did, it uses RDP Brute-Force attacks to gain access to the infected system.
Read more on how RDP is exploited by attackers to spread ransomware and other malware.
BTCWare Aleta ransomware uses the AES256 encryption scheme. An interesting IOC (indicator of compromise) observed with the ransomware is the email ID associated with requesting the decryption key – black.mirror@qq.com. This email has been previously reported to have been associated with different variants of Amnesia & BTCWare ransomware. Spam emails with malicious attachments containing malicious script, doc, and executable files are used by this ransomware as its carrier.
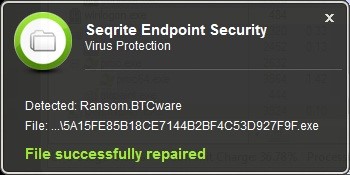
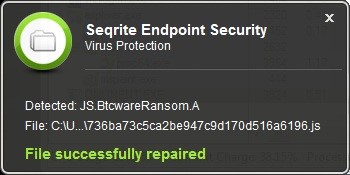
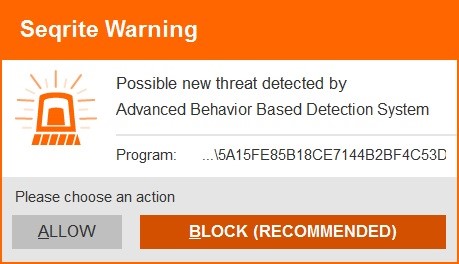
Seqrite Endpoint Protection against BTCWare (Aleta) Ransomware
Stay away from ransomware with these security tips
- Back up your files on a regular basis. A ransomware goes after your files when it infects your computer. If you have a backup of all your important files, there is no reason why you should give in to the ransomware’s demands. Remember to disconnect the Internet while you are backing up on an external hard drive. Unplug the drive before you go online again. Several free and paid Cloud backup services available on the market that can take data backup periodically.
- Provide Read/Write privileges to network shares only when required. Try not to keep open shares as they are likely to fall prey to encryption if there is a ransomware infection.
- Use strong login credentials for both the user and administrator. Weak credentials can be easily brute forced to gain system access.
- Use a security solution that gives multilayered protection against infected emails, malicious websites, and stop infections that can spread through USB drives. Keep the software up-to-date.
- Apply recommended security updates for your computer’s Operating System and all other programs such as Adobe, Java, Internet Browsers, etc.
- Do not click on links or download attachments that arrive in emails from unwanted or unexpected sources. Even if such emails seem to be from a known source, it is better to call up the sender and verify them first.
Acknowledgement
Subject Matter Expert
– Shantanu Vichare | Quick Heal Security Labs




