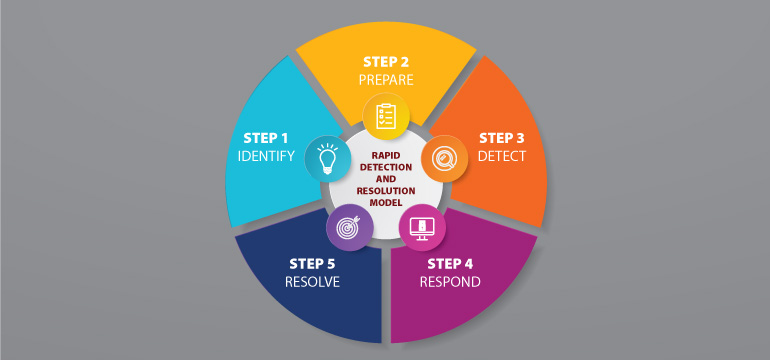
With the incidents of cybercrime rising at an enormous rate, especially targeted attacks on organizations, many companies now have a cybersecurity incident response plan in place.
However, a major reason these organizations still fail to respond effectively to a cybersecurity incident is because, in spite of having an incident response plan, it is never frequently tested nor consistently applied across the organization.
Given the ever evolving nature of threat landscape, it is extremely important to test the response plan on a frequent basis to check for loopholes in the process. Failure to upgrade this plan, often leaves organizations vulnerable and less prepared to handle the cybersecurity incident response process in the wake of a sudden cyber-attack.
The need is to test the plan regularly by making effective investments in skilled resources, technologies and processes, so that they can work in sync with each other when the need arises.
Few things that can help organizations test and implement an effective cybersecurity incident response plan include:
Automation
Investing in automation can be a good and cost effective option in this regard and can help organizations save up on millions of dollars that may otherwise be compromised in the event of a breach.
Automation here refers to replacing or augmenting human intervention with artificial intelligence and machine learning, to enable easy & efficient identification of breaches and exploits, for necessary and timely actions to be taken.
Studies indicate that organizations that leverage automation extensively across their organization are in a better position to detect, prevent and respond to cyber-attacks and breaches than organizations that don’t.
Skilled Resources
The lack of enough skilled resources for handling cyber-attacks and managing incident response plan, comes as a big hurdle for organizations to achieve cyber resilience. The major problem lies not just in hiring resources but mostly in retaining cybersecurity professionals.
On the other hand, deploying too many processes and technologies at once to achieve cyber resilience, can make the overall process complex for cybersecurity personnel to understand and reduce the effectiveness of the plan.
Thus, what organizations need, is to have a perfect collaboration of technology, resources and processes, in order to effectively test and implement a robust cybersecurity incident response plan.