In October 2016, AVLab protection test against ransomware threats gave a 100% effectiveness score to Seqrite Endpoint Security (EPS) Enterprise Suite Edition. 28 malicious software files of crypto-ransomware were used to test the effectiveness of the solution in terms of behavioral detection rate and comprehensive real-time protection against ransomware infections.
Crypto-ransomware is considered to be one of the nastiest threats that is spreading like wildfire from offices to homes and has recently shifted its focus to small and medium businesses targeting more Windows file types than ever.
The history of ransomware and the rise of crypto-ransomware
Ransomware has a surprisingly long history and has been the most potent cyber threat since 2005. It belongs to a type of malicious software that prevents or restricts users from accessing an operating system. Over the years, two distinct varieties of ransomware have remained consistent: crypto and locker based.
Crypto-ransomware is ransomware variants that encrypts files and folders, hard drives etc. on the victim’s machine using strong cryptography. The user is then notified that their files were encrypted and demands ransom to decrypt them. Attempts to recover files or declining to pay have often resulted in complete loss of information. The Windows-only ransomware has held rapt the attention of organizations worldwide since its formal appearance in September 2013. The other ransomware variant Locker-ransomware only locks users out of their devices and targets Android devices.
Why crypto-ransomware causes problem to SOHOs and SMEs?

Unlike traditional malware threats, crypto-ransomware is particularly nasty because users are in danger of losing their personal files forever. Cybercriminals have recently shifted their focus on small and medium enterprises. The objective is obvious-Money. Confidential and sensitive company information is too valuable to be written off and most organizations do not have a well-defined security infrastructure in place to prevent the loss and theft of company data. SMEs are unprepared for advanced attacks and that makes the task of cybercriminals easy as some percent of the victims will pay a ransom anyway.
AVLab protection test against ransomware threats
The objective of AVLab test was to indicate the best solution for the real-time protection against crypto-ransomware to home users and small and medium businesses. More than 28 malicious software files of crypto- ransomware were collected in order to test the protection effectiveness of most popular antivirus applications. The Lab prepared an image of Windows 10 Professional x64 with the latest updates dated the day before the test. This way, all products were tested in the identical test environment and had access to the Internet.
Seqrite EPS Enterprise Suite Edition was amongst the 17 security software applications tested under the category of small and medium businesses. The results of tested applications is given below:
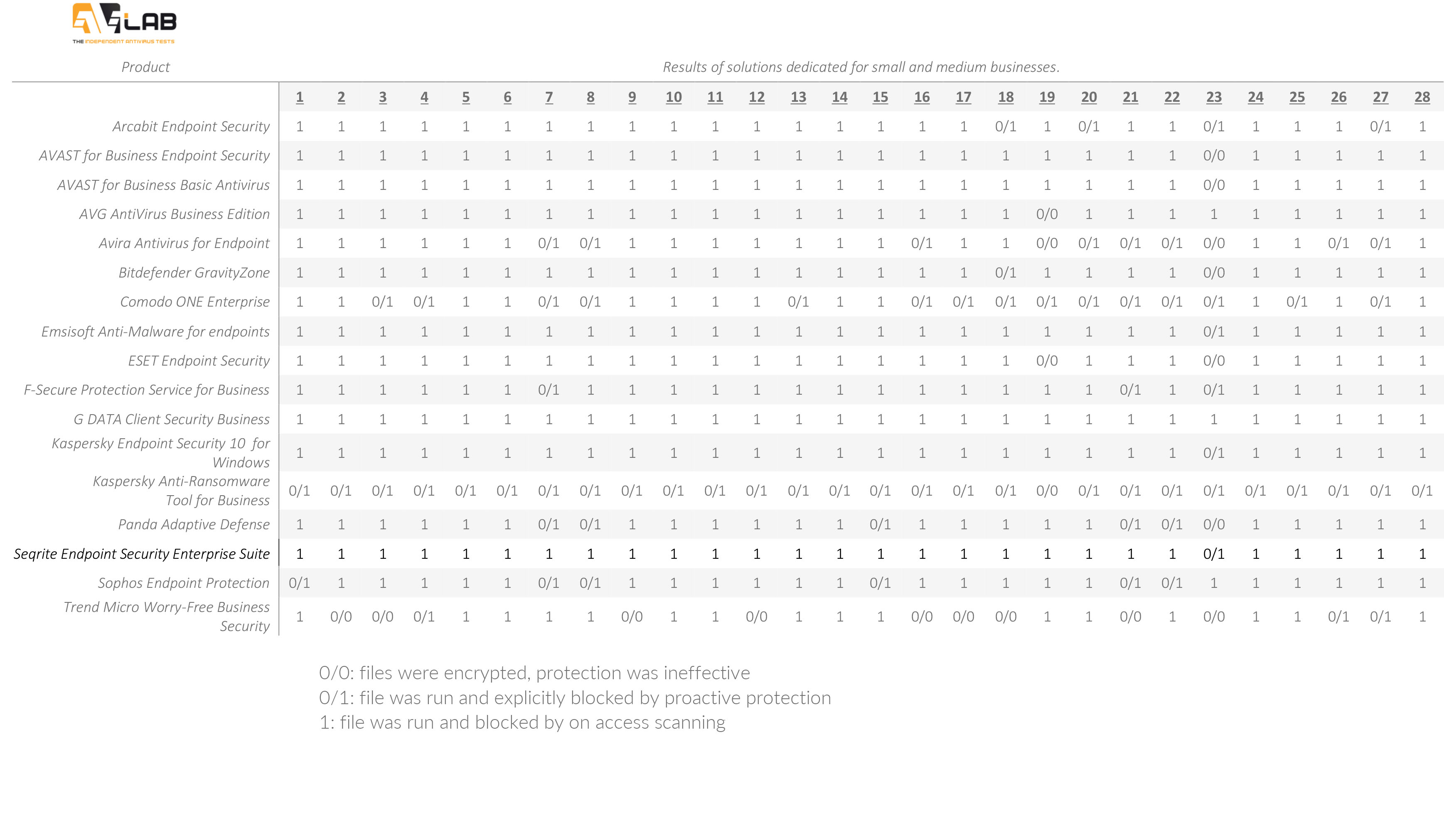
Seqrite EPS Enterprise Suite Edition was 100% effective in detecting and blocking malicious files of crypto-ransomware thus earning AVLab BEST+++ Award. Download the full AVLab report here.
About Seqrite EPS Enterprise Suite:
Enterprise Suite provides advanced endpoint security and data protection bundled in one solution. A combination of Enterprise Total and Data Loss Prevention (DLP), the solution comes with new and enhanced features such as Patch Management, Advanced Device Control and more. Enterprise Suite not only delivers and fixes security vulnerabilities but also combines malware, device, browsing, phishing and data protection-all in one solution.
For more information on Enterprise Suite Edition and anti-ransomware features visit https://bit.ly/2bH0VEh




