The decryption of CrySiS/XTBL Ransomware is now possible thanks to the recent release of its master decryption keys needed to recover the files encrypted by the ransomware. While we couldn’t guess the apparent reason behind the release, we have used this opportunity to help those who were affected by the ransomware.
The Quick Heal Threat Research Labs has developed a decryption tool for CrySiS/XTBL (known as QH-Ransom-Decryptor) with the published keys. This tool comes for free and can be downloaded from the link mentioned below:
Download link:
Seqrite Ransom Decryptor Tool
As of now, the decryption tool works on files affected by the below-listed ransomware families:
1. Troldesh Ransomware [.xtbl]
2. Crysis Ransomware [.CrySiS]
3. Cryptxxx Ransomware [.crypt]
4. Ninja Ransomware [@aol.com$.777]
5. Apocalypse Ransomware [.encrypted]
6. Nemucod Ransomware [.crypted]
7. ODC Ransomware [.odcodc]
8. LeChiffre Ransomware [.LeChiffre]
9. Globe1 Ransomware [.hnyear]
10. Globe2 Ransomware [.blt]
11. Globe3 Ransomware [.decrypt2017]
12. DeriaLock Ransomware [.deria]
13. Opentoyou Ransomware [.-opentoyou@india.com]
14. Globe3 Ransomware [.globe & .happydayzz]
15. Troldesh Ransomware [.dharma]
16. Troldesh Ransomware [.wallet]
17. Troldesh Ransomware [.onion]
Note:
A Crysis/XTBL encryption can be identified from the below pattern of encrypted file extension:
- File name.<extension>.<id-number>.<email>.xtbl/.CrySiS)
Example – “available.txt.id-340D4C04.{green_ray@india.com}.xtbl”
Instructions to use the QH-Ransom-Decryptor:
- Click on the Seqrite Ransom Decryptor Tool link and save the zip file on the system having the encrypted files. Extract the file.
- Right click on the extracted file and Run it as ‘Administrator’ to view the Decryption Window.
- Press Y to start the scan. The decryption tool will automatically scan the entire system for supported encrypted files. When an encrypted file is found, the tool will decrypt the file in its respective folder while keeping a copy of the encrypted file at the same time.
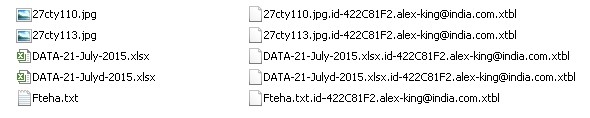
Fig1. Decrypted files will be present in the same folder along with their encrypted copies.
- After the scanning is complete, the decryption tool will show the final status displaying the number of encrypted files found and how many were successfully decrypted. The detailed information about the decryption status of each file can be obtained from the ‘Decryption.log’ generated in the same folder of the tool.
- Thereafter, you can open the decrypted files and verify if they are accessible/readable again.
If you come across any difficulty in using the decryption tool, kindly give us a call on 1800-212-7377 or visit our Support Center for further assistance.
Updated as of 7th March 2017.




