DDoS Attacks on Rise….
As per recent cyber security reports, there has been a rise in DDoS attacks in Q1 2019, with number of attacks lasting more than an hour. Many researchers believe that cyber attackers who had been doing DDoS attacks for monetary gain, had focused their attention on income sources like crypto mining. The decrease in crypto mining activity has once again led to increase in DDoS attacks.
What are DoS and DDoS Attacks?
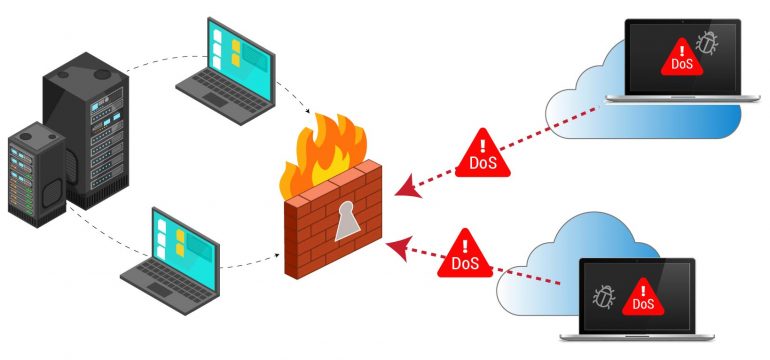
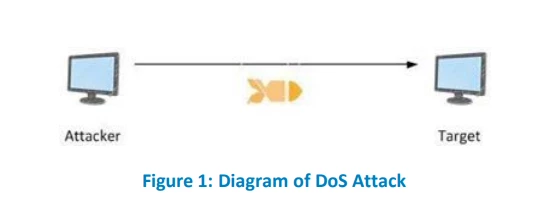
A denial of service (DoS) attack is a strategy in which unknown zombie aims to prevent others from accessing web server, web application or cloud service, by flooding them with service requests from single origin, rendering target internet service inaccessible.
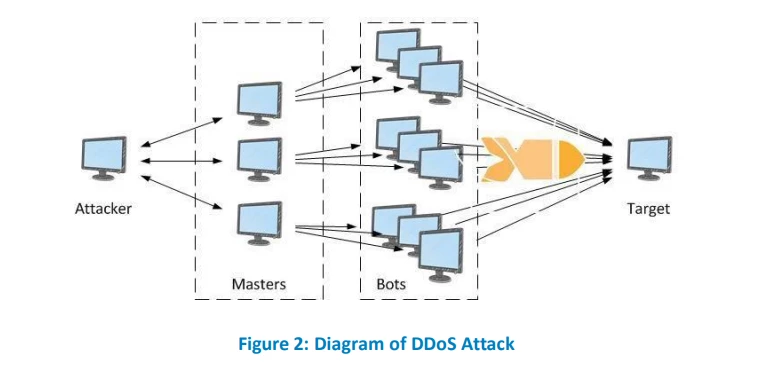
On the other hand, distributed denial of service (DDoS) attack is a DoS attack from multiple sources on different networks disrupting any service like mobile application API’s, web pages, email services or DNS services.
Why DDoS Attacks?
Attacker might be doing these attacks for fun, to slow down competitor business, public votes, monetary gains or other income sources like crypto mining etc. DDoS attacks can even cover up for stealing valuable data from victims.
Types of DDoS Attacks?
Basic DDoS attacks include UDP Flood, SYN Flood, ICMP (Ping) flood, DHCP starvation attack, Ping of Death attack.
UDP Flood
Flooding random ports on remote host with UDP packets. Victim continuously check for application listening on that port when no application found, victim replies with ICMP destination unreachable repeatedly. Hence resulting in victim resources exhaustion, leading to inaccessibility.
SYN Flood
Flooding SYN requests or even spoofing SYN requests for which no ACK will be received. Victim waits for acknowledgement from flooder for each request binding resources until new connection can be made then resulting in denial of service.
ICMP (PING) Flood
Flooding ICMP Echo Request packets without waiting for replies. Victim keep on generating ICMP Reply Packets for each request leading to exhaustion of both incoming and outgoing bandwidth, leading to system slowdown.
Ping of Death Attack
Flooding of malformed or malicious pings. Victim ends up with IP packet exceeding 65,535 bytes when reassembled. This results in overflow of memory buffers allocated for packet ending up in denial of service for legitimate packets.
DHCP Starvation attack
Flooding DHCP Discover Packets to DHCP servers with intent of exhausting all IP addresses that can be allocated by DHCP server, resulting in denial of service for legitimate network users.
Business Impact of DDoS attacks…
Generating DDoS attacks is not much expensive but then it can have huge impact on business. Imagine a service down for 24 hours; in addition to financial loss, company’s reputation is also at risk. In 2015, BBC’s server was flooded with traffic of 602 Gbps leading to collapse of BBC’s sites and content services provided by BBC’s server [1][2]. There are many more countless examples. IT administrator contact 3rd Party vendor to resolve this issue. Delay in controlling DDoS attack circumstances may lead competitor to quickly step in.
So, isn’t protection against DDoS attacks better than cure?
Day by day internet speeds are increasing, our application server could be attacked by hackers with high volume connections, which results in denial of service scenarios. We need to protect them from DoS and DDoS attack. So, what’s the solution?
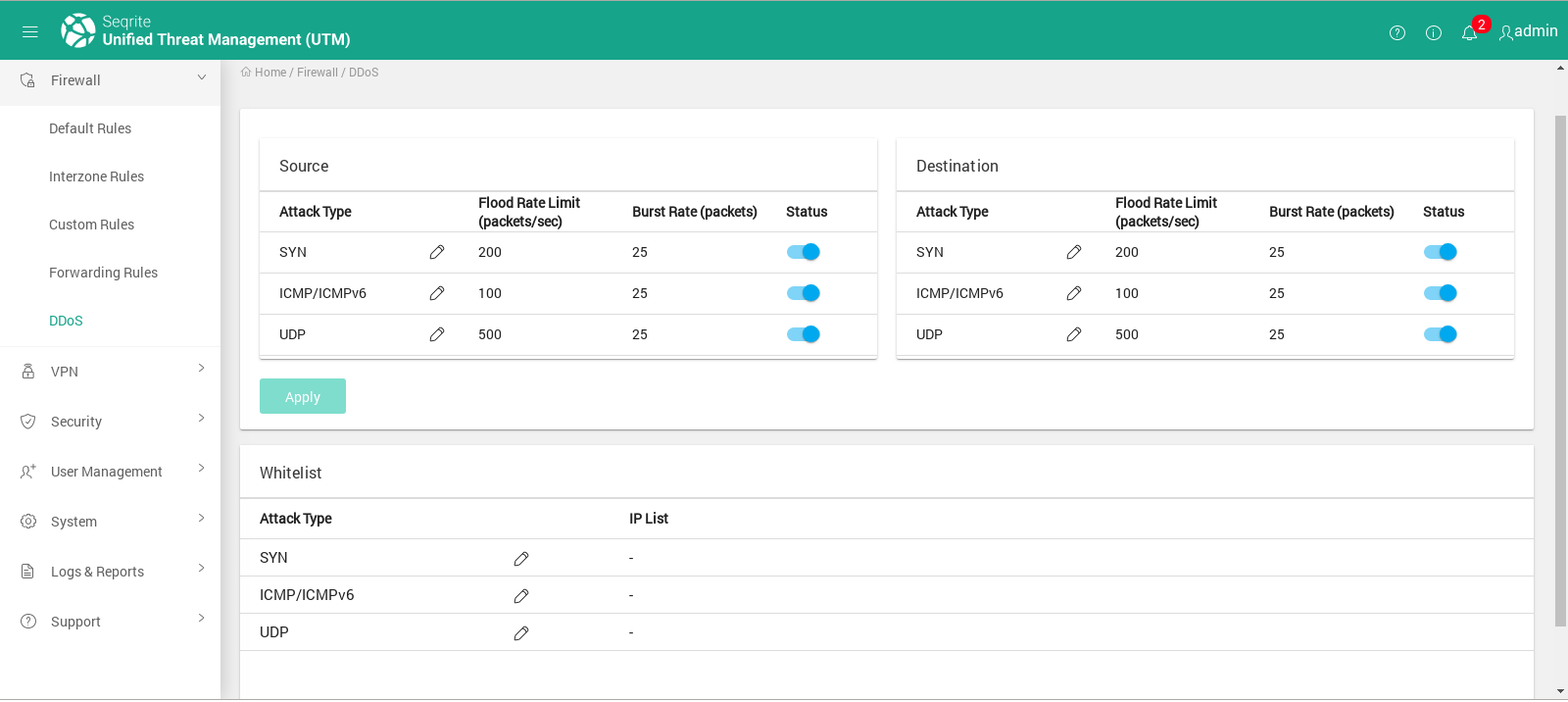
Protect your application servers with Seqrite UTM, a gateway security solution.
SEQRITE UTM (Unified Threat Management) has excellent Gateway Security Solution against DDoS attacks. It provides protection against DoS/DDoS attacks for SYN Flood, ICMP/ICMPv6 Flood and UDP Flood.
References
1.https://www.csoonline.com/article/3020292/cyber-attacks-espionage/ddos-attack-on-bbc-may-have-been-biggest-in-history.html