Estimated reading time: 3 minutes
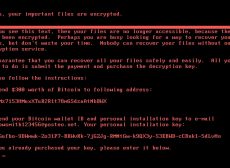
Malware, including ransomware, viruses, trojans are a grave threat to organizations. Out of these, ransomware is unique. Not only does it steal and corrupt data, but it also locks out the users from their own systems so that taking...