Cryptocurrency has become a famous and valuable digital asset. One of the ways to earn cryptocurrencies is to mine them. New coins are generated and brought into the market through the process of mining. Mining of cryptocurrency is a resource-intensive task but mining them on mobile devices is still a question because they have low computing power.
Quick Heal Security Labs came across apps on the Google Play Store that claimed to mine cryptocurrencies using Android devices. For obvious reasons, we found the occurrence of these apps suspicious because it’s nearly impossible to mine digital coins like Bitcoin and Ethereum using any mobile device.
Let’s take an example of Bitcoin currency which is the most valuable digital currency right now. Since November 2017, its value has jumped 142.11% according to coinbase.com.
Now, everybody is looking for various ways to get those coins to make money. On Google Play Store, there are many apps which promise to give away FREE cryptocurrency through mining on their Android phone. But in reality, these apps are fake and do nothing like they claim. Taking advantage of this opportunity, malware authors have uploaded fake cryptocurrency mining apps on the Play Store to lure users into downloading these apps to increase their download count and misguide users to give them a 5-star rating on the Play Store for free Satoshi. (A Satoshi is the smallest fraction of a Bitcoin).
Analysis of Bitcoin Miner Robot
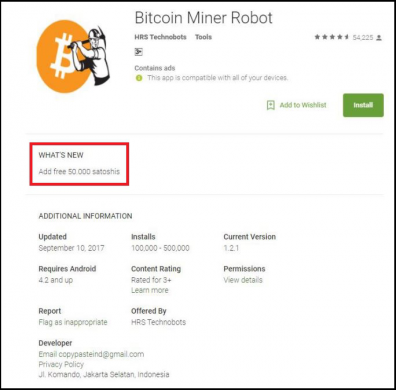
AppName: Bitcoin Miner Robot
Package name: hcss.killua.bitminerrobot.bitcoinminerrobot
MD5: 006be02ef2ca3f2305a23c201570cd03
Size: 2646 KB
What does it do?
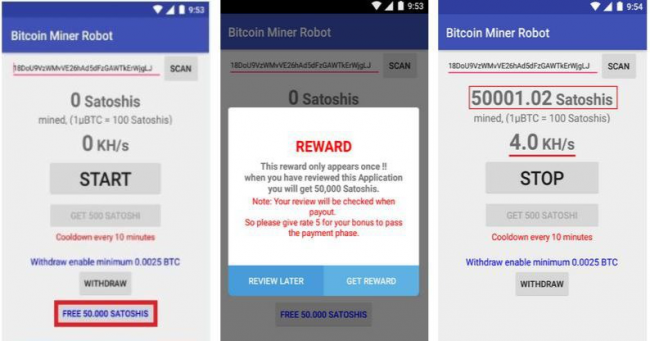
1) Once the user clicks on the button FREE 50,000 SATOSHIS, the app asks for a 5-star rating and then shows a credit of 50000 Satoshi on the app’s screen. This happens even if the user doesn’t give any rating.
2) To start the mining process, the user has to click on START button. After every 10 minutes, a GET 500 SATOSHI button gets activated and the user can save generated Satoshi on the device itself but they must watch a video/interstitial ad when the device is connected to the Internet. Ads are present at both start and stop event of mining.
After opening the app, it shows its main screen as shown in fig 3.
The following code shows how the app generates fake values of Satoshi and hash power using randomKH() function.

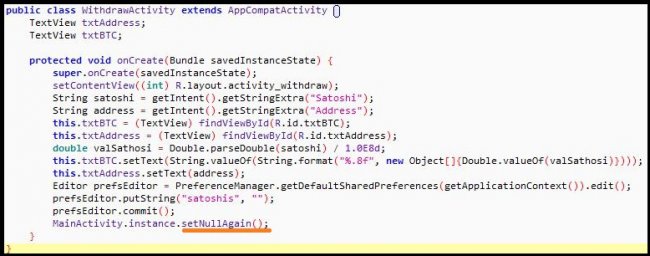
The following code belongs to a withdraw activity that is launched while withdrawing mined Satoshi amount. As we can clearly see that the app is just showing the Satoshi value and wallet address to the user and at last setting the Satoshi value to 0 by calling setNullAgain() method to misguide the user that the amount has been sent to provided wallet address which in reality is never received by the user.
Interesting facts about the Bitcoin Miner Robot
- The app can scan a digital wallet barcode address to pretend it’s genuine, show fake calculation value, increase the Satoshi value to fool the user into believing that it’s doing something. But, in the background, it does nothing except programmatically changing text values.
- The app continues to mine even when there is no Internet connectivity – this seems fake because a mining process requires an active Internet connection.
3) While running the app on the device, it does not heat up – this seems fishy because mining is a resource-intensive task which clearly heats up the device.
4) Here, the app developer’s aim behind publishing the app is to generate revenue by serving the user with too many interstitial ads that bring more revenue compared to banners ads. The app also shows video ads which often bring even more revenue to the developer. Furthermore, interstitial and video ads consume more mobile data.
The same developer has published a similar app on Google Play Store for Ethereum Cryptocurrency.
Ethereum is also a popular cryptocurrency after Bitcoin.
Indicator of compromise
AppName: ETH Miner Robot
Package name: ethereumminerrobot.eminerrobot.emr.ethereumminerrobot
MD5: 09315ac5b86fed423ed734b26badf9e9
Size: 2752 KB
Quick Heal Detection
Quick Heal successfully detects both these fake apps as Android.Fakeapp.Kc877 and Android.Fakeapp.Kc876
How to stay safe from fake mobile apps
- Check an app’s description before you download it.
- Check the app developer’s name and their website. If the name sounds strange or odd, you have reasons to suspect it.
- Go through the reviews and ratings of the app. But, note that, these can be fake too.
- Avoid downloading apps from third-party app stores.
- Use a reliable mobile antivirus that can prevent fake and malicious apps from getting installed on your phone.
Subject Matter Expert
Rohit Bhange| Quick Heal Security Labs




