Cases of the “Lime ransomware” have been recently reported to Quick Heal Security Labs. Our research team has analyzed these cases deeply and found some useful information. This post shares this information to help users stay safe from ransomware attacks.
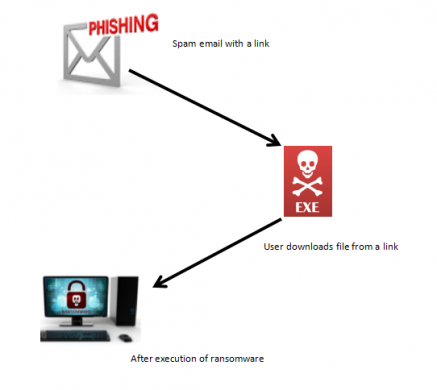
‘Lime’ is a newly discovered .net ransomware; it is also known as the ‘BigEyes’ ransomware. It uses two major ways to infect user’s systems, either spam emails or malicious downloads.
Ransomware usually comes into the system without the user’s knowledge through online activities like software bundling, spam email attachments, infected links, malvertising, by visiting unknown sites, RDP (Remote desktop protocol) and exploit kits.
Infection vector
Technical analysis
Encryption Process: in-depth description
Lime is a ransomware that encrypts your files and demands Bitcoin as a ransom to get your files restored. Files are locked with the AES-256 encryption algorithm. The Lime ransomware encrypts your files and appends the “.Lime” extension.
After encryption, the Lime ransomware drops a ransom note Fig 2.
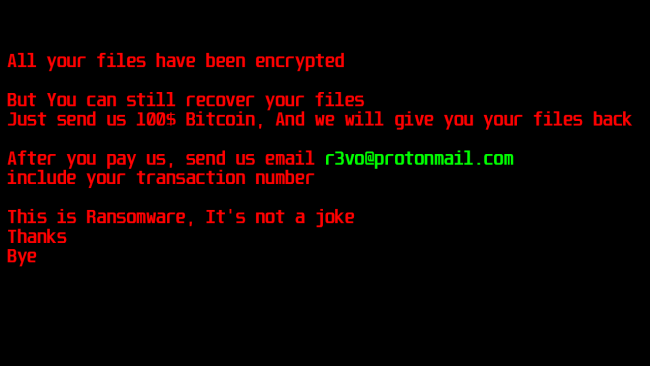
The following e-mail address is used to contact the malware author to decrypt the encrypted files by paying them:
“r3vo@protonmail-com”
Key generation
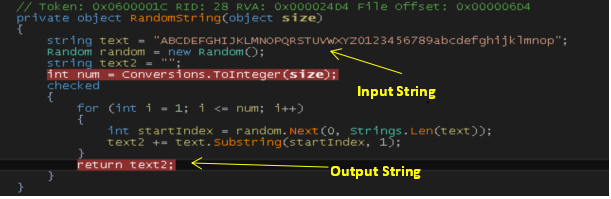
When Lime is first launched, it will call RandomString() function which will attempt to generate an AES key. It generates 50 bytes array from input string using a random index with the use of random() function to fetch one character and stores into output string as shown in Fig 3.
It calculates md5 of generated output string using Computehash() and then it will copy the result into the result array. It will use this result array as an AES key to encrypt the files present on the system.
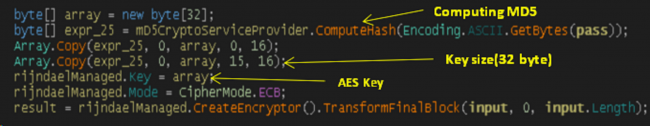
It drops output string at path “C:\Microsoft” by name “hash”. As we know that AES is symmetric algorithm so the key used for encryption and decryption will be the same. So, the malware author uses this hash file’s MD5 to decrypt the victim’s files when victim pays ransom amount to him.
Lime ransomware encrypts files on specific folder paths using AES-256 in ECB mode to encrypt files. Paths are as per given below:
- My Music
- My Pictures
- My Videos
- Desktop
- UserProfile
Components used in AES
Different modes used in AES:- ECB, CBC, CFB, OFB, CTR.
Key:- AES-128(16 Bytes), AES-192(24 Bytes), AES-256(32 Bytes)
IV:- Initialization vector to use for encryption or decryption
It encrypts files using AES-256 (32-byte key length) in ECB (Electronic Code Book) mode. In ECB mode, it doesn’t require IV (Initialization vector) for the encryption or decryption process.
For all other modes, it uses IV (Initialization vector). IV is optional and when IV is not present then it will be given a default value of all zeroes.
Modification in file extension
List of extensions of files which get encrypted by Lime ransomware:
.c, .cpp, .py, .ini, .hiv, .avi, .bmp, .log, .pdf, .zip, .bak, .rtf, .png, .wsf, .wsc, .ws, .vsw, .vst, .vss, .vsmac, .ros, .vbs, .vbe, .vb, .url, .tmp, .shs, .shb, .sct, .scr, .scf, .reg, .pst, .prg, .pif, .pcd, .ops, .mst, .msp, .msi, .msc, .mdz, .mdw, .mdt, .mde, .mdb, .mda, .maw, .mav, .mau, .mat, .mas, .mar, .maq, .mam, .mag, .maf, .mad, .lnk, .ksh, .jse, .js, .its, .isp, .ins, .inf, .hlp, .fxp, .exe, .csh, .crt, .cpl, .com, .cmd, .chm, .cer, .bat, .pdf, .pot, .xlt, .pps, .xlw, .dot, .rtf, .ppt, .xls, .doc, .xml, .htm, .html, .hta, .app, .asp
The extension ‘.lime’ is placed as a secondary extension, without altering the original names and its extension.
Example:
Original file name : mydemo.cpp
After encryption : mydemo.cpp.Lime
And yes! Recovery of Encrypted File is possible
We can decrypt all files which are encrypted by “Lime Ransomware”. The key is 32 bytes which is generated from MD5 of “hash” file which is dropped at “C:\Microsoft” location of victim’s mchine. So, the key is different for different victim.
To decrypt files, AES-256 is used in the ECB mode and key for that will be generated as given below,
If MD5 of hash file is dropped on the victim’s machine: “05FF78F91FE2D008018A2F53792C0C28”
Key generation from MD5
Take 15 bytes from MD5 + Take 16 bytes from MD5 + Append zero=32 bytes key
Key = 05FF78F91FE2D008018A2F53792C0C + 05FF78F91FE2D008018A2F53792C0C28 + 00
Key = 05FF78F91FE2D008018A2F53792C0C05FF78F91FE2D008018A2F53792C0C2800
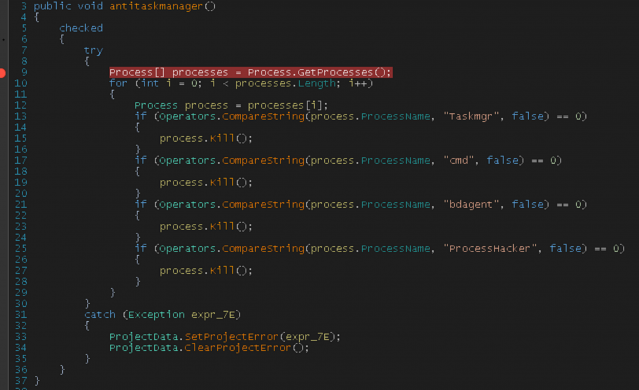
Process killing
It checks the presence for specific processes and try to kill these processes. These process names are as follows:
- Taskmgr
- Cmd
- Bdagent
- ProcessHacker
Indicators of compromise
- MD5: E1B571F1AD5266156C8233FA0D2BA1E0
- C:\Microsoft\hash
- The extension “.Lime” is placed as a secondary extension, without altering the original names and its extension.
Seqrite protects its users from the Lime ransomware
Seqrite EPS detected and successfully eliminated this threat using Static Detection and Behavior-based Detection.
- Malicious files are detected as “Ransom.Lime.S1809905”
How to stay away from ransomware
- Use a multi-layered antivirus in your system which will protect you from real-time threats.
- Keep your antivirus up-to-date.
- Update your Operating System regularly as critical patches are released almost every day.
- Keep your software up-to-date. Older and outdated versions of software have Vulnerabilities which are almost always exploited by attackers to infect a system with ransomware and other malware.
- Never directly connect remote systems to the Internet. Always use a VPN (Virtual Remote Network) to access a network remotely.
- Do not click on links or download attachments in emails received from unexpected or unknown sources.
- Take regular data backup and keep it in a secure location.
- Do not open suspicious email attachments.
Subject Matter Experts
Prashant Indalkar, Pandurang Terkar | Quick Heal Security Labs




