Dridex is a banking malware which uses macros to spread on windows systems. Spam email attachments are utilized to spread this infection. Banking malware are generally key loggers. They trick users into opening the attachment; it then records the keystrokes on user’s computer and uses them for their own benefit. Recently spotted Dridex engagement contained PDF files as the carrier. Attachment contained invoice or payment receipt.
Subject line is “Copy of your 123-reg invoice (123-458452066 )”
Message body has details about the order placed and they have attached the payment receipt. Support details are given at the end of the mail to make it look genuine and convince the user to open the attachment.
How it spreads on the system:
- Email has a PDF file and embedded Doc file in it
PDF name – 123-149715480-reg-invoice.pdf
Spreads via spam emails and tricks user to open it, stating payment receipt or invoice.
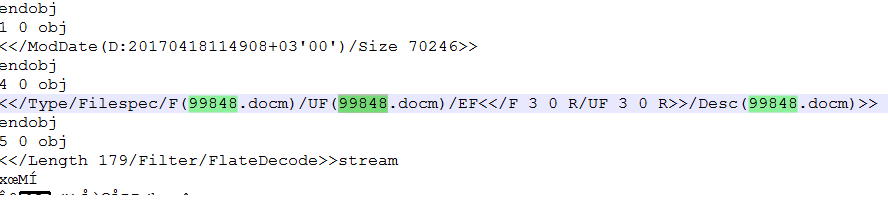
- Embedded Docm file inside the PDF
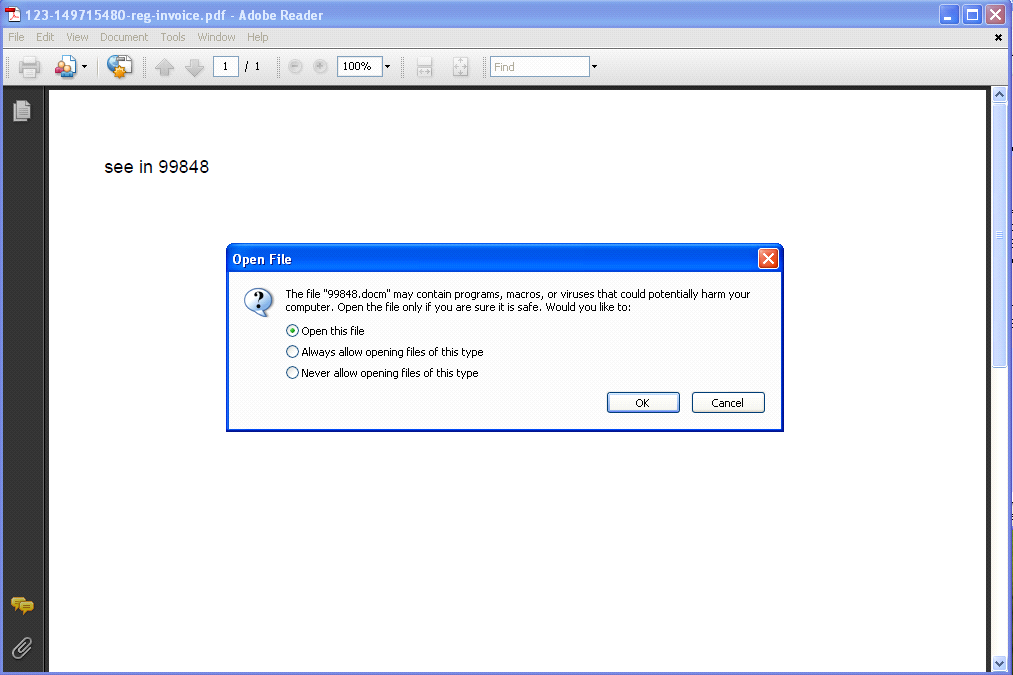
- After opening the PDF file, Adobe Reader shows a warning stating the Docm file you are opening can contain malicious macros or virus
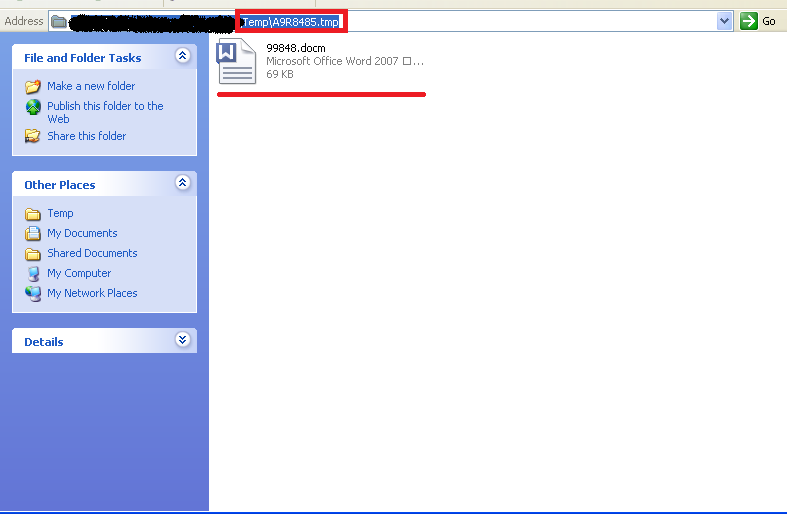
Here as we can see the docm file 99848 is responsible for infection.
- Drops Docm file at %temp% location such as “99848.docm”. Observed that it always drops a numeric docm file. File gets dropped when you click on “open the file” option shown during the warning when you open the PDF.
- Document file which is dropped opens in read only mode and a yellow bar appears to enable editing to gain access and execute.
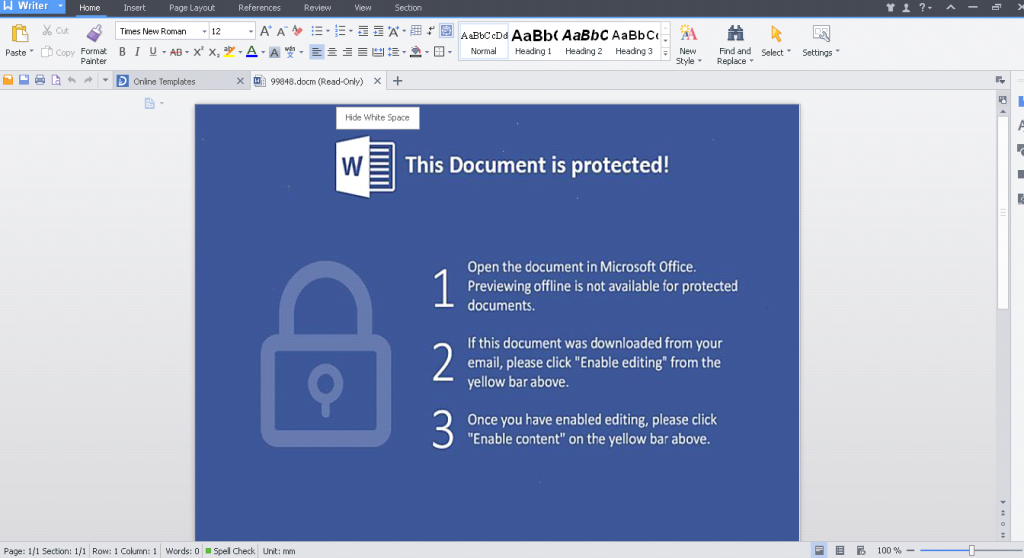
Dridex has changed its propagation method but the action remains the same. Similar way of spreading through Docm file, PDF just acts as a carrier. Stronger technique to identify spam mails and configure stronger firewall policy is a must.
Quick Heal Detection
- Quick Heal Email Protection feature successfully blocks such malicious attachments (the script file, in this case) even before they are executed.
- Quick Heal has given detection for the PDF and Embedded Doc file.
Precautionary Measures
- Email attachment containing double extension such as pdf.bin or doc.js should never be opened if they are from unknown or untrusted sources.
- Always visit websites which are known, do not click on any link or ad which shows tempting deals.
- Regularly update your antivirus so that your data and system is safe from the ongoing malware trends.
- Keep your software and operating system updated to ensure a secure digital environment.
ACKNOWLEDGMENT
Subject Matter Expert
• Nayan Vairagi
– Threat Research and Response Team




