Quick Heal Security Labs has been observing the infamous Locky ransomware outbreak which kicked off recently in the last week of September. The outbreak started with spam email with various subjects and different attachment names. On 26th September, spam campaign delivering a new variant of Locky ransomware started. The observed commonality in this campaign was the attachments ended with ‘.7z’ extension. After 26th September, we started seeing many such instances and soon it turned out to be a major outbreak. Let’s take a look at some of the important aspects of this campaign.
Infection Chain
A typical infection chain starts with spam email. Below is one such spam email used in this campaign,
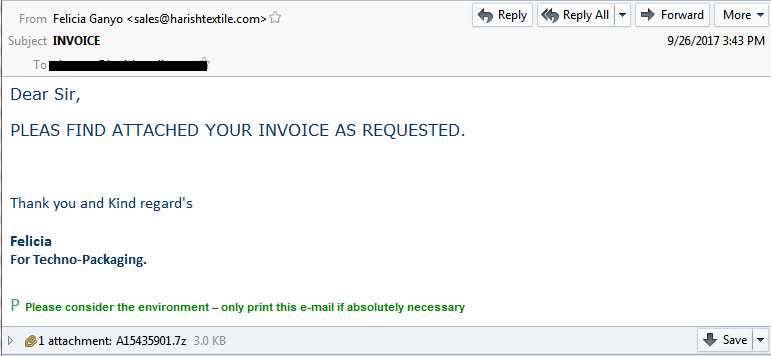
Fig 1: Spam e-mail with malicious ‘Invoice’ as an attachment
Few subject names and attachment observed are,
Subject Names:-
- Invoice PIS7316453
- 03_Invoice_7137
Attachment Names:-
- InvoicePIS7316453_7z.ANTIVIRUS-34287
- 001_4410.7z
As it can be seen from above, the subject names and attachments are different in every spam e-mail. This is generally done by attackers in order to evade the detection by security products.
The common thing between these emails is the attachments with .7z extensions which contains the malicious VBS file which downloads and launches the ransomware payload.
This variant is almost identical with the other Locky ransomware variants functionality wise with the only exception of the extension used by it for encrypted files. The extension used this time turned out to be an interesting one. It just reversed the previous well-known extension ‘.locky’ to ‘.ykcol’. Below is the screen-shot of the Locky ransom screen.
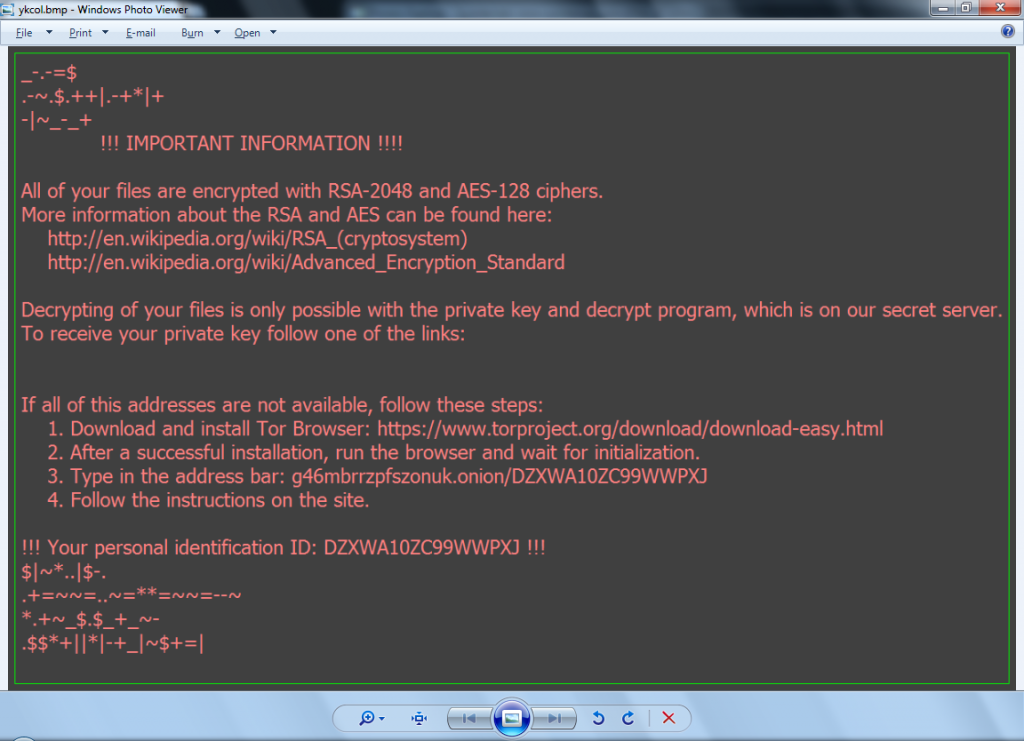
Fig 2: Locky Ransom screen
Also below HTML file with the same messages is dropped on the root of every drive.
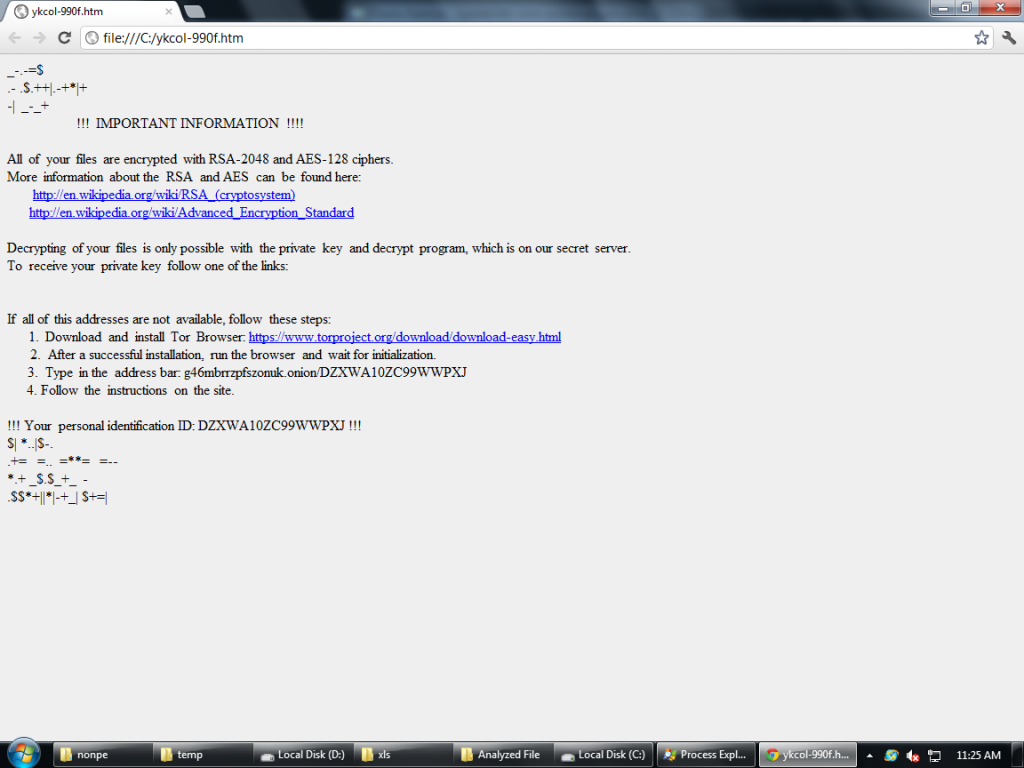
Fig 3: Locky ransom HTML message
Currently there is no decryptor available for any of the Locky ransomware encrypted files and this new version of Locky is no exception to it.
Quick Heal and Seqrite products provide protection against this outbreak of Locky ransomware through its multi-layered security offering.
Indicator of Compromise
- b035ddc1f0738c3f90cb5c0b804e1775
- efdb6033dccf27fe103b8fc13bc4f2d7
Subject Matter Experts
Shalaka Patil|Swapnil Nigade|Shriram Munde
Quick Heal Security Labs




