Contents
- Introduction
- Key Targets.
- Industries Affected.
- Geographical Focus.
- Infection Chain.
- Initial Findings.
- Looking into the decoy-document
- Technical Analysis
- Stage 1 – Malicious LNK Script
- Stage 2 – DUPERUNNER Implant
- Stage 3 – AdaptixC2 Beacon.
- Infrastructural Artefacts.
- Conclusion
- SEQRITE Protection.
- IOCs
- MITRE ATT&CK.
Introduction
SEQRITE APT-Team have recently uncovered a campaign, which has been targeting Russian corporate entities, specifically HR, payroll, and internal administrative departments—through the use of realistic decoy documents themed around employee bonuses and internal financial policies. The entire malware ecosystem involved in this campaign is based on usage of malicious LNK file, leading to we the usage of unknown implant, which we have dubbed as DUPERUNNER, which finally loads the AdaptixC2 Beacon which connects back the threat actor’s infrastructure.
In, this blog, we will explore the technical details of the campaign, we encountered during our analysis. We will explore the various stages of this campaign, starting from deep dive into the initial infection chain to the unknown implant used in this campaign, ending with a final overview covering the campaign.
Key Targets
Industries Affected
- Corporate Sector Employees.
- Human Resources & Payroll
Geographical Focus
- Russian Federation
Infection Chain
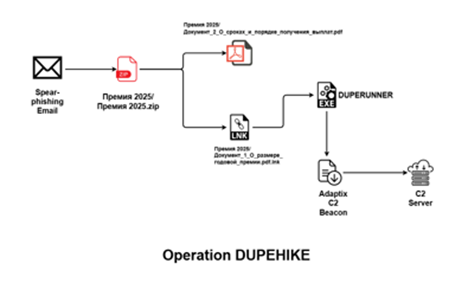
Initial Findings
Recently on 21 Nov 2025our team found a malicious ZIP archive, which surfaced on Virustotal, where the ZIP has been used as a preliminary source of spear-phishing based infection containing decoys with PDF and LNK extension, which downloads the implant DUPERUNNER which finally executes the Adaptix C2 Beacon.
The ZIP file named as Премия 2025.zip which translates to Bonus.Zip , which contains a malicious LNK named Документ_1_О_размере_годовой_премии.pdf.lnk which again translates to Document_1_On_the_size_of_the_annual_bonus.pdf.lnk , which basically is related to lure-oriented nomenclature. Then, this malicious shortcut(.LNK) is responsible for downloading the malicious implant using the LOLBIN known as powershell.exe, which we are track as DUPERUNNER. Further upon execution these downloads the Adaptix C2 beacon, connecting back to the command-and-control server. Now let us look into the decoy document.
Looking into the decoy-document
Initially looking into the decoy-document known as Document 2 – On the terms and procedure for receiving payments,which is initially named as Документ_2_О_сроках_и_порядке_получения_выплат.pdf is basically the lure related to the campaign.

The headline of the decoy, mentions On the size of Annual Bonus , further looking into the first paragraph, it mentions that the document is issued “for the purpose of regulating the system of material incentives for employees, and in accordance with the provisions of the Labor Code of the Russian Federation and the organization’s internal regulations.” It then outlines the procedure for determining the amount of the annual bonus, framing the document as a standard HR policy intended for internal corporate use, further laying down the entire lure into five key points.


Overall, the five key points in this decoy document outline the internal corporate rules for calculating an employee’s annual bonus, describing it as a performance-based incentive tied to KPIs, job responsibilities, and contribution to organizational goals.
The lure document sets a default bonus rate of 15% of the annual salary, unless otherwise specified, and explains that the final bonus amount depends on performance evaluations, strategic task completion, disciplinary record, and adherence to corporate standards.
It also furthers states that the employer may adjust the bonus upward or downward based on the company’s financial condition, departmental performance, and the employee’s personal contribution. Finally, the decision on the bonus is formalized through an official employer order that is final and must be communicated to the employee. This structure strongly aligns with internal HR and payroll workflows.
In the next section, we will look into the technical analysis.
Technical Analysis
We have divided the technical analysis into three stages. First, we will examine the malicious shortcut(.LNK) script embedded in the spear-phishing based ZIP file. Then, we will analyze the malicious implant, which we track as DUPERUNNER and then finally, we will focus on the Adaptix C2 based beacon, which is being downloaded and executed by the DUPERUNNER implant.
Stage 1 – Malicious LNK Script
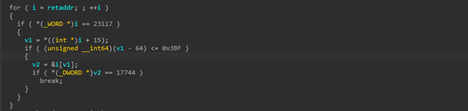
The ZIP file contains an LNK known as Документ_1_О_размере_годовой_премии.pdf.lnk, upon exploring it we became quite evident that the only sole purpose of the LNK is just to download from a remote server and execute the malicious implant DUPERUNNER using a Windows Utility known as powershell.exe
![]()
Looking into the command line arguments, it is now crystal clear that it is using powershell.exe with flags like -NoNI, -nop, and -w hidden to run completely in the background, while iwr (Invoke-WebRequest) is used to download the implant from the remote server 46[.]149[.]71[.]230 and save it as s.exe in the Temp folder. After that, the command immediately runs the downloaded implant.
In the next section, we will look into the technical capabilities of the implant known as DUPERUNNER.
Stage 2 – DUPERUNNER Implant
Upon initial analysis, we found that the s.exe file is the second stager which is programmed in C++.
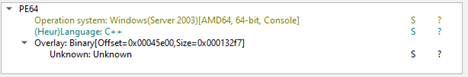
Now upon analyzing the very first fragments of the binary, we found that there are multiple interesting set of functionalities present inside the C++ implant known as DUPERUNNER.
Now, we will look into these interesting functions and analyze their functionalities.
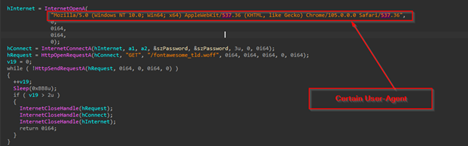
Upon looking into the first function that is DownloadAndOpenPDF , we encountered that this function takes two arguments, the one being the address, where the PDF is hosted and the other being the port number which is 80 . Finally, then using APIs such as InternetOpenA it uses a certain User-Agent and using GET request it tries to download a file which is hosted as fontawesome_tld.woff from the remote server, it also uses a small Sleep of 3 seconds before every multiple queries to download the file.
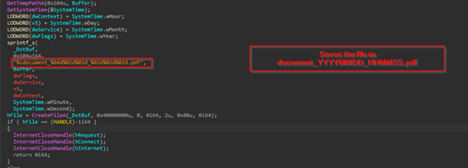
In, the next part of this same function, it enumerates the temporary path of the victim’s machine and also enumerates the system time using certain APIs and once enumerated the file is being saves to the Temp directory with the PDF named as per the time stamp of the machine, which leverages the benignness of the PDF.
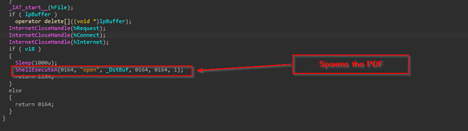
Well, finally once the PDF is downloaded, it then goes ahead and uses ShellExecuteA to spawn the PDF into the target machine.
Well, we found that there has been a little blunder from the threat actor’s end, as the PDF, which is being downloaded post this function, downloads the exact same decoy, which was already packed inside the spear-phishing ZIP, making the decoy present at the target’s machine twice, but unfortunately, due to unknown motives of this TA of dropping the decoy twice, we are still unsure whether this has been deliberately done or it is a blunder from TA’s end.
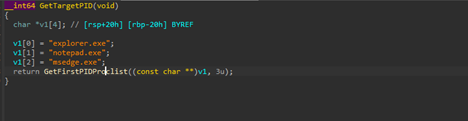
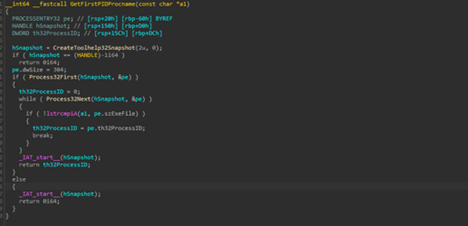
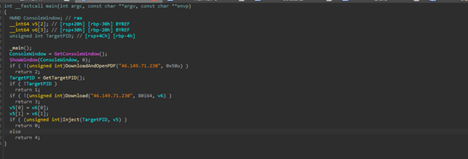
The next function GetTargetPID is quite straight-forward, that is, it enumerates for these set of processes which are explorer.exe, notepad.exe and msedge.exe, which will be used as a scape-goat process for classic process injection, and it does by using the CreateToolHelp API, which is commonly used for process enumeration before process injection.
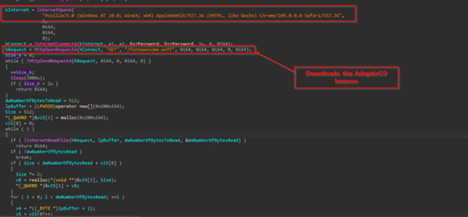
Now, looking into the third function Download , we can see that is using the similar User-Agent , just like the previous one, and this time it is downloading another file known as fontawesome.woff from the similar remote-webserver, and it uses a basic halt-try mechanism to query for the file and download it on the targets machine using the API known as InternetReadFile , which it saves to the target machine.
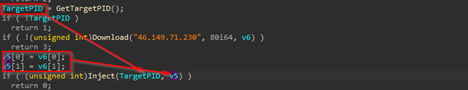
Now, moving onto the last function, of the DUPERUNNER implant, we see, that it takes two arguments, one being the TargetID and other being the shellcode of next stager buffer, which is then passed to perform process-injection.
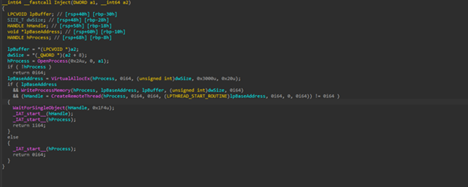
As, the name says, this function is using a classic Remote-Thread Injection where it allocates memory using VirtualAllocEx and then writes the shellcode into the target process, further going ahead with creating a new thread onto the target process, where the fourth parameter LPTHREAD_START_ROUTINE aka the lpBaseAddress contains the address of the shellcode which is the Adaptix C2 beacon in our case gets executed.
Finally, the last stager is executed on the target machine and the DUPERUNNER implant gracefully exits, in the next section, we will look into the Adaptix C2 beacon.
Stage 3 – AdaptixC2 Beacon
Now initially, looking into the file, we figured out, that this file named as fontawesome.woff is basically a stager file, which acts as a pseudo-bootstrapped loader to perform certain shenanigans and finally load the shellcode which is basically the C2 beacon onto the memory.
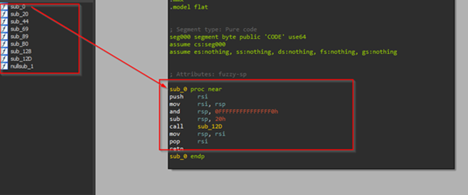
We also figured out that this stager-based payload only contains a few functions.
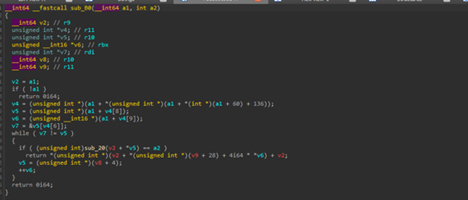
Moving ahead with sub_12D, it first does a clever trick to find its own hidden payload. It starts scanning its own memory from the current location and looks for the magic bytes 0x5A45 (which is “EZ” written backwards). When it finds this marker, it reads a number stored exactly 60 bytes later, that number is an offset to the real DLL that’s glued to the end of the shellcode. It then jumps there, does a quick sanity check, and confirms the data starts with “PE\0\0”.
![]()
Then looking ahead to the next set of functions, the sub_69 basically takes a hash of a DLL-Name which it is going to resolve.
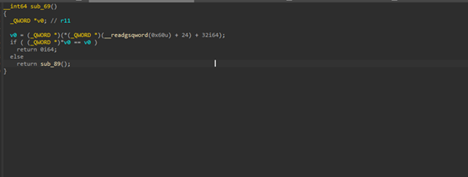
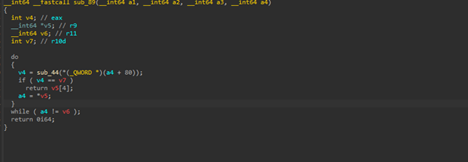
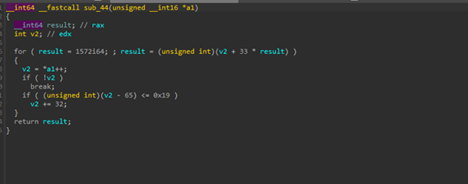
The entire DLL base address is resolved via the classic PEB->Ldr->InMemoryOrderModuleList traversal, where the malware walks the loaded module list and applies its custom, case-insensitive djb2-style hashing routine using a custom seed 1572 to each module name until it finds a match for the target hash (in this case, 0x19A59EC for ntdll.dll), where the other 0x7B348614 being kernel32.dll .
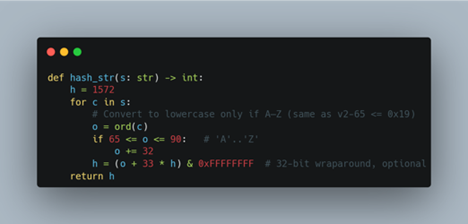
We wrote a simple Python-script which can be used to check against the ASCII-names of the DLL-Names.
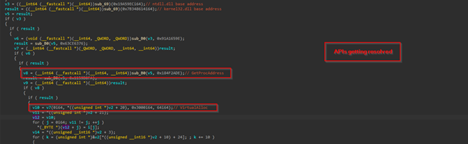
![]()
Next, once the DLLs’ base addresses were resolved, the APIs were also resolved by walking the export table and matching each exported function name against a custom hash value, allowing the malware to dynamically look up functions like VirtualAlloc, GetProcAddress and much more APIs for shellcode execution.
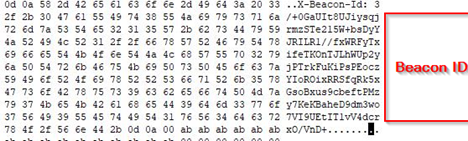
Now, once the shellcode was being executed, we extracted the config and found a few important artifacts such as the Beacon-ID of the implant.
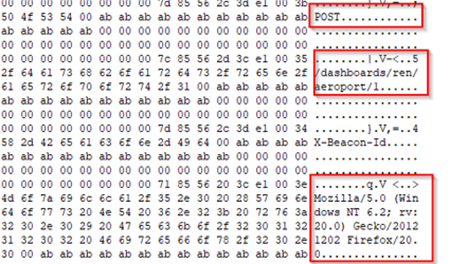
Apart from that, we also found that the beacon had been contacting the C2-remote host and using the POST method along with that, we also found the User-Agent related to it.
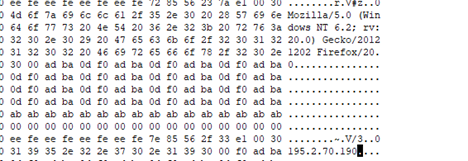
Well, the last interesting artefact, we found is the C2 URL, where the threat actor had hosted their infrastructure. As, the AdaptixC2 is an open-source project, we will not delve deep into the other code fragments, as it is already publicly available on the web, but the important artefacts such as the Beacon-ID, User-Agent and the C2-Host have been extracted above.
In, the next section, we will focus on the infrastructural details of this campaign.
Infrastructural Artefacts
Initially we found that there are two network related artefacts connected to these malicious campaigns, one of them, which the malicious LNK did use to download the DUPERUNNER implant, while the other being the remote host where the AdaptixC2 had been hosted.
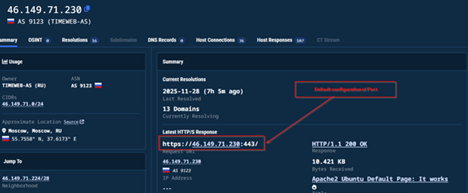
Well, upon quickly doing some network-based search, we saw that the IP address 46[.]149[.]71[.]230 latest update had been serving on port 443 which has been a default port configuration for AdaptixC2 HTTP Beacon, also a default Apache Web Server being running, with the default page.
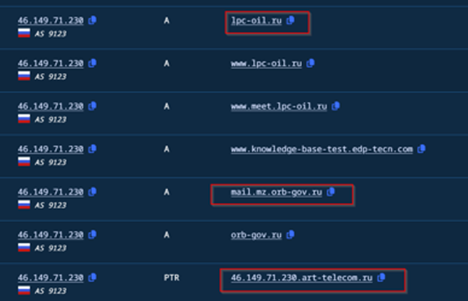
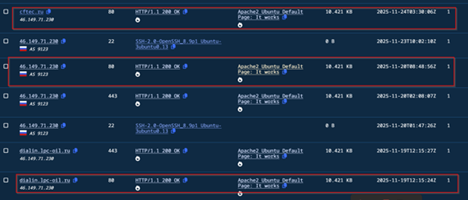
As, we saw on the DUPERUNNER implant, that this remote host, was only responsible for downloading the later stages, which was hosted on port 80, it is quite unique, we believe, that the TA have had changed the configurations to port 443, to later use it as the server to host AdaptixC2. Apart from that, we also saw that multiple interesting domains, with similar infrastructural overlaps, had been pointing to this similar address.
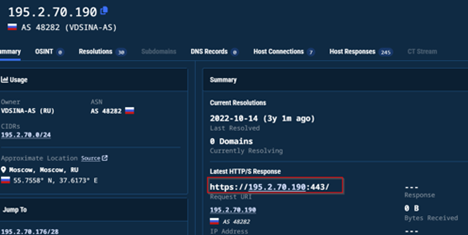
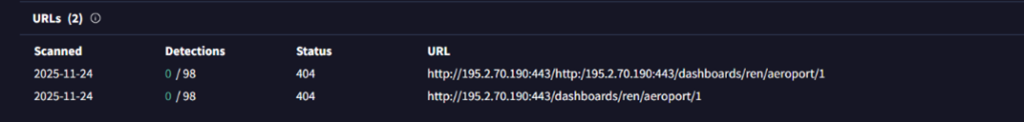
Now, going ahead to the next IP Address, we saw that the latest response on this C2-host, where the beacon had been connecting to, has the similar port-configurations, for the AdaptixC2 HTTP Beacon.
The malicious infrastructures are hosted under the ASN AS 48282 and AS 9123 under the organizations VDSINA-AS and TIMEWEB-AS.
Conclusion
We have been tracking this this campaign, since November 2025 under the cluster UNG0902 and discovered that it uses multiple malicious infrastructure and implants such as DUPERUNNER and AdaptixC2. Our research indicates that the threat actor is targeting employees of multiple organization. We will track this under the same cluster, while we attribute this ongoing campaign to any nation-state sponsored activity.
SEQRITE Protection
- Trojan.50169.SL
- Trojan.50168.GC
- Loader.S38592683
IOCs
| Hash (SHA-256) | File-Type |
| 87db5cbd76e7adeb6932c4ae14f3d3bb736d631460d65e067fb2a0083b675399 | EXE |
| d9e2b6341f6de5c95dd02cf3350c07cd2be3b0a78b82c073229396b6d4c8d3c1 | EXE |
| 3ce5ab897b7f33bc1b9036abc8e7d2812b385fbab404dad686afaf9fb83fe07a | EXE |
| 48b9f78899b8a3daaeb9cbf7245350a6222cbf0468cd5c2bab954c8dbbce3995 | EXE |
| 7157be86c6612c59e5120ae00260f4268b19560fa5a6fa52ed54d72868070d50 | 7zip |
| 432974205e1ce4c1d2c0e6bf6ebfafd90f6c19451eec0485ac46beaf65247763 | EXE |
| 1e0c5129ac74989754b7c27be9e12b1ebf90fa5f81db6d7fe5f1aa050a914cf9 | EXE |
| 3a52c13d00af0486095ee4007fd72dae646d3c7384754744507e33537b3fdf2a | EXE |
| 8c075d89eee37a58f1f3a8bf0cbd97e0c8f00e73179a36eb2cd8745024c1c4ee | EXE |
| 2cd715d0702fd70fda45c0569a38b3d983de1a8cf23b559293a7c0623da69c90 | EXE |
| ba6902efd3771a564785bdae68fa5f5ac12b7ebd828e8975459fff0136e2efdb | DLL |
MITRE ATT&CK
| Tactic | Technique ID | Technique Name | How It Applies to Operation DupeHike |
| Initial Access | T1566.001 | Spearphishing Attachment | Victims receive ZIP file containing malicious PDF-themed LNK lure (employee bonus policy). |
| Execution | T1204.002 | User Execution: Malicious File | User opens LNK file thinking it is a PDF, triggering execution. |
| Execution | T1059.001 | PowerShell | LNK launches PowerShell with -NoNI -nop -w hidden to download and execute DUPERUNNER from C2. |
| Execution | T1218.011 | System Binary Proxy Execution: Rundll32 / LOLBIN Execution | PowerShell and other LOLBINs are used to proxy execution of malicious components. |
| Execution | T1105 | Ingress Tool Transfer | PowerShell Invoke-WebRequest (iwr) downloads s.exe (DUPERUNNER) and later fontawesome.woff (AdaptixC2 stager). |
| Defense Evasion | T1036 | Masquerading | LNK posed as PDF, DLL posing as ZIP, WOFF posing as a font file. |
| Defense Evasion | T1027 | Obfuscated/Encrypted File | AdaptixC2 uses packed shellcode appended behind magic bytes (EZ). |
| Defense Evasion | T1027.007 | Dynamic API Resolution | AdaptixC2 resolves APIs using djb2-style hashing and PEB traversal. |
| Defense Evasion | T1055.003 | Thread Execution Hijacking | DUPERUNNER injects shellcode into legitimate processes (explorer.exe, notepad.exe, msedge.exe). |
| Defense Evasion | T1620 | Reflective Code Loading | AdaptixC2 loads its payload from appended shellcode using reflective loading techniques. |
| Discovery | T1082 | System Information Discovery | DUPERUNNER gathers hostname, domain, system time, Temp directory, creates victim GUID. |
| Discovery | T1057 | Process Discovery | DUPERUNNER enumerates processes (explorer.exe, notepad.exe, msedge.exe) using CreateToolHelp API. |
| Command & Control | T1071.001 | Application Layer Protocol: HTTP | DUPERUNNER uses HTTP GET to download decoy and beacon from 46.149.71.230. |
| Command & Control | T1132 | Data Encoding | Beacon results and communications encoded via internal routines. |
| Command & Control | T1095 | Non-Application Layer Protocol | AdaptixC2 may use raw TCP for beaconing (implied from C2 design). |
| Command & Control | T1573 | Encrypted Communication | AdaptixC2 beacon uses encryption during C2 communications. |
| Privilege Escalation / Defense Evasion | T1055 | Process Injection | DUPERUNNER injects AdaptixC2 shellcode into legitimate processes via Remote Thread Injection. |
| Collection | T1113 / T1005 | Local Data Collection | Beacon capable of retrieving system files as instructed by TA. |
| Exfiltration | T1041 | Exfiltration Over C2 Channel | Beacon sends encoded results/output to /result C2 endpoint via POST. |
| Impact | T1537 | Data Exfiltration | Steals system data and files from Russian corporate environments. |
Authors
- Subhajeet Singha
- Priya Patel
- Nandini Seth




