The SideCopy APT Group has expanded its activity this year and now targets critical Indian sectors this time.
Quick Heal Security Labs researchers have been tracking the notorious cyber-attack group – ‘Transparent Tribe’ since the first SideCopy campaign in September 2020, discovered by Quick Heal. The team has recently discovered an increase in SideCopy’s activities targeting certain Government agencies in India. The group has added new malware tools to its arsenal.
Another attack campaign that we discovered in March 2021 (ref. blog), seems to be part of the more extensive SideCopy campaign. The spear-phishing attack campaign used the Army Welfare Education Society’s scholarship form as a lure.
The second wave of SideCopy uses COVID-19 as a lure, which is not unique since, in the last year & a half, the COVID-19 theme has been used in numerous cyber-attacks. However, this is the first time that the COVID-19 theme is being used in the SideCopy campaign.
In most cases, successful execution of the attack would result in deploying a Remote Administration Tool. If a RAT gets installed, the attackers will get unrestricted access to the machine and steal sensitive data from these agencies.
Key Findings
- Operation SideCopy which is active from early 2019, is expanding its arsenal.
- The latest attacks in this campaign are using COVID-19 as a lure
- This campaign is targeting critical Government entities in India.
- Almost all CnC belongs to Contabo GmbH and server names are similar to machine names found in the previous report in September 2020.
- The attack results in the deployment of a Remote Administration Tool (RAT).
- The attack tools & methods have also been enhanced to make detection difficult.
Execution Chain
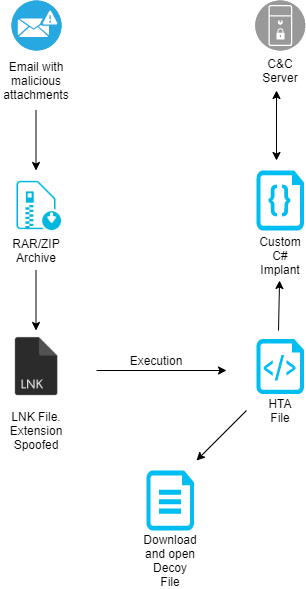
Custom C# Implant: ReverseRAT
The APT group carefully chooses their targets, upgrades tools in their arsenal based on the targets and mainly uses limited but effective functionality in being evasive.
Most of the backdoors used in the campaign are NJRat; however, in one specific case, we came across a new payload written in C#, which installs an implant enabling attackers to examine the target and install other backdoors. This implant appears to be an advanced version of the implant that we analyzed in our previous write-up.
How Seqrite protects its users?
We have the following detections for the malicious samples:
- APT.42504
- APT.42506
- Mshta.Downloader.41981
- Trojan.A1672450
- Trojan.Agent.41884
- YakbeexMSIL.ZZ4
- MsilFC.S17874654
- Ghanarava.1612026585faf3ed
- Agent
Also, the domains and IPs used are classified as malicious/compromised by Quick Heal.
Summary
The transparent Tribe attack group has been linked with Pakistan in the past as well. The evidence presented in this paper goes on to strengthen that claim even further.
In the current campaign, SideCopy/Transparent Tribe is once again targeting critical government entities in India. The attack tools & methods have also been enhanced to make detection difficult. This shows that this attack group is well-funded and actively improves attack mechanisms to infiltrate the target entities.
We advise our customers to be aware of such attacks, set up necessary cybersecurity controls, follow good cybersecurity practices, train their employees on cyber risks, and keep monitoring their environment for anything suspicious. For a more detailed analysis of operation SideCopy, please download our Targeting Critical Indian Infrastructure Operation SideCopy here:
Subject matter experts:
Chaitanya Haritash, Security Researcher II
Nihar Deshpande, Senior Security Researcher
Shayak Tarafdar, Security Research Lead




