Cyber Security threats today have become increasingly sophisticated and complex. Organizations, however, have not been able to evolve at the same pace. As organizations move ahead and embrace new technologies without fully comprehending the implications these have on the entire enterprise, they are rendering themselves vulnerable to an array of cyber security threats. The need for securing the IT infrastructure has been of prime importance for many organizations.
Windows 10 continues to be one of the most popular desktop operating systems for end users and, also for hackers for launching targeted cyber-attacks. Combating these attacks becomes a high priority for enterprises. Microsoft® releases security patches for their system vulnerabilities regularly and the best way to protect the IT infrastructure against attacks is to ensure that these patches are installed on every endpoint, as and when required.
The constantly evolving software landscape demands that the solution to managing Microsoft OS and apps has to be a centralized, automated and controlled process. Seqrite EPS v.7.0 now supports centralized patch management solution for all Microsoft application vulnerability needs from one single location. The feature is available with EPS Total and Enterprise Suite editions and is designed to improve IT efficiency, minimize IT downtime and protect enterprise endpoints from vulnerabilities.
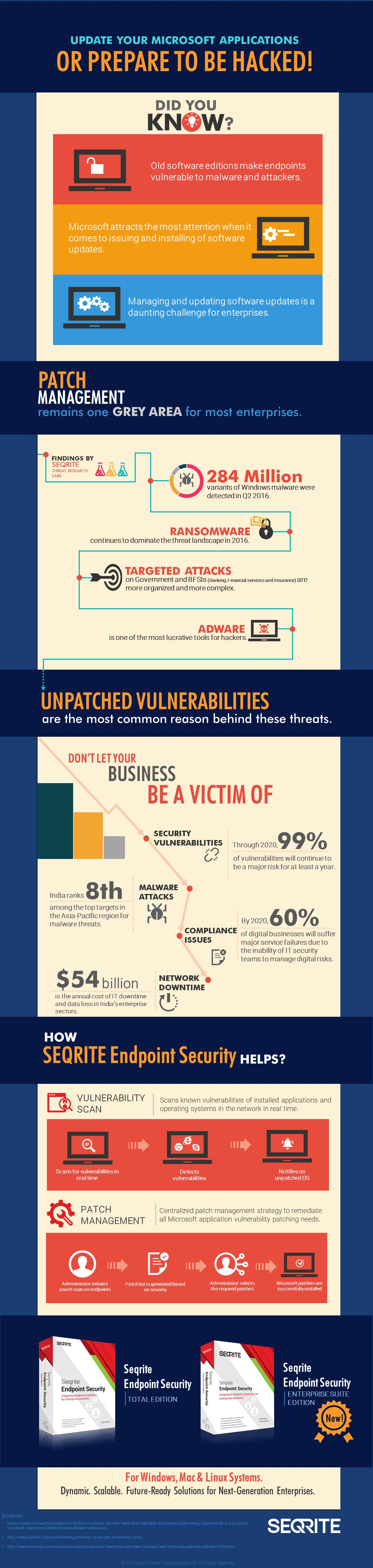
The infographic gives you information on the overall cyber threat scenario and how a centralized patch management solution works.
Click on the image below to view an enlarged version of the infographic.
Source:
www.microsoft.com