A few months back, Delphibased malware was being distributed on multiple systems via SMB exploit. The payloads used by this malware have close similarities with open-source Gh0stRAT code. Gh0st has been used by Chinese threat actors to target multiple agencies in Asia — Gh0st is a Remote Access Trojan having multiple capabilities like keylogging, microphone surveillance, download and execution of payloads from remote servers, restarting computers, taking the remote shell of systems, et al.
We have observed this malware targeting important institutions in India such as –
- Banks
- Railways
- Milk Distributors
- Hospitals and Pharmaceuticals
- Agro Industries
- Food Production Industries
After analysis, it was found that this malware is creating two different payloads app.exe and mfc.exe. After execution, both executables extract dlls in ststem32 folder of Windows directory and register them as service for persistence. Major code of all exacted payloads shares similarities with the open-source code of Ghost RAT.
Technical Analysis
Payload 1 – app.exe
This executable had an embedded DLL file stored in reverse order as shown in the below figure.
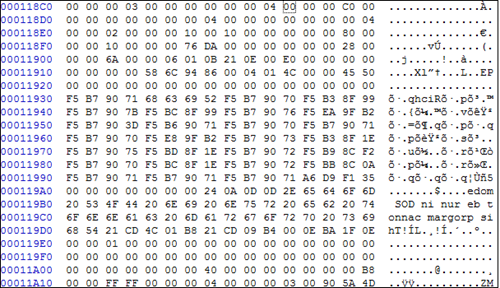
This embedded binary is decrypted and written to %SYSTEMROOT%\System32\ folder. The below code shows the decryption code — DLL name is generated from the return value of GetTickCount() API.
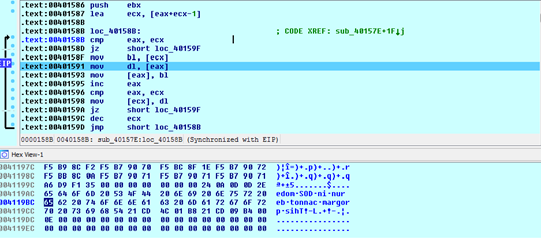
App.exe then registers this DLL as service by calling Install exported function. Below are details of service:
ServiceName: csrss
DisplayName: Security Manager Accounts
DesiredAccess: SERVICE_ALL_ACCESS
ServiceType: SERVICE_WIN32_OWN_PROCESS|SERVICE_INTERACTIVE_PROCESS
StartType: SERVICE_AUTO_START
ErrorControl: SERVICE_ERROR_IGNORE
BinaryPathName: %SystemRoot%\System32\svchost.exe -k “csrss”
The exported function of DLL are as below:
- DllUpdate
- Install
- MainThread
- ServiceMain
- Uninstall
C2 Functions
There are multiple C2 commands observed in the code of Gh0stRat. Some C2 functions observed by static analysis of DLL are as below:
- Shutdown System
- Open URL
- Download and Execute File
- Find Process
- Clean Event Logs
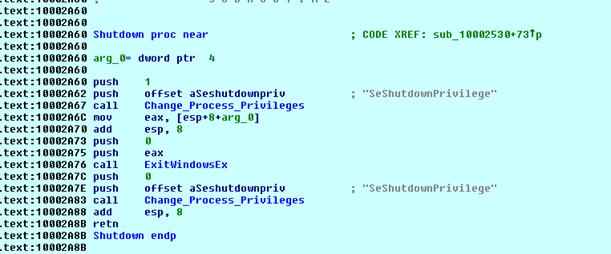
Shutdown System
This function takes shutdown debug privileges and calls the ExitWindowsEx() function to shut down systems.
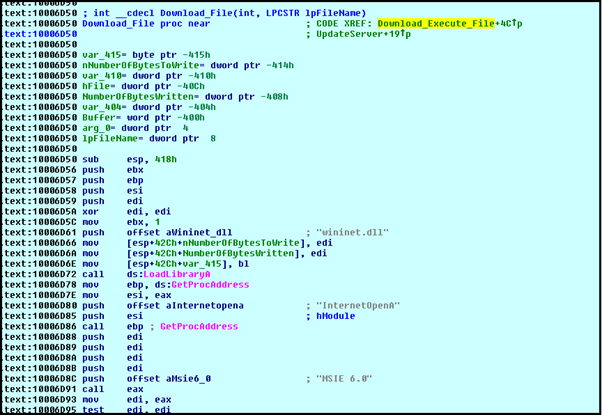
Download and Execute File
This function will download a specific file from the server and execute it.
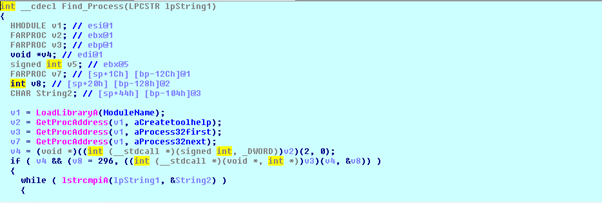
Find Process
This function searches for a specific process by calling process enumeration APIs.
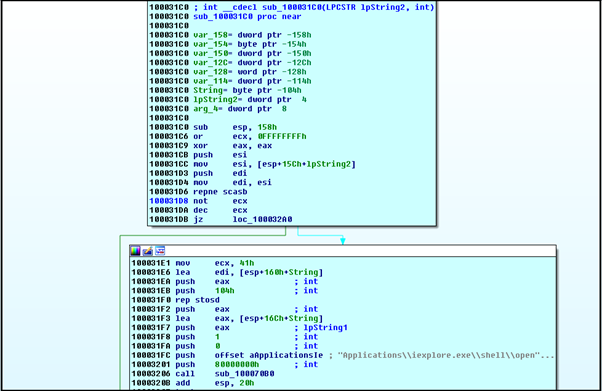
Open URL
This function creates an iexplore.exe process with a specified URL.
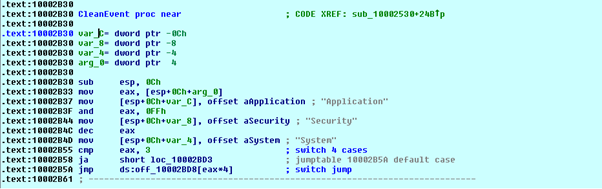
Clean Event Logs
This function clears all event logs of Application, Security, and System
Payload 2 – mfc.exe
The second executable dropped by the main payload is mfc.exe having embedded executable in resource under the name “BIN”.
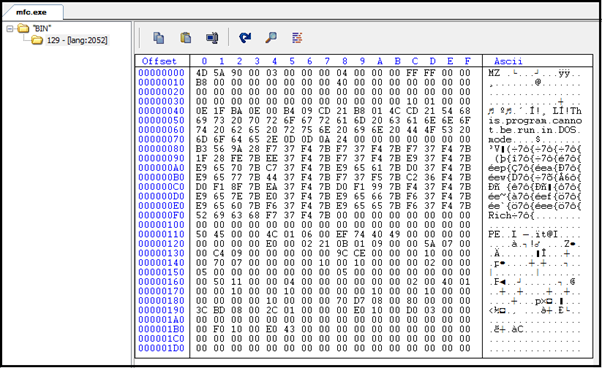
When this payload is run it drops dll (random name) from the above resource into the system32 folder and installed as a service with the name “NetworkServices” on an infected system. After creating DLL into the system32 folder, mfc.exe calls the Install() function of dll.
This DLL has four exported functions as below:
- Install
- Launch
- ServiceMain
- UnInstall
Below are C2 Commands observed in this sample:
- Install Keyboard Hook
- Process Enumeration
- Remote Shell
- Audio Capture
- Download and Execute File
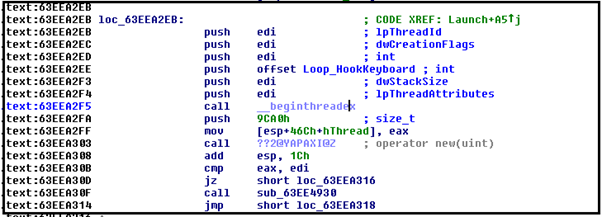
Install Keyboard Hook
Below figure, XX shows that a thread is created to install a keyboard hook. All keylogging data is written to a file named “syslog.dat”.
Figure XX shows a similar keylogger code of Gh0st RAT.
Process Enumeration
Process enumeration involves getting the list of running processes to enumerate modules.
Remote Shell
This function will create a remote shell to accept and execute any command.
Audio Capture
This function records audio with the help of functions like waveInOpen(), waveInStart(), waveInStop() etc.
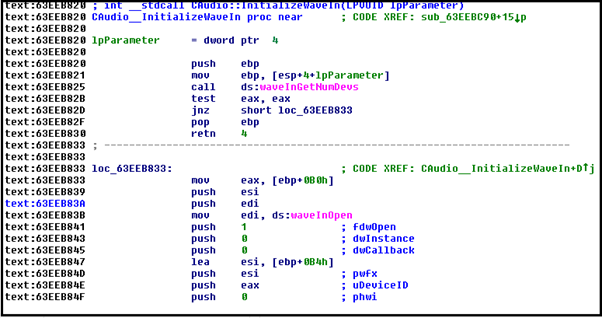
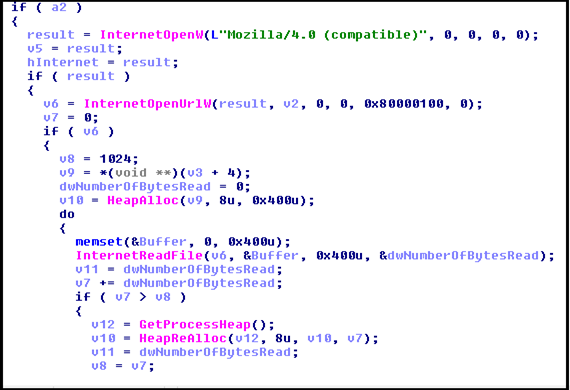
Download and Execute File
Function to download the executable file from a remote server and execute it.
IOCs
- FF6511DE176A434FA2F7C939795A13CC
- A6CC92A1993F040E87090F8B89836332
- 550C055339A9FEC141997CDA3F32FD0A
- A2B75BD7254997BEC6A19D752E26FA50
- 4B8C6D70A186FEC7C79D5B52B2FF0E76
- E22E5A85ED5294B179EBD416EEB5BEBB
- 5CE36CBD7D4A58A1B1A8C5B7BE194F23
- E94F9AF9EA11301831AAA1BDE34D3DEB
- 23D4EC869960CE02865C98F64581136A
- 367150E5DA2ED1BFAAE9210105BCEEA1
- BFB095C595FAA47CBFD4AB6199A7E297
- CA07E26D95D927953197840EA93EDD03
- 6B8A19DF9827CFB95F6461FEF9929F83
- 7DC43FCA774E612BF611ACD882400308
- 1127149CB5378FCA7181F81EB8149FC9
- F1E921F5730919E946D9A64019867E13
- B80A559CD7D48C9D3115A013EA662263
- 9403464BB99D87A02667E3E5DBA4A57C
Alerts
Conclusion
These samples are modified variants of Gh0st RAT and actors are constantly updating them to evade AV detections. Samples and TTPs that are seen in victim organizations are mostly associated with China-based APT groups. We have been following these samples for the last 1 month but were unable to identify the initial attack vector. As they are targeted towards specific industries, we suspect to find more malware associated with these attack chains. Interestingly few of the victims were also infected with Monero miners during the same period. We would be closely monitoring the campaign to hunt for the entire infection chain.
Subject matter experts
Pavankumar Chaudhari
Kalpesh Mantri




