Authors: Dixit Panchal, Soumen Burma & Kartik Jivani
Table of Contents
- Introduction:
- Initial Analysis:
- Analysis of Decoy:
- Infection Chain:
- Technical Analysis:
- Infrastructure Hunting:
- Conclusion:
- Seqrite Coverage:
- IoCs:
- MITRE ATT&CK:
Introduction:
Seqrite Lab has been actively monitoring global cyber threat activity and has recently uncovered an ongoing campaign leveraging a Command and Control (C2) infrastructure hosted in the United States. The threat actors behind this operation are specifically targeting Chinese individuals seeking employment opportunities in the FinTech, cryptocurrency exchange, and trading platform sectors—particularly for engineering and technical roles.
This campaign primarily employs sophisticated spear-phishing techniques. The adversaries craft highly targeted emails impersonating job seekers and send them to HR departments and technical hiring teams within Chinese firms. These emails often contain malicious .LNK (Windows shortcut) files embedded within seemingly legitimate résumés or portfolio documents. When executed, these .LNK files act as droppers, initiating the execution of payloads that facilitate initial compromise.
Initial Analysis:
Upon detailed analysis of the campaign, it was observed that the deployed malware establishes persistence within the compromised system and initiates various reconnaissance operations. These include capturing screenshots, harvesting clipboard contents, and exfiltrating critical system metadata. The collected data is covertly transmitted to a remote Command and Control (C2) server under the control of the threat actors. This exfiltrated information significantly elevates the risk of advanced cyber-espionage, identity theft, and credential compromise, thereby posing a serious threat to both organizational infrastructure and individual privacy.
Analysis of Decoy:
Basically, The PDF is a Chinese-language résumé, which contain experience as senior backend / blockchain full-stack engineer (Java + Solidity) with experience building high-throughput trading systems and DeFi/smart-contract projects. It lists a bachelor’s degree from 华南农业大学 – South China Agricultural University (2008–2012), work history in 惠州 and 深圳 (Guangdong province) including founder/tech-lead roles, and many crypto/DeFi and high-concurrency trading system projects. The CV emphasizes Spring Cloud microservices, RocketMQ, MySQL, Solidity/Hardhat, and production experience for trading exchanges and DeFi protocols (TVL and customer counts are claimed).

Evidence locating origin / country:
- Language: the entire document is written in Simplified Chinese — typical for mainland China.
- University: 华南农业大学 (South China Agricultural University)— a university located in Guangdong, China.
- Work locations / companies: the CV mentions 惠州 (Huizhou) and 深圳 (Shenzhen) — both cities in Guangdong province, PRC. Company names like “惠州智灰兔科技有限公司 (Huizhou Zhihuitu Technology Co., Ltd.)” and “惠州市睿思通网络科技有限公司 (Huizhou Ruisitong Network Technology Co., Ltd.)” point to Chinese companies.

The resume is localized and credible for Chinese targets: Chinese language, Chinese universities, and local company names make it believable to Chinese users. That increases the chance a user will open it (social engineering).
Infection Chain:
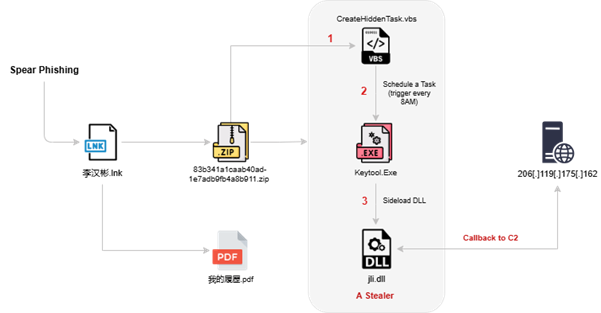
Technical Analysis:
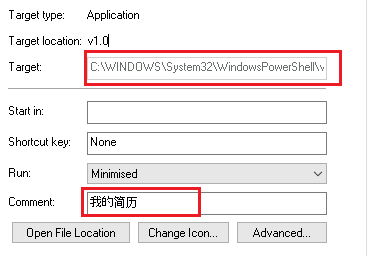
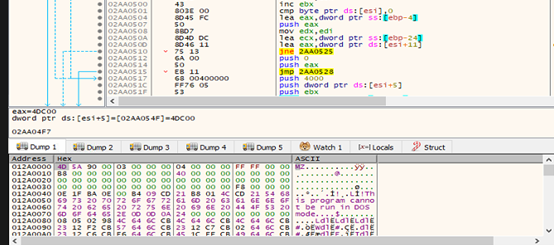
During initial static analysis of the downloaded shortcut 李汉彬.lnk, we observed more than 260-character sequences consistent with a PowerShell command-line payload. The command appears to reference a target file path (see snapshot), suggesting the LNK acts as a dropper/execution vector for a subsequent PowerShell-based stage.
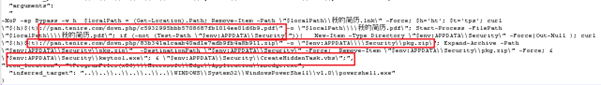
During initial analysis and parsing of the code, we discovered the following notable indicators: the sample appears capable of downloading additional files (see snapshot).
The sample connects to pan.tenire.com and downloads additional artifacts, including a decoy resume document, keytool.exe, CreateHiddenTask.vbs, and jli.dll.
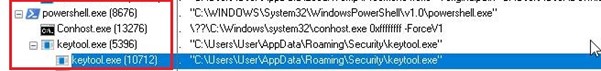
When we executed the sample LNK in our secure environment, it downloaded a second-stage payload to C:\Users\<user>\AppData\Roaming\Security and executed it.
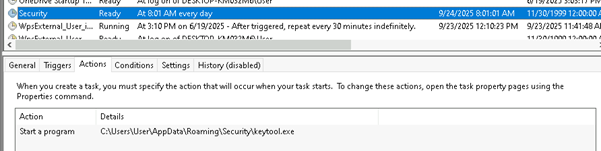
Additionally, the malware deploys a scheduled task via the CreateHiddenTask.vbs script. This task is designed to execute keytool.exe every day at 8:00 AM, ensuring persistence and regular execution of the malicious payload.
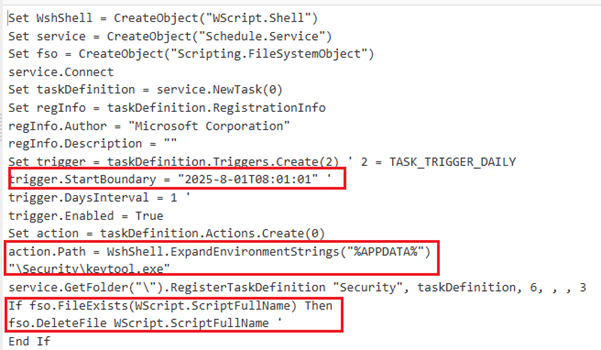
The VBScript instantiates COM objects (WScript.Shell, Schedule.Service, Scripting.FileSystemObject), connects to the Task Scheduler, and programmatically creates a daily scheduled task named “Security” (trigger type = daily, StartBoundary = 2025-08-01T08:01:01, DaysInterval = 1) whose action executes %APPDATA%\Security\keytool.exe (constructed via ExpandEnvironmentStrings); it also sets the task registration metadata to Author = “Microsoft Corporation” (likely spoofing a benign author) and, after registering the task in the root folder, deletes the VBScript file itself to reduce forensic traces—effectively providing persistent, scheduled execution of the dropped payload.
Analysis of Keytool and Jli.dll
Upon analyzing keytool.exe we found that it is calling different export funtion of Jli.dll like JLI_CmdToArgs, JLI_GetStdArgc, JLI_GetStdArgs etc as shown in below fig.
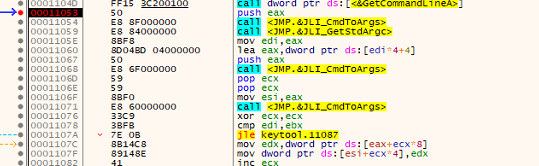
Upon analysing the loader Jli.dll we found that this loader quietly opens its own executable (keytool.exe), reads a specific region derived from the PE headers, and scans that region for a distinct 8-byte marker sequence: 1C 3B 7E FF 1C 3B 7E FF. Once it finds the marker, everything after it is copied into a buffer and treated as an encrypted payload. The function then constructs a 256-byte S-box and runs the standard RC4 routine: a KSA (key scheduling) seeded with the ASCII key “123cba”, followed by the PRGA (keystream generation) which XORs the keystream with the copied bytes to produce the decrypted payload.
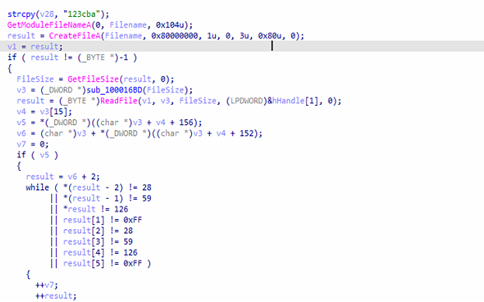
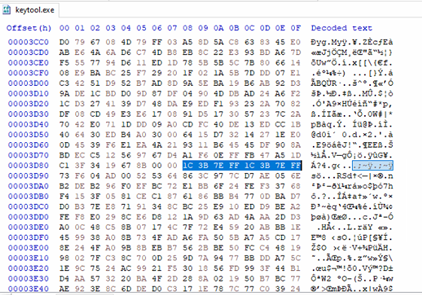
Inside Keytool.exe there is an encrypted shellcode payload — i.e. the malicious code is hidden and scrambled so that static analysis won’t detect it immediately.
Once the shellcode is decrypted (at runtime, in memory), it reveals its built‑in command‑and‑control (C2) server address: 206.119.175.16.
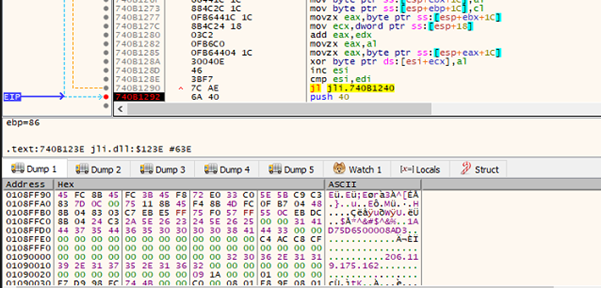
After decryption the routine calls a set of helper functions that appear to prepare and launch the payload (likely by creating or duplicating a process/handle and injecting or executing the decrypted data), performs a few process-related housekeeping calls, and finally waits on a handle to synchronize execution. In short: it’s a compact self-extracting loader — marker-based extraction + RC4 decryption using a fixed key — that drops an in-memory payload and then triggers its execution while waiting for completion.
Analysis of 2nd Payload (ValleyRAT)
Upon our analysis, we found the 2nd payload file, we found that it contains code of ValleyRAT.
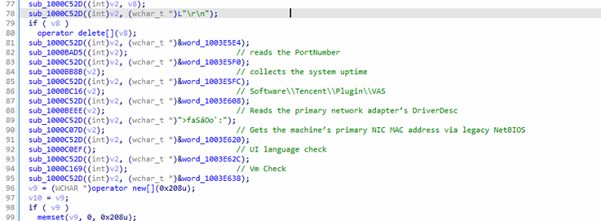
System fingerprinting
It collects CPU info, username, screen resolution, port number, uptime, NIC details, MAC, locale, VM check, registry values, and other identifiers.
| Function | One-line Purpose | Notes | ||
| sub_1000BAD5 | Opens HKLM\\…\\Tds\\tcp, reads PortNumber DWORD and appends its decimal + \\r\\n. | reads of …\\Tds\\tcp\\PortNumber. | ||
| sub_1000BB8B | Reads GetTickCount() and appends formatted uptime (days/hours/minutes) + \\r\\n. | Simple uptime fingerprint; benign but useful for reconnaissance. | ||
| sub_1000BC16 | Enumerates HKCU\\Software\\Tencent\\Plugin\\VAS subkeys (6–11 chars) or scans user folder for numeric directory names; appends space-separated results + \\r\\n. | Fingerprints QQ/Tencent accounts or numeric IDs; detect enumeration of that Tencent key or folder scans for numeric dir names. | ||
| sub_1000BEEE | Uses NetBIOS (NCBENUM/NCBRESET/NCBASTAT) to obtain NIC MAC, formats XX-XX-… and appends + \\r\\n. | Legacy NetBIOS calls to read MAC — uncommon in modern apps; monitor NetBIOS NCB usage. | ||
| sub_1000C07D | Attempts to read primary NIC DriverDesc from device-class registry and append it + \\r\\n. | |||
|
Maps GetSystemDefaultUILanguage() to a stored locale string and appends it + \\r\\n (locale fingerprinting) | Checks whether the UI language is Taiwanese, Mainland Chinese, Hong Kong, Singapore, Macau, or English (US/UK) |
Anti-Vm Tricks
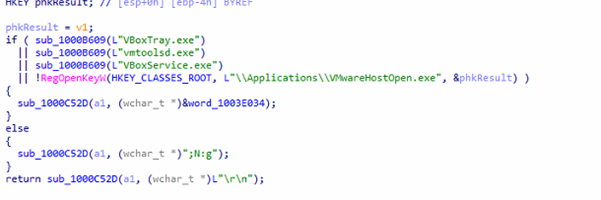
Valleyrat malware checks for virtualization by looking for VirtualBox/VMware processes or the VMware registry key.
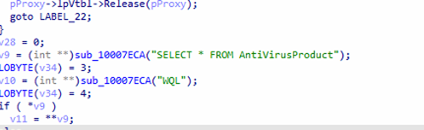
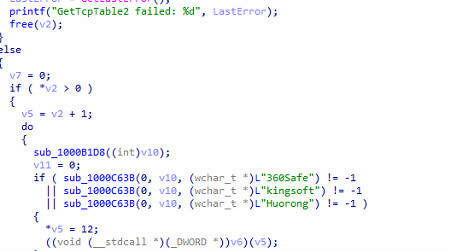
AV Evasion
It leverages COM/WMI to query ROOT\SecurityCenter2 for AntiVirusProduct, executes SELECT * FROM AntiVirusProduct, retrieves each displayName, and then converts/normalizes the results.
Afterward, it invokes the function to locate and uninstall the detected AV products.
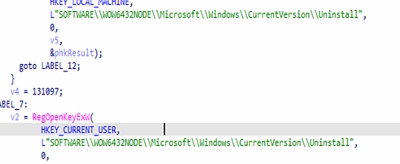
Kill AV network connections
This function repeatedly queries the system’s TCP connection table using dynamically resolved APIs.
It identifies processes associated with “360Safe”, “kingsoft”, or “Huorong” by checking the owning process path.
If a match is found, it forcefully terminates their TCP connections by setting the state to DELETE_TCB.
Overall, it’s an anti-AV routine designed to disrupt security software’s network activity. Shown in below fig.
Exfiltration Activities through command
The variant is designed to capture visual user activity (screenshots/recording) and to deliver and install plugins or other malicious payloads on the victim machine.
These are some commands
| Offset (Opcode) | Description |
| 0x78 (120) | Save IP list |
| 0x7B (123) | Session/HWID |
| 0x7D (125) | File/transfer handler |
| 0x83 (131) | Plugin update (216-byte header) |
| 0x84 (132) | Plugin install/add |
| 0x85 (133) | Filter management |
| 0x86 (134) | Screenshot config |
| 0x87 (135) | Clipboard config |
| 0x88 (136) | Keylogger control |
| 0x89 (137) | Recording / cleanup |
| 0x8A (138) | BoxedApp SDK init |
| 0xA1 (161) | Format/route frame |
| 0xA2 (162) | Self-uninstall |
| 0xA4 (164) | Group/Remark strings |
| 0xA5 (165) | Info sync |
| 0xA6 (166) | UI “OK” |
| 0xA7 (167) | Console profile |
| 0xC8 (200) | Transport/socket setup |
Malware’s keylogging capability
It prepares the logging environment by creating a dedicated directory and log file (Regedit.log) under ProgramData, performing simple log rotation if the file grows too large, and initializing a DirectInput keyboard device to capture keystrokes with a buffered input model. It also records the Caps Lock state at startup to ensure accurate key interpretation.
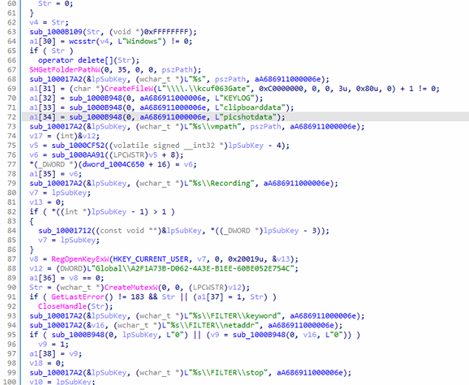
System reconnaissance routine
Valleyrat has a system environment survey routine that collects host information by probing registry keys, security settings, file paths, and custom driver handles.
It sets a series of feature flags (a1[26..39]) indicating things like UAC mode, AV/driver presence, keylogger/clipboard/screenshot toggles, and single-instance mutex status.
It helps the malware decide which features to enable, what protections exist, and whether it’s already running. that indicate features such as UAC mode, AV/driver presence, keylogger/clipboard/screenshot toggles, as well as
| Index | What it checks | How it checks | Meaning when set (=1) |
| a1[26] | IE config present for current user | Reads HKCU\Software\Microsoft\Internet Explorer (via sub_10009F0E) | IE settings value exists (string ptr non-null) |
| a1[27] | Ability to open SECURITY hive | RegOpenKeyExW(HKLM, “SECURITY”, KEY_READ | …)` |
| a1[28] | UAC secure desktop prompt enabled | HKLM\…\Policies\System\PromptOnSecureDesktop == 1 | Secure Desktop for elevation prompts is ON |
| a1[29] | 360 HVM service autostart | HKLM\SYSTEM\ControlSet001\Services\360Hvm\Start | Value == 1 (system/auto start) ⇒ 360 driver/service present |
| a1[30] | OS string contains “Windows” | Fills buffer via sub_1000B109, searches wcsstr(…,”Windows”) | Host OS looks like Windows |
| a1[31] | Custom device handle exists | CreateFileW(“\\\\.\\kcuf063Gate”, …) | Can open that device (likely a rootkit/driver comms gate) |
| a1[32] | “KEYLOG” feature toggle | “%APPDATA%\\A686911000006E”, “KEYLOG”) | Keylogging folder/key present/enabled |
| a1[33] | “clipboarddata” feature toggle | Same path lookup with “clipboarddata” | Clipboard capture enabled |
| a1[34] | “picshotdata” feature toggle | Same path lookup with “picshotdata” | Screen/webcam snapshot enabled |
| a1[35] | VM path byte/flag | Builds %APPDATA%\A686911000006E\vmpath, parses via sub_1000CF52/sub_1000AA91 | Extracted byte set and copied to a global + this flag |
| a1[36] | “Recording” subkey exists | Opens %APPDATA%\A686911000006E\Recording in HKCU | Recording config present |
| a1[37] | Single-instance mutex present | CreateMutexW(“Global\\A2F1A73B-…E754C”), checks GetLastError()==ERROR_ALREADY_EXISTS | Another instance is running (or it marks itself as such) |
| a1[38] | Filter rules enabled | Checks %APPDATA%\A686911000006E\FILTER\keyword or …\FILTER\netaddr against “0” | Any non-“0” ⇒ filters active |
| a1[39] | “stop” kill-switch | Reads %APPDATA%\A686911000006E\FILTER\stop into v18 | Non-zero byte ⇒ stop/disable behavior |
Infrastructure Hunting:
Upon analysing the C2 infrastructure, we discovered that it is hosted by SONDERCLOUDLIMITED (SonderCloud Limited). Additionally, several associated domains resolve to IP addresses located in the HK. All identified domains use the. work TLD and are actively being utilized by threat actors.
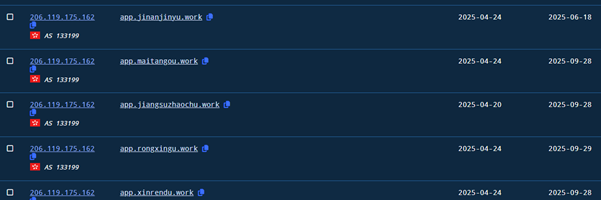
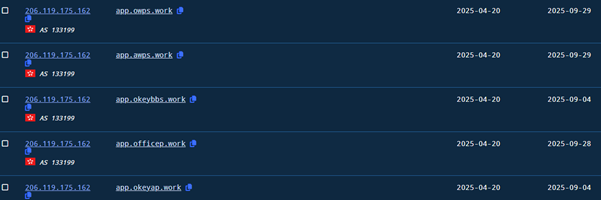

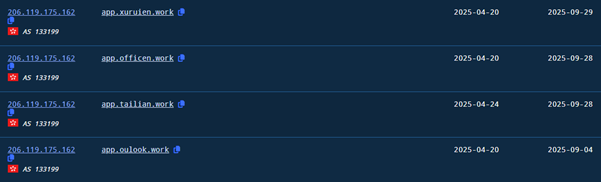
In addition to the pan.tenire.com domain used to deliver the résumé decoy and malicious payloads, we identified a broader infrastructure cluster on 206.119.175.162 (AS133199, SonderCloud Limited, Hong Kong). At more then 20+ sibling domains (app.jinanjinyu.work, app.maitangou.work, app.jiangsuzhaochu.work, app.rongxingu.work, app.xinrendu.work, app.owps.work, app.awps.work) were observed pointing to the same IP. The consistent naming convention (app.*.work) and use of the .work TLD strongly suggest these were intended to impersonate job portals or work applications, fitting neatly with the résumé-themed lure. This indicates a deliberate effort to build a thematic, resilient infrastructure set supporting Operation Silk Lure.
Conclusion: Why Operation Silk Lure?
“Silk” = China-related footprint, and “Lure” = the résumé decoy used to entice victims.
We named this campaign Operation Silk Lure: Scheduled Tasks Weaponized for DLL Side-Loading because each element of the label maps directly to observable, evidence-backed TTPs: “Silk” signals the campaign’s China-centric footprint (a Simplified-Chinese résumé decoy, hosting and DNS activity on Tencent Cloud/DNSPod and Chinese-pinyin domain names), “Lure” calls out the social-engineering vector (a believable CV used to trick developers, recruiters and HR into opening the file), “Scheduled Tasks” points to the persistence mechanism we recovered (a dropped CreateHiddenTask.vbs that registers a daily Task Scheduler job named Security), and “DLL Side-Loading” highlights the post-execution technique (a keytool.exe loader that side-loads a malicious DLL).
The name is intentionally descriptive and non-speculative — every token corresponds to an observed artifact or behavior — and is therefore immediately actionable for defenders hunt for pan.tenire.com DNS queries and -NoP -ep Bypass PowerShell commandlines, %APPDATA%\Security\* artifacts, the Security scheduled task, and anomalous ImageLoad events tied to keytool.exe.
Seqrite Coverage:
- Ghanarava.17599037699ce501
- Trojan.50027.GC
- Trojan.50026.GC
IoCs:
| MD5 | File Name |
| 6ea9555f1874d13246726579263161e8 | CreateHiddenTask.vbs |
| f5b9ad341ccfe06352b8818b90b2413e | 李汉彬.lnk |
|
83b341a1caab40ad1e7adb9fb4a8b911 |
83b341a1caab40ad1e7adb9fb4a8b911.zip |
| 3ca440a3f4800090ee691e037a9ce501 | jli.dll |
| e94e7b953e67cc7f080b83d3a1cdcb1f | keytool.exe |
C2:
- 206.119.175.65
- 206.119.175.178
MITRE ATT&CK:
| Initial Access | T1566.001 | Spearphishing Attachment |
| Execution | T1059.001 | Command and Scripting Interpreter: PowerShell |
| T1059.005 | Command and Scripting Interpreter: Visul Basic | |
| T1053.005 | Scheduled Task/Job: Scheduled Task | |
| T1204.002 | User Execution: Malicious File | |
| Persistence | T1053.005 | Scheduled Task/Job: Scheduled Task |
| T1547.001 | Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder | |
| Privilege Escalation | T1055.001 | Process Injection: Dynamic-link Library Injection |
| T1055.002 | Process Injection: Portable Executable Injection | |
| Defense Evasion | T1140 | Deobfuscate/Decode Files or Information |
| T1574.001 | Hijack Execution Flow: DLL | |
| T1070.004 | Indicator Removal: File Deletion | |
| T1070.009 | Indicator Removal: Clear Persistence | |
| T1036.008 | Masquerading: Masquerade File Type | |
| T1112 | Modify Registry | |
| T1027.009 | Obfuscated Files or Information: Embedded Payloads | |
| T1027.010 | Obfuscated Files or Information: Command Obfuscation | |
| T1027.013 | Obfuscated Files or Information: Encrypted/Encoded File | |
| T1055.001 | Process Injection: Dynamic-link Library Injection | |
| T1497.001 | Virtualization/Sandbox Evasion: System Checks | |
| T1497.002 | Virtualization/Sandbox Evasion: User Activity Based Checks | |
| Credential Access | T1555.003 | Credentials from Password Stores: Credentials from Web Browsers |
| T1056.001 | Input Capture: Keylogging | |
| T1056.002 | Input Capture: GUI Input Capture | |
| T1556.004 | Modify Authentication Process: Network Device Authentication | |
| Discovery | T1083 | File and Directory Discovery |
| Data Collection | T1115 | Clipboard Data |
| T1005 | Data from Local System | |
| T1039 | Data from Network Shared Drive | |
| T1113 | Screen Capture | |
| Command and Control | T1071.001 | Application Layer Protocol: Web Protocols |
| Exfiltration | T1041 | Exfiltration Over C2 Channel |




